
Hunt & Response Senior Manager @HuntressLabs || "Competition is the law of the jungle, but cooperation is the law of civilisation” - Kropotkin
How to get URL link on X (Twitter) App

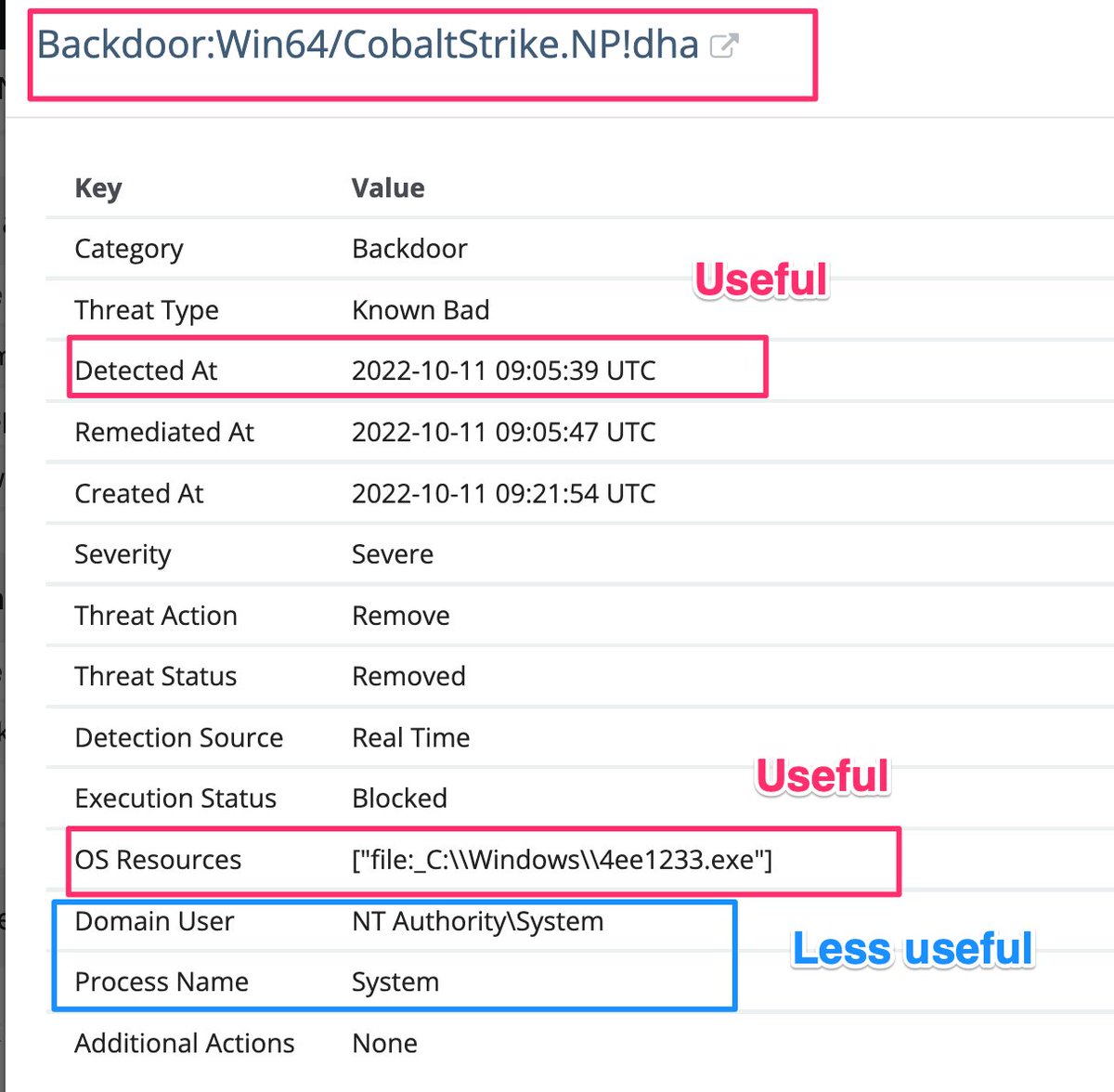

 This gave us a tonne of starter info
This gave us a tonne of starter info
 I kept finding LogonType 3s (network)
I kept finding LogonType 3s (network)

https://twitter.com/huntresslabs/status/1559779051480530944
 Our article couldn’t show what this cleartext credential gathering looked like on the compromised machine, but we recreated the electrifying end product
Our article couldn’t show what this cleartext credential gathering looked like on the compromised machine, but we recreated the electrifying end product 



 The scenario : if given only product-relevant raw data & logs, would X security solution have data on the host that provides any security value and help with our investigation.
The scenario : if given only product-relevant raw data & logs, would X security solution have data on the host that provides any security value and help with our investigation.

 When drafting some internal docs the other morning, I wanted a screenshot of an Elastic search.
When drafting some internal docs the other morning, I wanted a screenshot of an Elastic search.




https://twitter.com/WhyDee86/status/1492911256612880390Let's start off by compiling it.


https://twitter.com/x86matthew/status/1489624392627859458Let's execute the PoC of the .LNK, which brings a pop up.

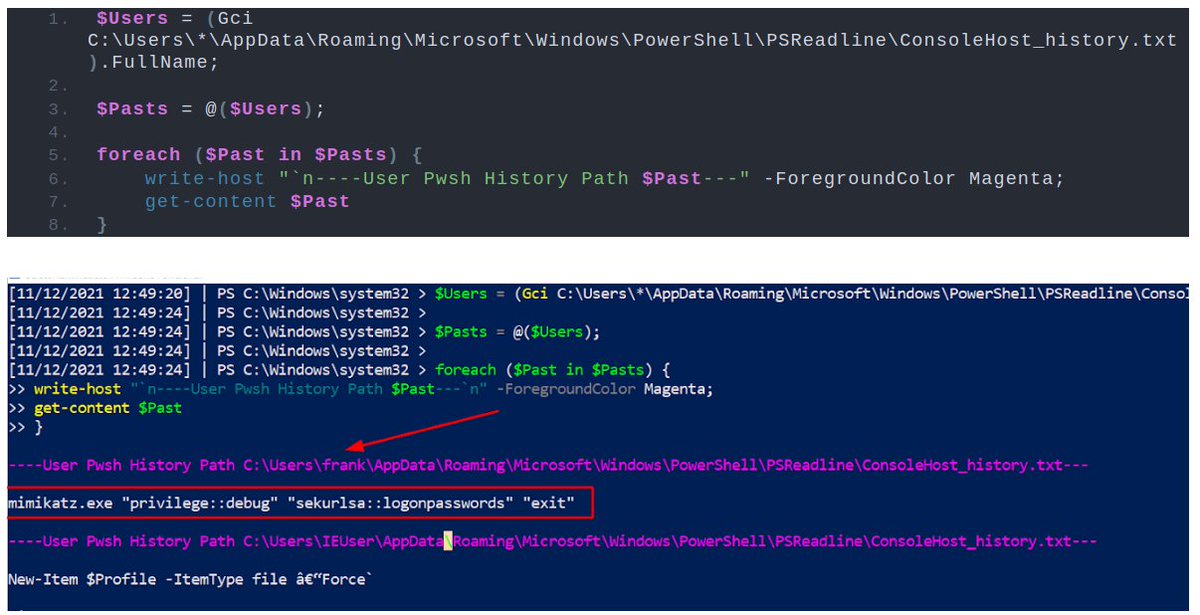
https://twitter.com/JumpsecLabs/status/1462705713935958021The first technique in the article discusses how to retrieve the PowerShell history for every user account via the 'ConsoleHost_History file' (typically enabled on Windows 10 endpoints)
