PHISHING Attacks | Twitter
#hackingwithfriends
@TOTTechs @ITexpertTz @HabariTech @blackninja233 @INFLUENCERjr @nicl4ssic @anon_codex @asatayo @abdoolkhery
KILA mtu anajua maana ya phishing attack na currently kuna watu wanadiriki kusema siwezi kuwa hacked via phishing. .....
#hackingwithfriends
@TOTTechs @ITexpertTz @HabariTech @blackninja233 @INFLUENCERjr @nicl4ssic @anon_codex @asatayo @abdoolkhery
KILA mtu anajua maana ya phishing attack na currently kuna watu wanadiriki kusema siwezi kuwa hacked via phishing. .....

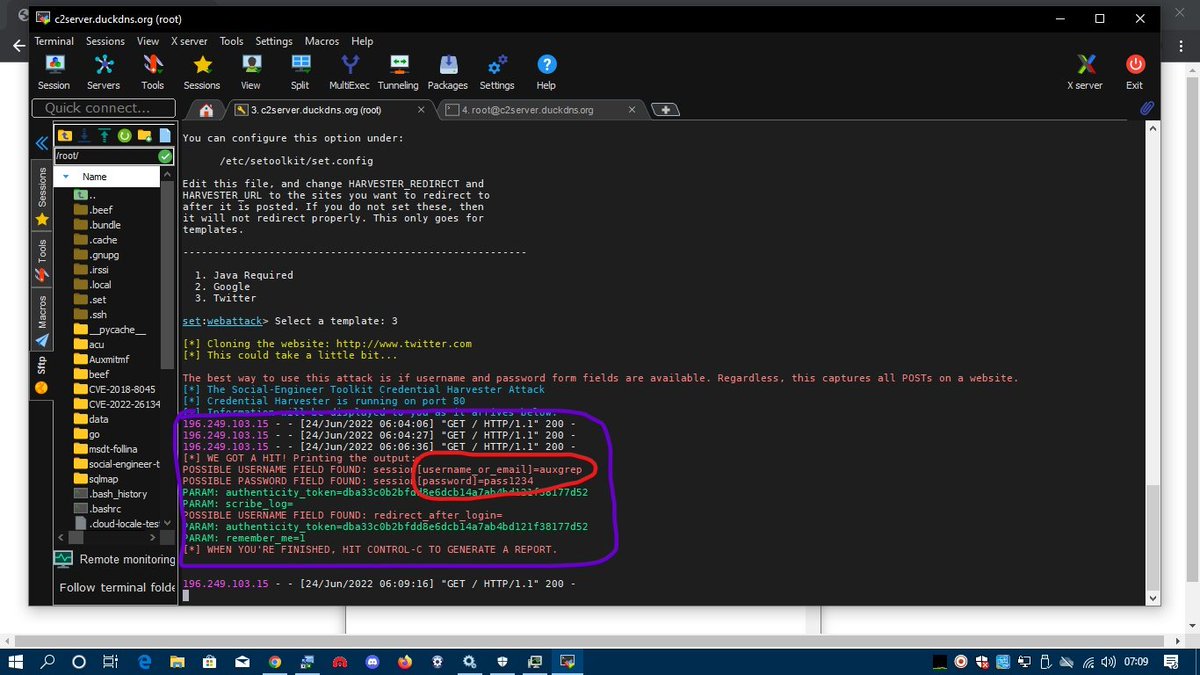
Jibu ni No Anyways leo kwenye hacking with friends tutachek namna gani unaweza kuwa phished kwa kutumia BITB ATTACK
Phishing ni udanganyifu unafanywa na cyber crimes kupitia cloned web pages ambazo zinaonekana kama legitimate website za mtoa huduma kwa lengo la kupata ur logs
Phishing ni udanganyifu unafanywa na cyber crimes kupitia cloned web pages ambazo zinaonekana kama legitimate website za mtoa huduma kwa lengo la kupata ur logs
Kupitia hii wanaweza iba credit cards info , social media accounts nk.
Sasa leo lets see ni jinsi unaweza kuwa capture easy bila kujua kutumia browser in the browser attack.
As attacker , Nimegundua miongoni mwa users wengi hupendelea sana kusign up using social media accounts
Sasa leo lets see ni jinsi unaweza kuwa capture easy bila kujua kutumia browser in the browser attack.
As attacker , Nimegundua miongoni mwa users wengi hupendelea sana kusign up using social media accounts
Yani unakuta website imekupa options usign up kwa kutumia social media acc mfano twitter, Facebook, au even google A/c Na wengi hupendelea kwasabb inaokoa muda na ukichek website ni secured inatumia https kwenye kuexchange data between client na server
Okay as u can see here👇
Okay as u can see here👇
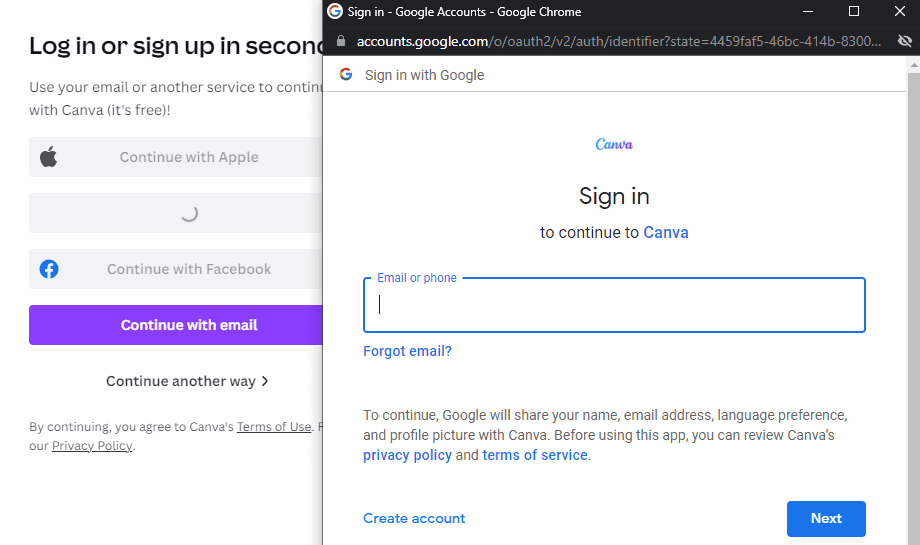
Na tunajua ukipress kale ka botton sign with Facebook au google huwa inatokea ka window fulan ili ki authenticate user logs na ile service ambayo unataka kuregister nayo.
Sasa kupitia hii unaweza kuwa hacked na usijijue ....lets see
1. Nitaprepare my C&C server kwa host simple
Sasa kupitia hii unaweza kuwa hacked na usijijue ....lets see
1. Nitaprepare my C&C server kwa host simple
Websites ambayo huwez pata service bila kusign up na nitaweka hizo signing options. Sasa demonstration nitaclone imgbb.com website na kuihost kwenye apache server via port 89. Hii ndo landing page kwa user.
Baada ya hapo nitatumia simple FSOCIETY scripts ku launch
Baada ya hapo nitatumia simple FSOCIETY scripts ku launch
Phishing page . Na hapa nitatumia twitter kama mfano , 👇
Lakini issue iko moja , ukitumia hii script connection zote zitakuwa zinapita kwenye unencrypted channel yani http , na kumbuka apache2 iko kwenye port 89 na hii phishing yangu iko kwenye port 80 .
Now nitakachokifanya ..
Lakini issue iko moja , ukitumia hii script connection zote zitakuwa zinapita kwenye unencrypted channel yani http , na kumbuka apache2 iko kwenye port 89 na hii phishing yangu iko kwenye port 80 .
Now nitakachokifanya ..
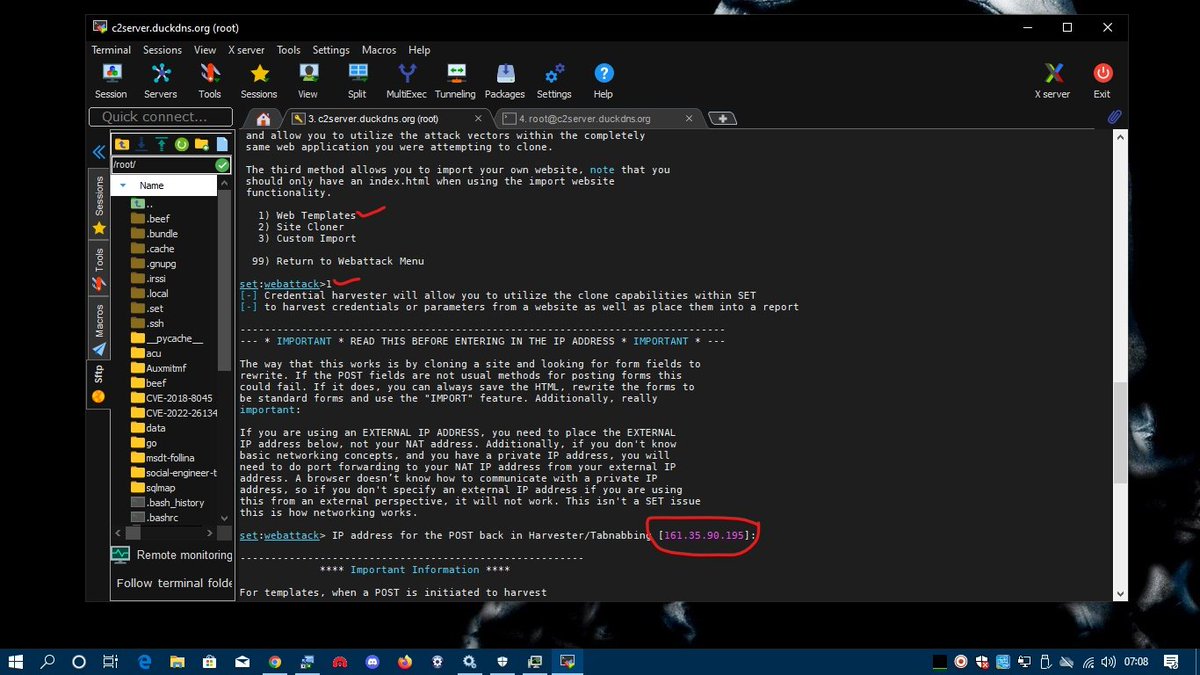
Ni kupandisha ssl ili site yangu iwe From http to https (secured) , hapa nitumia cloudflare tunnel nitaiconnect na ile service port 89.
CLOUDFLARE TUNNEL HOOK PORT 89 👇
nitapataaa HTTPS domain name ambayo iko na https na itahook ile apache2 server kwenye port 89
CLOUDFLARE TUNNEL HOOK PORT 89 👇
nitapataaa HTTPS domain name ambayo iko na https na itahook ile apache2 server kwenye port 89
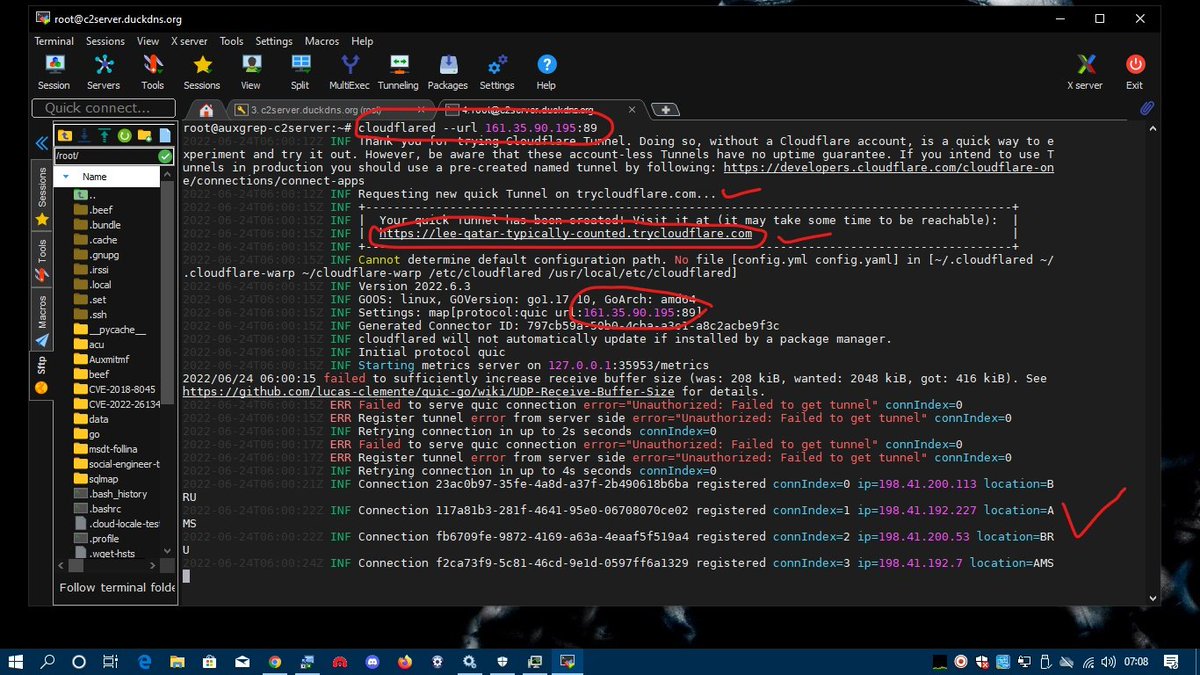
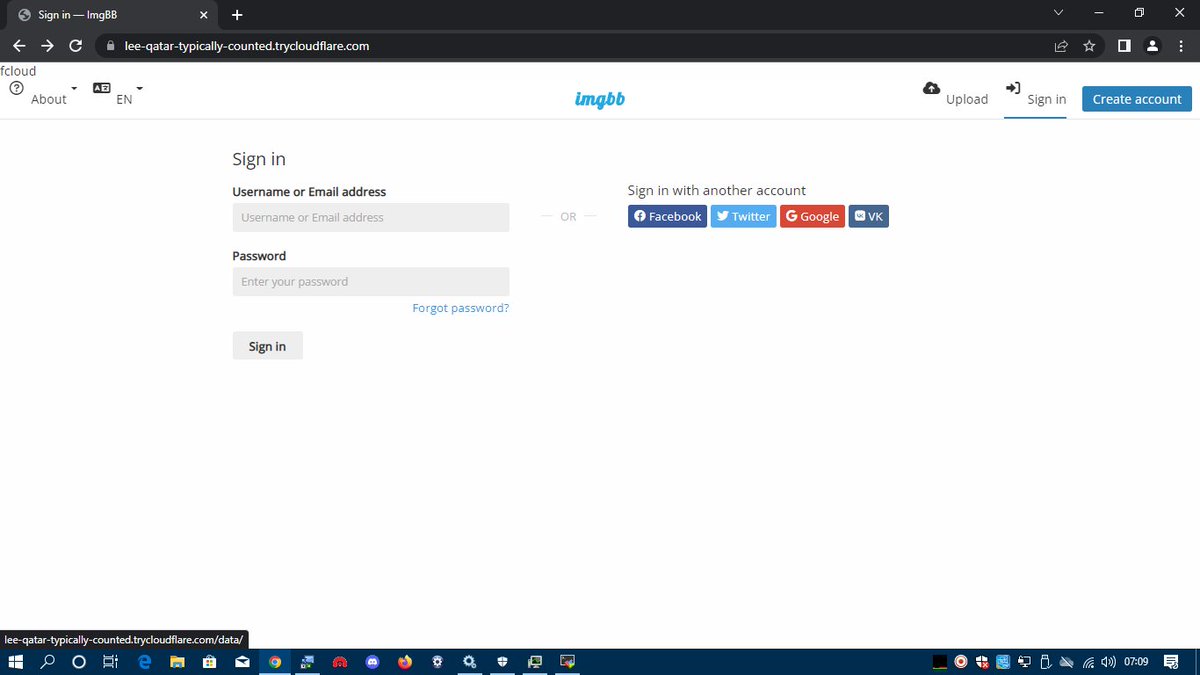
Ukija kwenye browser now my phishing website iko na https na ni secured, 😎
now nadhani kwenye picha utaona kulia kuna hizo sign in options na me hapa ndipo nitahost phishing yangu ambayo ina run kwenye port 80 kama ulivyooiona hapo juu.
(Don't worry ukihitaji video setup ipo)
now nadhani kwenye picha utaona kulia kuna hizo sign in options na me hapa ndipo nitahost phishing yangu ambayo ina run kwenye port 80 kama ulivyooiona hapo juu.
(Don't worry ukihitaji video setup ipo)
Kumbuka hii phishing mdukuzi anaweza host evilgnx2 phishing campaign na ubaya hii inauwezo wa kuipa session cookies, logs nk (OTP BYPASSED)
niliwahi iongelea last summer.
So now nitaweka BITB framework iconnect na ile fsociety twitter phishing page iload kwenye iframe ambazo
niliwahi iongelea last summer.
So now nitaweka BITB framework iconnect na ile fsociety twitter phishing page iload kwenye iframe ambazo

Itampumbaza user , mfano ukipress ile botton ya sign in with Twitter itatokea kitu hiki hapa 👇, yani kama haupo makini u will never notice hii mambo utaona kwanza legitimate twitter URL kila kitu kiko legitimate na ni secured connection.
Sasa mfano ukisubmit logs zako.
Sasa mfano ukisubmit logs zako.
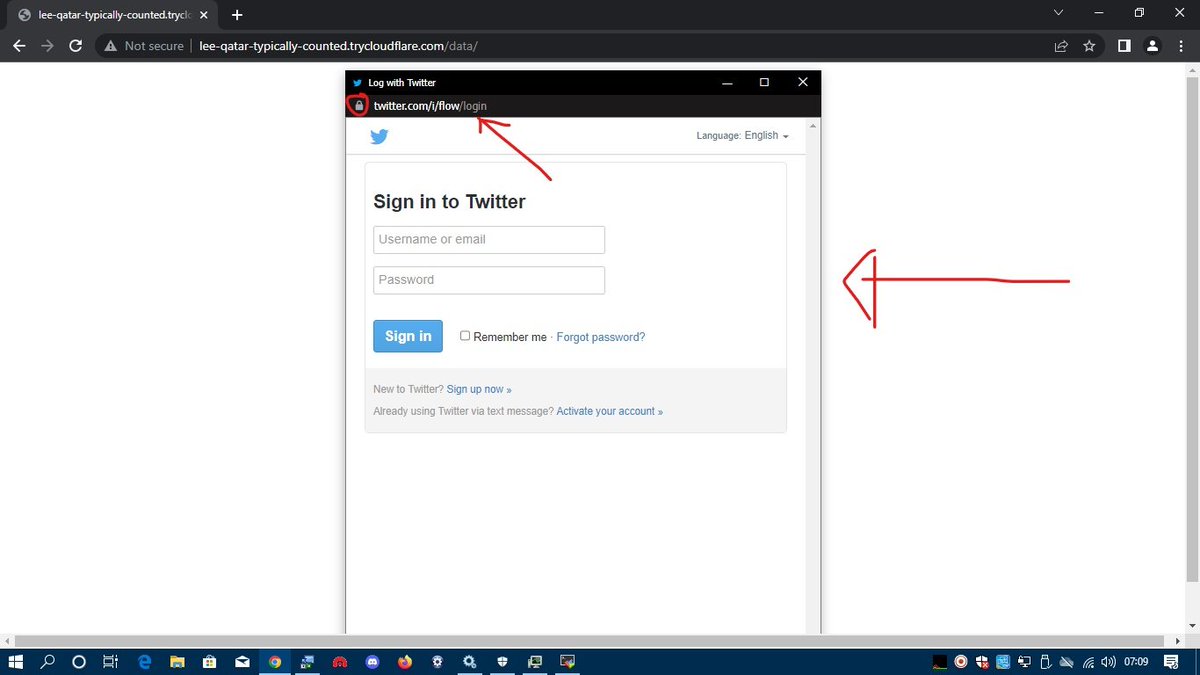
Utaaambiwa tu connection refused by twitter na hapa kama tungetumia evilgnx2 ungekuwa ndani kabisa kwenye ur twitter profile ila tu kwa upande mwingine mdukuzi atapata your username , password + session cookies 

• • •
Missing some Tweet in this thread? You can try to
force a refresh