1\ #ThreatHunting: Detecting OAuth Token Theft in Azure / M365
This technique is STILL being abused by Chinese APT groups. This blog covers several methods of detecting this technique😈.
It's also a good reminder to always perform browser forensics ;)
inversecos.com/2022/08/how-to…
This technique is STILL being abused by Chinese APT groups. This blog covers several methods of detecting this technique😈.
It's also a good reminder to always perform browser forensics ;)
inversecos.com/2022/08/how-to…
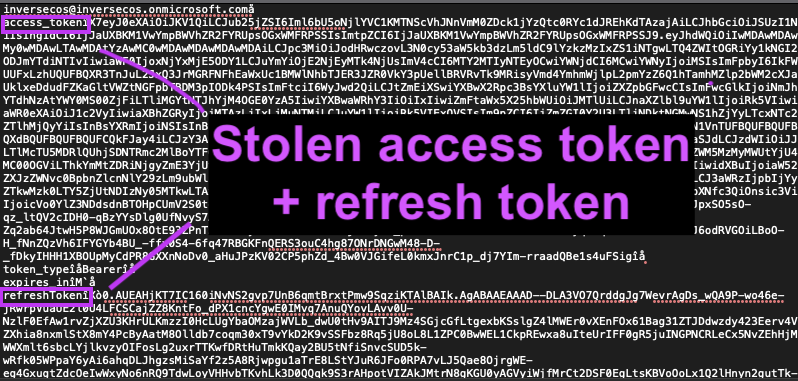
2\ METHOD 1: Look for the OAuth redirect consent link in browser history and/or proxy logs.
Take note of the following fields:
- client_id (malicious app id)
- redirect_uri (malicious domain)
- scope (API permissions requested)
Take note of the following fields:
- client_id (malicious app id)
- redirect_uri (malicious domain)
- scope (API permissions requested)

3\ Review permissions requested in the scope field (I'll show you where else to find these permissions in the logs).
Take note of these:
- User.Read
- User.ReadWrite
- User.ReadWrite.All
- Mail.ReadWrite
- Calendars.ReadWrite
- Files.ReadWrite
- User.Export.All
Take note of these:
- User.Read
- User.ReadWrite
- User.ReadWrite.All
- Mail.ReadWrite
- Calendars.ReadWrite
- Files.ReadWrite
- User.Export.All
4\ METHOD 2: Review Azure Audit Logs
Look for 3 log entries that will be created when a user authorises a malicious app. These are covered in the blog (too long to write into a tweet).
These logs will reveal:
> Malicious Object ID (important later)
> App name
> Permissions
Look for 3 log entries that will be created when a user authorises a malicious app. These are covered in the blog (too long to write into a tweet).
These logs will reveal:
> Malicious Object ID (important later)
> App name
> Permissions

5\ METHOD 3: Review Azure Sign-in Logs or UAL
These will show logons into a user account originating from the malicious application.
It's important you do Method 2 before Method 3 so you can get the application object ID and application name to make this high-fidelity ;)
These will show logons into a user account originating from the malicious application.
It's important you do Method 2 before Method 3 so you can get the application object ID and application name to make this high-fidelity ;)

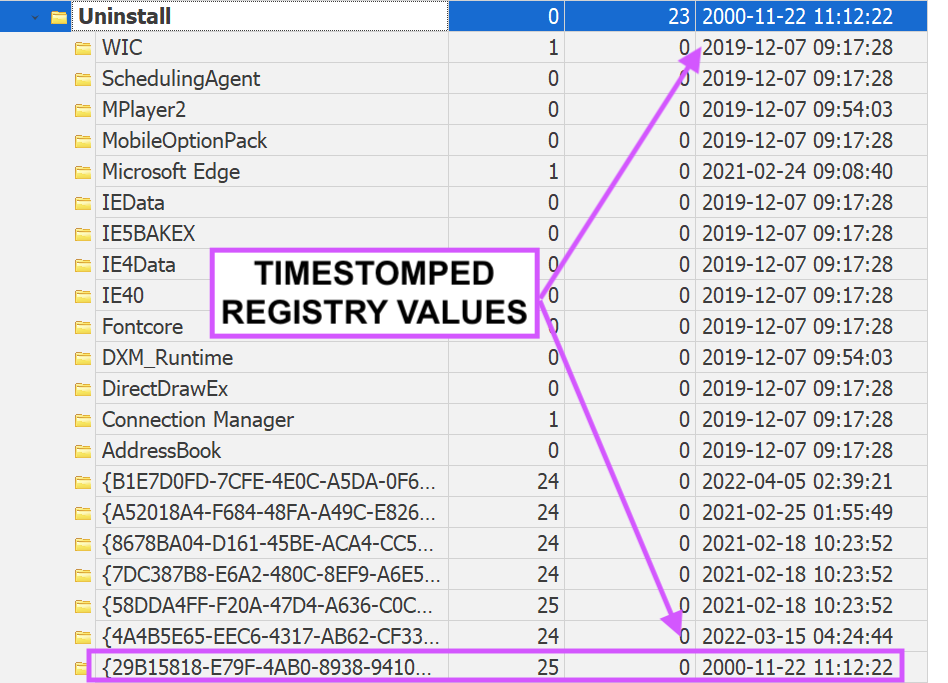
happy hunting also i think i use way too many purple things.
• • •
Missing some Tweet in this thread? You can try to
force a refresh