#ESETResearch warns of a new campaign using a fake Salesforce update as a lure to deploy the Sliver malware for macOS and Windows 1/9 

The Mac infection chain is very similar to a COVID-19-themed campaign documented by SentinelOne last week. sentinelone.com/blog/from-the-… 2/9
This new campaign uses an additional GoLang Mach-O executable that downloads and runs the bash script used to deploy Sliver. 3/9 



The shell script to deploy Sliver is very similar to the one found by SentinelOne, except it doesn’t include the “covid” malware and only installs the Sliver implant, which is sufficient to deploy additional malware if needed. 4/9 

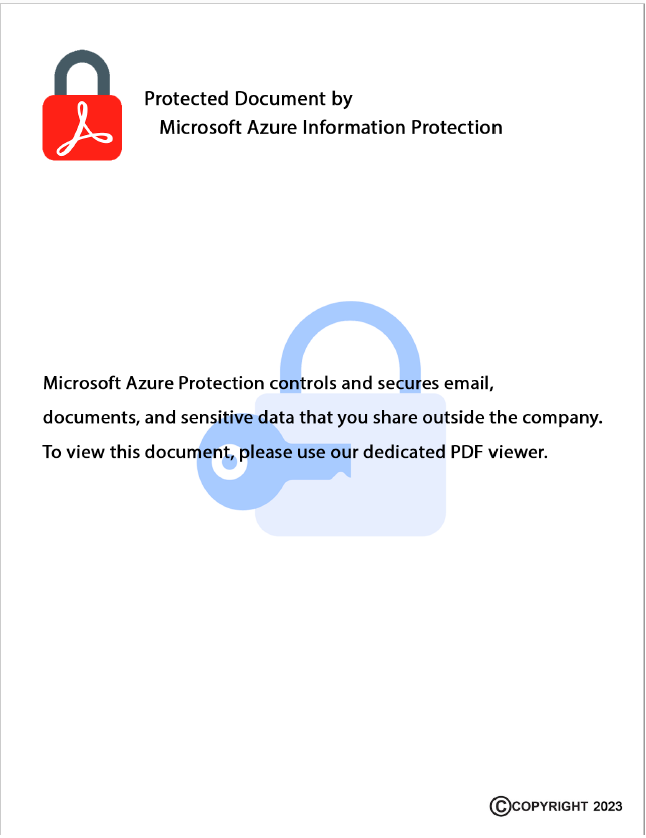
The download page includes a link to a PDF with instructions on how to disable macOS security features. 5/9 



Also interesting: it seems Salesforce credentials are phished before landing on the download page. 7/9 

IoCs
saleforces-it[.]com
saleforces.s3-accelerate.amazonaws[.]com
3A72E433D2F5CC355BF6AA921D194C10F6CE6A71 SalesforceUpdate.dmg
5A1F7A22BE5C284D8FC419F022626F04D1EA0C7C salesforceupdate.exe
0E1BA414B40D783E17DB92C09F8CE8600C03DDA1 scupdate.exe
8/9
saleforces-it[.]com
saleforces.s3-accelerate.amazonaws[.]com
3A72E433D2F5CC355BF6AA921D194C10F6CE6A71 SalesforceUpdate.dmg
5A1F7A22BE5C284D8FC419F022626F04D1EA0C7C salesforceupdate.exe
0E1BA414B40D783E17DB92C09F8CE8600C03DDA1 scupdate.exe
8/9
1C8A2D3AB764BF7D72B8CB869C33767707A4E50C SalesForceUpdate
D73FB7BA6A459ABFD382842A3384EC25EEA65196 yVcq.js
69780BA5E6DD19D0CB3F35E749273123393B464D salesforceupdate-arm
EFE8D0545D9629E424BBCECE73A21FD91E4E5635 salesforceupdate-amd
9/9
D73FB7BA6A459ABFD382842A3384EC25EEA65196 yVcq.js
69780BA5E6DD19D0CB3F35E749273123393B464D salesforceupdate-arm
EFE8D0545D9629E424BBCECE73A21FD91E4E5635 salesforceupdate-amd
9/9
• • •
Missing some Tweet in this thread? You can try to
force a refresh