
A task force composed of our CTU, SophosLabs, SecOps, and SophosAI teams working together towards one goal: protecting our customers.
2 subscribers
How to get URL link on X (Twitter) App






https://twitter.com/timhwang/status/1694812433242612159We asked around our team of researchers, and we found what might be the largest, most complex regex anyone has ever seen: 272,816 UTF-8 characters in length, created for our Data Loss Prevention product.









 Malicious macros in Office documents have long been a favorite tactic of threat actors. So Microsoft’s announcement in February 2022 that macros in documents originating from the internet would be blocked by default came as welcome news. 2/13
Malicious macros in Office documents have long been a favorite tactic of threat actors. So Microsoft’s announcement in February 2022 that macros in documents originating from the internet would be blocked by default came as welcome news. 2/13 

 Microsoft today released 83 patches for five product families – Windows, Office, Sharepoint, Azure, and Visual Studio / .NET. It may feel as if something is missing in that list. 2/8
Microsoft today released 83 patches for five product families – Windows, Office, Sharepoint, Azure, and Visual Studio / .NET. It may feel as if something is missing in that list. 2/8


 Remember Follina, the MSDT issue that rolled onstage in late May? Turns out that vulnerability (CVE-2022-30190) has a cousin. An *older* cousin. 2/6
Remember Follina, the MSDT issue that rolled onstage in late May? Turns out that vulnerability (CVE-2022-30190) has a cousin. An *older* cousin. 2/6
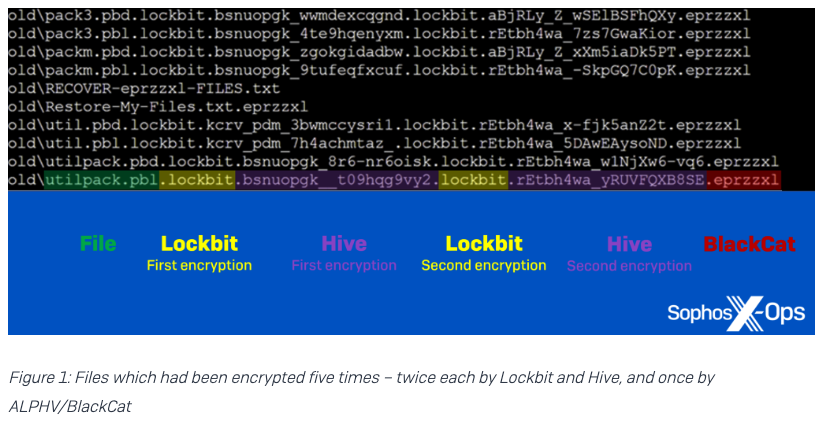
 In May 2022, an automotive supplier was hit with three separate ransomware attacks. All three threat actors abused the same misconfiguration – a firewall rule exposing Remote Desktop Protocol (RDP) on a management server – but used different ransomware strains and tactics. 2/17
In May 2022, an automotive supplier was hit with three separate ransomware attacks. All three threat actors abused the same misconfiguration – a firewall rule exposing Remote Desktop Protocol (RDP) on a management server – but used different ransomware strains and tactics. 2/17 
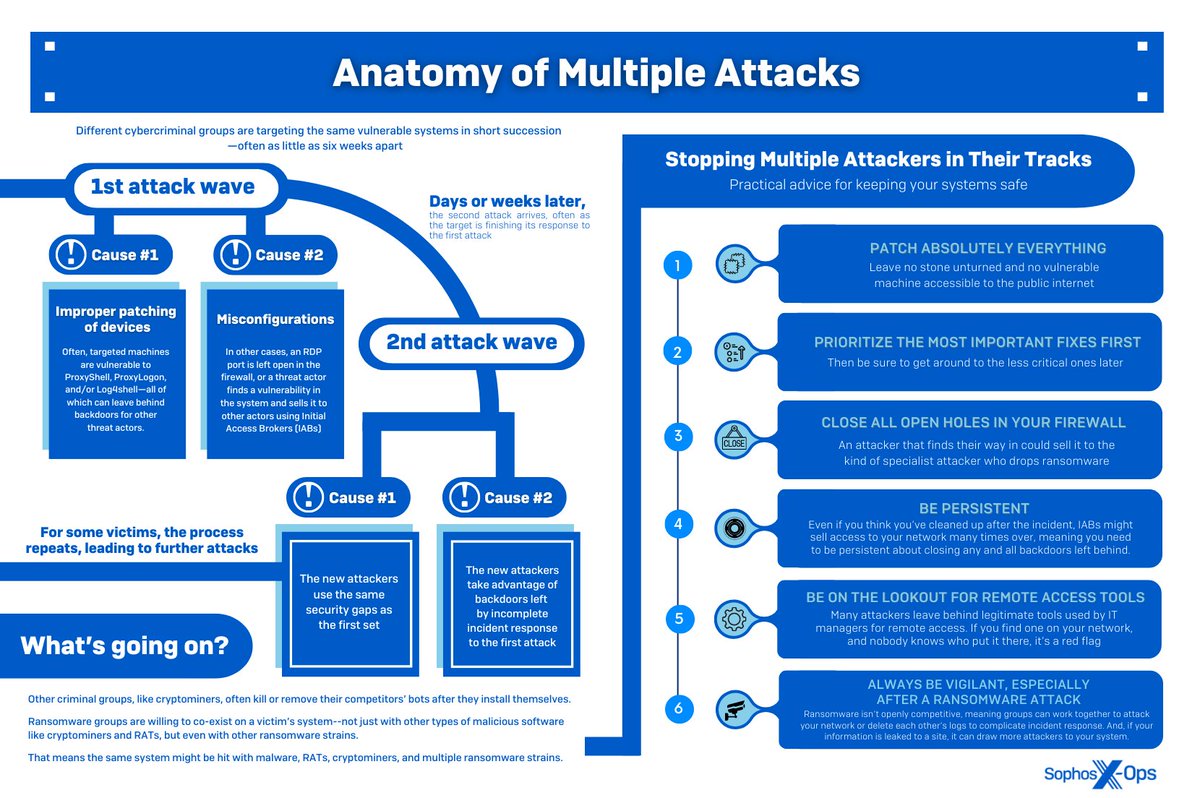
 There’s a well-worn industry phrase about the probability of a cyberattack: “It’s not a matter of if, but when.”
There’s a well-worn industry phrase about the probability of a cyberattack: “It’s not a matter of if, but when.” 
 Researchers can set alerts in Virustotal to flag when a file of interest gets submitted. I get periodic bursts of these -40444 #maldocs, but there was something notable about the document titles in this batch last week: They all parrot specific Russian disinformation topics. 2/16
Researchers can set alerts in Virustotal to flag when a file of interest gets submitted. I get periodic bursts of these -40444 #maldocs, but there was something notable about the document titles in this batch last week: They all parrot specific Russian disinformation topics. 2/16 

 Adversaries continue to abuse PowerShell to execute malicious commands and scripts. It's easy to understand its popularity among attackers: Not only is it present on all versions of Windows by default (and crucial to so many Windows applications that few disable it)... 2/19
Adversaries continue to abuse PowerShell to execute malicious commands and scripts. It's easy to understand its popularity among attackers: Not only is it present on all versions of Windows by default (and crucial to so many Windows applications that few disable it)... 2/19

 In the wake of December 2021 exposure of a remote code execution vulnerability (dubbed “Log4Shell”) in the ubiquitous Log4J Java logging library, we tracked widespread attempts to scan for and exploit the weakness—particularly among cryptocurrency mining bots. 2/14
In the wake of December 2021 exposure of a remote code execution vulnerability (dubbed “Log4Shell”) in the ubiquitous Log4J Java logging library, we tracked widespread attempts to scan for and exploit the weakness—particularly among cryptocurrency mining bots. 2/14


 Over the past few weeks, an up-and-coming ransomware family that calls itself Avos Locker has been ramping up attacks while making significant effort to disable endpoint security products on the systems they target. 2/16
Over the past few weeks, an up-and-coming ransomware family that calls itself Avos Locker has been ramping up attacks while making significant effort to disable endpoint security products on the systems they target. 2/16
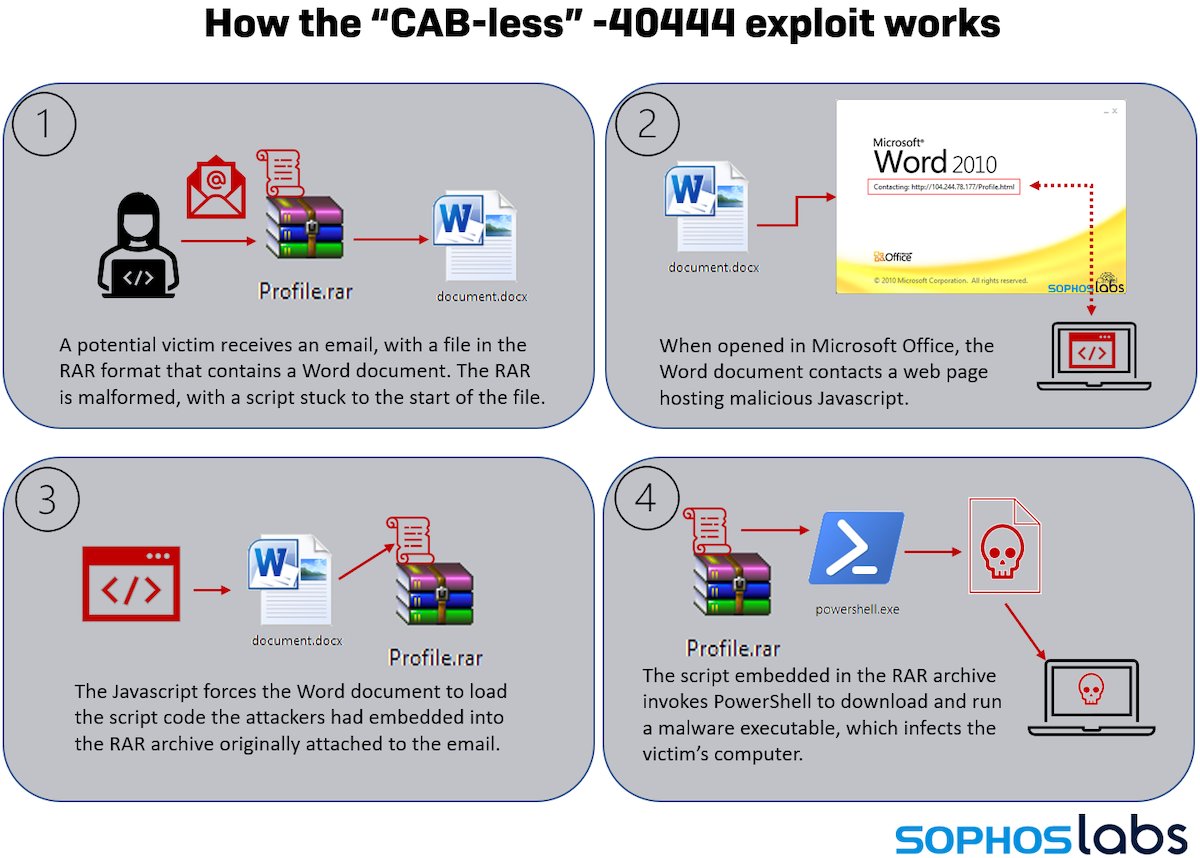
 In September, Microsoft published mitigation steps and released a patch to a serious bug (CVE-2021-40444) in the Office suite of products. Criminals began exploiting the Microsoft MSHTML Remote Code Execution Vulnerability at least a week before September’s Patch Tuesday... 2/11
In September, Microsoft published mitigation steps and released a patch to a serious bug (CVE-2021-40444) in the Office suite of products. Criminals began exploiting the Microsoft MSHTML Remote Code Execution Vulnerability at least a week before September’s Patch Tuesday... 2/11