Day 67 of #100DaysOfDeFI 🚀 Today I continued creating a basic DEX 👩🏻💻 and focused on developing a Pair smart contract 👾 Pair represents the Liquidity Pool 🪙 it is in charge of swapping 💱 managing the liquidity pool and burning 🔥
#womenwhocode #100DaysOfCode
Summary 🧵
#womenwhocode #100DaysOfCode
Summary 🧵

1/ In this example of the Pair smart contract I’ll implement the following methods:
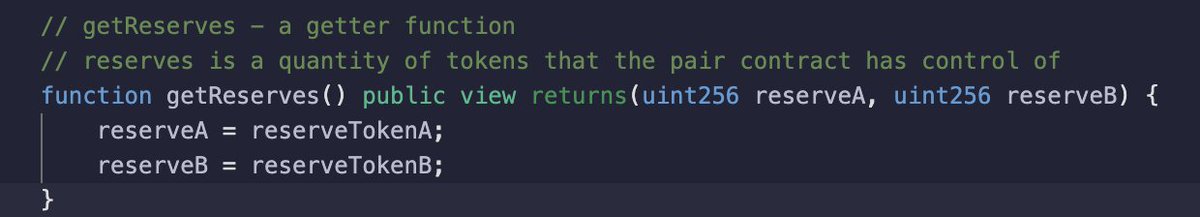
🔶 getReservers - get quantities of each token;
🔶 updateReserves - update the tokens’ quantities;
🔶 swap - exchange two tokens;
🔶 withdrawTokens - send the tokens back to the LP.
🔶 getReservers - get quantities of each token;
🔶 updateReserves - update the tokens’ quantities;
🔶 swap - exchange two tokens;
🔶 withdrawTokens - send the tokens back to the LP.
2/ First, initialize the Pair contract. We’ll need to import some contracts from OpenZeppelin and a Tokens contract from the day 66 of the challenge. Initialize state variables and constructor, too👩🏻💻 



4/ updateReserves → when the amount of tokens changes in the pool because of withdrawing, swapping or adding the tokens, we have to update the token's quantities 💰 
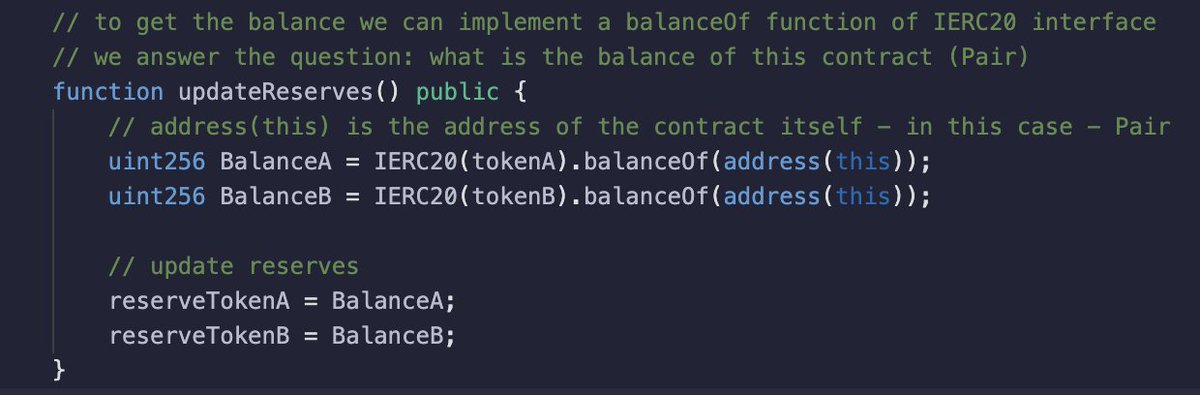
5/ swap function 👾 is the main functionality of the DEX 💱 as an input we have the amounts of tokens to swap and the address to transfer them. This address corresponds to the caller of the contract 🤖 Basically, swapping is transferring of the tokens 🪙 
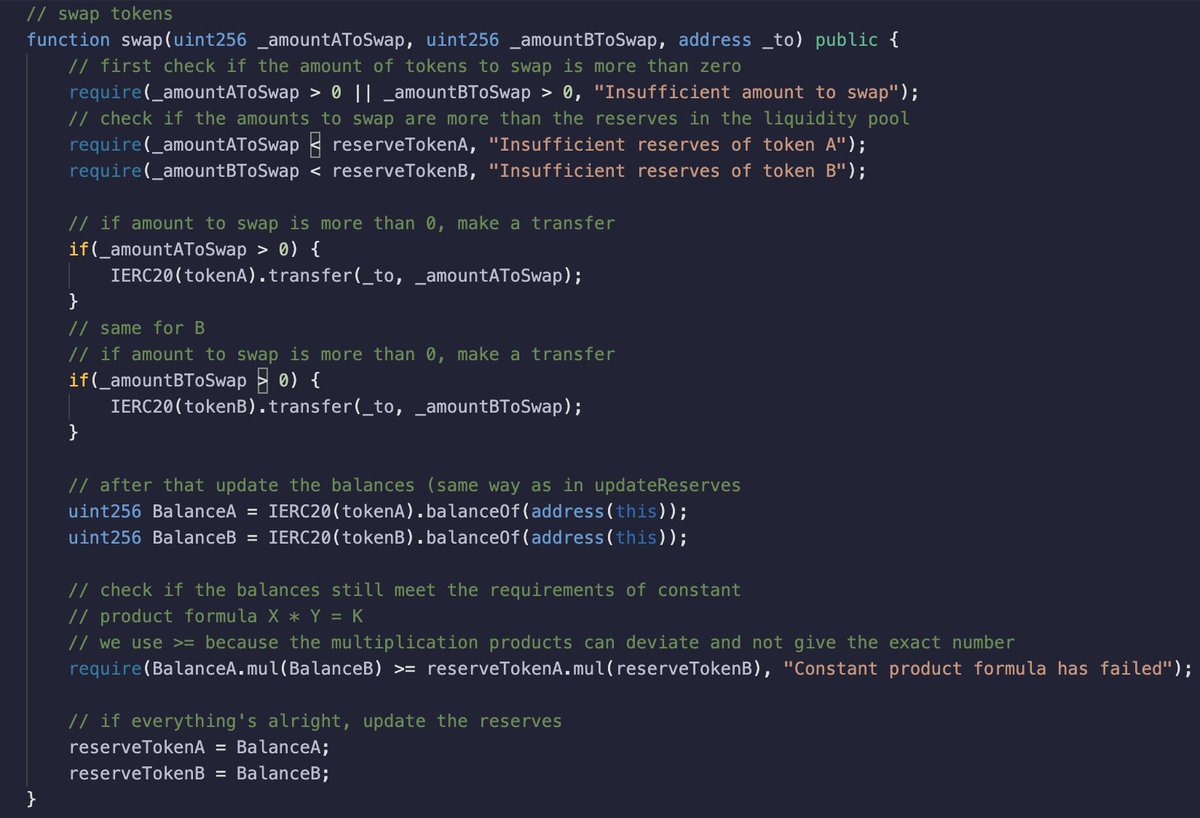
6/ withdrawTokens functions is executed when the caller wants to get their tokens back from the Liquidity Pool 💰 It is performed with the help of transferFrom function of ERC20 interface and is basically the transfer of tokens from the Pair’s to the caller’s addresses 🤖 

• • •
Missing some Tweet in this thread? You can try to
force a refresh