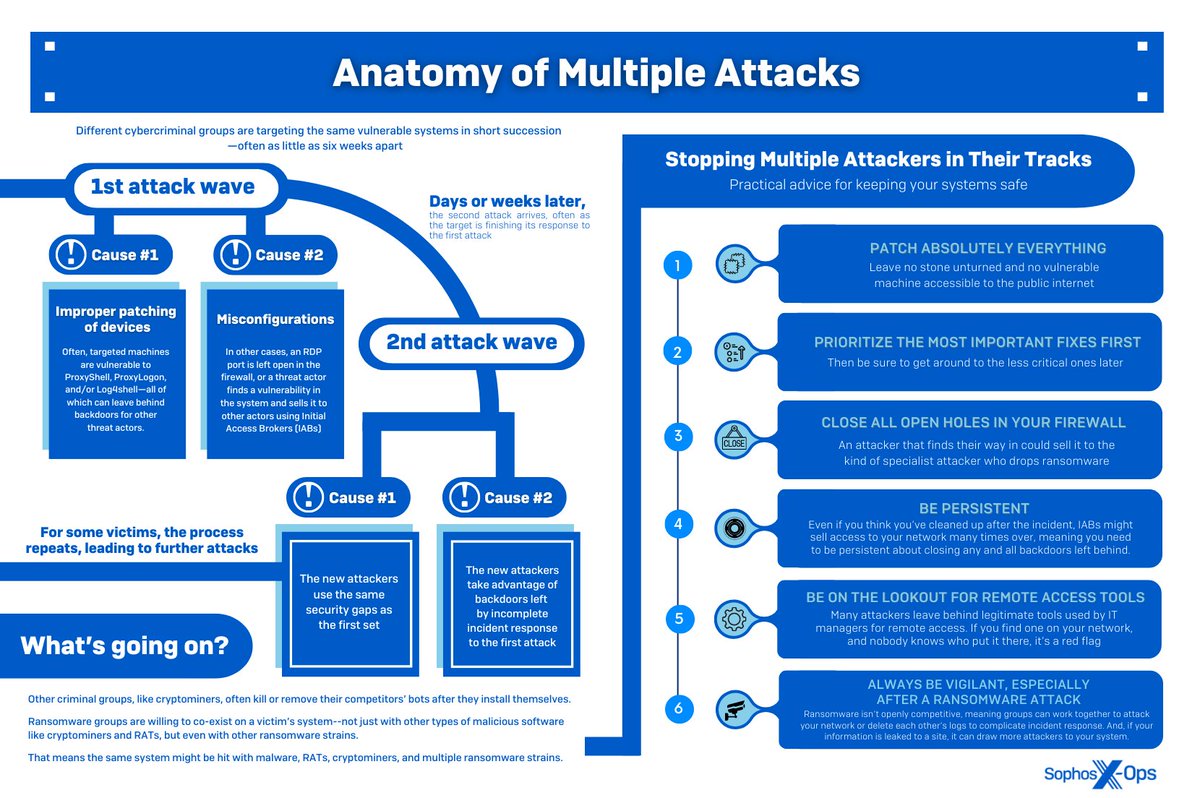
3 attackers, 2 weeks – 1 entry point...
Lockbit, Hive, and BlackCat attack an automotive supplier in this triple #ransomware attack.
After gaining access via RDP, all three threat actors encrypted files, in an investigation complicated by event log clearing and backups.
1/17
Lockbit, Hive, and BlackCat attack an automotive supplier in this triple #ransomware attack.
After gaining access via RDP, all three threat actors encrypted files, in an investigation complicated by event log clearing and backups.
1/17
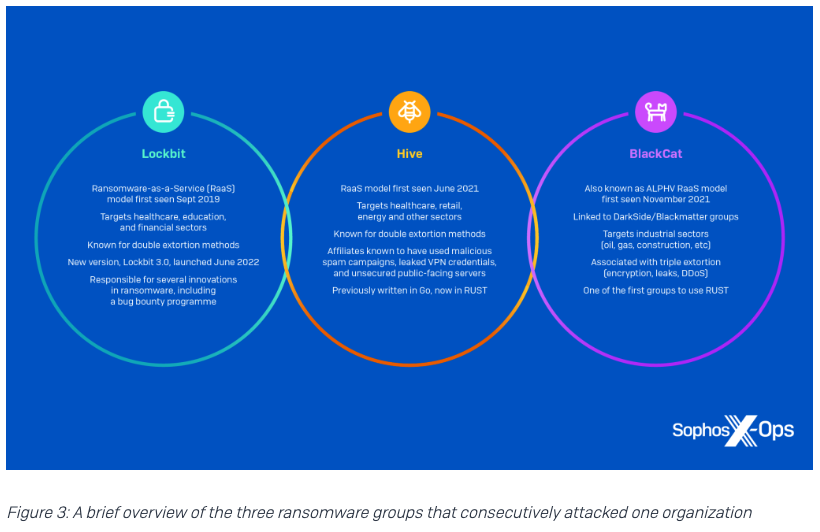
In May 2022, an automotive supplier was hit with three separate ransomware attacks. All three threat actors abused the same misconfiguration – a firewall rule exposing Remote Desktop Protocol (RDP) on a management server – but used different ransomware strains and tactics. 2/17 

The first ransomware group, identified as Lockbit, exfiltrated data to the Mega cloud storage service, used Mimikatz to extract passwords, and distributed their ransomware binary using PsExec. 3/17 

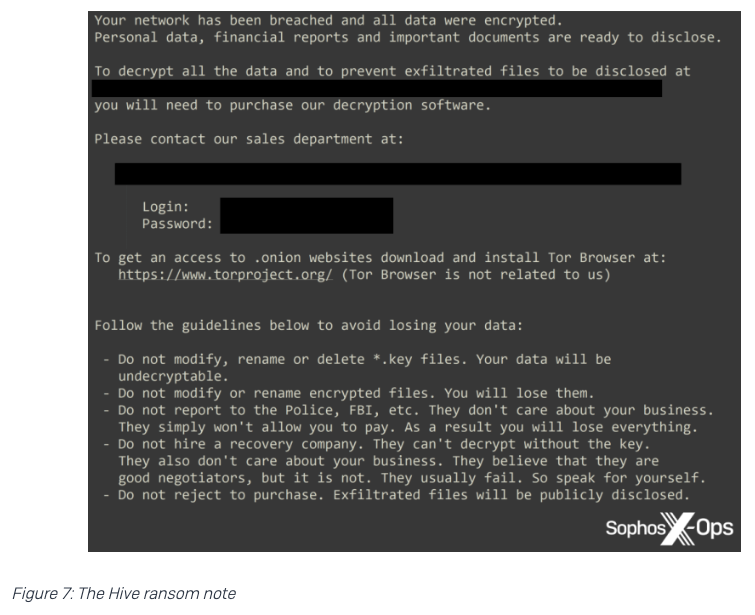
The second group, identified as Hive, used RDP to move laterally, before dropping their ransomware just two hours after the Lockbit threat actor. 4/17 
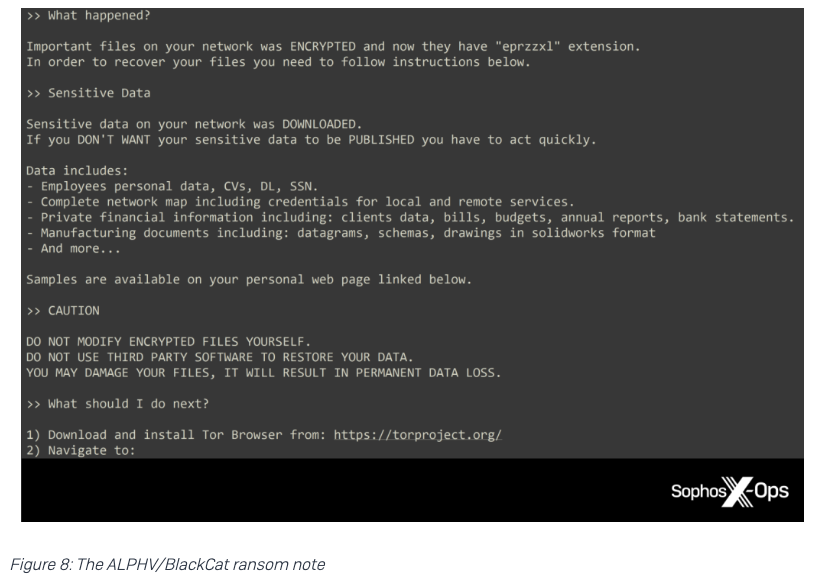
As the victim restored data from backups, an ALPHV/BlackCat affiliate accessed the network, installed Atera Agent (a legitimate remote access tool) to establish persistence, and exfiltrated data. 5/17 
Two weeks after the Lockbit and Hive attacks, the threat actor distributed their ransomware, and cleared Windows Event Logs.
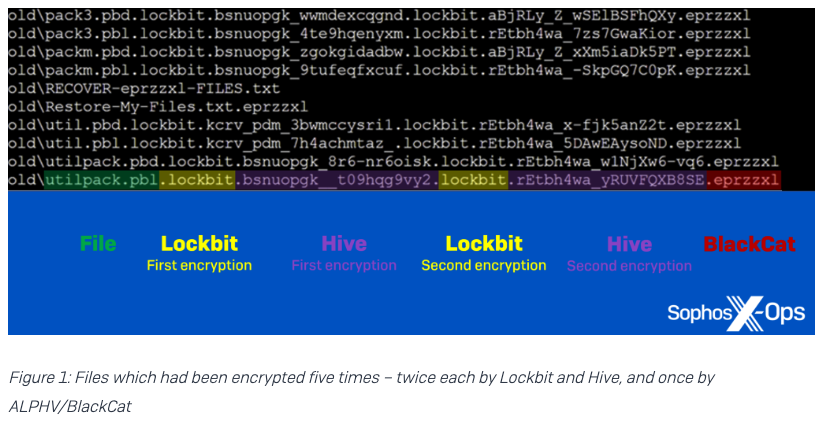
@Sophos’ Rapid Response (RR) team investigated, and found several files which had been encrypted multiple times – as many as five in some instances. 6/17
@Sophos’ Rapid Response (RR) team investigated, and found several files which had been encrypted multiple times – as many as five in some instances. 6/17
We’ve covered several dual ransomware attacks before – and recently investigated the phenomenon of multiple attacks more generally, as it’s something which appears to be increasingly common... 7/17
...but this is the first incident we’ve seen where three separate ransomware actors used the same point of entry to attack a single organization. 8/17
Check out a more detailed breakdown of the attacks that our team investigated in the article linked below. 9/17 
After the dust had settled, Sophos’ RR team found files that had been encrypted by all three ransomware groups. In fact, as shown in the screenshot below, some files had even been encrypted five times! 10/17
Because the Hive attack started 2 hours after Lockbit, the Lockbit ransomware was still running – so both groups kept finding files without the extension signifying that they were encrypted. 11/17
However, despite all three ransomware groups being known for ‘double extortion’ techniques (where, in addition to encrypting files, threat actors threaten to publish the victim’s data if the ransom is not paid), no information was published on any of the groups’ leak sites. 12/17
When it comes to defense, there are two elements: proactive (following security best practices to minimize the risk of being attacked), and reactive (how to recover quickly and safely if an attack does happen). 13/17
On the proactive side, our white paper on multiple attackers includes several learning points and best-practice guidance, including:
🔹Patch and investigate
🔹Lock down accessible services
🔹Practice segmentation and zero-trust 14/17
🔹Patch and investigate
🔹Lock down accessible services
🔹Practice segmentation and zero-trust 14/17
🔹Set and enforce strong passwords and multifactor authentication (MFA)
🔹Inventory your assets and accounts
🔹Install layered protection to block attackers at as many points as possible 15/17
🔹Inventory your assets and accounts
🔹Install layered protection to block attackers at as many points as possible 15/17
But once threat actors are inside a network, there’s not much that can be done to ‘stop the bleeding’ without having comprehensive Incident Response and remediation plans, and taking immediate action. 16/17
Sophos X-Ops has posted IOCs relating to the Lockbit, Hive, and BlackCat attacks covered in this report on our Github repository.
Read more from authors Linda Smith, Rajat Wason, and Syed Zaidi: news.sophos.com/en-us/2022/08/… 17/17
Read more from authors Linda Smith, Rajat Wason, and Syed Zaidi: news.sophos.com/en-us/2022/08/… 17/17
• • •
Missing some Tweet in this thread? You can try to
force a refresh