
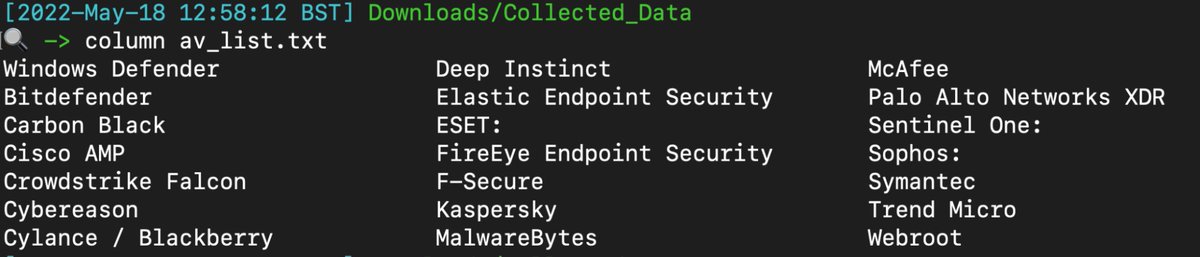
Inspired by a SANS poster, I wanted to look at a couple of security solutions and see if their logs provided any key insights an analyst could leverage.
sans.org/posters/window…
sans.org/posters/window…

The scenario : if given only product-relevant raw data & logs, would X security solution have data on the host that provides any security value and help with our investigation.
This is a specific use case I know. But it's something I find myself needing every day at work
This is a specific use case I know. But it's something I find myself needing every day at work
Our conversation is about a singular machine, and the transparency, ease-of-access, and security-value of the logs and raw data of various security solutions. We’ll be staying in Windows world for this particular thread.
In our scenario, we have no GUI access to the AV
In our scenario, we have no GUI access to the AV
We're not talking about the effectiveness of a solution.
We're only taking a look at one very specific thing about it: the security value of raw data it leaves in some kind of retrievable file
We're only taking a look at one very specific thing about it: the security value of raw data it leaves in some kind of retrievable file
Lots of gaps in the data collected, so please contribute and correct where necessary.
Not numbered in any particular order!
Okay let’s go!
Not numbered in any particular order!
Okay let’s go!
Windows Defender
Path : C:\windows\System32\winevt\Logs\Microsoft-Windows-Windows Defender%4Operational.evtx
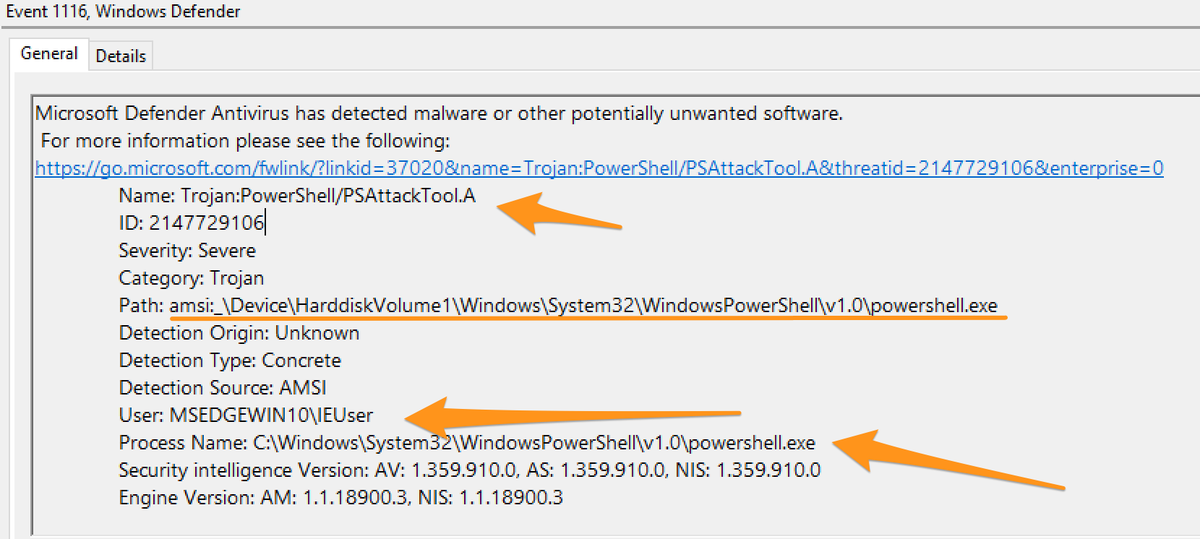
Defender is a good standard. It tells you the trigger time, offending file, the parent process, and snitches on the user account responsible.
Path : C:\windows\System32\winevt\Logs\Microsoft-Windows-Windows Defender%4Operational.evtx
Defender is a good standard. It tells you the trigger time, offending file, the parent process, and snitches on the user account responsible.
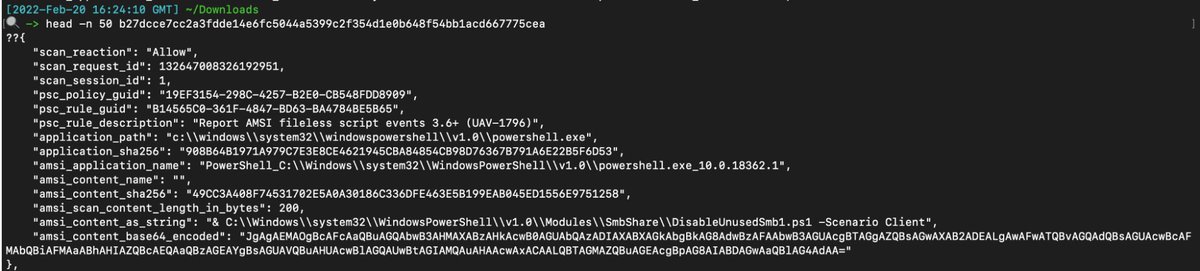
The categorisation near the top is hit and miss though. And good lord AMSI alerts are useless. TELL ME the PowerShell that was malicious?! Don’t make me go and pull the PwSh Op log?! 


Bitdefender:
Paths:
C:\ProgramData\Bitdefender\Endpoint Security\Logs\
C:\ProgramData\Bitdefender\Desktop\Profiles\Logs\
C:\Program Files*\Bitdefender\*\.db
C:\Program Files\Bitdefender\Endpoint Security\Logs\system\*\*.xml
Paths:
C:\ProgramData\Bitdefender\Endpoint Security\Logs\
C:\ProgramData\Bitdefender\Desktop\Profiles\Logs\
C:\Program Files*\Bitdefender\*\.db
C:\Program Files\Bitdefender\Endpoint Security\Logs\system\*\*.xml
C:\ProgramData\Bitdefender\Endpoint Security\Logs\Firewall\*.txt
Provides a good general context, good allrounder.

Provides a good general context, good allrounder.

Carbon Black
Paths:
C:\ProgramData\CarbonBlack\Logs\*.log
C:\ProgramData\CarbonBlack\Logs\AmsiEvents.log
Like this gives the PowerShell detail behind AMSI alert - which is REALLY useful for an investigation.

Paths:
C:\ProgramData\CarbonBlack\Logs\*.log
C:\ProgramData\CarbonBlack\Logs\AmsiEvents.log
Like this gives the PowerShell detail behind AMSI alert - which is REALLY useful for an investigation.

Cisco AMP
Path: C:\Program Files\Cisco\AMP\*.db
Wonderful to database to read with tonne of security value.
Some .ETL data also, but diagnostic only.
Path: C:\Program Files\Cisco\AMP\*.db
Wonderful to database to read with tonne of security value.
Some .ETL data also, but diagnostic only.
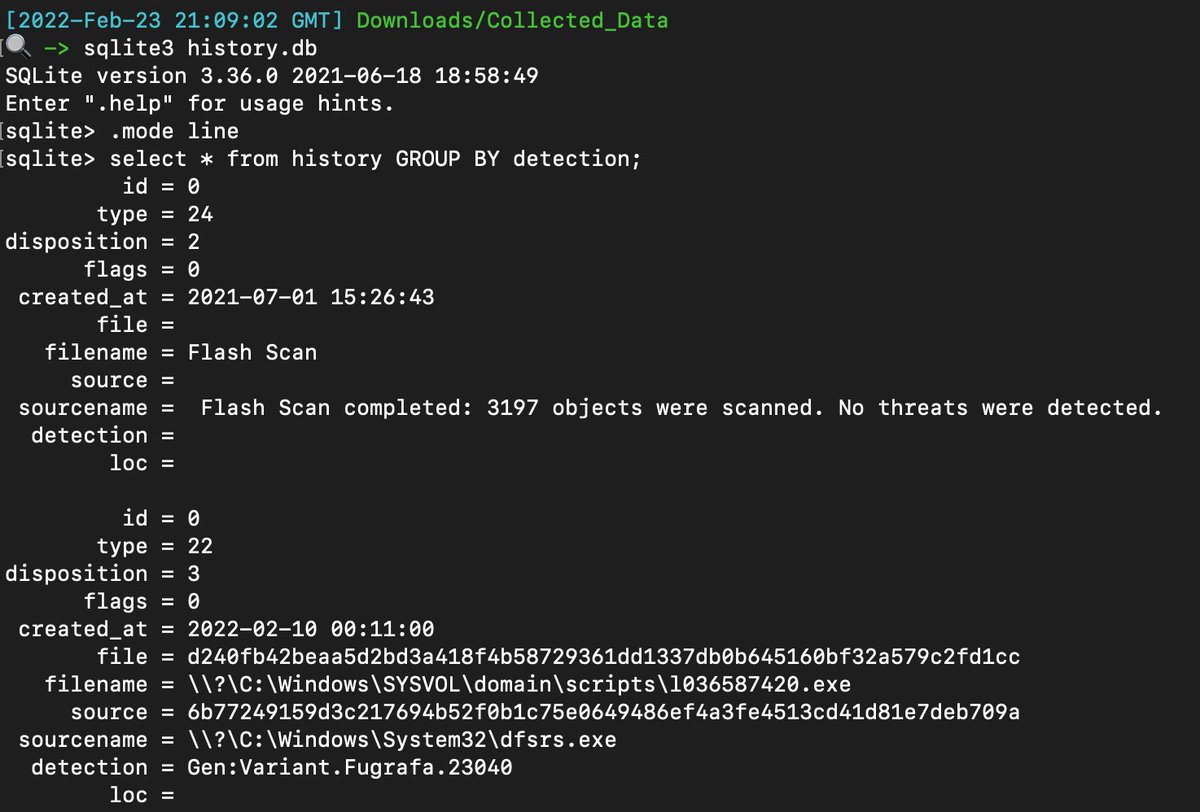
Crowdstrike Falcon
Path: C:\windows\System32\winevt\Logs\
Tried really hard but could only find diagnostic info. I’d be grateful for some pointers here.


Path: C:\windows\System32\winevt\Logs\
Tried really hard but could only find diagnostic info. I’d be grateful for some pointers here.


Cybereason
Paths:
C:\ProgramData\crs1\*.txt
C:\ProgramData\crs1\Logs
Tried really hard to find valuable , but could only find stuff pertaining to diagnostics.
Would be grateful if someone pointed out what I couldn’t find.
Paths:
C:\ProgramData\crs1\*.txt
C:\ProgramData\crs1\Logs
Tried really hard to find valuable , but could only find stuff pertaining to diagnostics.
Would be grateful if someone pointed out what I couldn’t find.
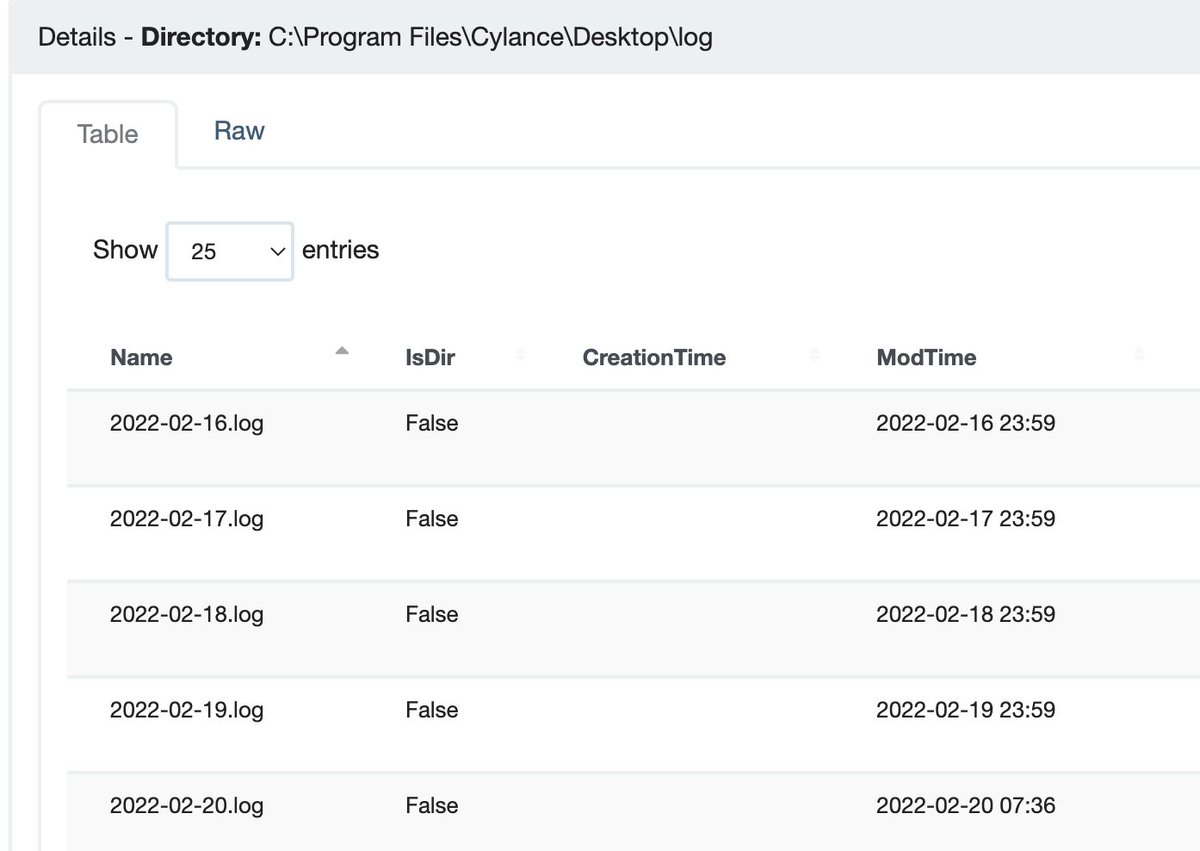
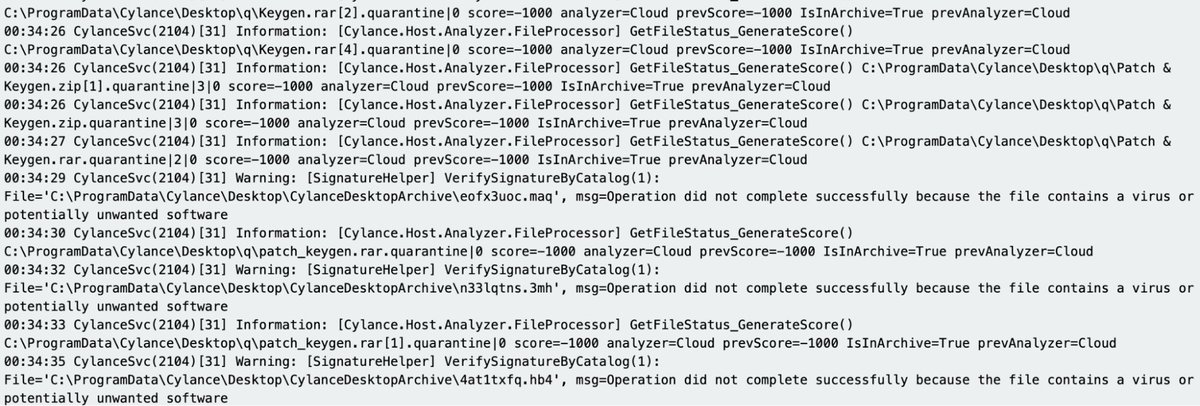
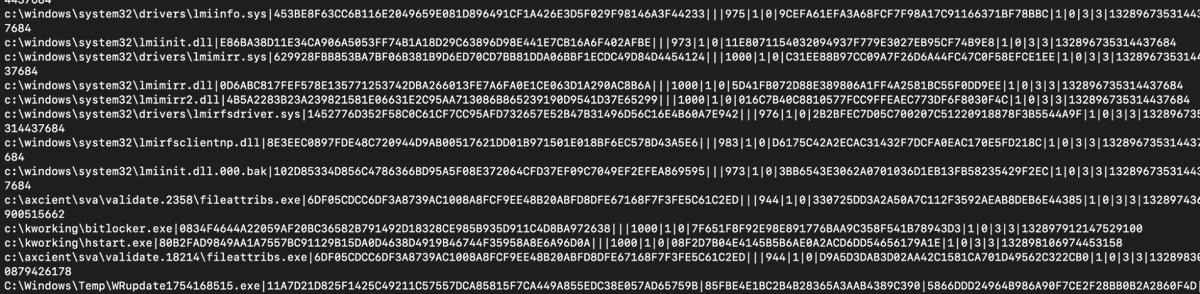
Cylance / Blackberry
Paths:
C:\ProgramData\Cylance\Desktop
C:\Program Files\Cylance\Desktop\log\* log
C:\ProgramData\Cylance\Desktop\chp.db
C:\ProgramData\Cylance\Optics\Log
You could do a thorough investigation from their data and get good insight into what happened.



Paths:
C:\ProgramData\Cylance\Desktop
C:\Program Files\Cylance\Desktop\log\* log
C:\ProgramData\Cylance\Desktop\chp.db
C:\ProgramData\Cylance\Optics\Log
You could do a thorough investigation from their data and get good insight into what happened.

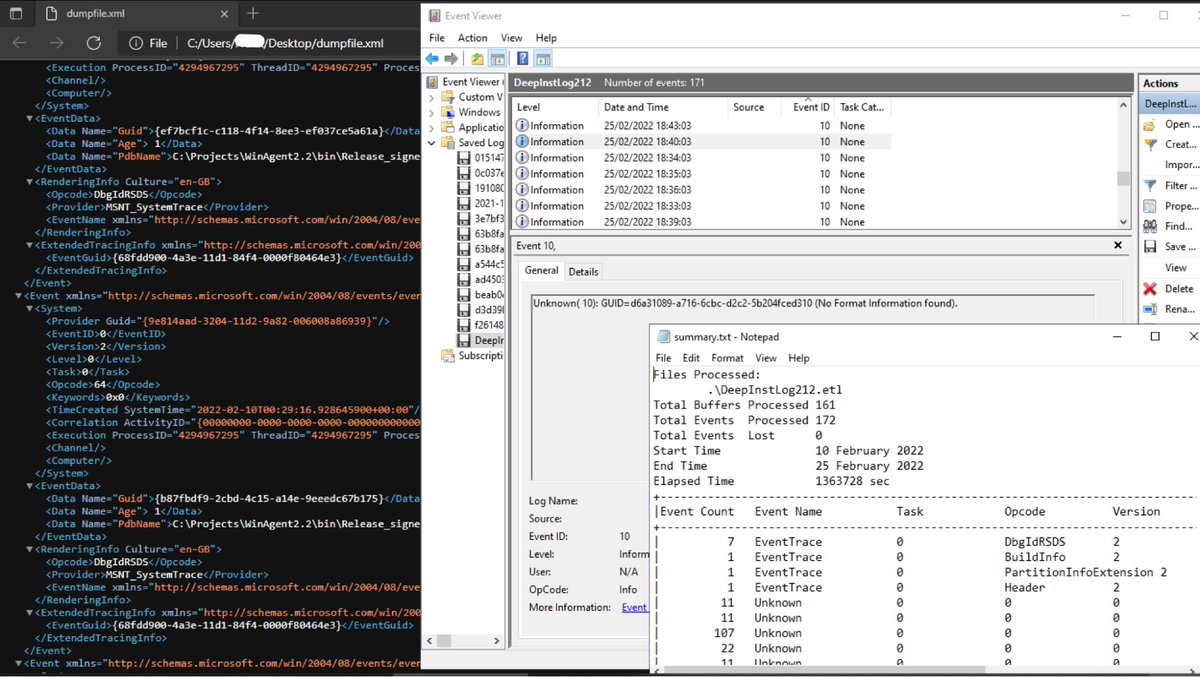
Deep Instinct
Path: C:\ProgramData\DeepInstinct\Logs\*.etl
Other than esoteric diagnostics, couldn't find anything of security value. I’d be grateful if anyone could contribute to improve on this.
Path: C:\ProgramData\DeepInstinct\Logs\*.etl
Other than esoteric diagnostics, couldn't find anything of security value. I’d be grateful if anyone could contribute to improve on this.
Elastic Endpoint Security
Path: C:\program files \elastic\endpoint\state\log
One big log, Includes great security insight.
Path: C:\program files \elastic\endpoint\state\log
One big log, Includes great security insight.

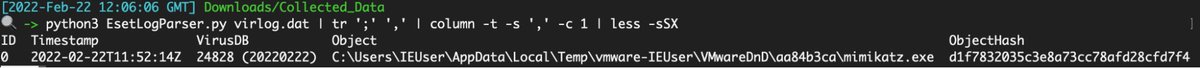
ESET:
Path: C:\ProgramData\ESET\ESET Security\Logs\virlog.dat
Requires a parser, but once you get the data it’s good detailed stuff
github.com/laciKE/EsetLog…
Path: C:\ProgramData\ESET\ESET Security\Logs\virlog.dat
Requires a parser, but once you get the data it’s good detailed stuff
github.com/laciKE/EsetLog…
FireEye Endpoint Security
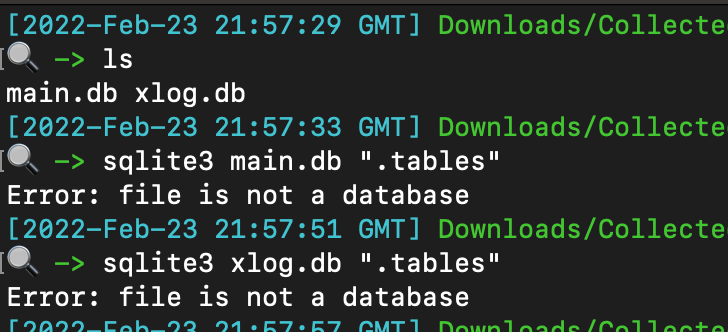
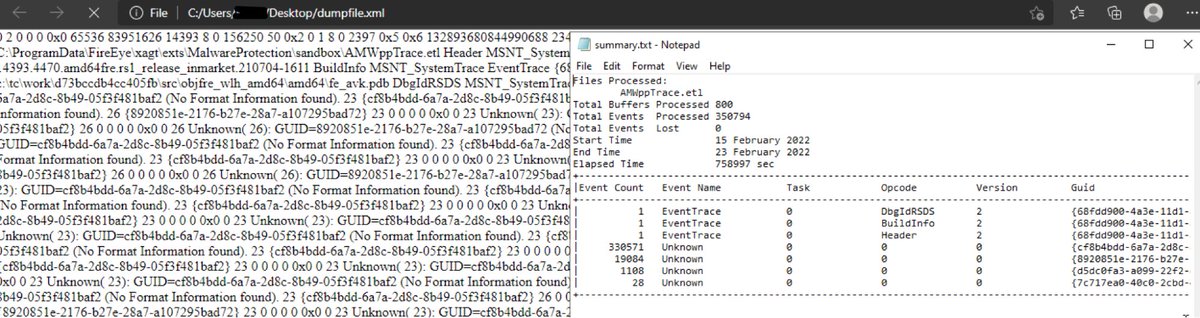
Path: C:\ProgramData\FireEye\xagt\*.db
Databases were encrypted. I didn’t want to root around and find an encryption key packed into a binary.
You can get logs via command ‘xagt -g example_log.txt’.
But this requires an interactive machine


Path: C:\ProgramData\FireEye\xagt\*.db
Databases were encrypted. I didn’t want to root around and find an encryption key packed into a binary.
You can get logs via command ‘xagt -g example_log.txt’.
But this requires an interactive machine

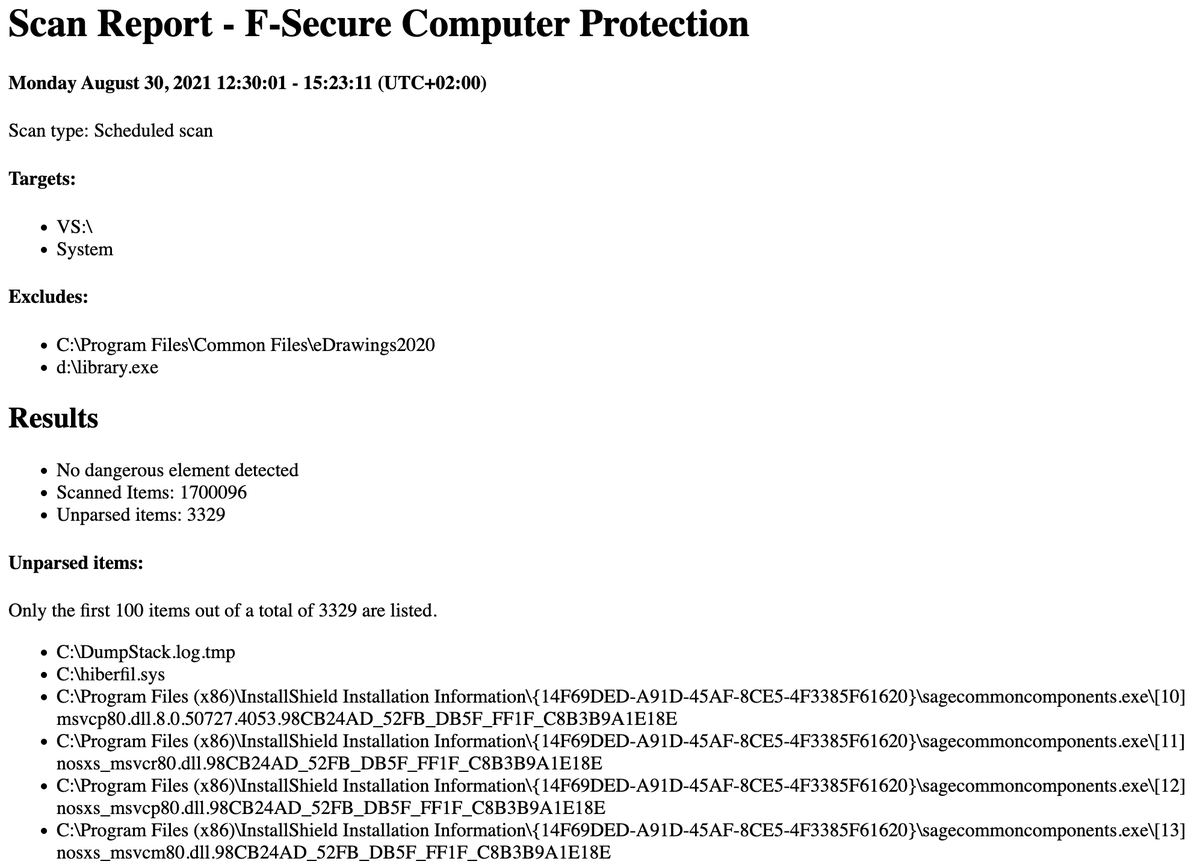
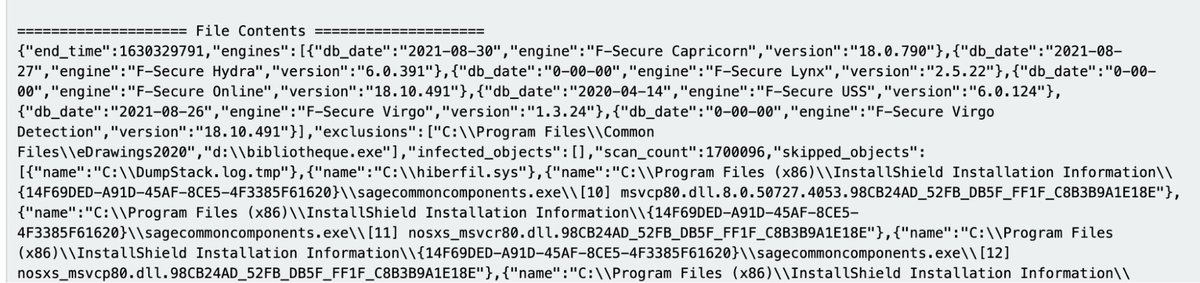
9. F-Secure
Paths:
C:\Users\*\AppData\Local\F-Secure\Log\*\*.log
C:\ProgramData\F-Secure\Antivirus\ScheduledScanReports\
C:\ProgramData\F-Secure\EventHistory\event
Straight forward to read, good security value, but a lot of diagnostic logs

Paths:
C:\Users\*\AppData\Local\F-Secure\Log\*\*.log
C:\ProgramData\F-Secure\Antivirus\ScheduledScanReports\
C:\ProgramData\F-Secure\EventHistory\event
Straight forward to read, good security value, but a lot of diagnostic logs
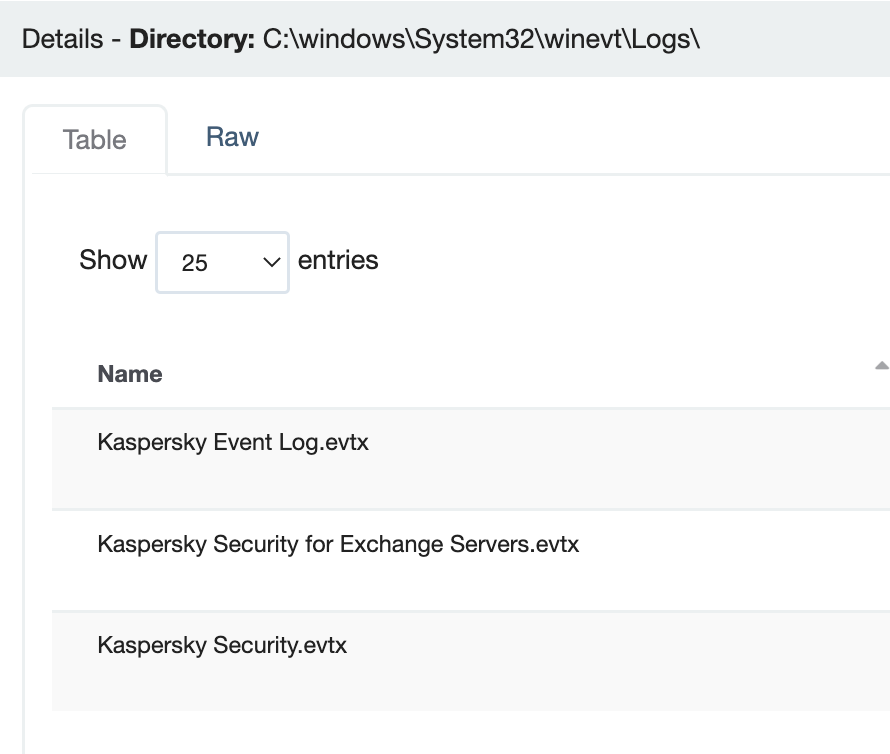
Kaspersky
Path: C:\Windows\system32\winevt\logs
The EVTX has great security value, similar to Defender’s format.

Path: C:\Windows\system32\winevt\logs
The EVTX has great security value, similar to Defender’s format.

MalwareBytes
Path
C:\ProgramData\Malwarebytes\Malwarebytes Anti-Malware\Logs\mbam-log-*.xml
C:\ProgramData\Malwarebytes\MBAMService\logs\mbamservice.log
C:\Users\*\AppData\Roaming\Malwarebytes\Malwarebytes Anti-Malware\Logs\
C:\ProgramData\Malwarebytes\MBAMService\ScanResults\
Path
C:\ProgramData\Malwarebytes\Malwarebytes Anti-Malware\Logs\mbam-log-*.xml
C:\ProgramData\Malwarebytes\MBAMService\logs\mbamservice.log
C:\Users\*\AppData\Roaming\Malwarebytes\Malwarebytes Anti-Malware\Logs\
C:\ProgramData\Malwarebytes\MBAMService\ScanResults\
More than enough data to work with. But you do have to bounce between multiple log sources to piece information together 




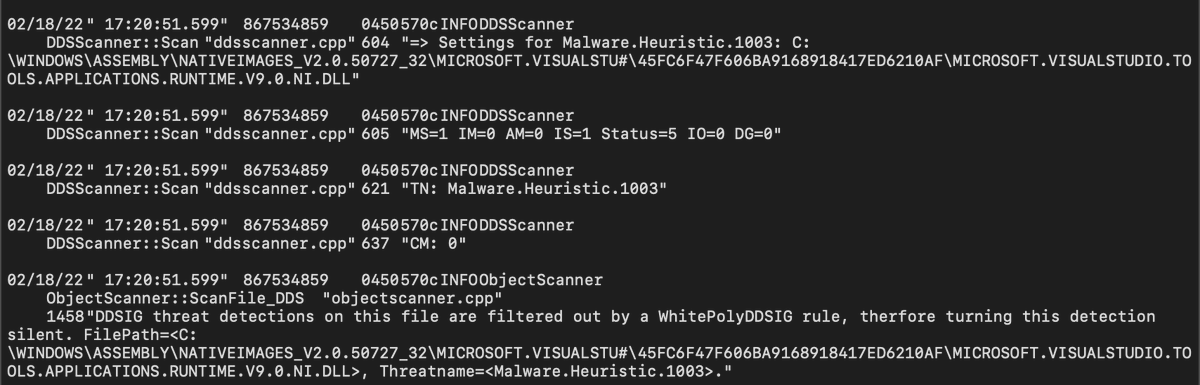
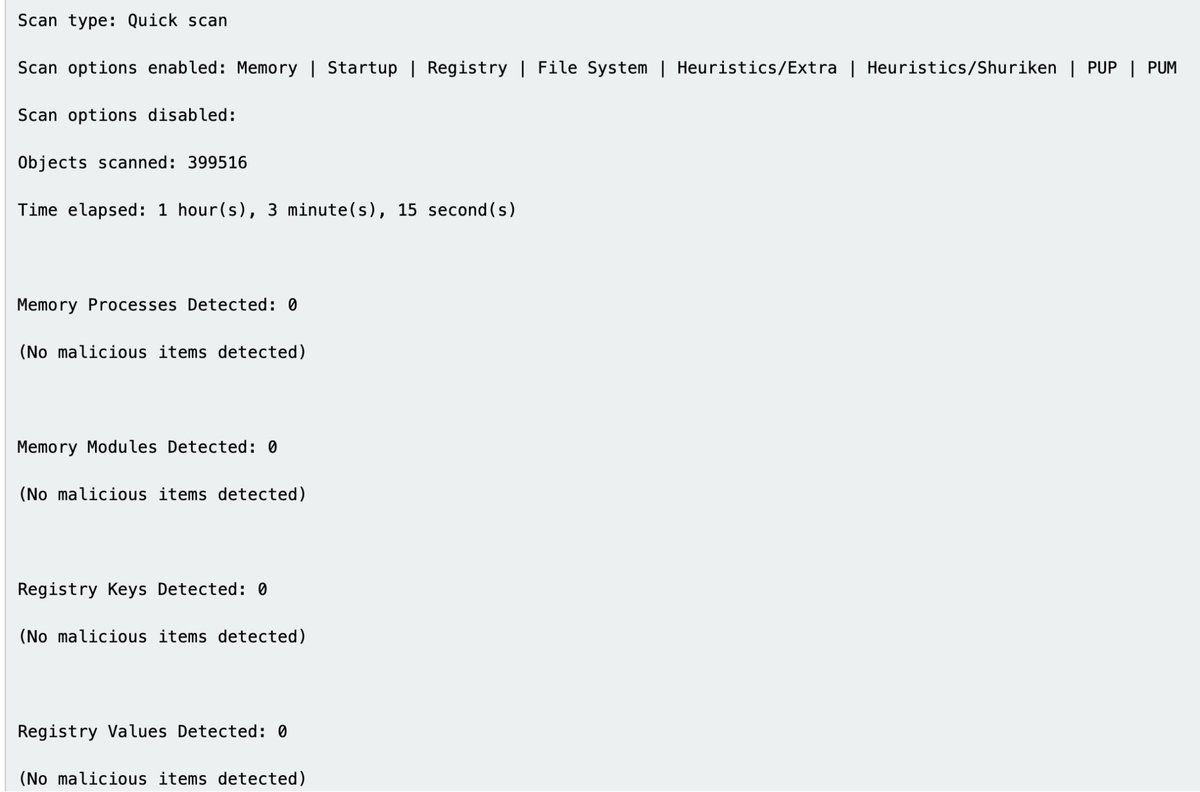
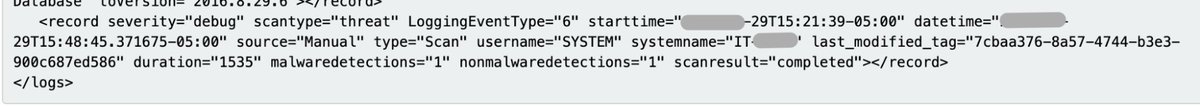
McAfee
Paths:
C:\ProgramData\McAfee\Endpoint Security\Logs\*.log
C:\ProgramData\McAfee\Endpoint Security\Logs_Old\*
C:\ProgramData\Mcafee\VirusScan\*
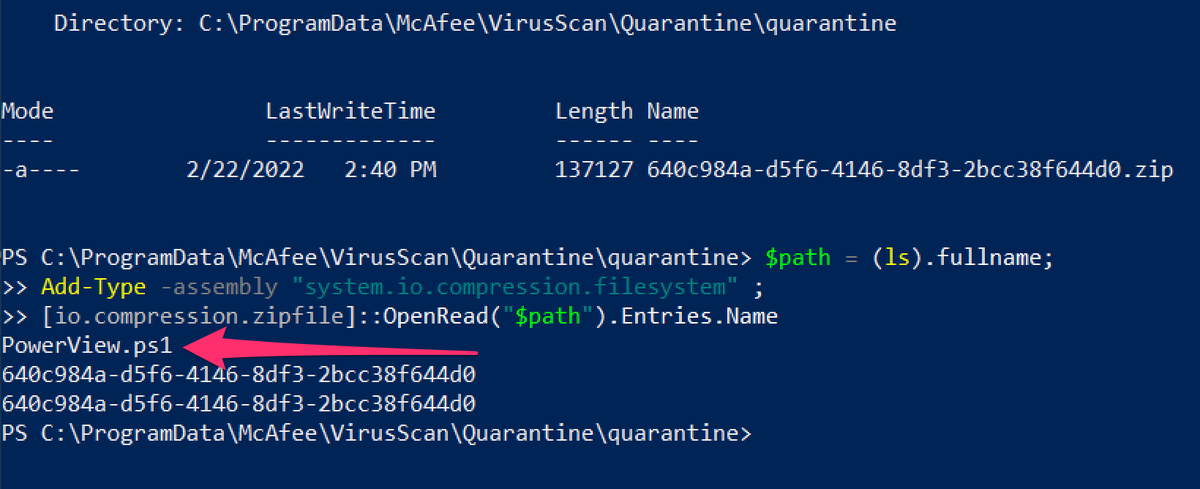
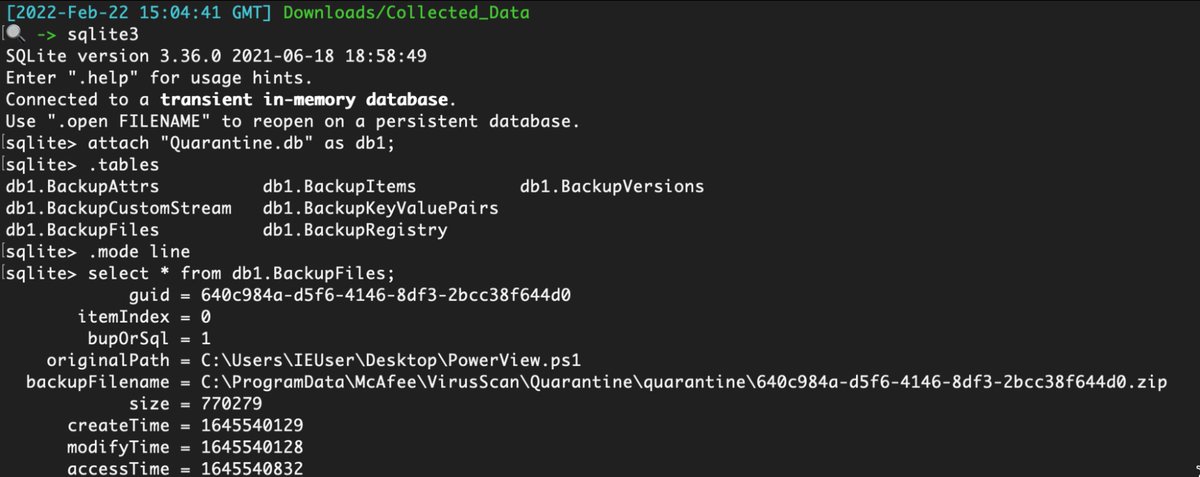
C:\ProgramData\McAfee\VirusScan\Quarantine\quarantine\*.db
C:\ProgramData\McAfee\DesktopProtection\*.txt
Paths:
C:\ProgramData\McAfee\Endpoint Security\Logs\*.log
C:\ProgramData\McAfee\Endpoint Security\Logs_Old\*
C:\ProgramData\Mcafee\VirusScan\*
C:\ProgramData\McAfee\VirusScan\Quarantine\quarantine\*.db
C:\ProgramData\McAfee\DesktopProtection\*.txt
Great data. A bit inconsistent across products, but I forgive due to the transparency and security value in the logs 





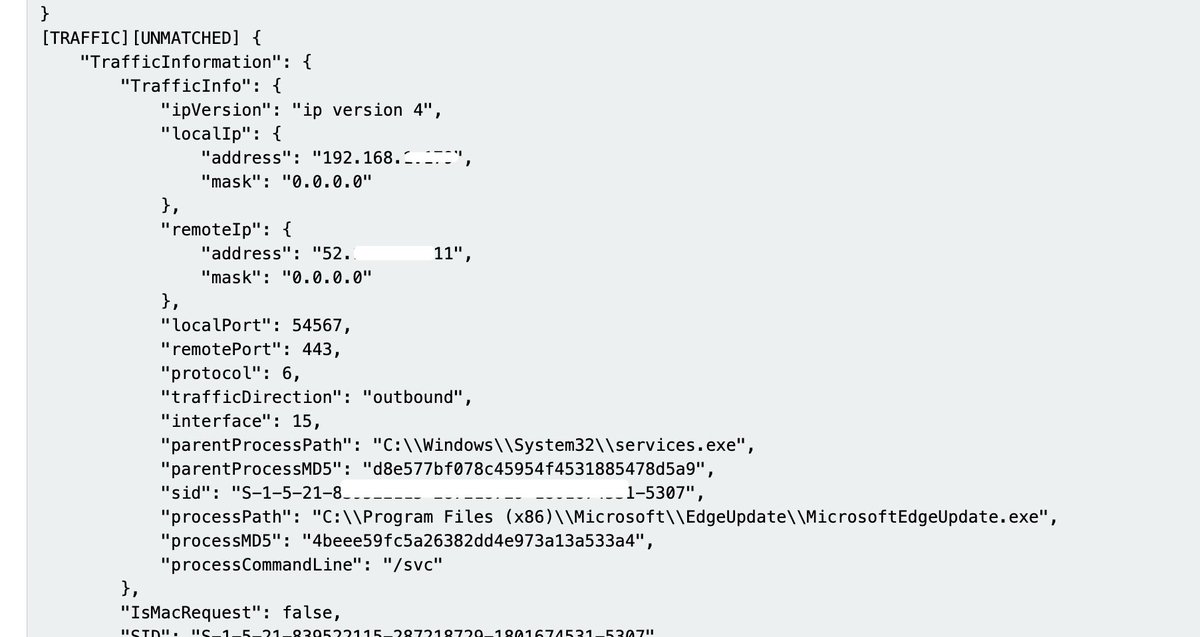
Palo Alto Networks XDR
Path: C:\ProgramData\Cyvera\Logs\*.log
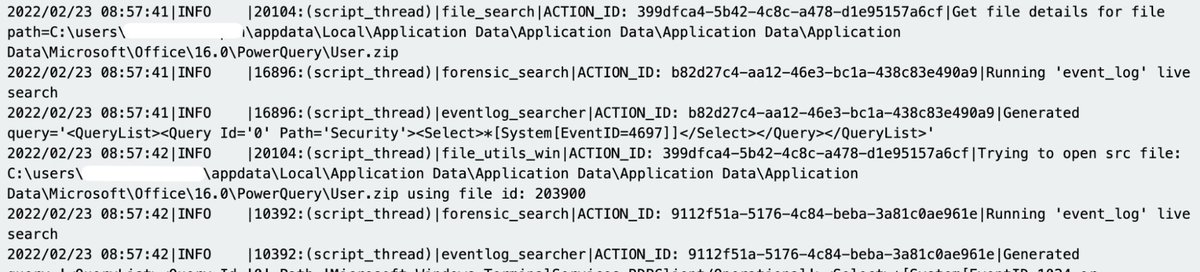
Great security value in the various logs, and easy to read
Path: C:\ProgramData\Cyvera\Logs\*.log
Great security value in the various logs, and easy to read
Sentinel One:
Paths:
C:\programdata\sentinel\logs\*.log, *.txt
C:\windows\System32\winevt\Logs\SentinelOne*.evtx
C:\ProgramData\Sentinel\Quarantine
Sometimes some security data in EVTXs!
Tried hard to parse the .BINLOG files but couldn't. Hope someone can educate me here


Paths:
C:\programdata\sentinel\logs\*.log, *.txt
C:\windows\System32\winevt\Logs\SentinelOne*.evtx
C:\ProgramData\Sentinel\Quarantine
Sometimes some security data in EVTXs!
Tried hard to parse the .BINLOG files but couldn't. Hope someone can educate me here


Sophos:
Paths:
C:\ProgramData\Sophos\Sophos Anti-Virus\logs\*.txt.
C:\ProgramData\Sophos\Endpoint Defense\Logs\*.txt
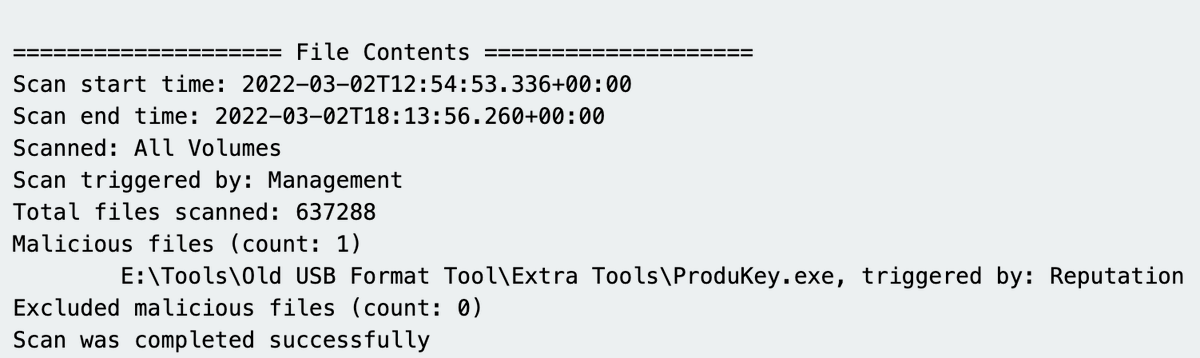
Great logs, verbose granular, full of security value.
Can be parsed by chainsaw from application evtx


Paths:
C:\ProgramData\Sophos\Sophos Anti-Virus\logs\*.txt.
C:\ProgramData\Sophos\Endpoint Defense\Logs\*.txt
Great logs, verbose granular, full of security value.
Can be parsed by chainsaw from application evtx


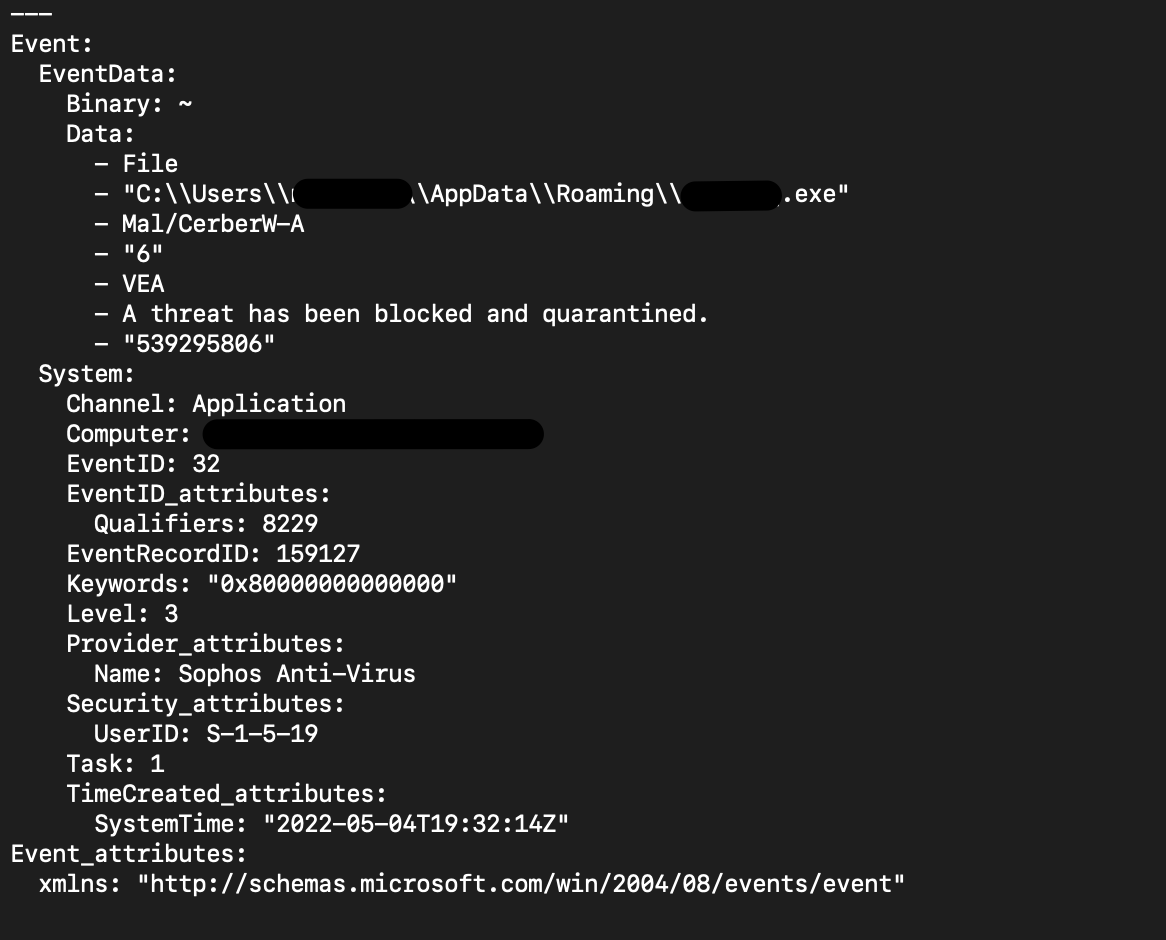
Symantec
Paths:
C:\ProgramData\Symantec\Symantec Endpoint Protection\*\Data\Logs\
C:\Users\*\AppData\Local\Symantec\Symantec Endpoint Protection\Logs\
C:\Windows\System32\winevt\logs\Symantec Endpoint Protection Client.evtx
Paths:
C:\ProgramData\Symantec\Symantec Endpoint Protection\*\Data\Logs\
C:\Users\*\AppData\Local\Symantec\Symantec Endpoint Protection\Logs\
C:\Windows\System32\winevt\logs\Symantec Endpoint Protection Client.evtx
C:\ ProgramData\Symantec\Symantec Endpoint Protection\*\Data\Quarantine\
All the logs are good, with a mixture of diagnostic and security value



All the logs are good, with a mixture of diagnostic and security value
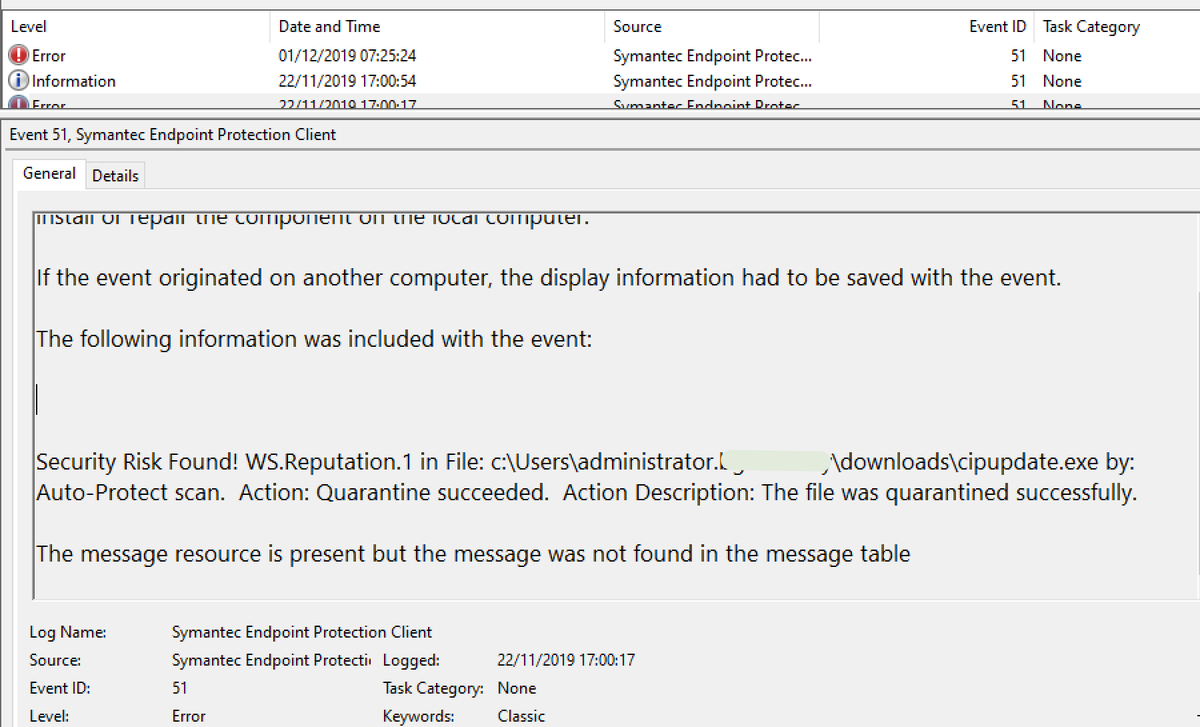
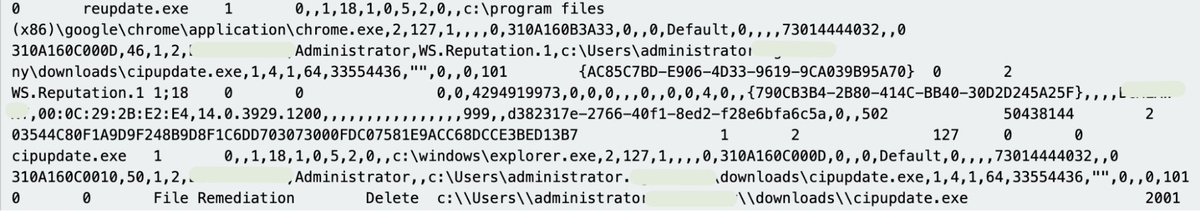
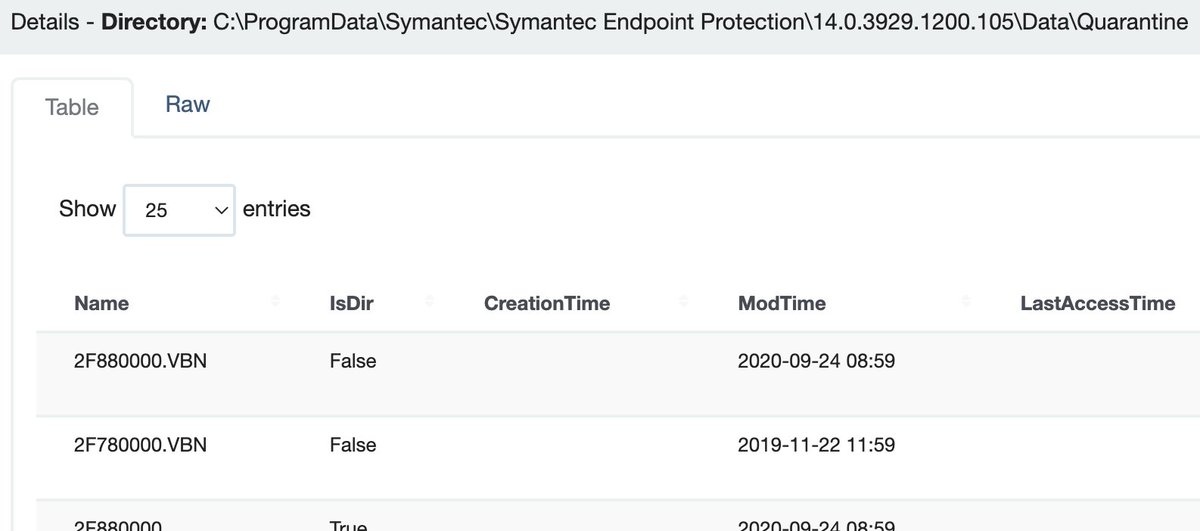
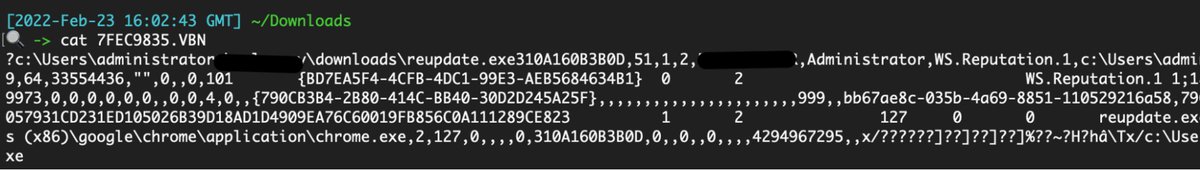
Trend Micro
Paths:
C:\ProgramData\Trend Micro\
C:\Program Files (x86)\Trend Micro\Client Server Security Agent\
C:\Program Files*\Trend Micro\Security Agent\Report\*.log,
C:\Program Files*\Trend Micro\Security Agent\ConnLog\*.log
Transparent, well laid out, good security value

Paths:
C:\ProgramData\Trend Micro\
C:\Program Files (x86)\Trend Micro\Client Server Security Agent\
C:\Program Files*\Trend Micro\Security Agent\Report\*.log,
C:\Program Files*\Trend Micro\Security Agent\ConnLog\*.log
Transparent, well laid out, good security value


Webroot
Path: C:\ProgramData\WRData\WRLog.log
Good security value and straight to read. There were some DBs but they were encrypted from the looks of it.

Path: C:\ProgramData\WRData\WRLog.log
Good security value and straight to read. There were some DBs but they were encrypted from the looks of it.
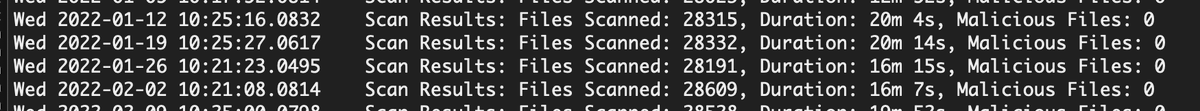
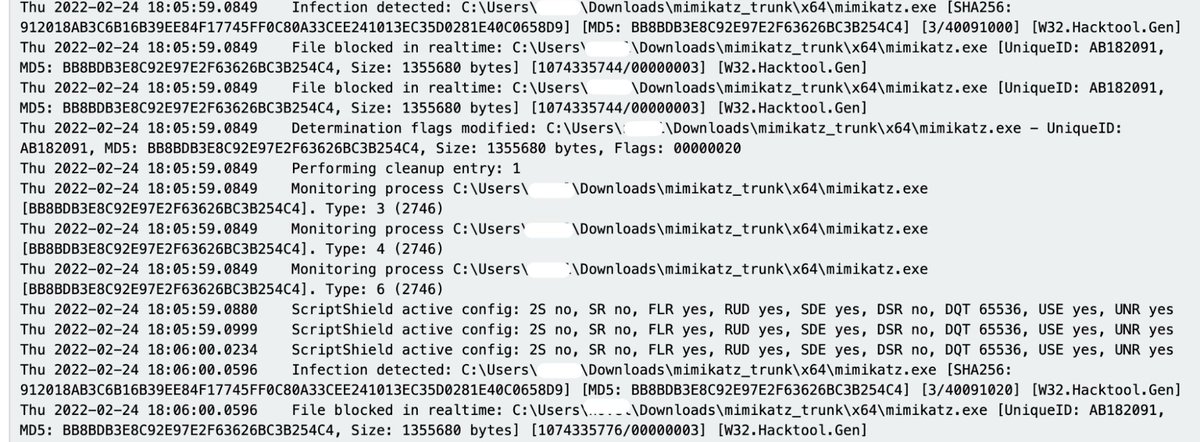
By the way
You may encounter quarantined malware in some of these above directories.
Try this script to undo the quarantine process that defangs the malware, and turn it into something executable and analysable
hexacorn.com/d/DeXRAY.pl


You may encounter quarantined malware in some of these above directories.
Try this script to undo the quarantine process that defangs the malware, and turn it into something executable and analysable
hexacorn.com/d/DeXRAY.pl


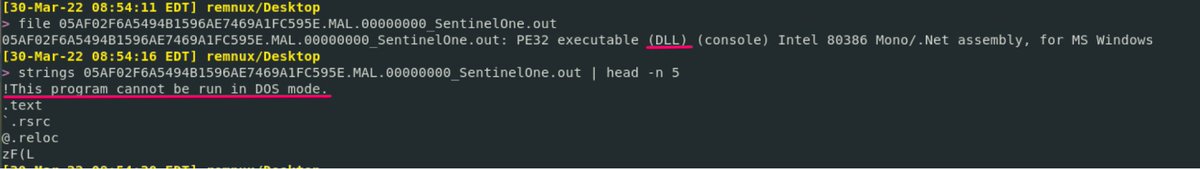
That's all I've got for you!
You can follow my blue team notes for more defensive security tips : github.com/Purp1eW0lf/Blu…
There’s so much more to contribute and correct for this thread, I look forward to how this conversation develops.
You can follow my blue team notes for more defensive security tips : github.com/Purp1eW0lf/Blu…
There’s so much more to contribute and correct for this thread, I look forward to how this conversation develops.
• • •
Missing some Tweet in this thread? You can try to
force a refresh













