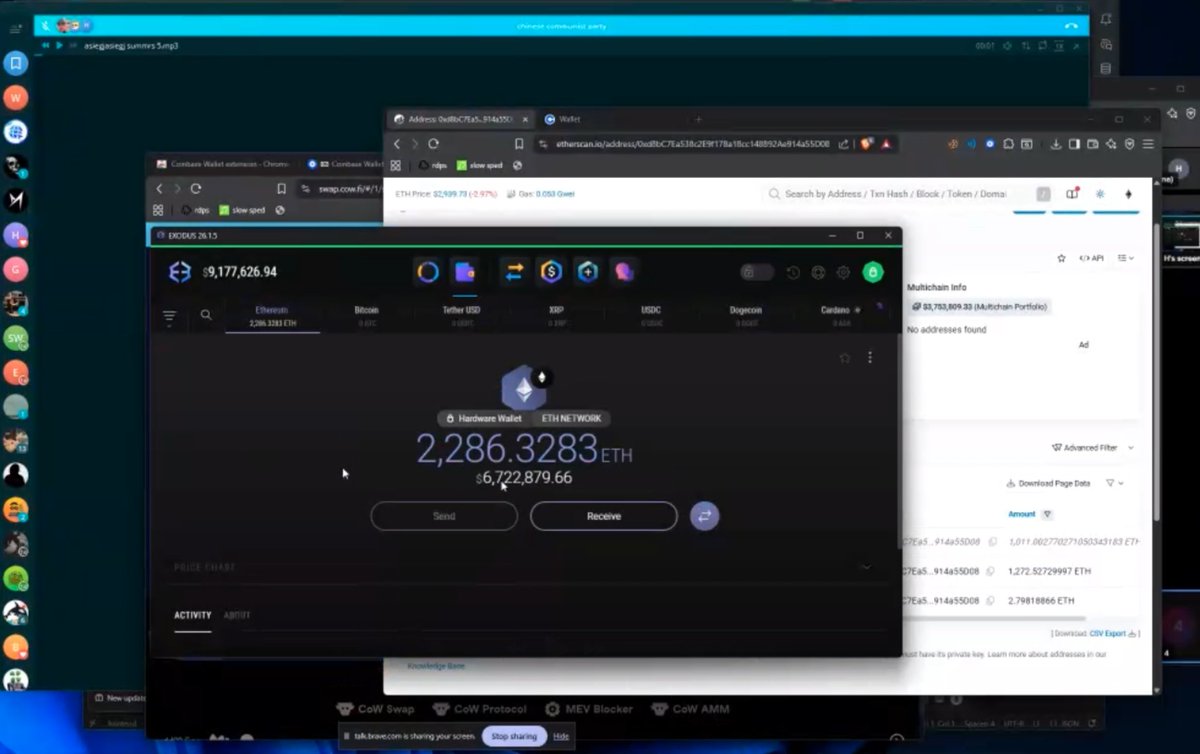
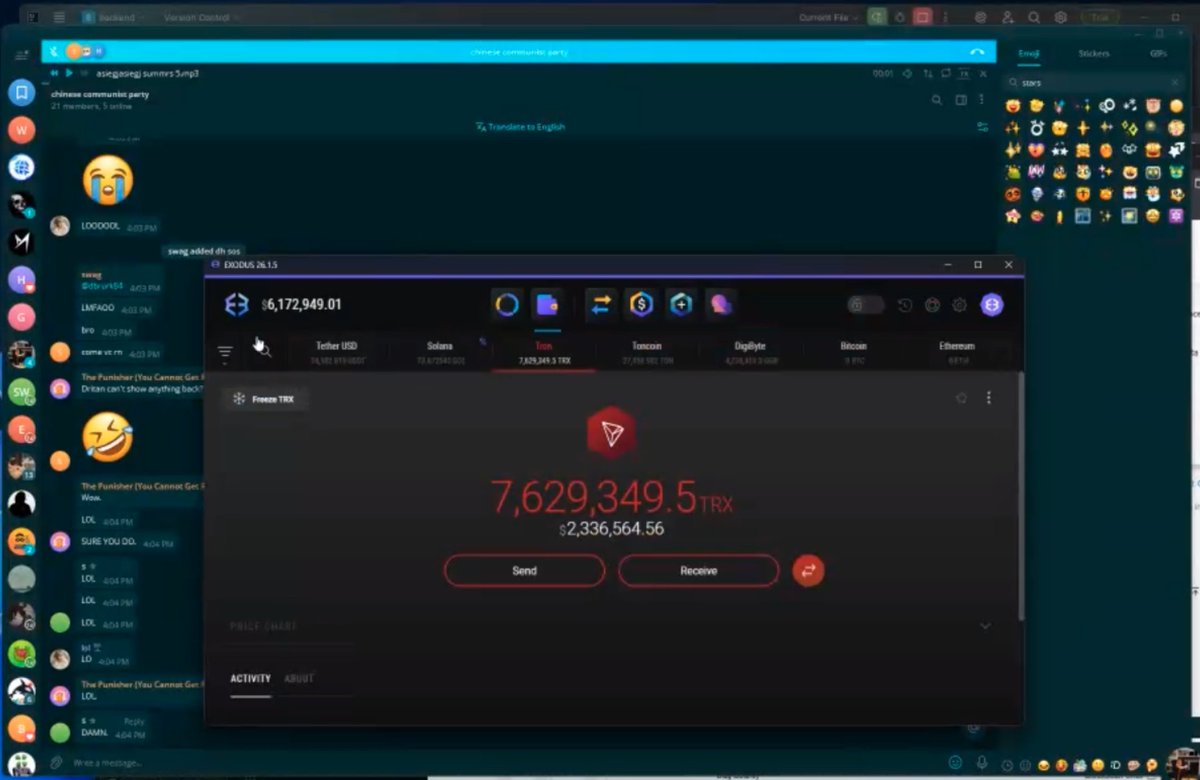
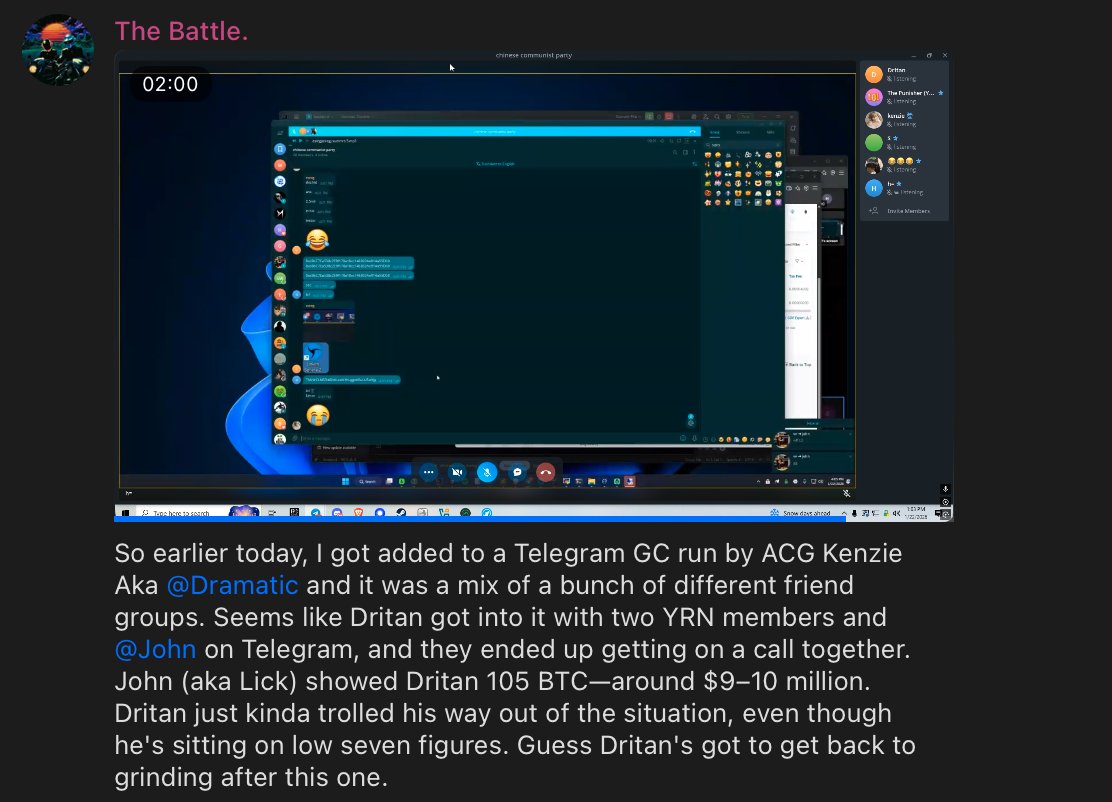
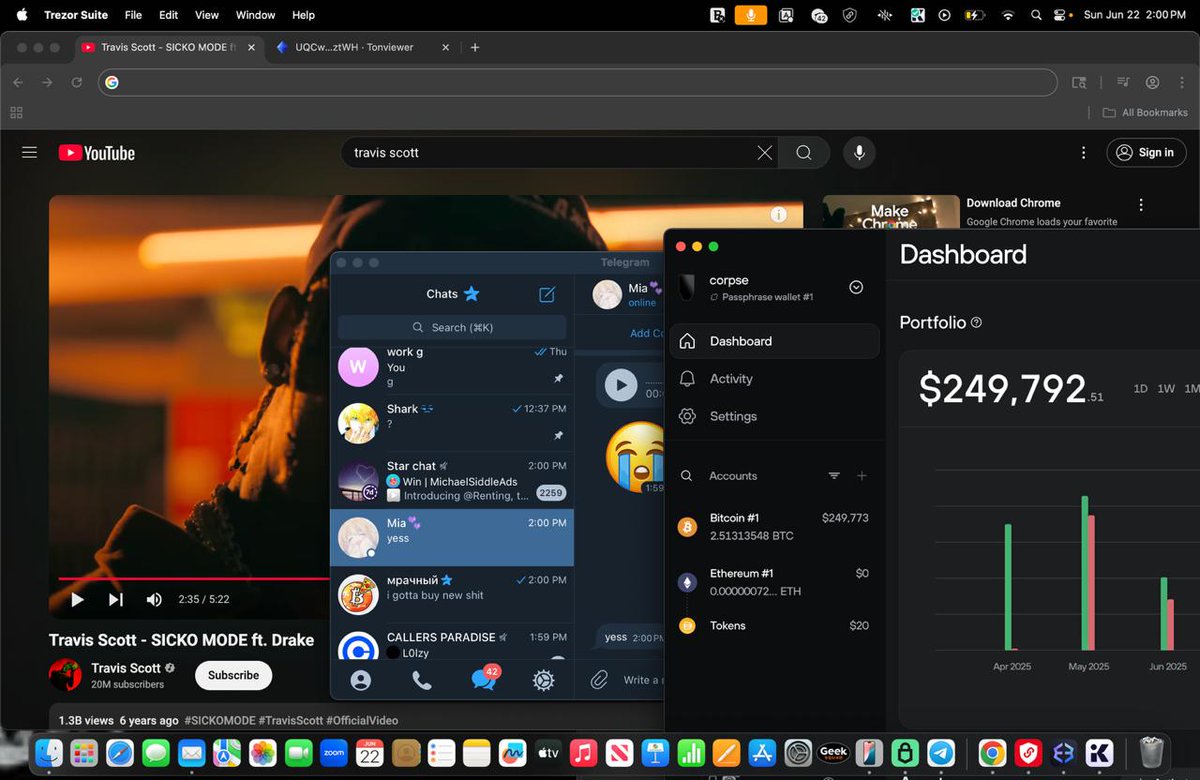
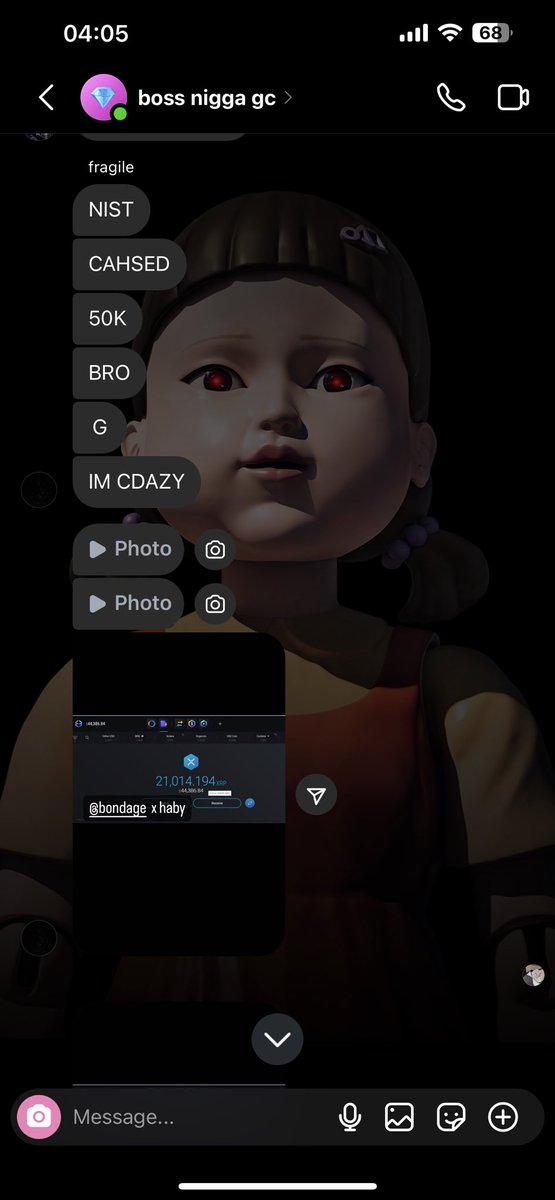
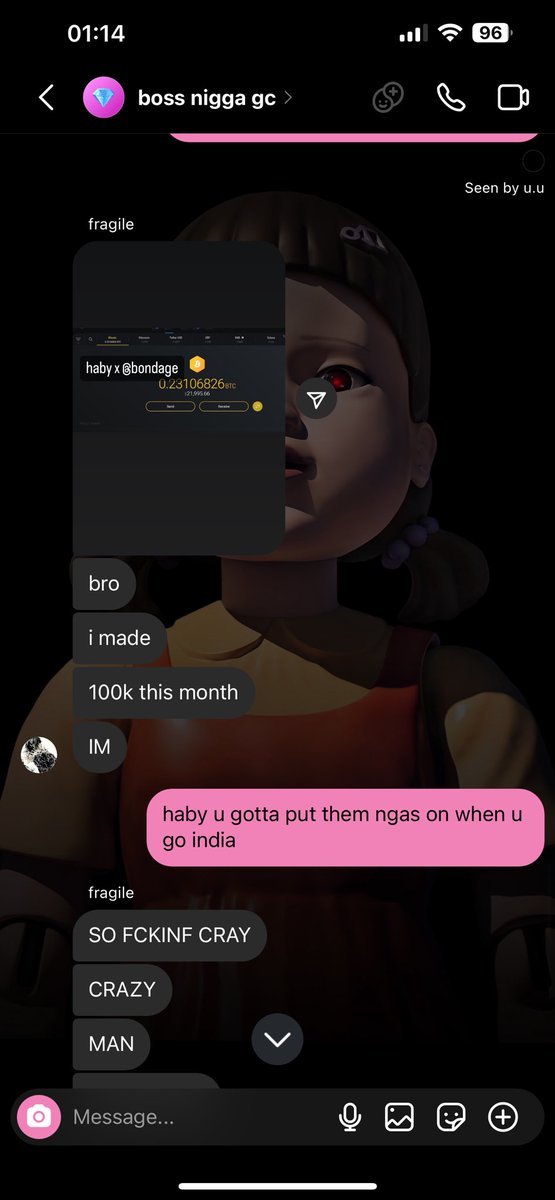
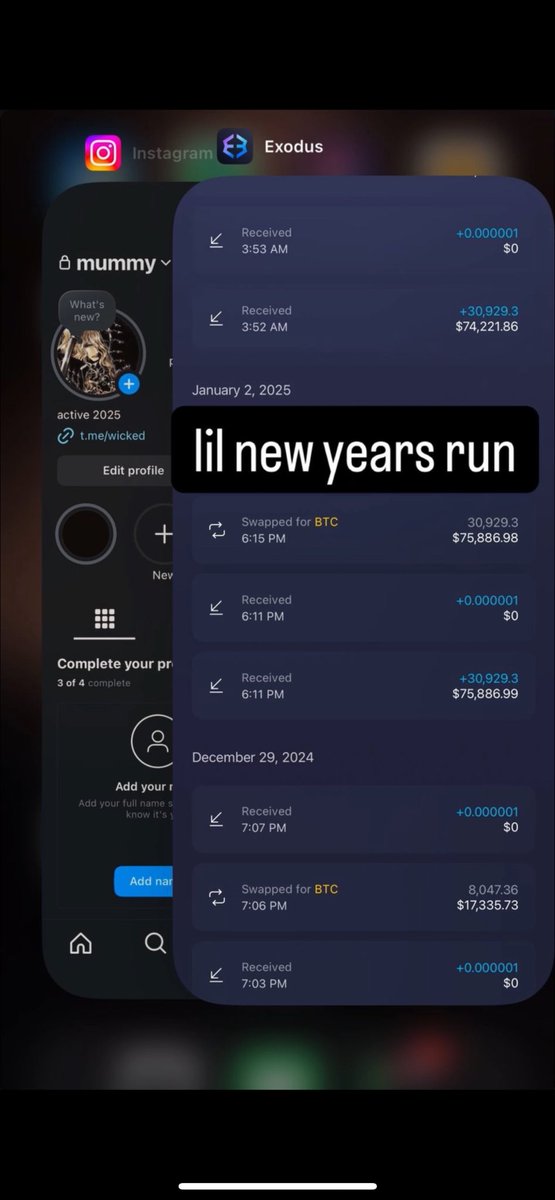
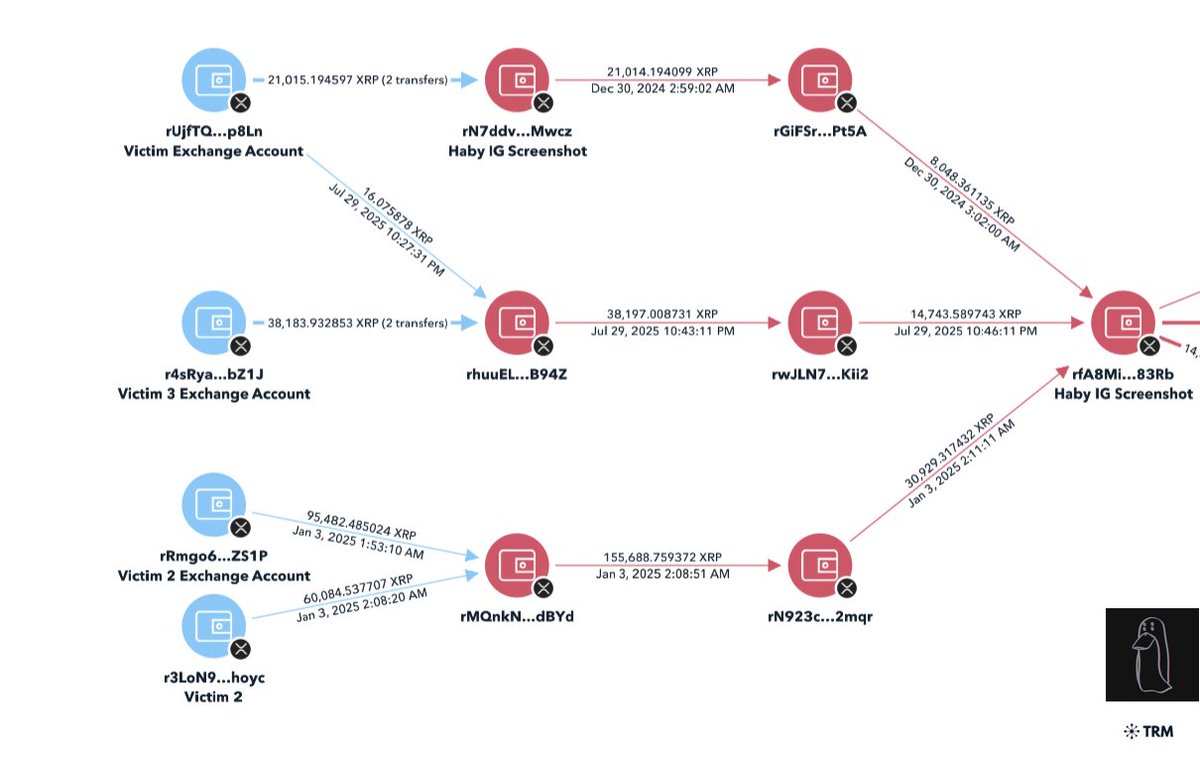
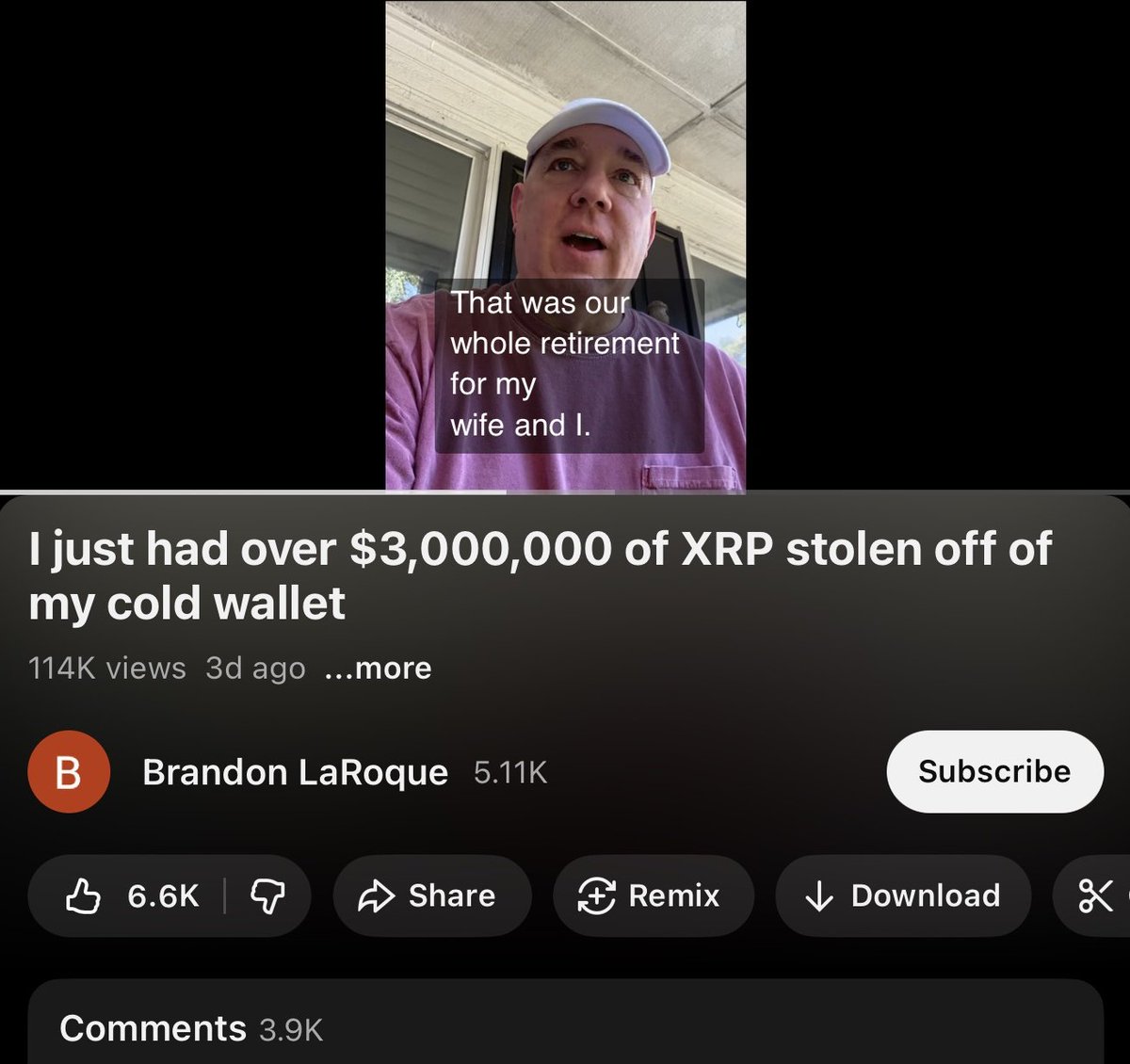
1/ Let’s breakdown the $6.3m NFT rug Animoon, a project that has constantly screwed over its holders since day 1. 

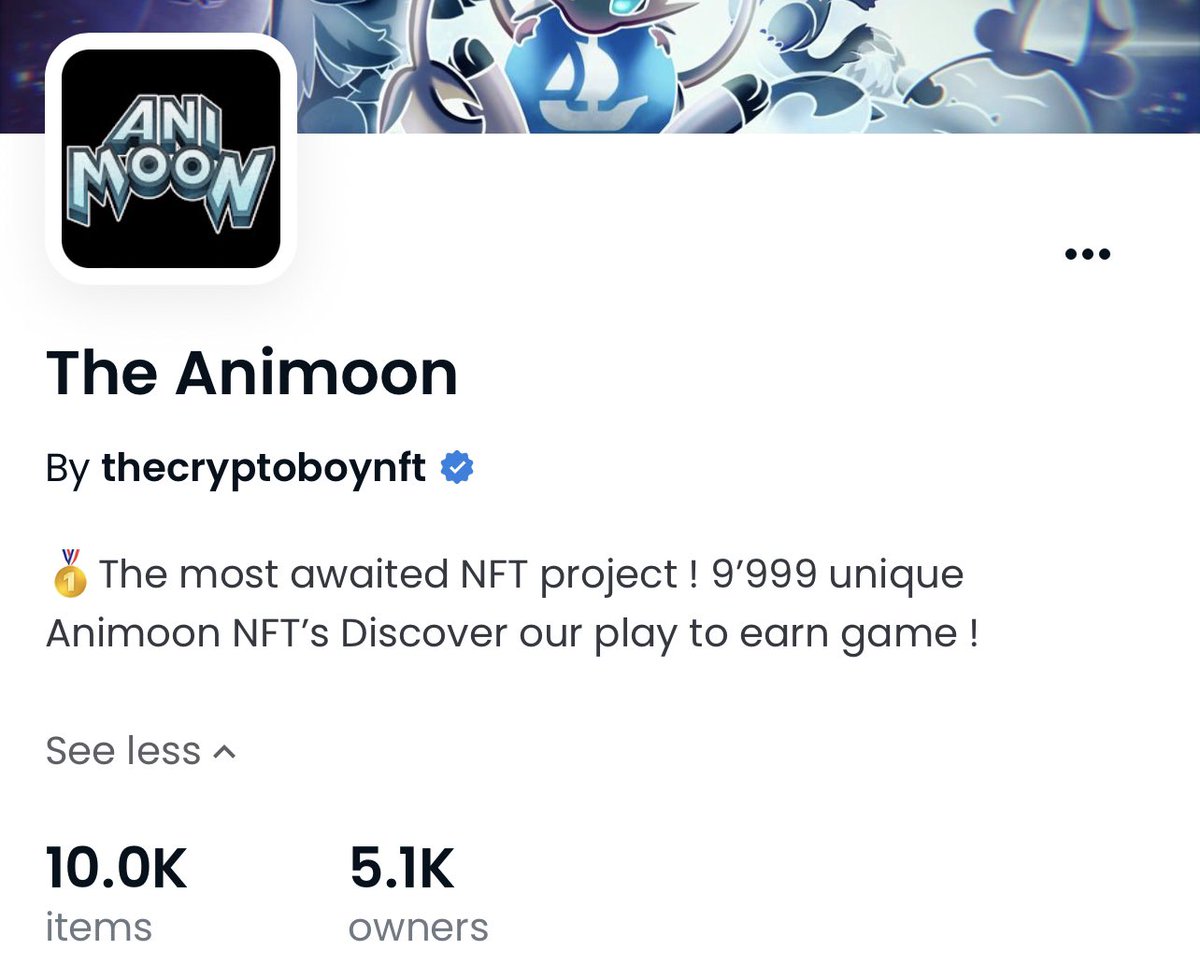

2/ The pfp NFT project was a collection of 9,999 NFTs @ 0.2 ETH advertised as a P2E game with utility such as large giveaways, breeding, irl trips, & more.
After almost 5 months nothing has been delivered. Yet another rug promoted by Jake Paul.



After almost 5 months nothing has been delivered. Yet another rug promoted by Jake Paul.
https://twitter.com/bestvideosofct/status/1532379293451530240


3/ Funny enough Animoon claims to have an NDA signed with Pokémon.
Why would Pokémon associate their IP with a low effort project and sketchy team that has zero background in gaming. Not to mention the art is a blatant rip off.

Why would Pokémon associate their IP with a low effort project and sketchy team that has zero background in gaming. Not to mention the art is a blatant rip off.
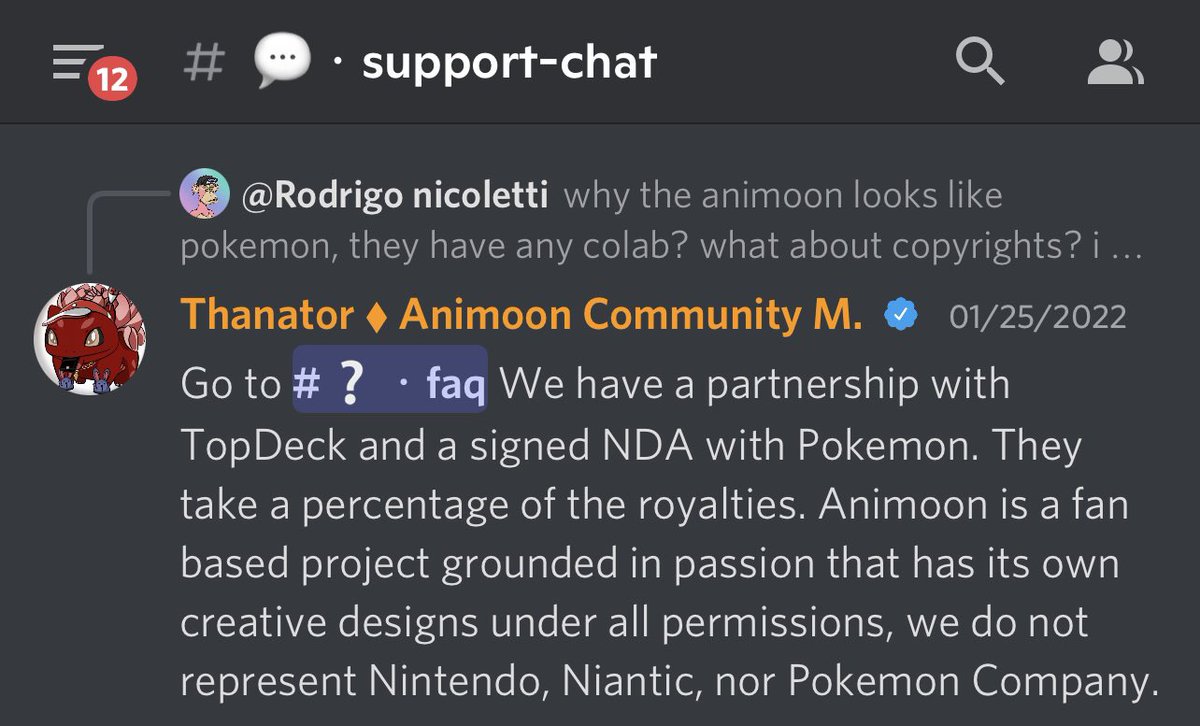

4/ Not long after launch the team begins to act very distant making announcements/appearing in chat every 3-4 weeks.
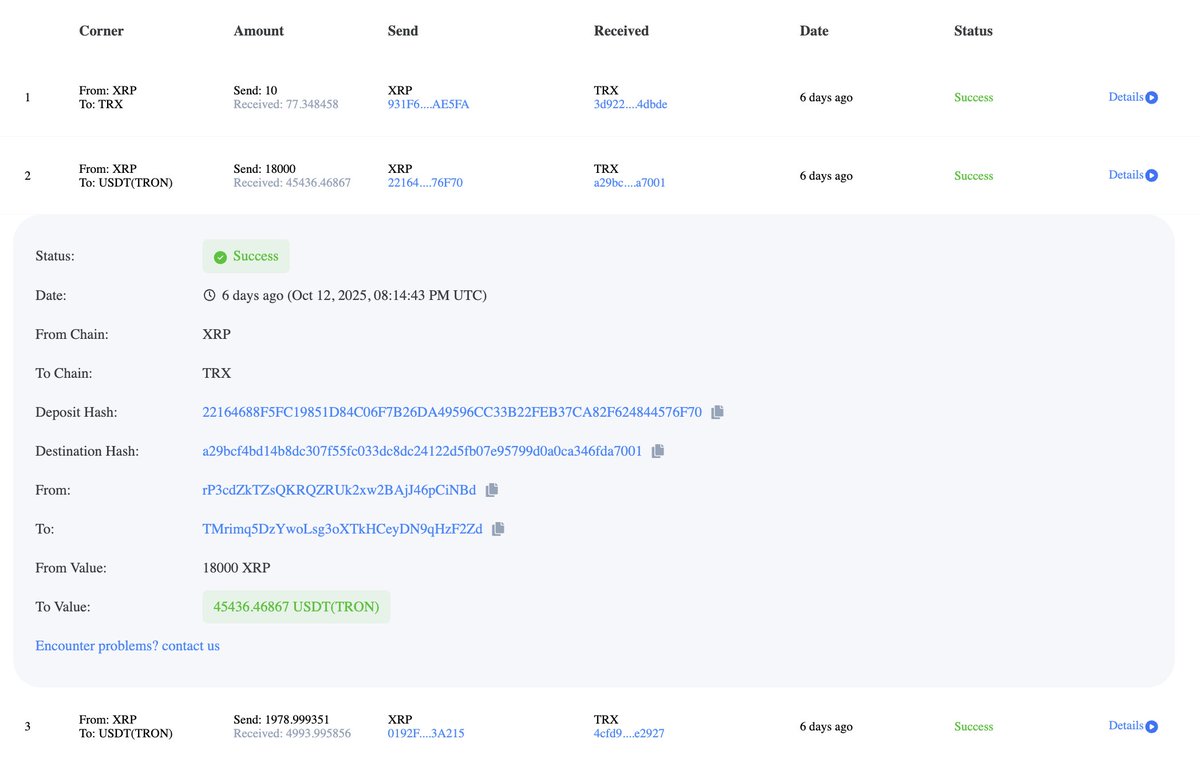
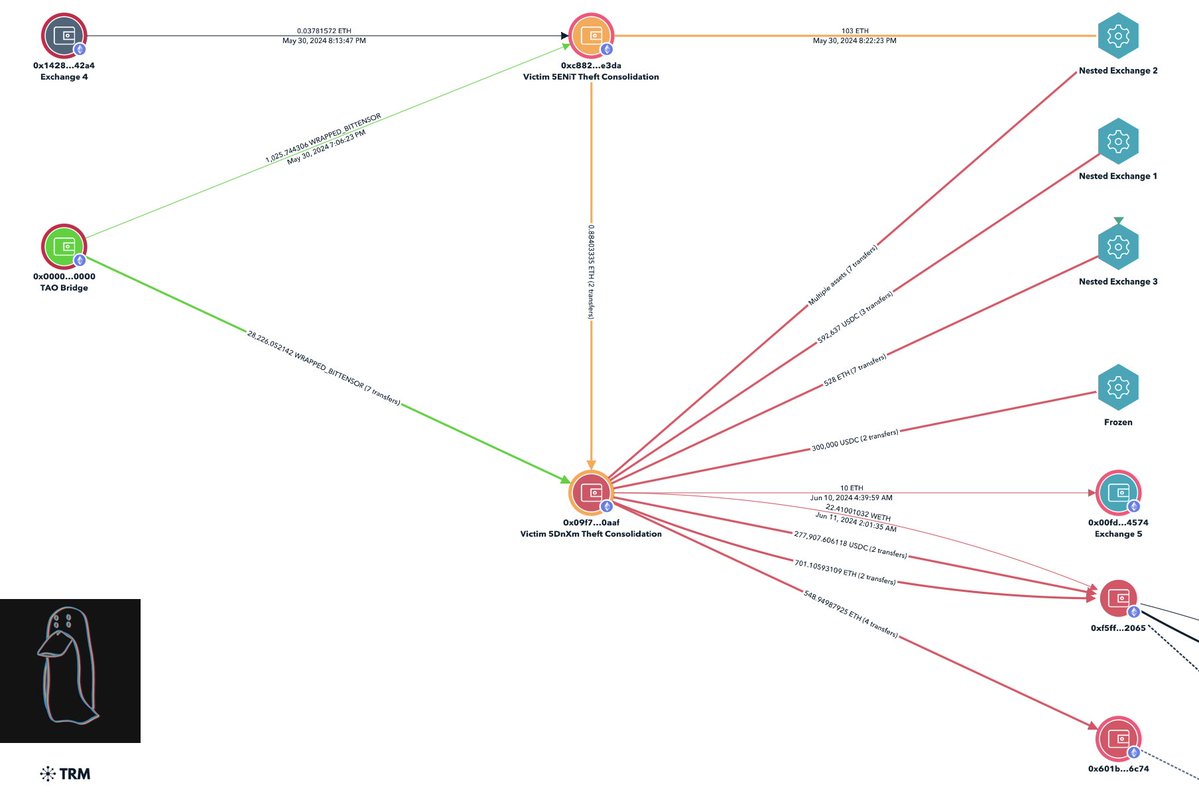
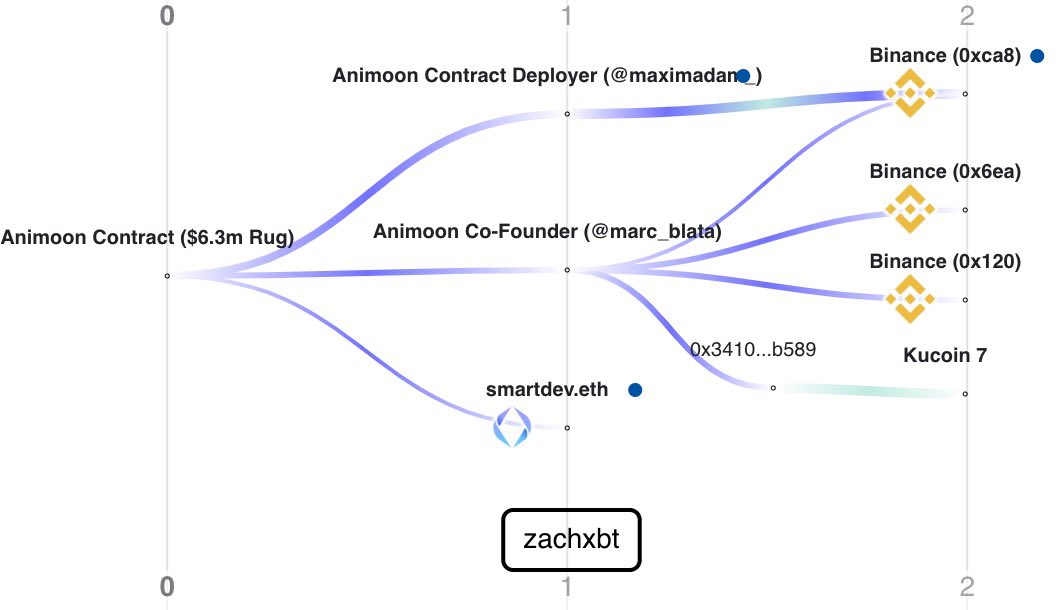
Meanwhile the $6.3m has been transferred away to Binance & Kucoin exchange accounts.
breadcrumbs.app/reports/1934
Meanwhile the $6.3m has been transferred away to Binance & Kucoin exchange accounts.
breadcrumbs.app/reports/1934
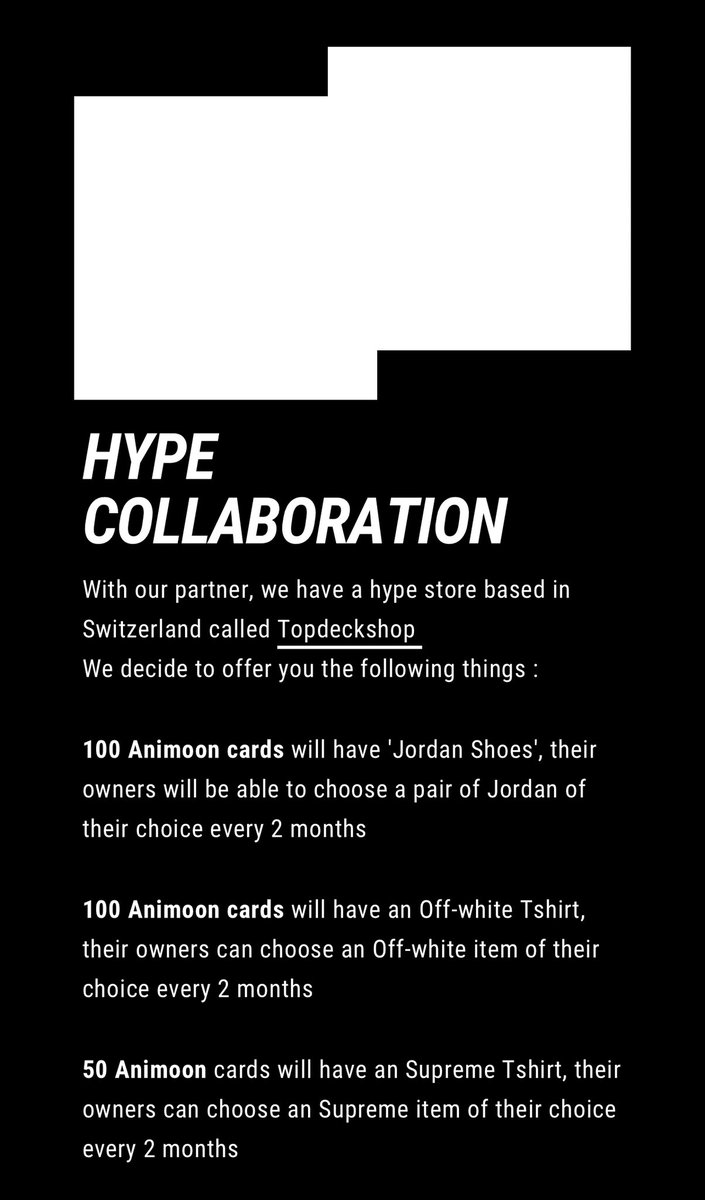
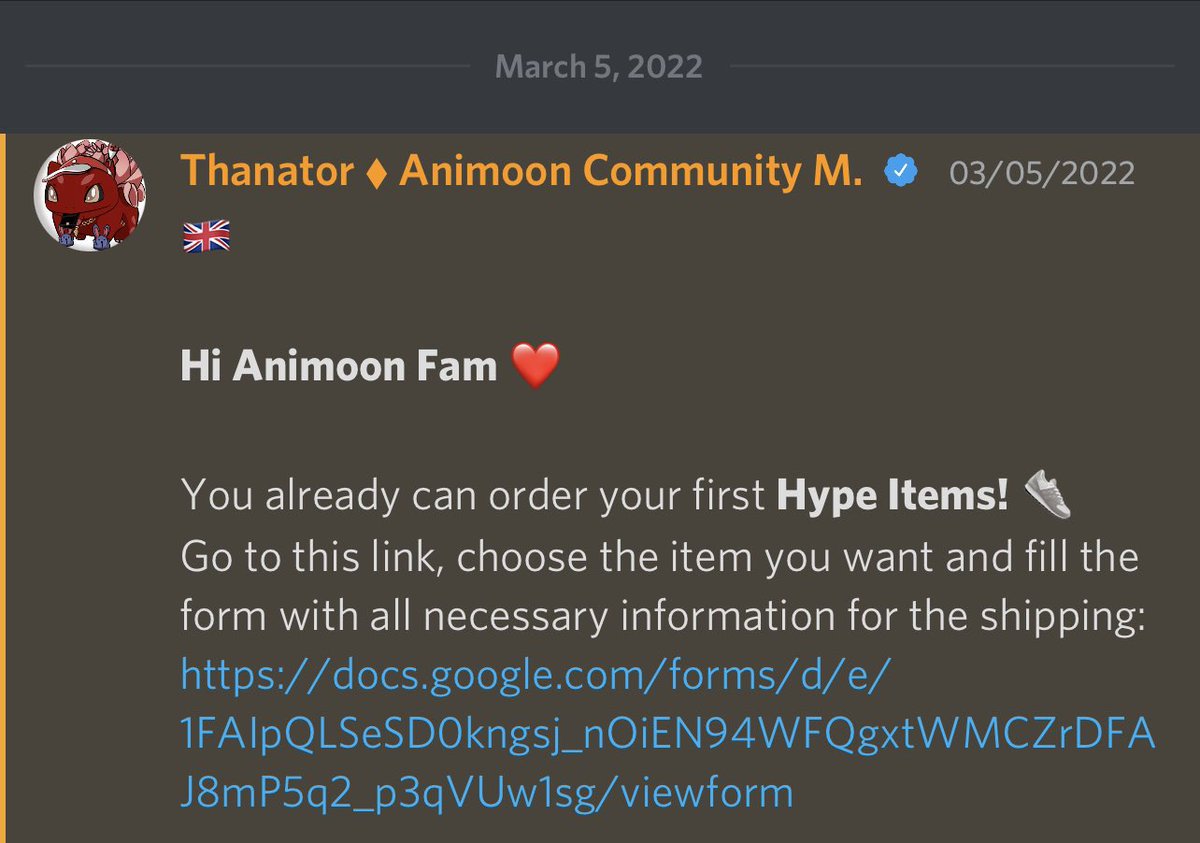
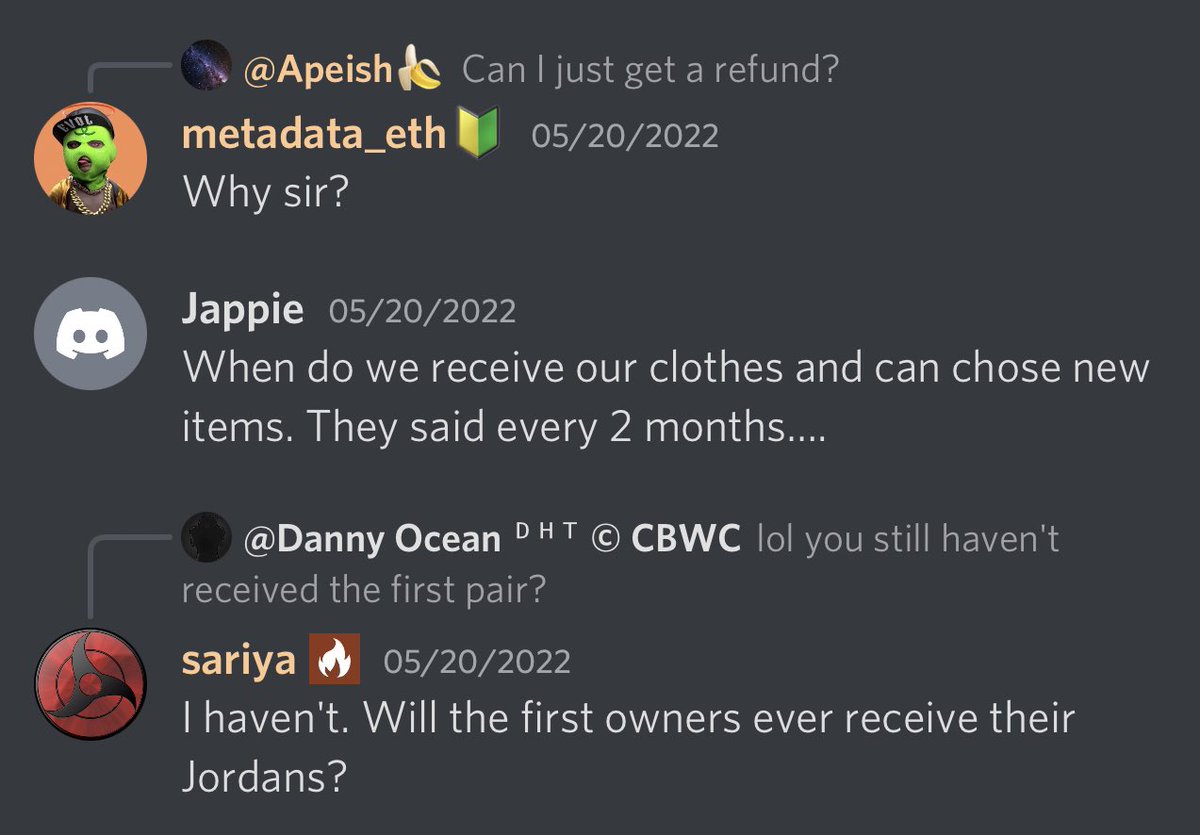
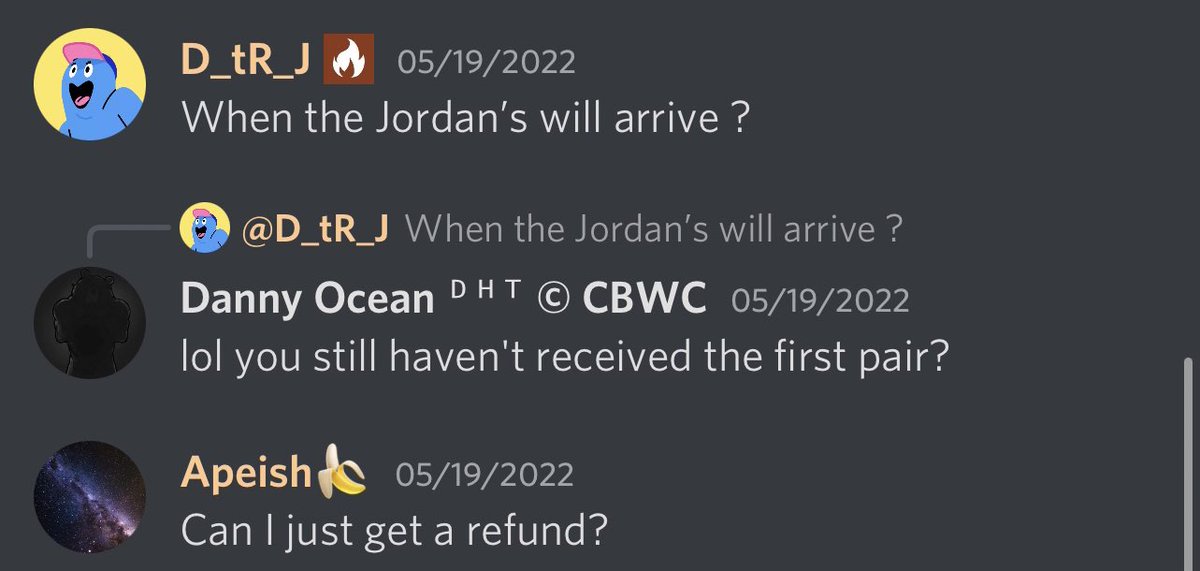
5/ In March 100 holders were supposed to receive Jordan shoes, another 100 holders to receive off white shirts, and another 50 holders to receive supreme shirts.
Yet it’s now June and no one has received anything.



Yet it’s now June and no one has received anything.

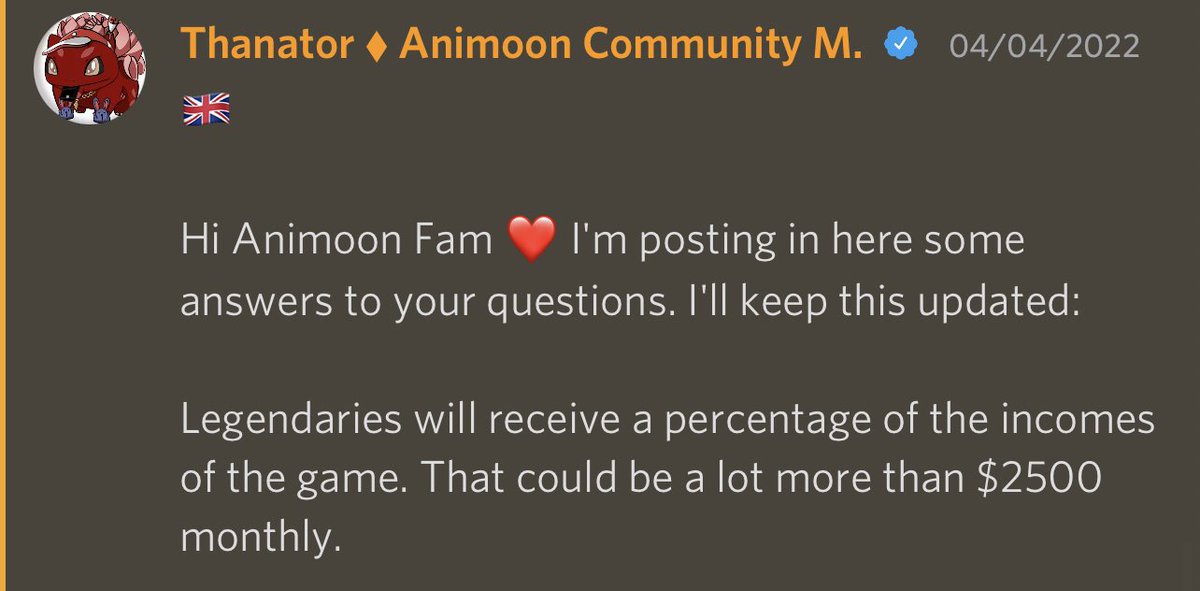
6/ As advertised the 15 Legendary NFT holders were supposed to received $2.5k every month for life from the public wallet.
There’s no evidence from either public wallet these have been sent out.

There’s no evidence from either public wallet these have been sent out.


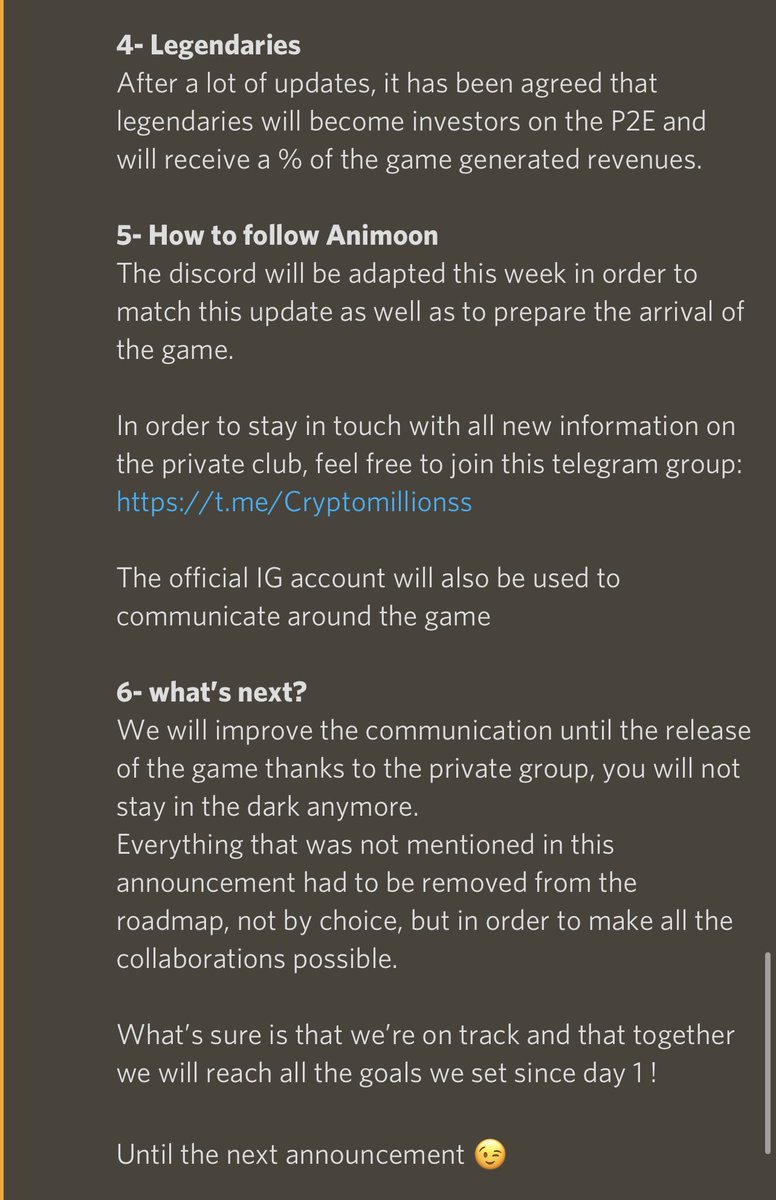
7/ In April the team changed it so Legendary holders now receive a % of the revenue from the P2E game.
Nonetheless this change didn’t ever get approval from legendary holders screwing them over.
Keep in mind their has been zero proof of this P2E game even being developed.
Nonetheless this change didn’t ever get approval from legendary holders screwing them over.
Keep in mind their has been zero proof of this P2E game even being developed.
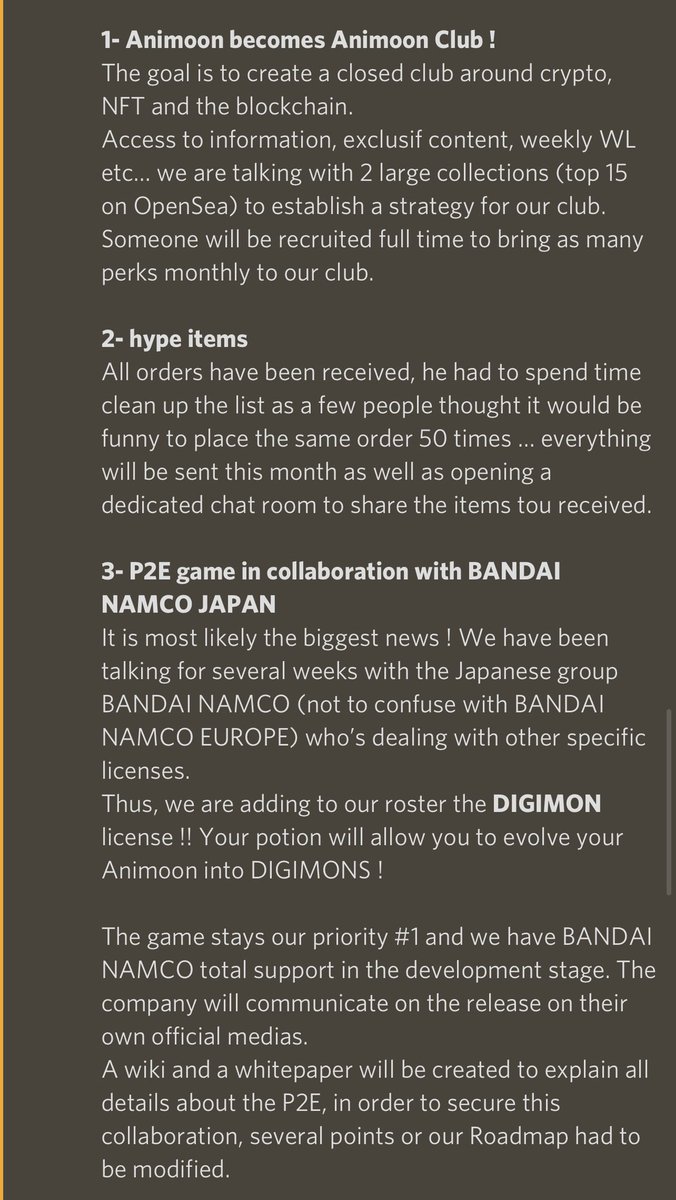
8/ Fast forward to early May and the team now claims to be working with Bandai Namco (Digimon)
Once again there is zero proof.
I DM’d BN on Twitter but am still waiting to hear back.

Once again there is zero proof.
I DM’d BN on Twitter but am still waiting to hear back.
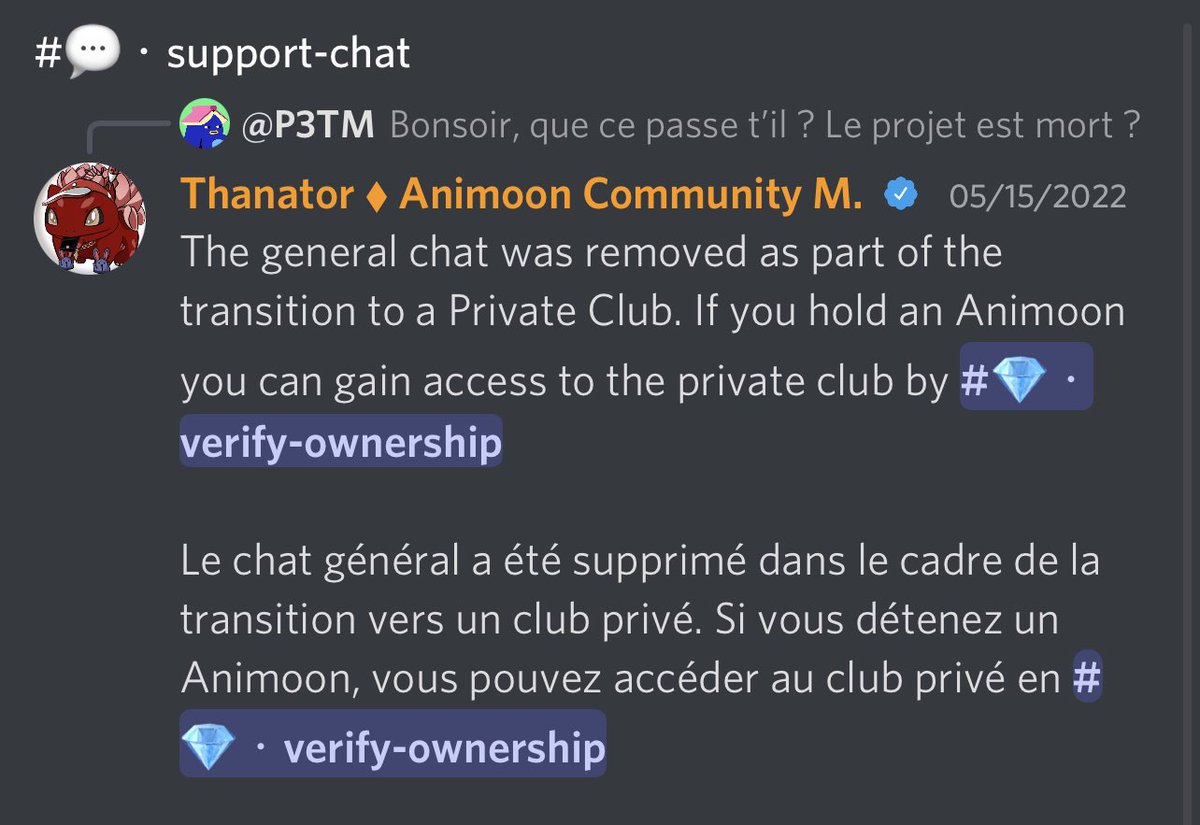
9/ At this point the Twitter account for Animoon is gone, the website isn’t functional, and general chat has been removed from the Discord 



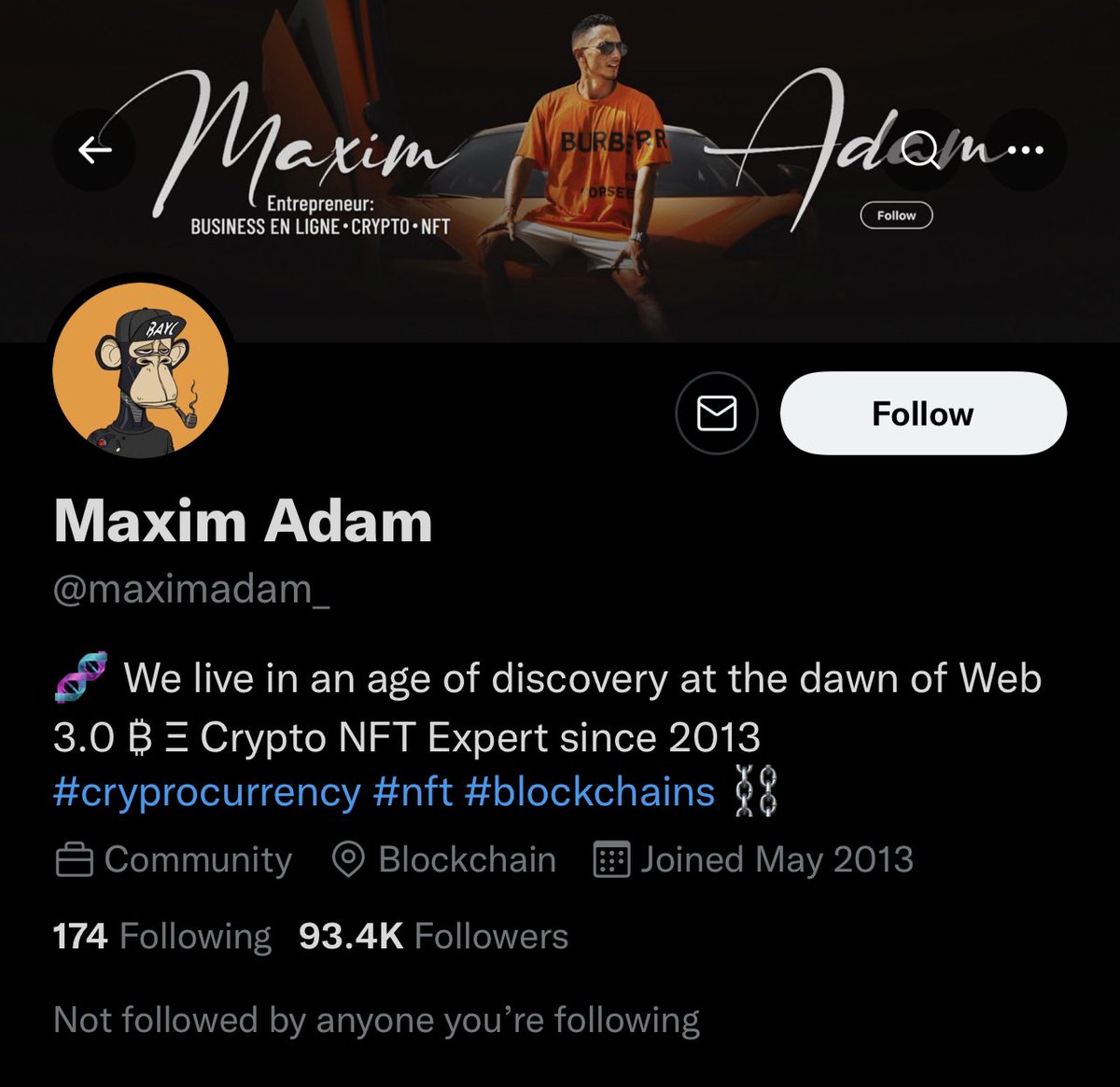
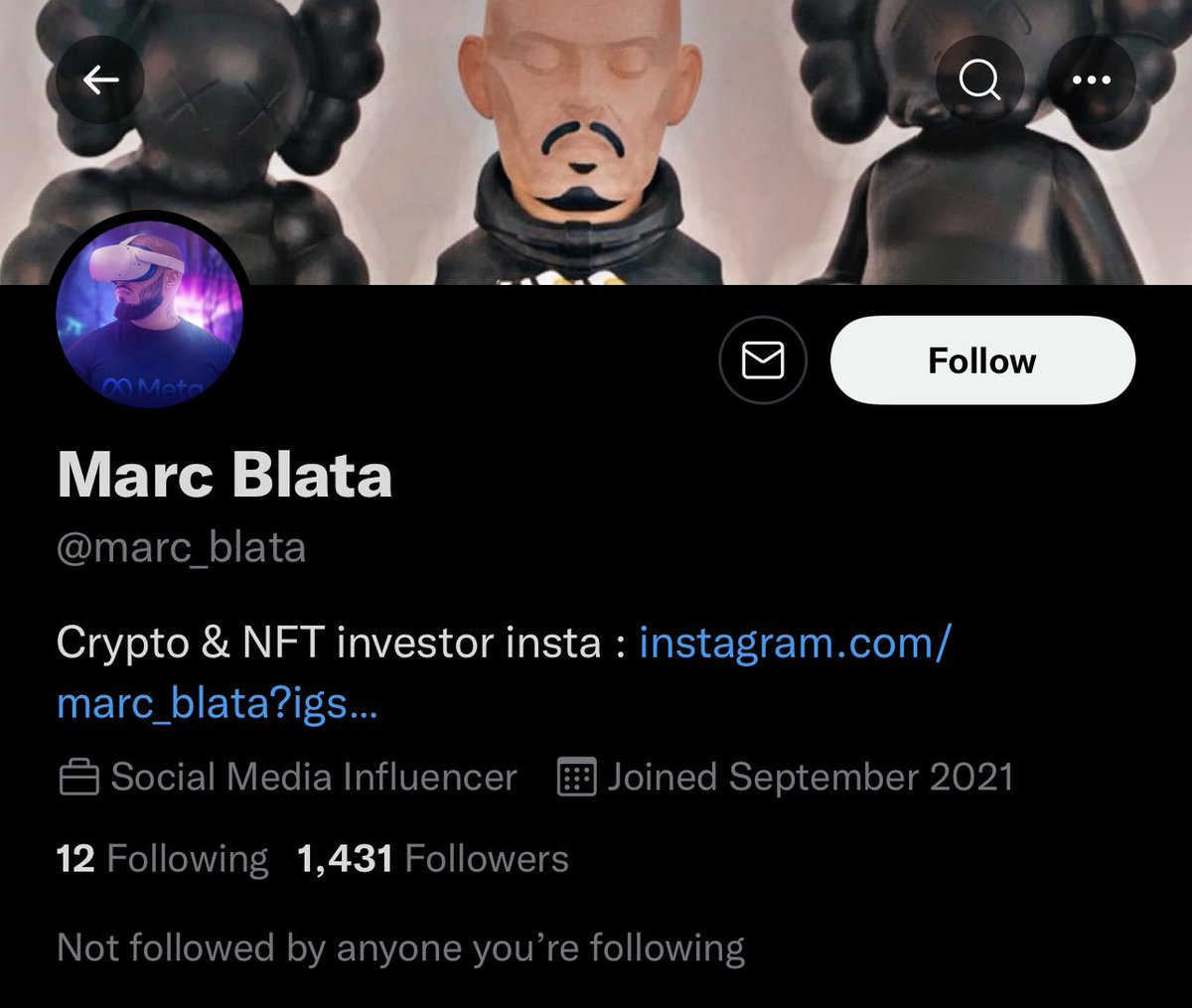
10/ The two founders behind Animoon used the names @maximadam_ & @marc_blata (not their real names).
Maxim’s bio claims to be a “NFT expert since 2013”
Both happen to post pics flexing in Dubai on Instagram.



Maxim’s bio claims to be a “NFT expert since 2013”
Both happen to post pics flexing in Dubai on Instagram.
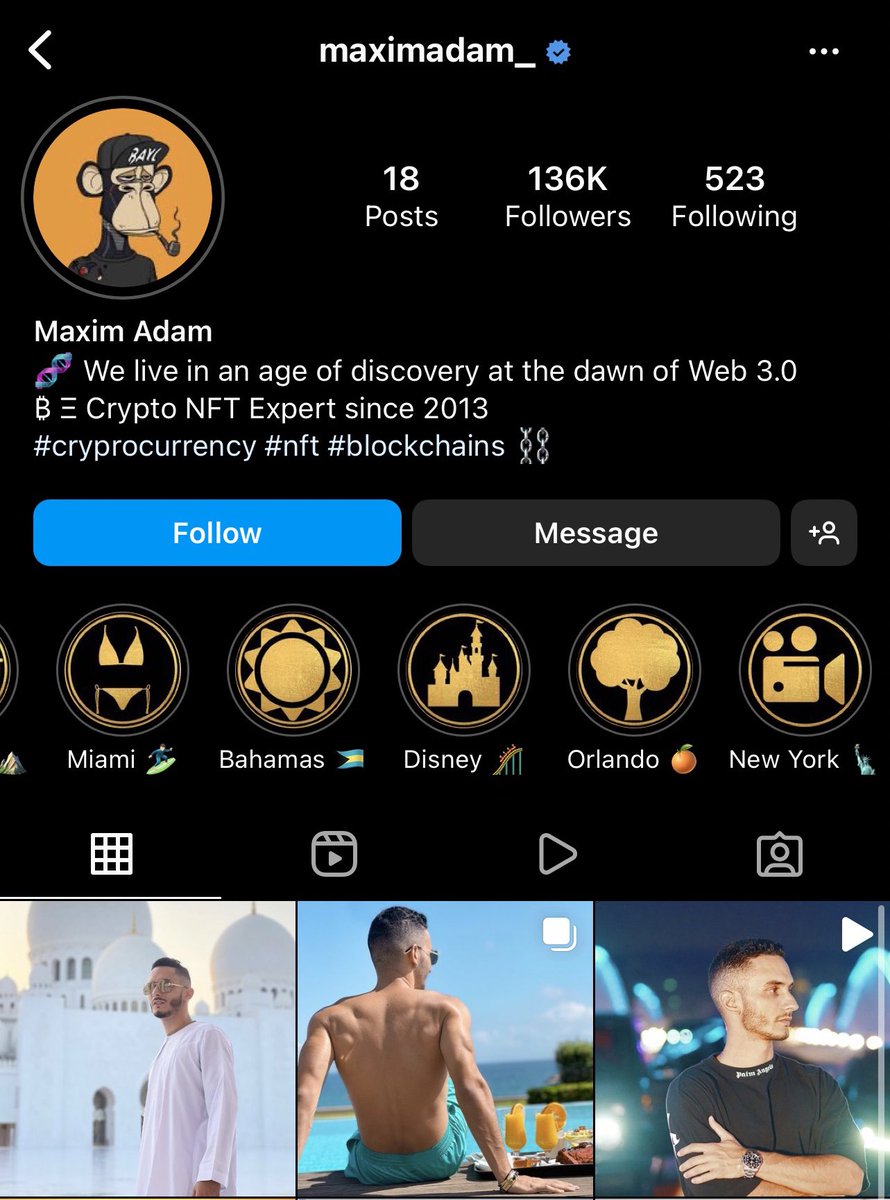
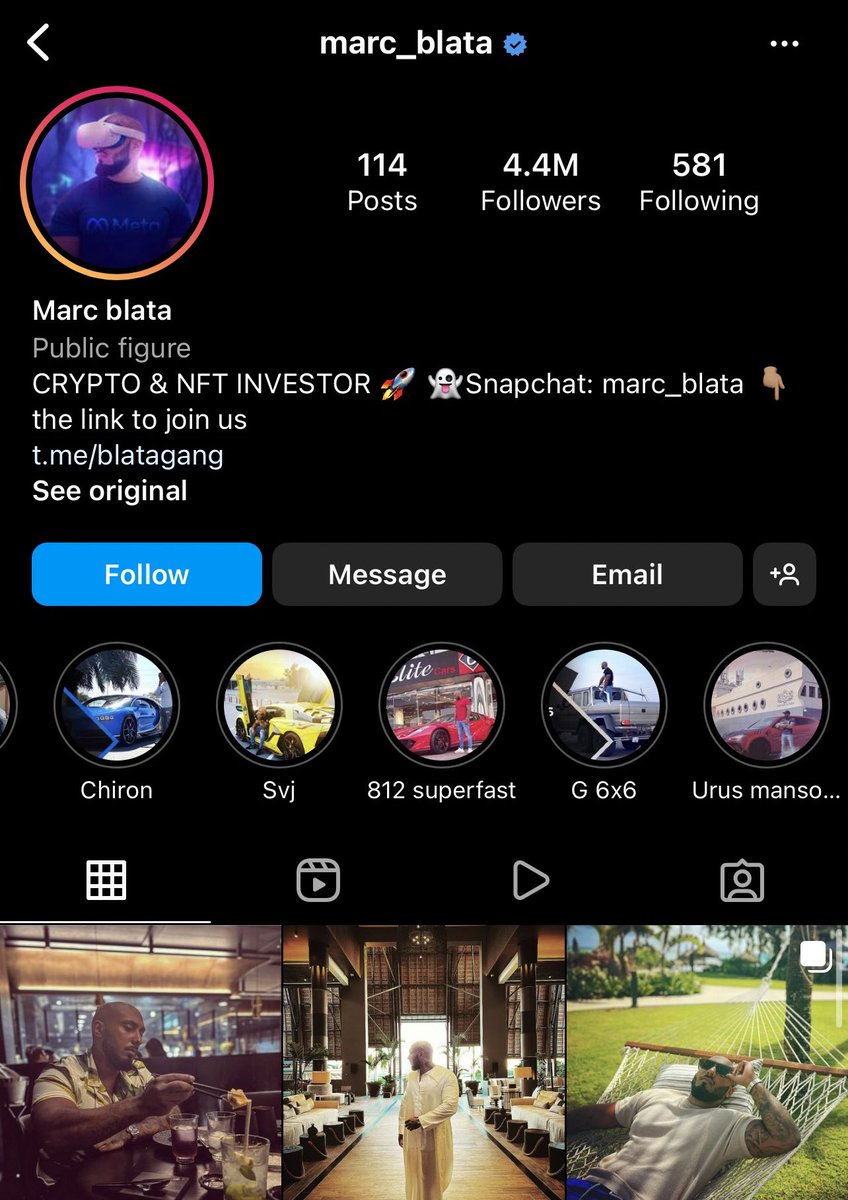
11/ I then went to look at wallet that corresponds with the BAYC in Maxim’s PFP.
It’s very clear @maximadam_ doesn’t own the NFT and is impersonating @OGDeathBot so I DM him.
He makes a tweet then what do you know @maximadam_ deletes his Twitter and goes private on insta.

It’s very clear @maximadam_ doesn’t own the NFT and is impersonating @OGDeathBot so I DM him.
He makes a tweet then what do you know @maximadam_ deletes his Twitter and goes private on insta.
https://twitter.com/OGDeathBot/status/1532232447873536005
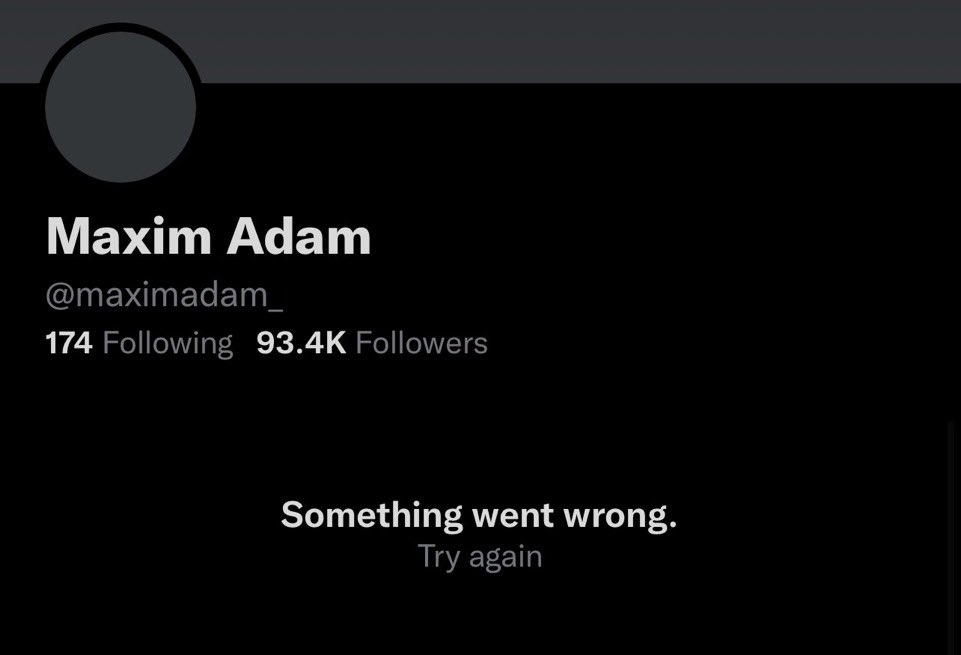
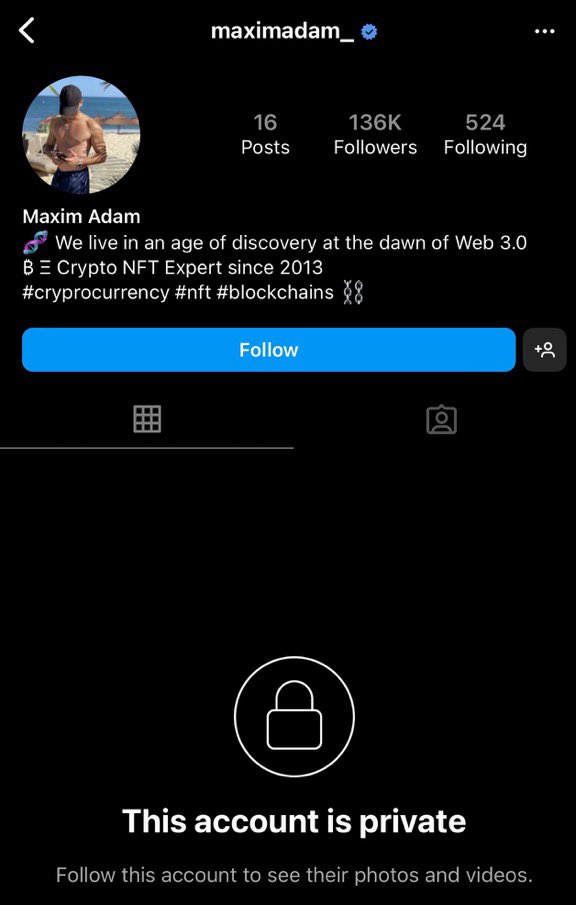
12/ To verify @maximadam_ real wallet I look at his recent Tweets and see he has purchased an NFT.
The address that purchased that NFT of course is none other than the one who deployed the Animoon contract.



The address that purchased that NFT of course is none other than the one who deployed the Animoon contract.
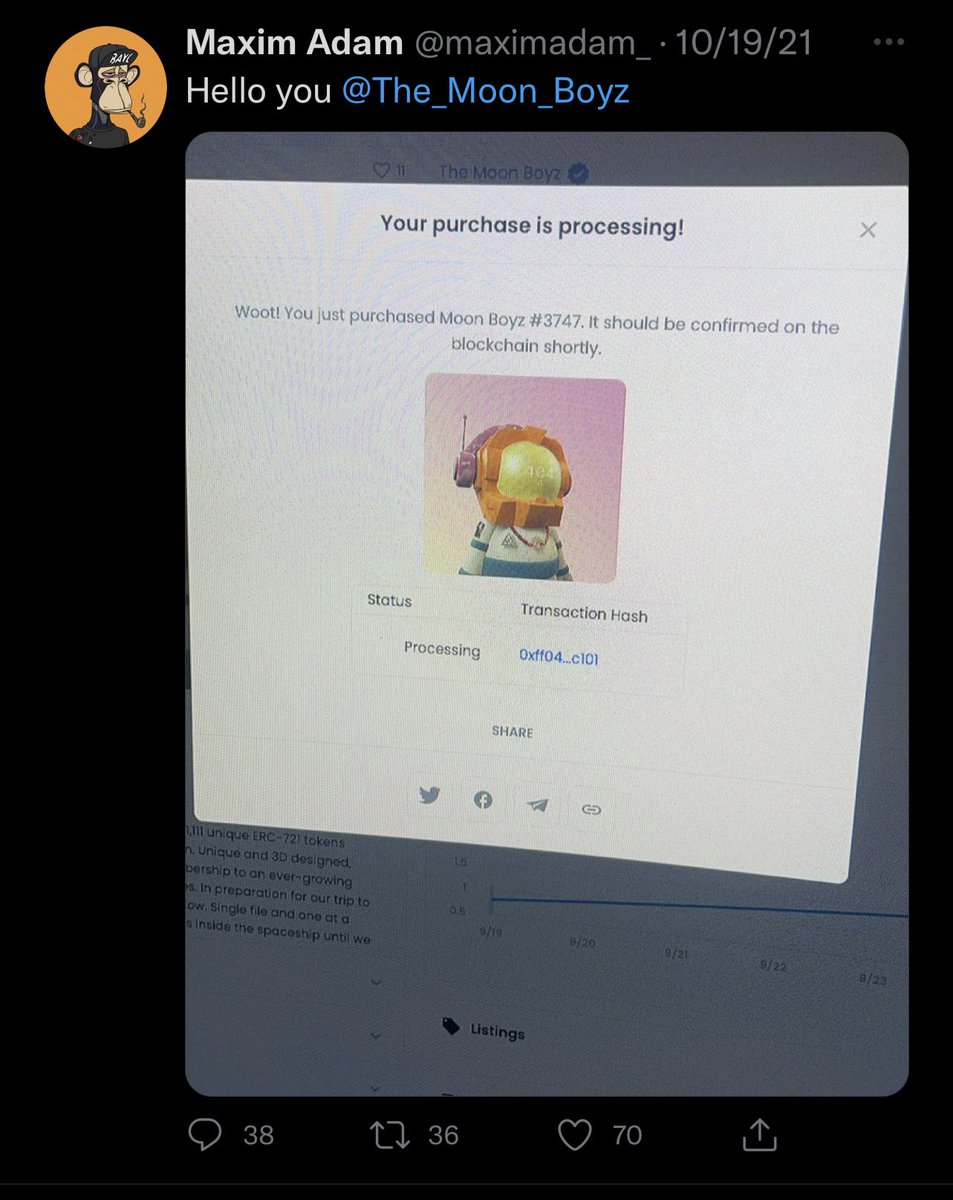
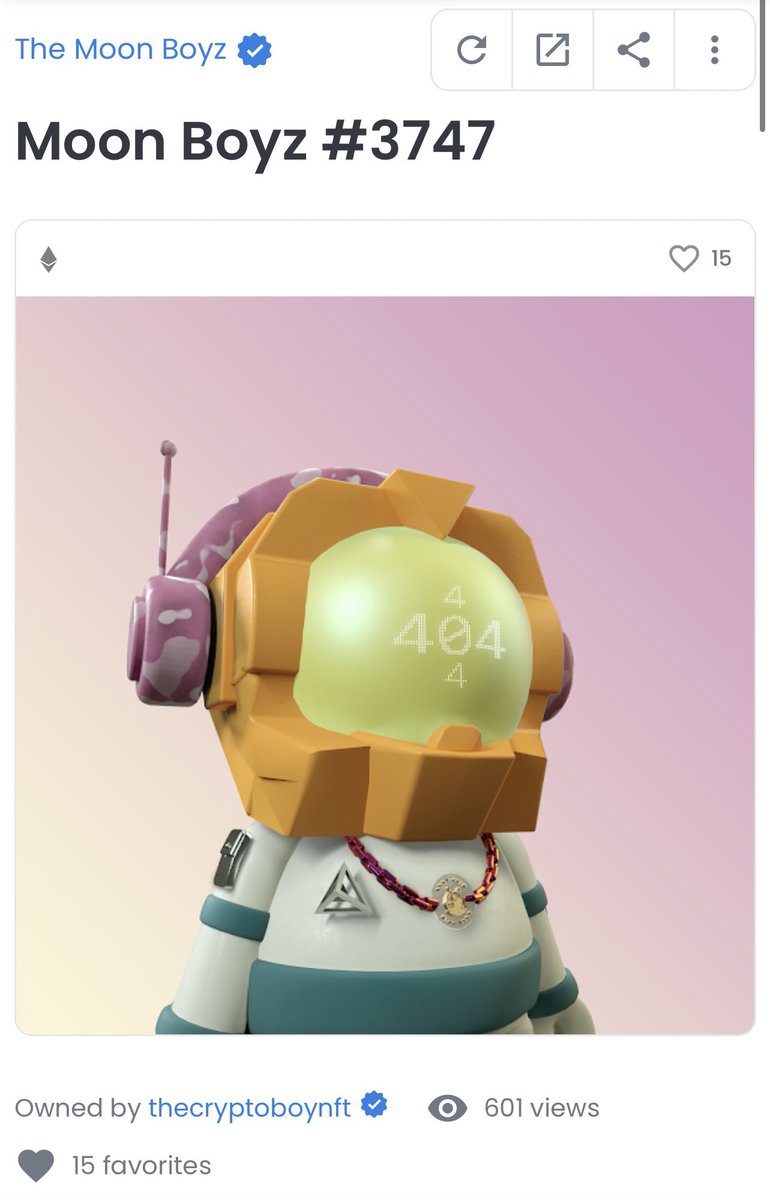
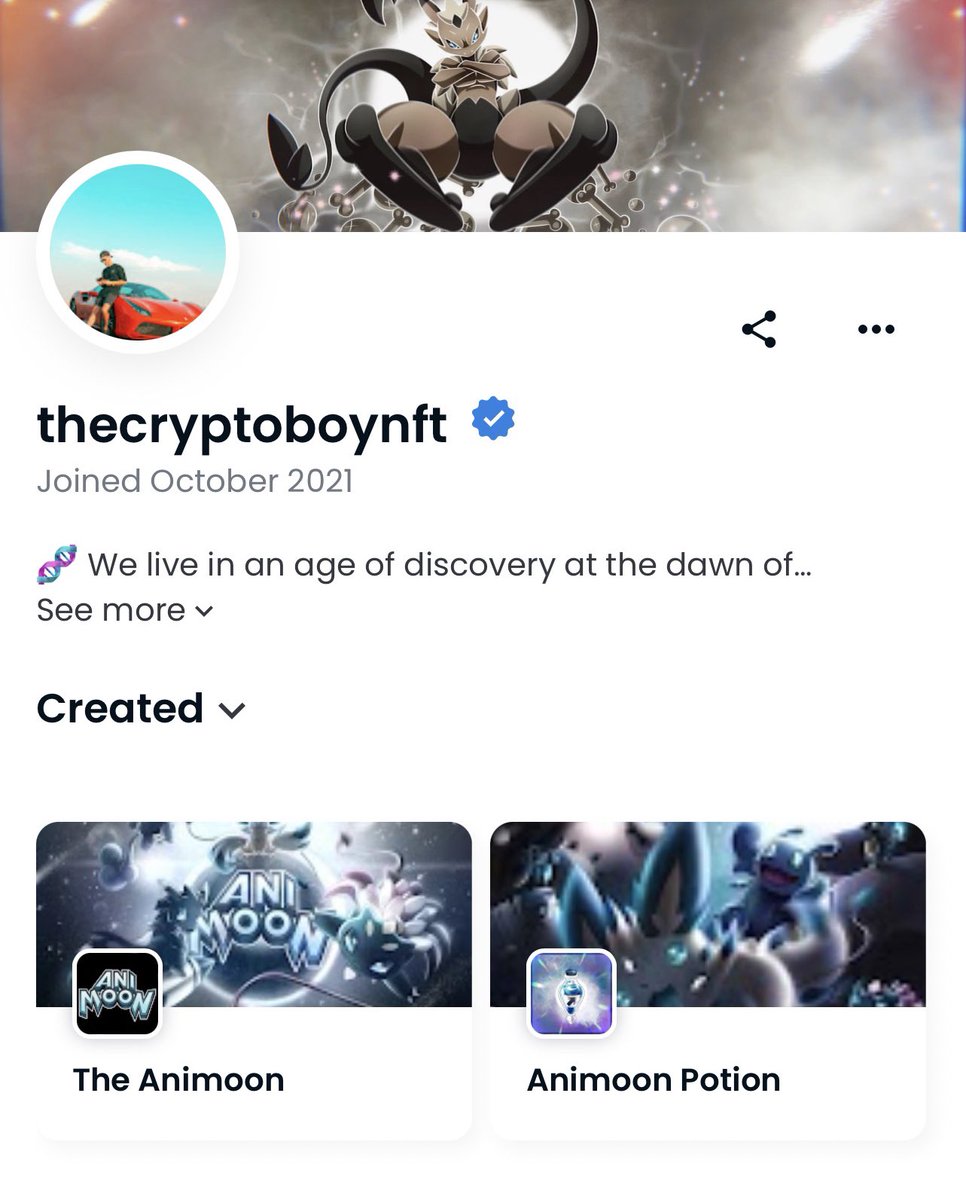
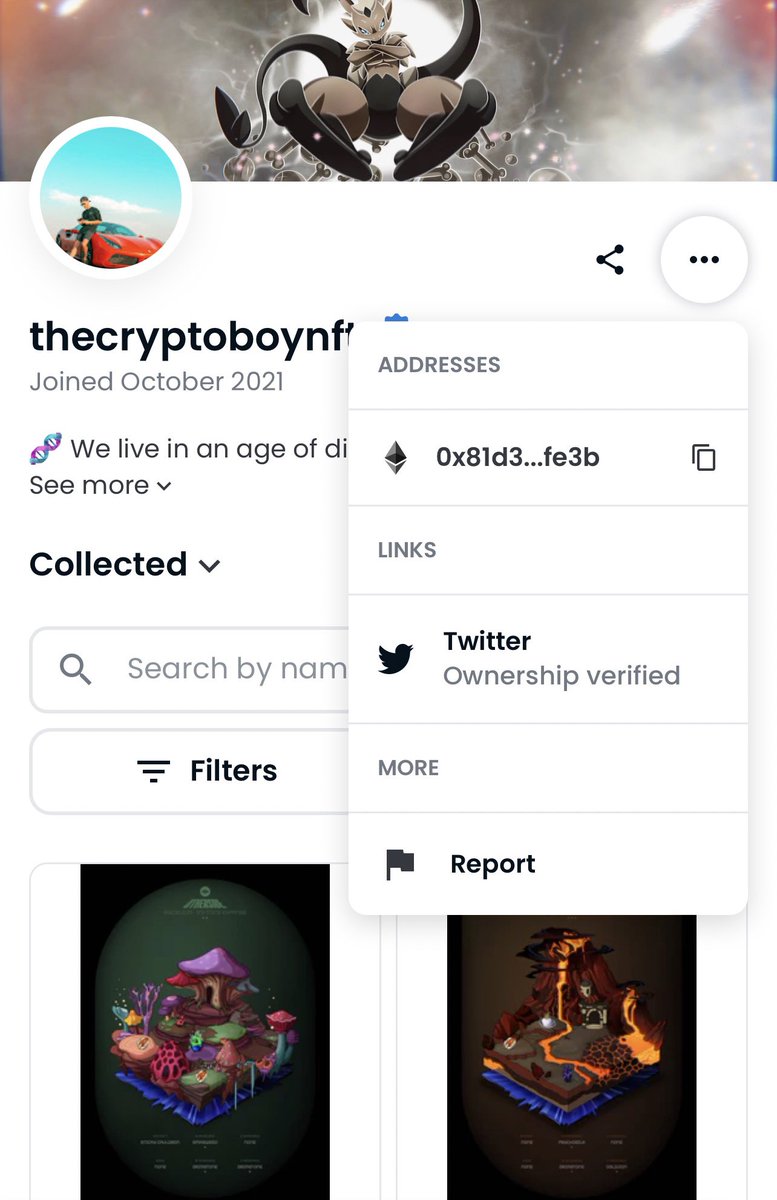
12/ So who are the actual names of the founders behind Animoon?
Over the past few week the French rapper @booba has been relentless going after founders for all their different schemes.
It is revealed they are Mounir Mokaddem & Singainy Marc Oceane
Over the past few week the French rapper @booba has been relentless going after founders for all their different schemes.
It is revealed they are Mounir Mokaddem & Singainy Marc Oceane
https://twitter.com/booba/status/1522295775929245696
13/ It’s quite comedic at all the different partnerships the Animoon founders claim to have and all the things they’ve failed to deliver on.
They currently reside in Dubai. If you were a victim you can file a report here.
dubaipolice.gov.ae/wps/portal/hom…
@DubaiPoliceHQ
They currently reside in Dubai. If you were a victim you can file a report here.
dubaipolice.gov.ae/wps/portal/hom…
@DubaiPoliceHQ
Update: If you were a victim of Animoon feel free to join the class action lawsuit here.
https://twitter.com/ZieglerAssocies/status/1537834456312078342
• • •
Missing some Tweet in this thread? You can try to
force a refresh