@SBSDiva Yes, I understand. You see, he uses PS2EXE for his tool, which is very often used for malicious purposes. I simply highlight that. Nothing more.
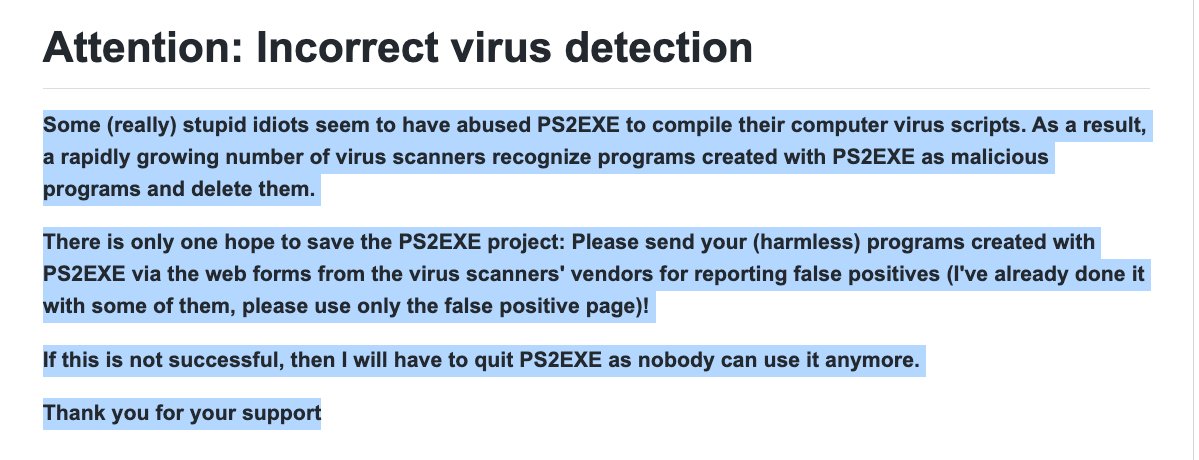
The author of PS2EXE noticed that as well, btw
github.com/MScholtes/PS2E…
Other samples build with PS2EXE
valhalla.nextron-systems.com/info/rule/SUSP…
The author of PS2EXE noticed that as well, btw
github.com/MScholtes/PS2E…
Other samples build with PS2EXE
valhalla.nextron-systems.com/info/rule/SUSP…
• • •
Missing some Tweet in this thread? You can try to
force a refresh