
Righto. Lets talk about this data and how to use it. To start, I'm uploading a zip file of all samples as well to allow downloading in bulk. I'll also share out some more parts of this as we go. So, off we go...
🧵(1/14)
🧵(1/14)
https://twitter.com/silascutler/status/1529322242017992706
For background, #CobaltStrike is an "adversary simulation tool" (pentesting tools vs malware sometimes are only philosophically different #FightMe). It is widely used for legitimate security testing, pre-ransomware operations and other malicious threat actors.
🧵(2/14)
🧵(2/14)
The files provide are called Beacon. It's the malware deployed and controlled by CobaltStrike. While the two names are commonly misused interchangeably (even by myself). @Mandiant did a solid write-up on names. mandiant.com/resources/defi…
🧵(3/14)
🧵(3/14)
Now that's out of the way, lets get technical. When executed, each of these /should/ try and connect out to a corresponding control server. A nice aspect of Beacon is configuration settings (including control server addresses) can be extracted without sandboxing...
🧵(4/14)
🧵(4/14)
@LabsSentinel / @SentinelOne created a fantastic tool for this. It's written in Python and really easy to use. Run it against one of the samples and you should get an output similar to below.
github.com/Sentinel-One/C…
🧵(5/14)
github.com/Sentinel-One/C…
🧵(5/14)
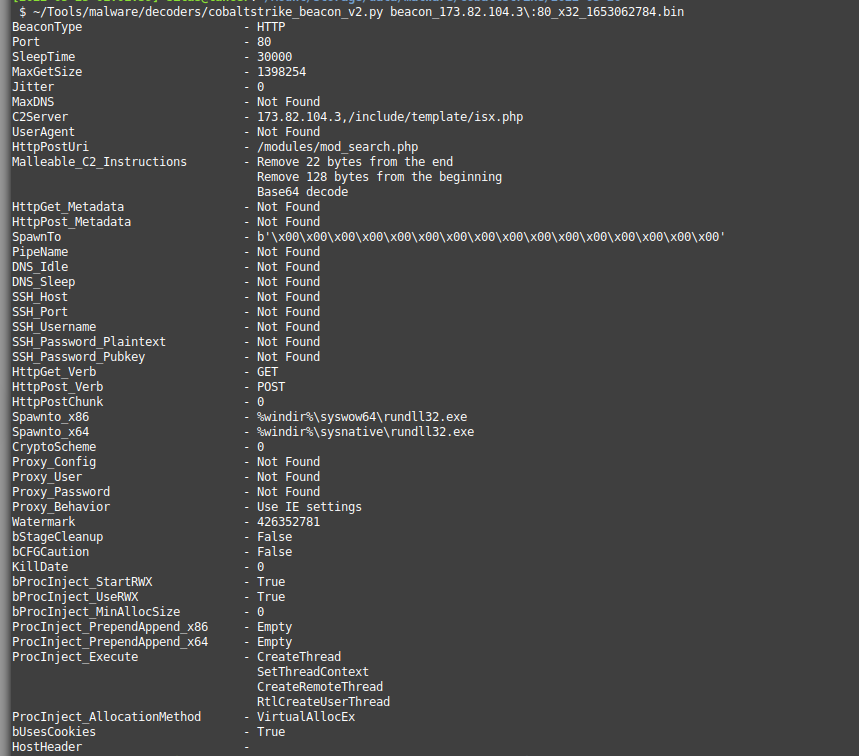
Configuration details are stored using a nifty setup. The buffer containing the settings is encoded using a single byte XOR cipher. You can brute force it out or use blog.didierstevens.com/programs/xorse….
Each setting (BeaconType, Port, etc.) are each preceded by a 6-byte string .
🧵(6/14)
Each setting (BeaconType, Port, etc.) are each preceded by a 6-byte string .
🧵(6/14)

Fun trick - you can write Yara rules to track unique settings by creating a string comprised of sentinel + value with an xor modifier to catch cool stuff. #100DaysOfYara
🧵(7/14)
🧵(7/14)
So, lets skip all that. As I'm typing this out, I'll start a mass-decode, compress it and upload it with the collection.
🧵(8/14)
🧵(8/14)
Right, enough background, but before we move on, I'm a researcher, If I misrepresent the difficulty of applying something to a detection system, please let me know. I'm still learning / growing too ♥️. Anyways, moving right along...
🧵(9/14)
🧵(9/14)
For defenders, fire up the cat, grep and sed out the control servers and get those into your network detection systems. Some of these servers will have rolled over and are no longer malicious, so a 1-2 year expiration is likely fair. Watch out for CDNs + Legit domains.
🧵(10/14)
🧵(10/14)
Hashes should be added to block-lists, though based on how they were collected, this may not be super reliable. #I_Tried.
🧵(11/14)
🧵(11/14)
If you can hunt across your environment - named pipes, User-Agents and other unique technical artifacts may help identify infections originating from samples outside of this collection. @cobaltstrikebot does an outstanding job of highlighting some of the most/least...
🧵(12/14)
🧵(12/14)
common of these values.
They're also bad-ass. Keep on being awesome @cobaltstrikebot
🧵(13/14)
https://twitter.com/cobaltstrikebot/status/1529188317291421696
They're also bad-ass. Keep on being awesome @cobaltstrikebot
🧵(13/14)
Zip of all the samples just finished uploading and can be downloaded from bit.ly/3sW8JaR. No registering needed. Battery's about to die on my laptop, so I'll end this thread and post up when the decoded data is available.
#BeExcellentToEachOther
#HackThePlanet
🧵(14/14)
#BeExcellentToEachOther
#HackThePlanet
🧵(14/14)
• • •
Missing some Tweet in this thread? You can try to
force a refresh



