
Security research and breaking news straight from ESET Research Labs.
2 subscribers
How to get URL link on X (Twitter) App


 PromptLock leverages Lua scripts generated from hard-coded prompts to enumerate the local filesystem, inspect target files, exfiltrate selected data, and perform encryption. These Lua scripts are cross-platform compatible, functioning on #Windows, #Linux, and #macOS 2/6
PromptLock leverages Lua scripts generated from hard-coded prompts to enumerate the local filesystem, inspect target files, exfiltrate selected data, and perform encryption. These Lua scripts are cross-platform compatible, functioning on #Windows, #Linux, and #macOS 2/6 




 Using Windows’ notification callbacks, the driver component monitors new browsers or tabs being opened. Under certain conditions, the adware will use various techniques to inject shellcode into browser processes to load network-tampering libraries. 2/7
Using Windows’ notification callbacks, the driver component monitors new browsers or tabs being opened. Under certain conditions, the adware will use various techniques to inject shellcode into browser processes to load network-tampering libraries. 2/7 

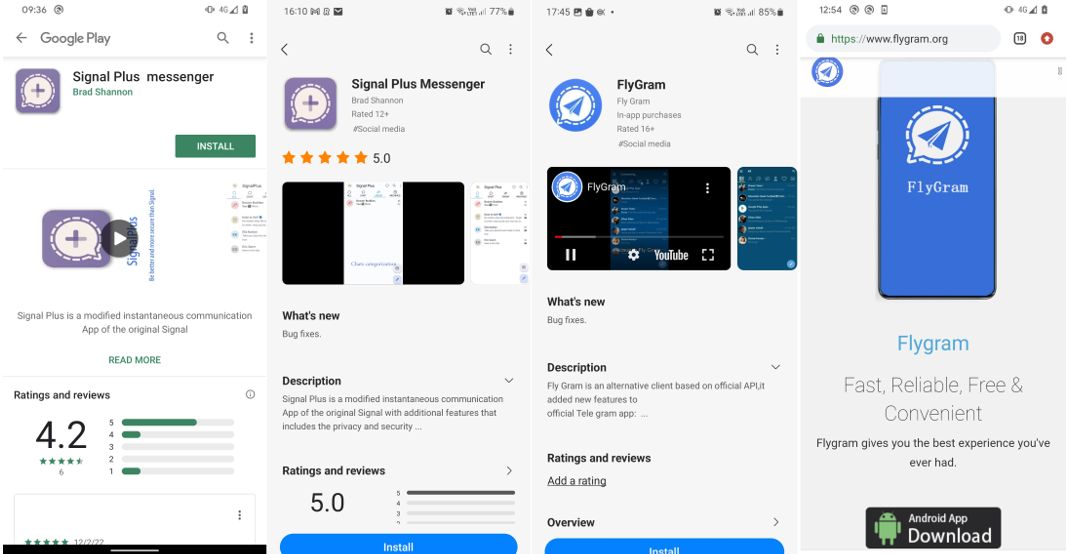
 Signal Plus Messenger and FlyGram were built by merging the BadBazaar espionage code, previously used to target #Uyghurs and other #Turkic minorities, into the respective base app’s code. 2/9
Signal Plus Messenger and FlyGram were built by merging the BadBazaar espionage code, previously used to target #Uyghurs and other #Turkic minorities, into the respective base app’s code. 2/9

https://twitter.com/jbradley89/status/1649434597309005824
 @pkalnai @michalmalik The archive contains a fully functional – but malicious – PDF viewer, and a crafted “locked” PDF file. When the file is opened in the viewer, the malicious code is triggered. The functionality is very similar to the malware reported by @JamfSoftware. 2/7 jamf.com/blog/bluenorof…
@pkalnai @michalmalik The archive contains a fully functional – but malicious – PDF viewer, and a crafted “locked” PDF file. When the file is opened in the viewer, the malicious code is triggered. The functionality is very similar to the malware reported by @JamfSoftware. 2/7 jamf.com/blog/bluenorof…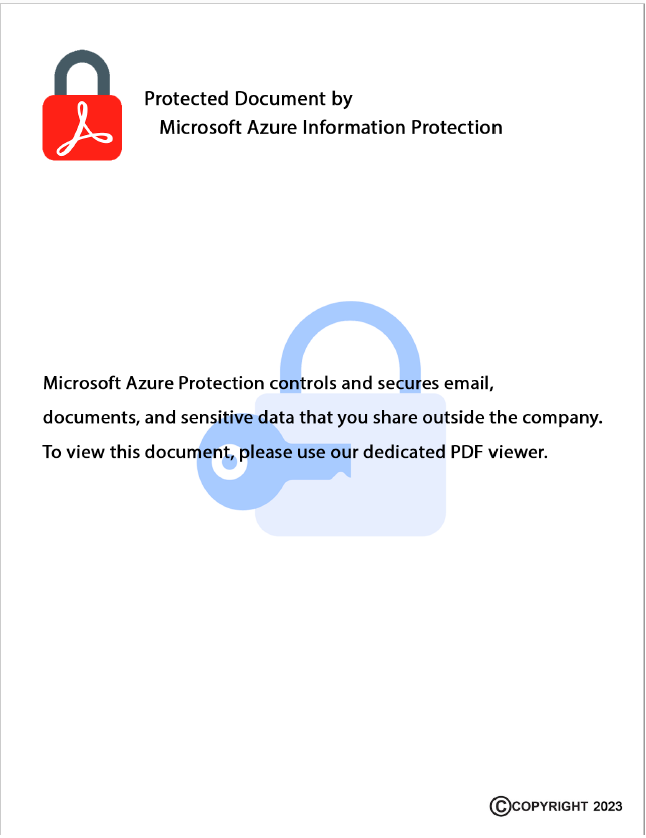




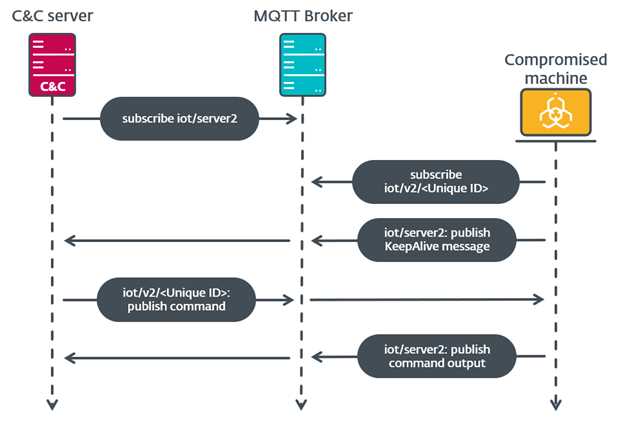
 A sample of MQsTTang was identified by @Unit42_Intel on 2023-02-17. As stated in that thread, the backdoor uses the legitimate MQTT broker 3.228.54.173. This has the benefit of hiding their actual C&C servers from victims and analysts.
A sample of MQsTTang was identified by @Unit42_Intel on 2023-02-17. As stated in that thread, the backdoor uses the legitimate MQTT broker 3.228.54.173. This has the benefit of hiding their actual C&C servers from victims and analysts. https://twitter.com/Unit42_Intel/status/16266137227004723202/5



 This phenomenon was caused by the prevalence of the web skimmer JS/Spy.Banker, also known as #Magecart. Throughout the year, it consistently accounted for about three-fourths of banking malware detections. It was also the third most detected infostealer overall in T3 2022. 2/4
This phenomenon was caused by the prevalence of the web skimmer JS/Spy.Banker, also known as #Magecart. Throughout the year, it consistently accounted for about three-fourths of banking malware detections. It was also the third most detected infostealer overall in T3 2022. 2/4

https://twitter.com/threatinsight/status/1623269199098306561In their February 2022 espionage campaign, attackers delivered a LUA downloader that installed #AHKBOT / #SunSeed AutoHotkey, the same implant used in recent crimeware campaigns. 2/5





 The RAT has extensive capabilities like exfiltrating SMS, call logs, contact list, photos, clipboard, files with particular extensions, record phone calls, take pictures, etc. Exfiltrated data is encrypted and uploaded to attacker’s server. 2/4
The RAT has extensive capabilities like exfiltrating SMS, call logs, contact list, photos, clipboard, files with particular extensions, record phone calls, take pictures, etc. Exfiltrated data is encrypted and uploaded to attacker’s server. 2/4 

 @_CERT_UA Its authors make multiple references to Monsters, Inc., the 2001 movie by Pixar. The ransom note (SullivanDecryptsYourFiles.txt) shows the authors impersonate James P. Sullivan, the main character of the movie, whose job is to scare kids. 2/9
@_CERT_UA Its authors make multiple references to Monsters, Inc., the 2001 movie by Pixar. The ransom note (SullivanDecryptsYourFiles.txt) shows the authors impersonate James P. Sullivan, the main character of the movie, whose job is to scare kids. 2/9



 Pivoting on the certificate, we found genuine VMPsoft binaries and a sample of SysUpdate signed and packed with VMProtect. Since LuckyMouse rarely use VMProtect, it is possible that they also stole VMProtect packer when they got the digi certificate. 2/4
Pivoting on the certificate, we found genuine VMPsoft binaries and a sample of SysUpdate signed and packed with VMProtect. Since LuckyMouse rarely use VMProtect, it is possible that they also stole VMProtect packer when they got the digi certificate. 2/4 








https://twitter.com/ESETresearch/status/1549329017853067264The Windows and macOS malware variants are not copycats of each other, but share the following similarities: ➡️ 2/9