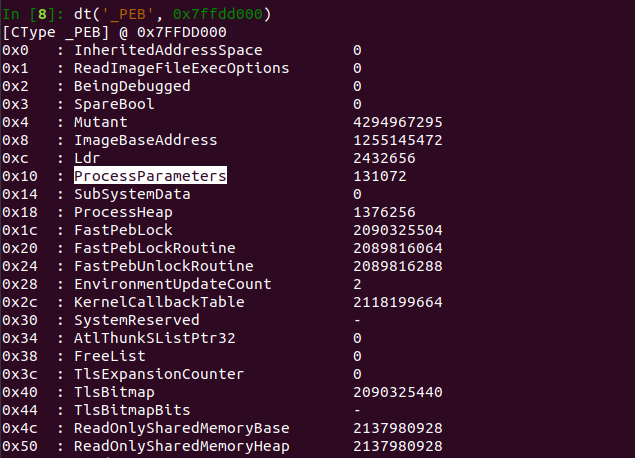
1\ #DFIR: How to detect Linux Timestomping
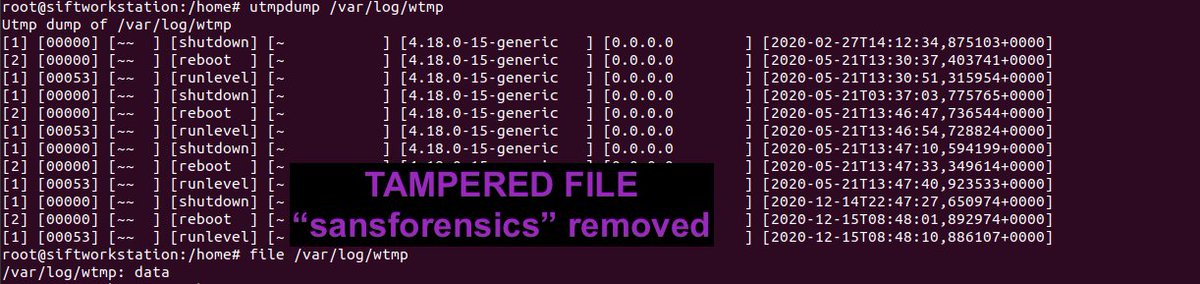
Analyse the entries in these two files:
> filesystem.db
> filesystem.db-wal
Most writeups focus on detecting the use of "touch". But you can timestomp without using "touch". 😈
Check out my blog below 👇
inversecos.com/2022/08/detect…
Analyse the entries in these two files:
> filesystem.db
> filesystem.db-wal
Most writeups focus on detecting the use of "touch". But you can timestomp without using "touch". 😈
Check out my blog below 👇
inversecos.com/2022/08/detect…
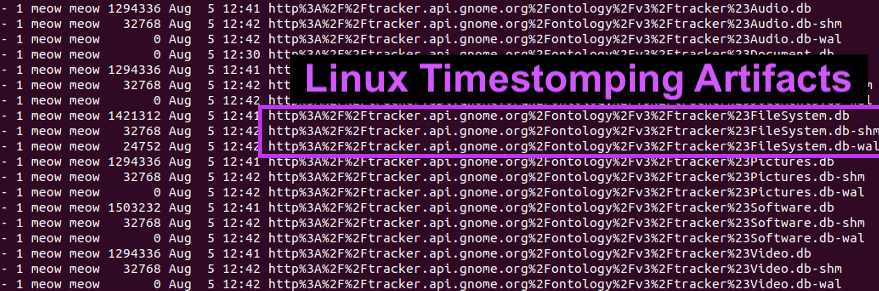
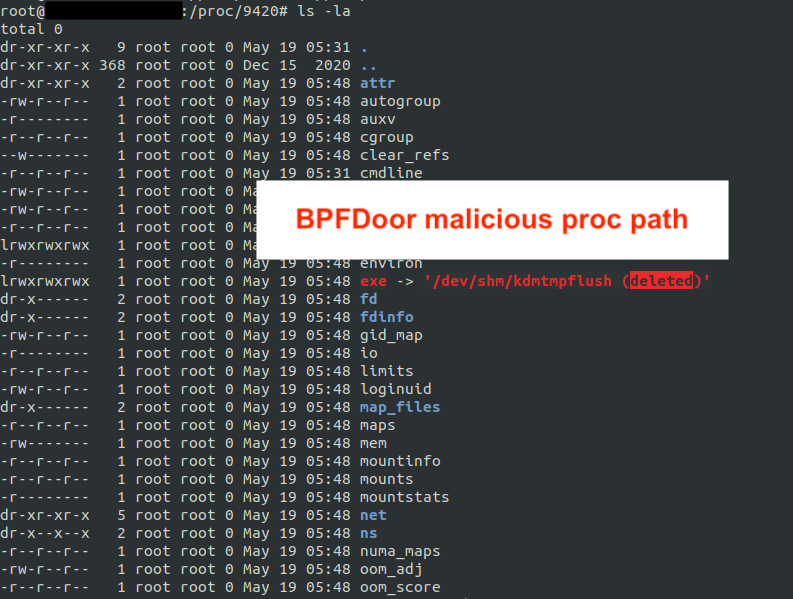
2\ The file "filesystem.db" (enabled by default) tracks:
> fileCreated time
> fileLastAccessed time
Look for discrepancies in the fileCreated time in this DB file vs the times that "stat" show on a file.
There's also a correlating WAL that contains uncommitted data :3
> fileCreated time
> fileLastAccessed time
Look for discrepancies in the fileCreated time in this DB file vs the times that "stat" show on a file.
There's also a correlating WAL that contains uncommitted data :3
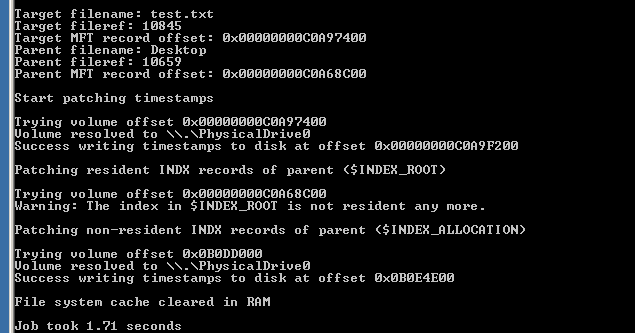
3\ As you can see, this has caught an instance of timestomping where you can observe the creation time is after the access time.
You can query the db using this command:
sqlite3 *filesystem.db .dump | grep <filename>


You can query the db using this command:
sqlite3 *filesystem.db .dump | grep <filename>



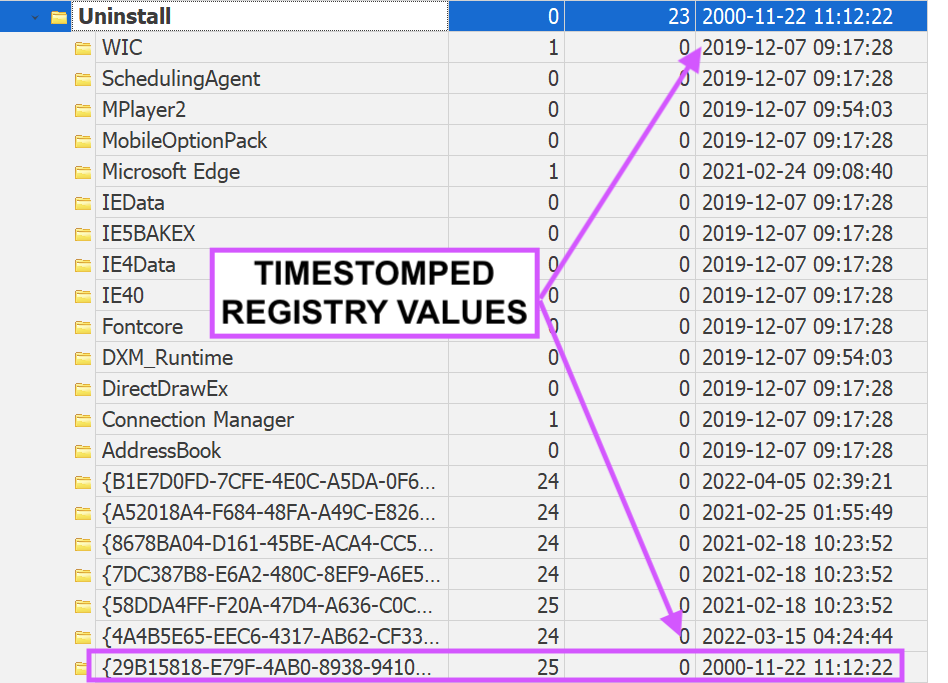
4\ To make things juicier. Every time a file is created, two entries are pushed into TWO tables inside FileSystem.db:
> Nfo:FileDataObject
> Nie:DataObject
Across both of these tables, they track:
> fileCreated
> fileLastAccessed
> fileLastModified

> Nfo:FileDataObject
> Nie:DataObject
Across both of these tables, they track:
> fileCreated
> fileLastAccessed
> fileLastModified


5\ The blog covers how to timestomp without using "touch" and some other detection considerations :)
feet pics coming soon too... JOKEEEESSSSSSS
MUAHAHAHAHAA WILL NEVER SHOW U MY FEET NOW THAT I KNOW WHAT URE THINKING
xD xD xD
unless... 👉👈
feet pics coming soon too... JOKEEEESSSSSSS
MUAHAHAHAHAA WILL NEVER SHOW U MY FEET NOW THAT I KNOW WHAT URE THINKING
xD xD xD
unless... 👉👈
• • •
Missing some Tweet in this thread? You can try to
force a refresh