#ChromeLoader #malware persists via obfuscated content stored in the registry. Here's how to decode it using #Cyberchef.
1/


1/



2/ First, locate a scheduled task containing content that you suspect to be chromeloader malware. Decode the first stage using "From Base64" and "Remove Null Bytes". This will give you the first stage loader in its #decoded form. 

3/ Next, check the location of the next stage in the registry. This should be near the beginning of the code. 

4/ Use the value from the previous tweet to locate stage 2 in the registry. Copy this entire base64 value into #cyberchef. Noting that if you decode it using base64, you will get junk. 



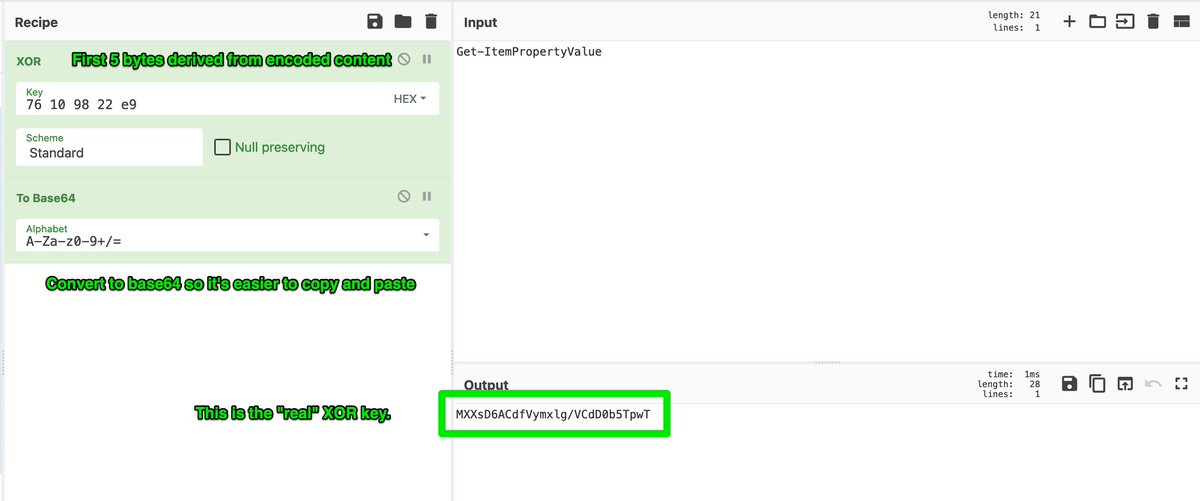
5/ Now comes a bit of a tricky part, we need to generate an XOR key to decode the stage2 payload. To do that, we must XOR the first 5 bytes of the second payload, with the string "Get-ItemPropertyValue" 

6/ We can see what that tricky part looks like here. Note that this XOR key is the same as the 5 bytes we obtained before. If done correctly, we now have the "real" XOR key. 
7/ Now that we've generated a key, we can finally decode the second stage malware. Noting that the first 5 bytes are thrown away after the key is generated, so we will need to implement that in our cyberchef recipe. 

8/ Here, we can see our XOR key used to decode the #malware. This results in the malicious chrome extension that is compiled, deployed and installed via powershell commands. 

9/ There is one final encoded section which follows a similar pattern, but without the use of "Get-ItemPropertyValue" to generate the XOR key. 

10/ To decode that last part, just take the 5 bytes as we did before and use them directly as an XOR key. No need to throw away the first 5 bytes this time. 



11/ There's a lot more to this #chromeloader #malware outside of the decoding, however I won't go into them here since there are already well documented by @redcanary and @Unit42_Intel. You can read about them here.
unit42.paloaltonetworks.com/chromeloader-m…
redcanary.com/blog/chromeloa…
unit42.paloaltonetworks.com/chromeloader-m…
redcanary.com/blog/chromeloa…
• • •
Missing some Tweet in this thread? You can try to
force a refresh