
How to get URL link on X (Twitter) App


 2\ In a joint report, Qihoo 360 and CVERC accused the NSA’s TAO unit of breaching China's Northwestern Polytechnical University in 2022 (a key institution in aerospace and defense research).
2\ In a joint report, Qihoo 360 and CVERC accused the NSA’s TAO unit of breaching China's Northwestern Polytechnical University in 2022 (a key institution in aerospace and defense research).

https://twitter.com/AzakaSekai_/status/17593260492620190252\ The iOS spyware requires no jailbreak.


 2\ In some instances (more on this) the session and tab files inside that folder show the webkit/chrome date for when the session was exited.
2\ In some instances (more on this) the session and tab files inside that folder show the webkit/chrome date for when the session was exited. 

 2\ The questions that I use to guide the analysis and prioritisation of analysis are:
2\ The questions that I use to guide the analysis and prioritisation of analysis are: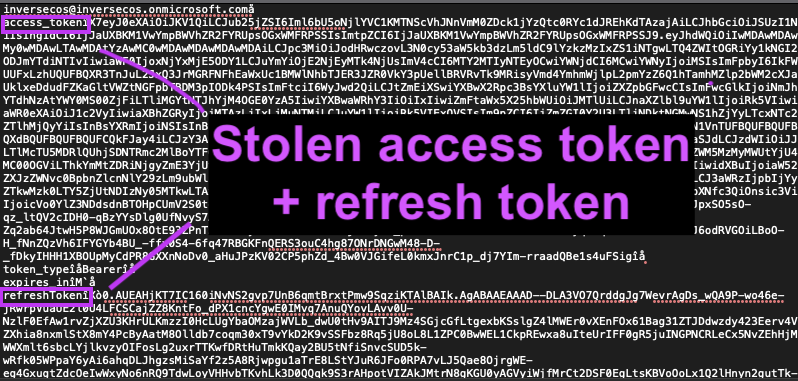
 2\ METHOD 1: Look for the OAuth redirect consent link in browser history and/or proxy logs.
2\ METHOD 1: Look for the OAuth redirect consent link in browser history and/or proxy logs.
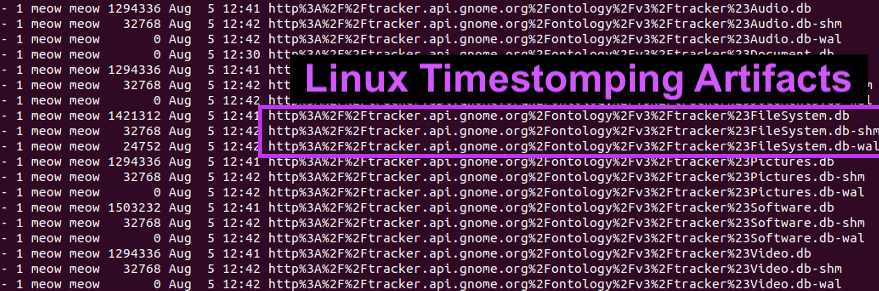
 2\ The file "filesystem.db" (enabled by default) tracks:
2\ The file "filesystem.db" (enabled by default) tracks:
 2\ EWS and other legacy auth is commonly abused by APT groups (when enabled).
2\ EWS and other legacy auth is commonly abused by APT groups (when enabled). 

 2\ Method 1: Zeroing entries in hex
2\ Method 1: Zeroing entries in hex

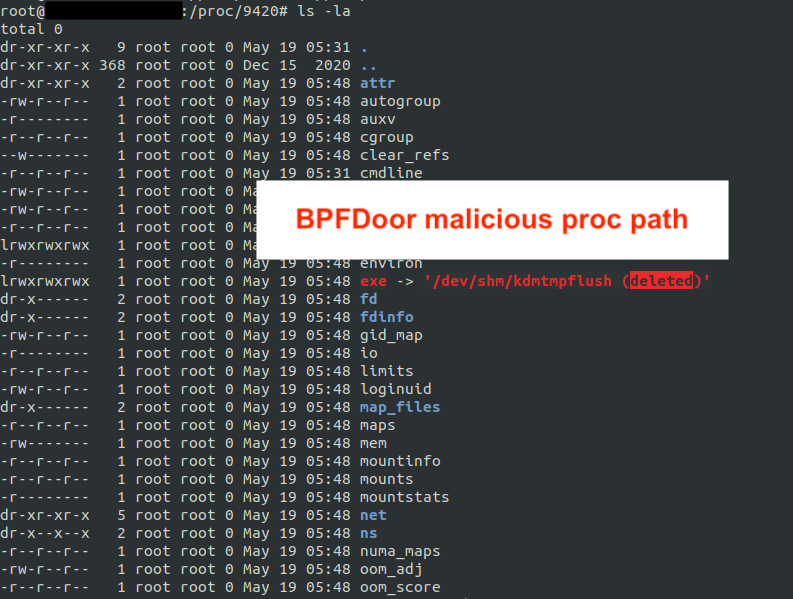

 2\ To recover/extract these binaries running in memory - you can copying them out from this location:
2\ To recover/extract these binaries running in memory - you can copying them out from this location:
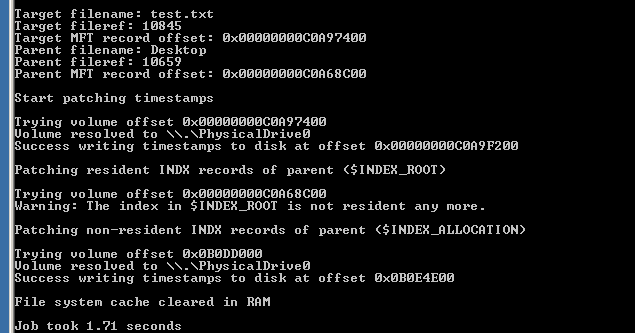
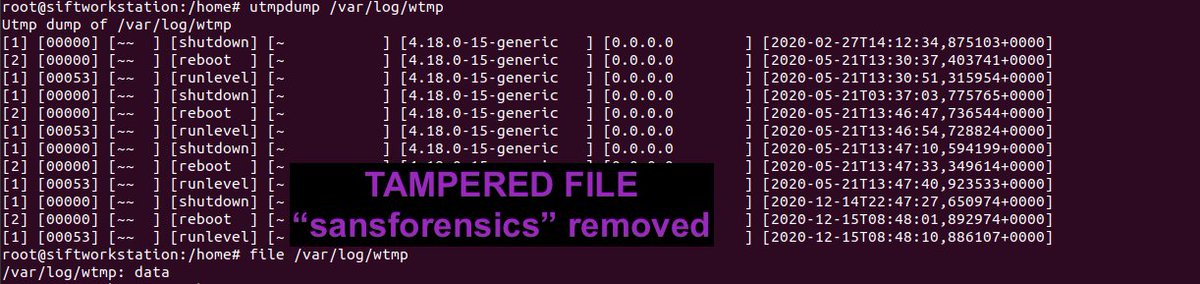
 2\ Most IR analysts are taught to detect timestomping using two methods:
2\ Most IR analysts are taught to detect timestomping using two methods: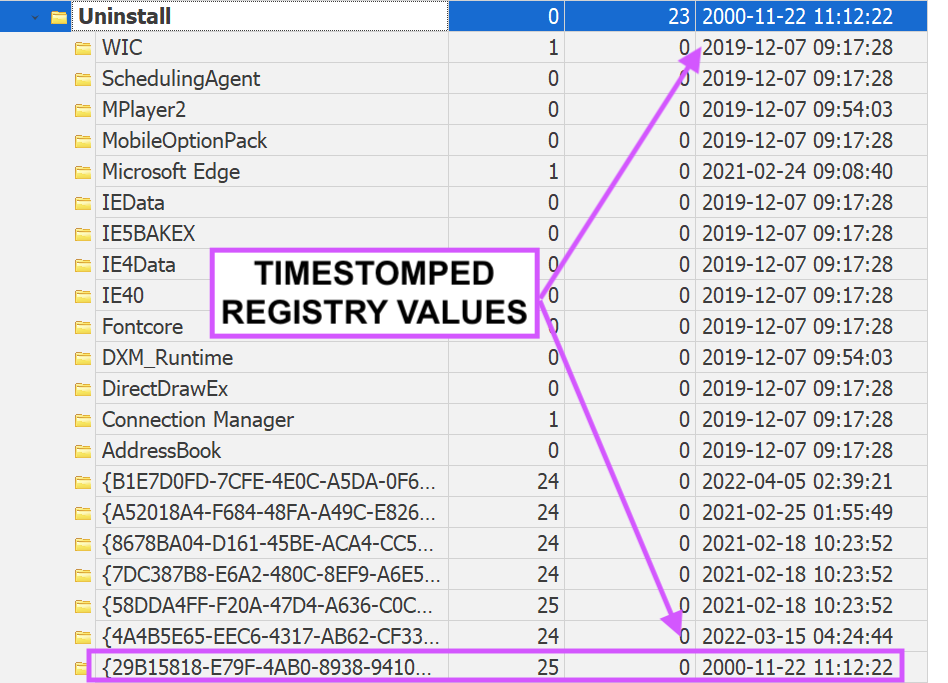


 2\ Why should you care?
2\ Why should you care? 
 2\ High level of how the technique works.....
2\ High level of how the technique works.....
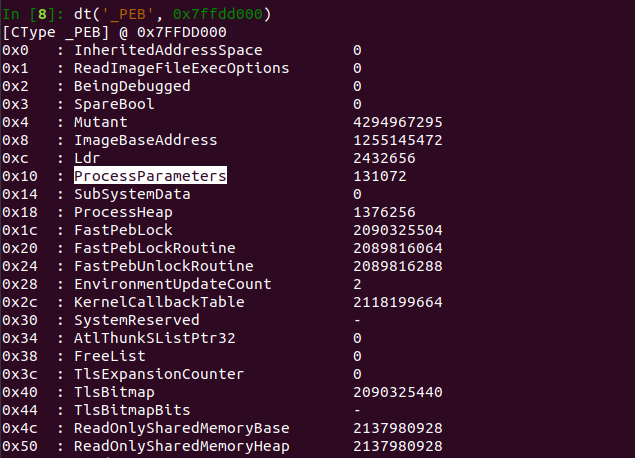

 2\ Each process in Windows is represented by an "EPROCESS" structure.
2\ Each process in Windows is represented by an "EPROCESS" structure. 

 2\ In light of the recent Emotet campaigns, make sure you check INetCache Outlook folder as it stores the attachments that were opened in Outlook.
2\ In light of the recent Emotet campaigns, make sure you check INetCache Outlook folder as it stores the attachments that were opened in Outlook. 
 2\ Following the process being started in a suspended state... (usually svchost.exe but who's counting). Then there are API calls to native/non native APIs:
2\ Following the process being started in a suspended state... (usually svchost.exe but who's counting). Then there are API calls to native/non native APIs:
 2\ In your iPhone the local.sqlite will render like this - as you can see I went to a grocery store 13 times. I was in lockdown don’t judge me.
2\ In your iPhone the local.sqlite will render like this - as you can see I went to a grocery store 13 times. I was in lockdown don’t judge me. 