NEW: Multiple attackers increase pressure on victims, complicate incident response
Sophos’ latest Active Adversary report explores the issue of organizations being hit multiple times by attackers...
1/17
Sophos’ latest Active Adversary report explores the issue of organizations being hit multiple times by attackers...
1/17
There’s a well-worn industry phrase about the probability of a cyberattack: “It’s not a matter of if, but when.”
Some of the incidents @Sophos recently investigated may force the industry to consider changing this: The question is not if, or when – but how many times? 2/17
Some of the incidents @Sophos recently investigated may force the industry to consider changing this: The question is not if, or when – but how many times? 2/17
In an issue we highlighted in our Active Adversary Playbook 2022, we’re seeing organizations being hit by multiple attackers. 3/17
Some attacks take place simultaneously; others are separated by a few days, weeks, or months. Some involve different kinds of malware, or double – even triple – infections of the same type. 4/17
Today, Sophos X-Ops is releasing our latest Active Adversary white paper: Multiple Attackers: A Clear and Present Danger. In the paper, we take a deep dive into the problem of multiple attackers, exploring how and why organizations are attacked several times. 5/17
Recent case studies from our Managed Detection and Response (#MDR) and Rapid Response (RR) teams provide insight into the how, and exploring cooperation and competition among threat actors helps explain the why. 6/17
Our key findings are:
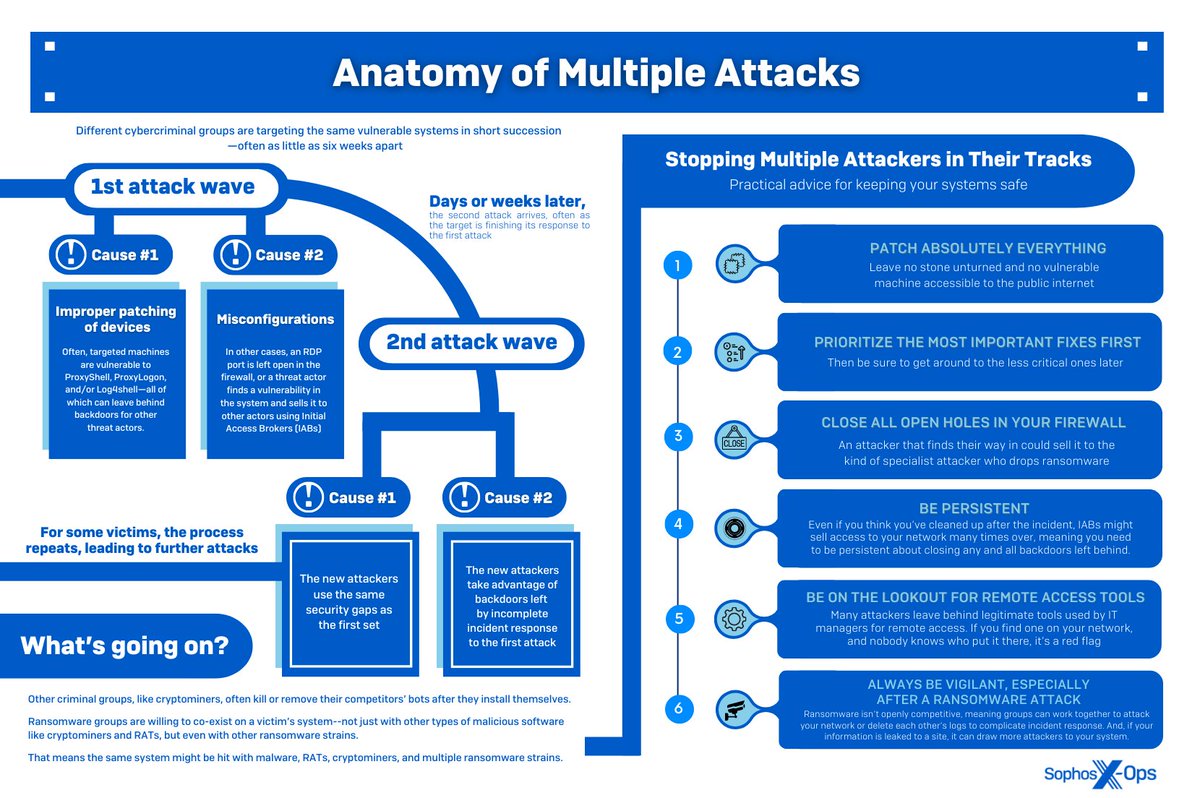
🔹The key drivers of multiple exploitations are vulnerabilities and misconfigurations going unaddressed after a first attack. 7/17
🔹The key drivers of multiple exploitations are vulnerabilities and misconfigurations going unaddressed after a first attack. 7/17
🔹Multiple attacks often involve a specific sequence of exploitation, especially after widespread vulnerabilities like ProxyLogon/ProxyShell are disclosed – with cryptominers arriving first, followed by wormable botnet builders, RATs, initial access brokers, and #ransomware. 8/17
🔹While some threat actors are interdependent (e.g., IABs later enabling ransomware), others, such as cryptominers, try to terminate rival #malware, and may even ‘close the door’ by patching vulnerabilities or disabling vulnerable services after gaining access. 9/17
🔹Historically, threat actors have been protective of their infections, to the extent of kicking rivals off compromised systems. 10/17
🔹Ransomware actors, despite occasionally tangling with each other, seem less concerned about competition, and sometimes adopt strategies which directly or indirectly benefit other groups. 11/17
🔹Certain features of the underground economy may enable multiple attacks – for instance, IABs reselling accesses, and ransomware leak sites providing data that other threat actors can later weaponize. 12/17
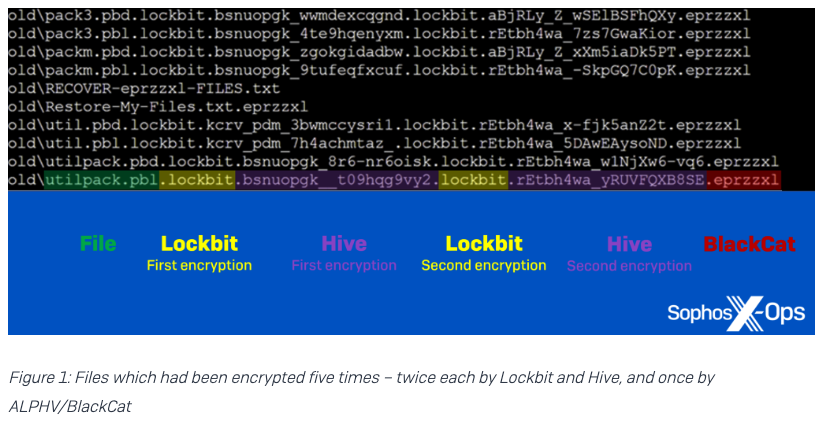
🔹Some of the case studies we analyze include a ransomware actor installing a backdoor which was later abused by a second ransomware group; and an incident where... 13/17
... one organization was attacked by three ransomware groups in the space of a few weeks, all using the same misconfigured RDP server to gain access. After the dust had settled, Sophos discovered some files which had been encrypted by all three groups. 14/17
At this stage there’s only anecdotal evidence to suggest that multiple attacks are on the rise, but, as Sophos’ Director of Incident Response, @AltShiftPrtScn, notes: 15/17
“This is something we’re seeing affecting more and more organizations, and it’s likely due to an increasingly crowded market for threat actors, as well as ransomware-as-a-service (RaaS) becoming more professionalized and lowering the bar to entry.” 16/17
Read more from @darkartlab and see our latest Active Adversary whitepaper, Multiple Attackers: A Clear and Present Danger...
news.sophos.com/en-us/2022/08/…
17/17
news.sophos.com/en-us/2022/08/…
17/17
• • •
Missing some Tweet in this thread? You can try to
force a refresh