
Cobalt Strike ain't 💩
Let's chat about how to unravel Cobalt Strike and deny the adversary further access
As ALWAYS, I am showing you data so fresh out the kitchen it hasn't even been cleared by ThreatOps Director @MaxRogers5 👀🧑🍳 🧵
Let's chat about how to unravel Cobalt Strike and deny the adversary further access
As ALWAYS, I am showing you data so fresh out the kitchen it hasn't even been cleared by ThreatOps Director @MaxRogers5 👀🧑🍳 🧵
Cobalt Strike can often trigger AMSI alerts in Defender. The frustrating thing about AMSI alerts is that they don't tell you what the offending activity WAS.
The alert here was PowerShell based....so let's dig a lil deeper
The alert here was PowerShell based....so let's dig a lil deeper

Go collect C:\System32\winevt\Logs\Microsoft-Windows-PowerShell%4Operational.evtx , and go get my favourite tool - Chainsaw.
Take note your detection time (06:43).
Point chainsaw at your PwSh log, with this time
Take note your detection time (06:43).
Point chainsaw at your PwSh log, with this time

Cutting through the PowerShell evtx, we're shown the offending bit of PwSh that triggered the alert
It's the threat actor reaching out to a Chinese public IPv4, to download further tooling.
It's the threat actor reaching out to a Chinese public IPv4, to download further tooling.

Our nefarious friend wanted to pull their tools down from http://101[.]132[.]112[.]124:88/Horizon
Why don't we help them with that?
Via whatever secure means you care to deploy, let's pull their tools down to our analysis machine
Why don't we help them with that?
Via whatever secure means you care to deploy, let's pull their tools down to our analysis machine
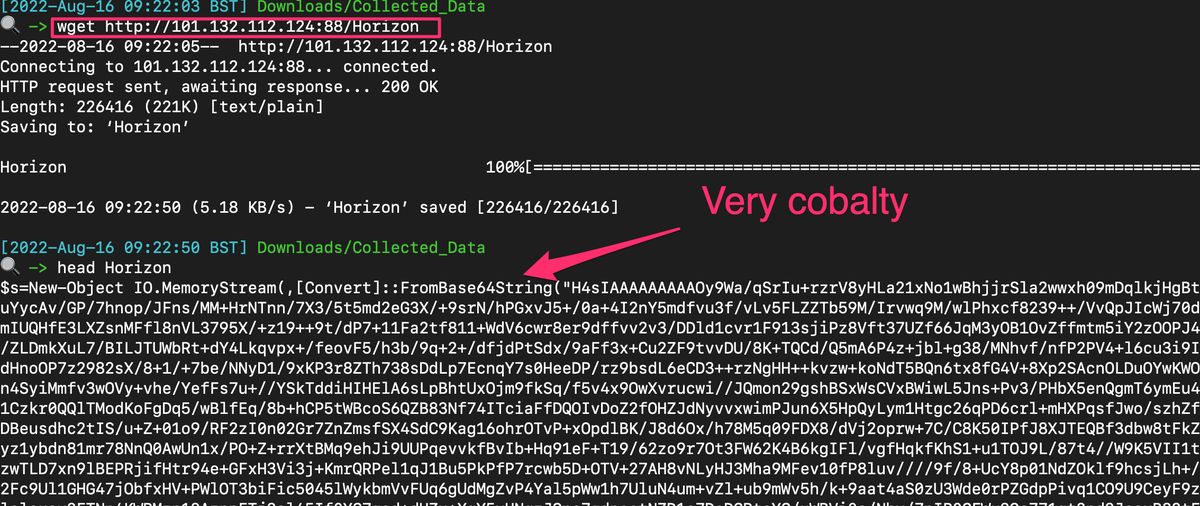
Carve out the big blob base64, and hop over to gchq.github.io/CyberChef
The results are not useful, yet, because we need to unravel some of the trivial obstacles Cobalt Strike has in store for us.
From base64, cyberchef advises us the resulting data is gzip.
The results are not useful, yet, because we need to unravel some of the trivial obstacles Cobalt Strike has in store for us.
From base64, cyberchef advises us the resulting data is gzip.

So add the gunzip option, and take a look at human readable data.
Though it's readable, we ain't done - notice there are more obfuscating obstacles to waste our time

Though it's readable, we ain't done - notice there are more obfuscating obstacles to waste our time


Extract out the second base64 , and open an additional cyberchef tab
Decoding this layer doesn't produce anything useful because there's an additional obstacle.
Scroll to the bottom of our previous script, which should be in the tab to your left.
Take a note of `xor` line

Decoding this layer doesn't produce anything useful because there's an additional obstacle.
Scroll to the bottom of our previous script, which should be in the tab to your left.
Take a note of `xor` line


Copy the number, pop back to your junk data tab, and pick the Xor option in cyberchef
Change it to decimal, and add the number you just copied.
Change it to decimal, and add the number you just copied.

From here, you'll start to have recognisable data!
The MZ header will make some people think mission accomplished. And I guess you can look at the strings to find some IoCs....
But what if we had an additional step that made our lives much easier?
The MZ header will make some people think mission accomplished. And I guess you can look at the strings to find some IoCs....
But what if we had an additional step that made our lives much easier?
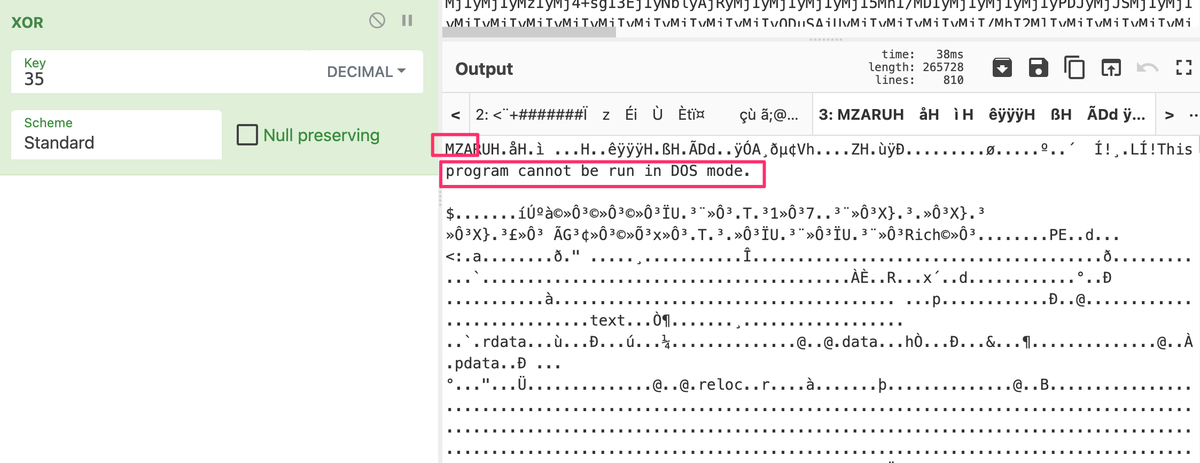
Save the output of our MZ data into a file - I called mine cobalt.exe, because my imagination knows no bounds
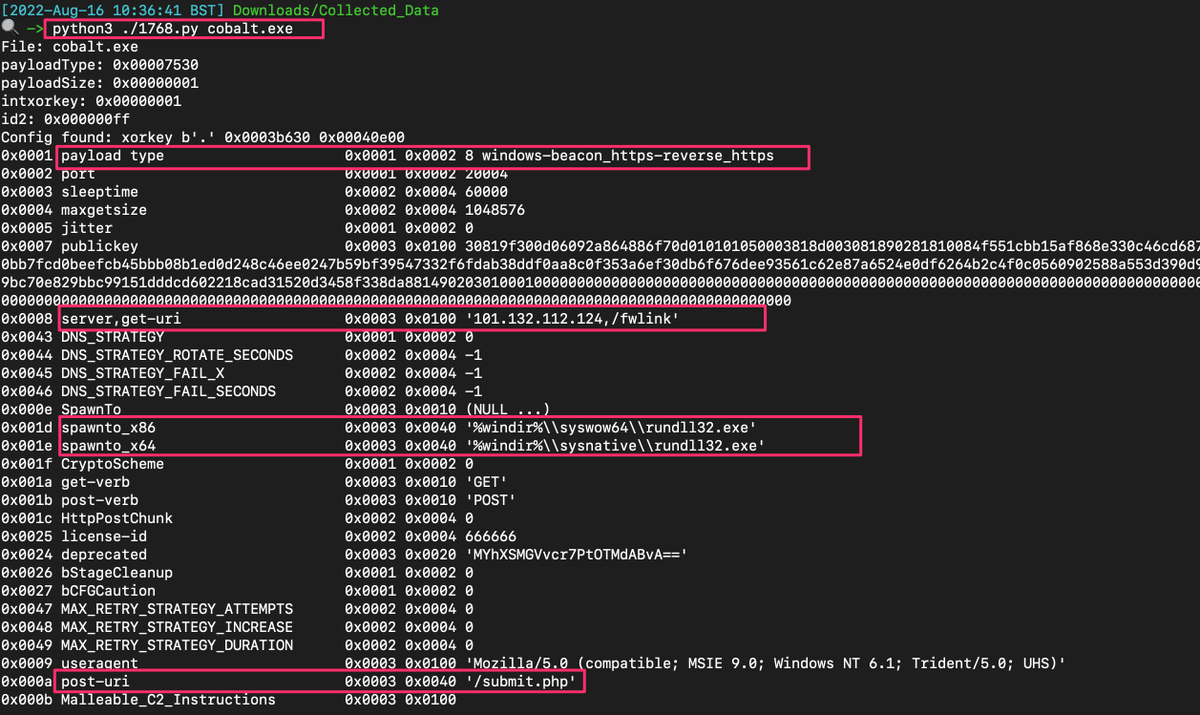
Now go and get @DidierStevens's 1768.py, a script aptly named after the boiling point of cobalt the metal.
raw.githubusercontent.com/DidierStevens/…

Now go and get @DidierStevens's 1768.py, a script aptly named after the boiling point of cobalt the metal.
raw.githubusercontent.com/DidierStevens/…


Simply point 1768.py at your cobalt strike file
The results are huge. We're told incredibly useful information that we can immediately action - for example, let's add the server IP to our firewall deny list
The results are huge. We're told incredibly useful information that we can immediately action - for example, let's add the server IP to our firewall deny list
I hope this has demystified any supposed complexities of Cobalt Strike.
It's just a tool. It comes with various obstacles that are a pain in the behind, but trivial to overcome; 161% tryna waste our time.
Thanks to @DidierStevens for the great script
👨🍳
It's just a tool. It comes with various obstacles that are a pain in the behind, but trivial to overcome; 161% tryna waste our time.
Thanks to @DidierStevens for the great script
👨🍳

• • •
Missing some Tweet in this thread? You can try to
force a refresh












