
You may know me from your logs
Research @Censysio
Advisor #DEVSEC
#Hacking #Cyber #CTI
How to get URL link on X (Twitter) App


https://twitter.com/clintgibler/status/1779955150138097994
 Login page after registration. 3.6/10. Not great, not terrible.
Login page after registration. 3.6/10. Not great, not terrible. 

https://twitter.com/silascutler/status/1773793808578154545
 The main channels for updates that I've been following are:
The main channels for updates that I've been following are:
https://twitter.com/BleepinComputer/status/1744838018974785746Based on the SFJ's description, sender information was recovered from a recipient device. Sender details were stored in a hash form, which SFJ cracked using rainbow tables of phone numbers and email addresses.




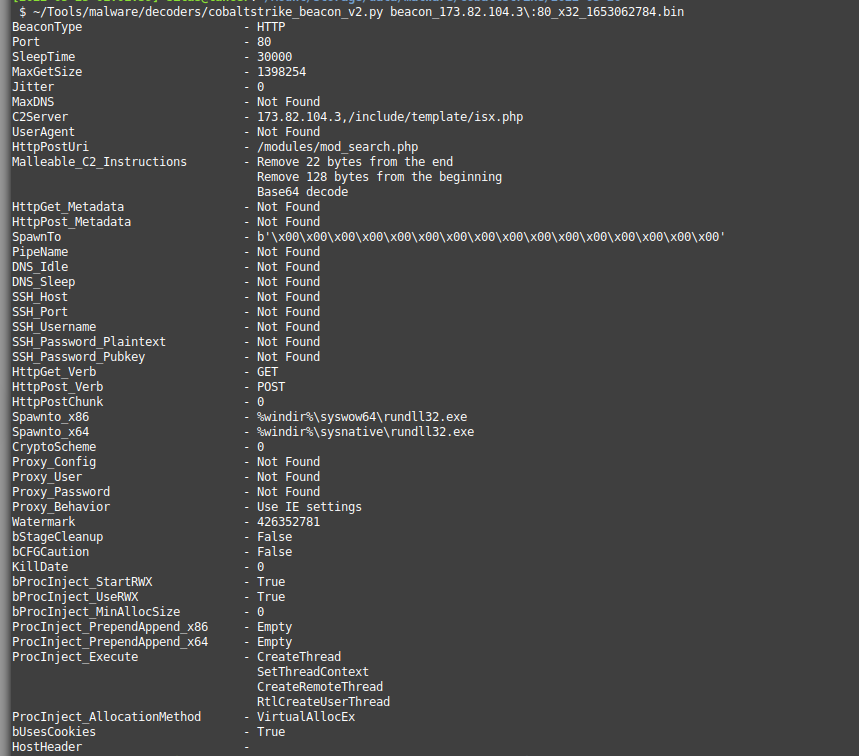
https://twitter.com/silascutler/status/1529322242017992706For background, #CobaltStrike is an "adversary simulation tool" (pentesting tools vs malware sometimes are only philosophically different #FightMe). It is widely used for legitimate security testing, pre-ransomware operations and other malicious threat actors.