Day 75 of #100DaysOfDeFI 🚀 today 3/4 of the challenge is done! 🎉 Also today I finish exploring Solidity vulnerabilities with learning about Denial of service (DoS) attacks 🦹🏼♀️
#womenwhocode #100DaysOfCode
How it works 🧵
#womenwhocode #100DaysOfCode
How it works 🧵

1/ There are many ways to attack a smart contract and at some point create a DoS⚡
2/ Denial of Service attack paralyzes a smart contract and makes it temporarily unusable 🛑
3/ Let’s see an example of a simple game EtherKing that can be broken by a DoS. A goal of the game is to send more Ether to the contract than the previous king; then the former king gets their funds back 💸 

4/ Now define the Attack smart contract 🦹🏽♀️ The contract doesn’t have a fallback function, so any attempt to send the Ether back will fail 💸 

5/ Let’s try it out! Deploy KingOfEther then set value to 1 Ether and click “claimThrone” 👑 We can see that the king is the account address we used to claim the throne 👇 



7/ Set the value to 2 Ether and claim the throne again! Now the balance is 2 Ether king is the Attack 👺 
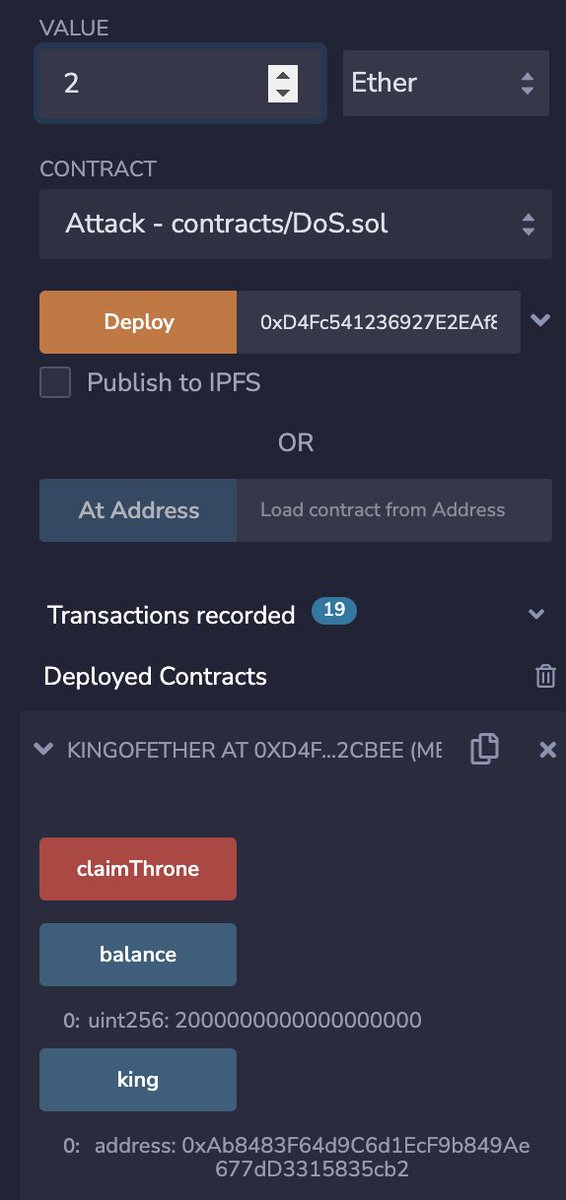
8/ Finally try to beat the Attack and get the crown back. Change the account again and set value to more than 2 Ether. Click claim the throne function and we’ll get an error 👇 

• • •
Missing some Tweet in this thread? You can try to
force a refresh

















