
If you utilise API hashing in your #malware or offensive security tooling. Try rotating your API hashes. This can have a significant impact on #detection rates and improve your chances of remaining undetected by AV/EDR. See below for an example with a Bind Shell vs #Virustotal. 





Since API hashing can be confusing, most attackers won't rotate their hashes with each iteration of malware. Those same hashes can be a reliable detection mechanism if you can recognize them in code.
Luckily finding these hashes isn't too difficult, just look for random hex values prior to a "call rbp".
If you're unsure whether the value is an API hash, just google it and see if you get any hits. Most of the time, identification can be a simple google search away.

If you're unsure whether the value is an API hash, just google it and see if you get any hits. Most of the time, identification can be a simple google search away.

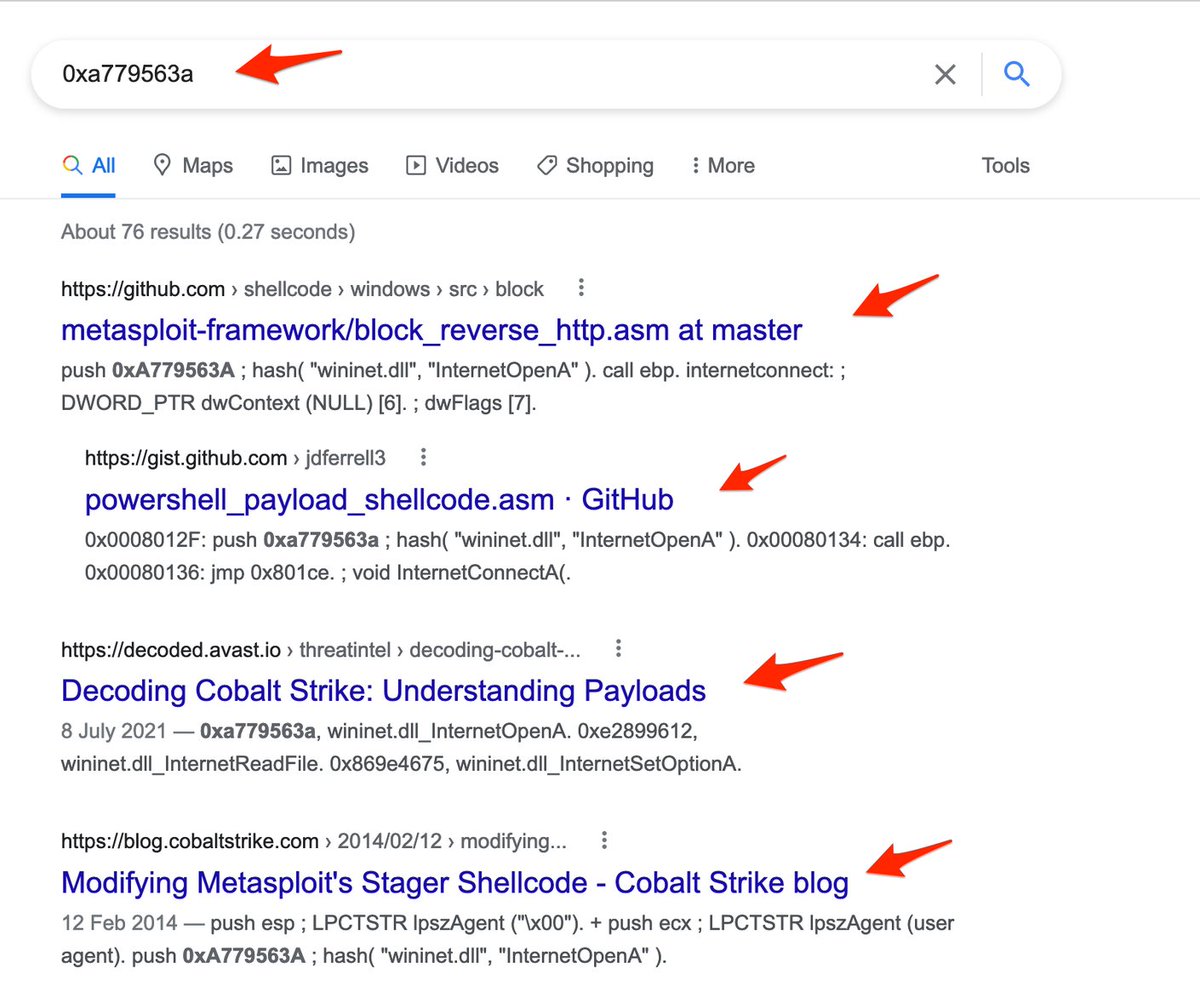
Once you've learnt to recognize these hashes, you can implement them in #yara rules to aid with #detection and identification of malware. Avast has a great blog on this with some examples. They've explained a lot of this better than I can.
decoded.avast.io/threatintel/de…
decoded.avast.io/threatintel/de…
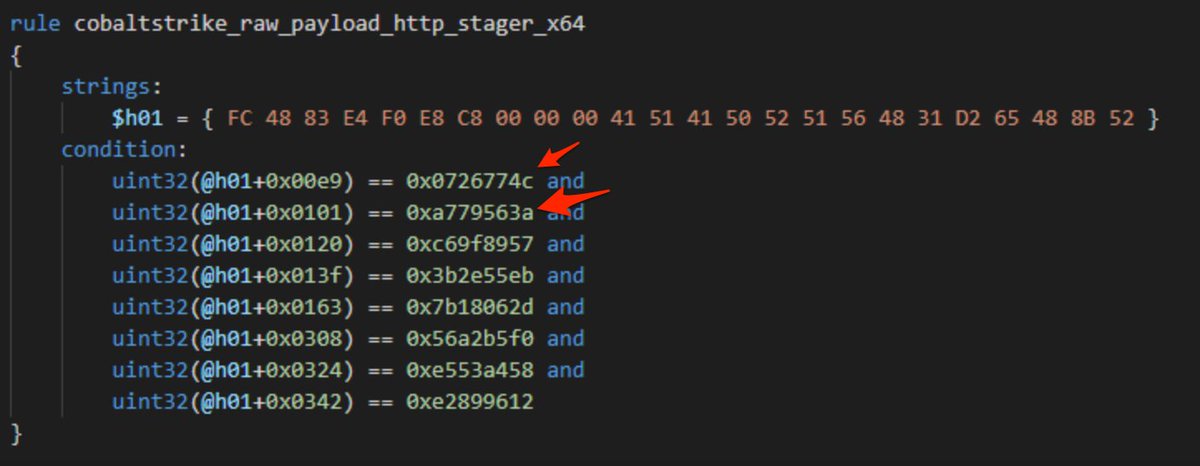
If you're interested in learning more about API hashing and how to better evade and detect it, I've written a blog about it here.
huntress.com/blog/hackers-n…
huntress.com/blog/hackers-n…
Worth noting that API hashes won't always exactly look like this, but this is a common format often used in #metasploit and #cobaltstrike shellcode.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



