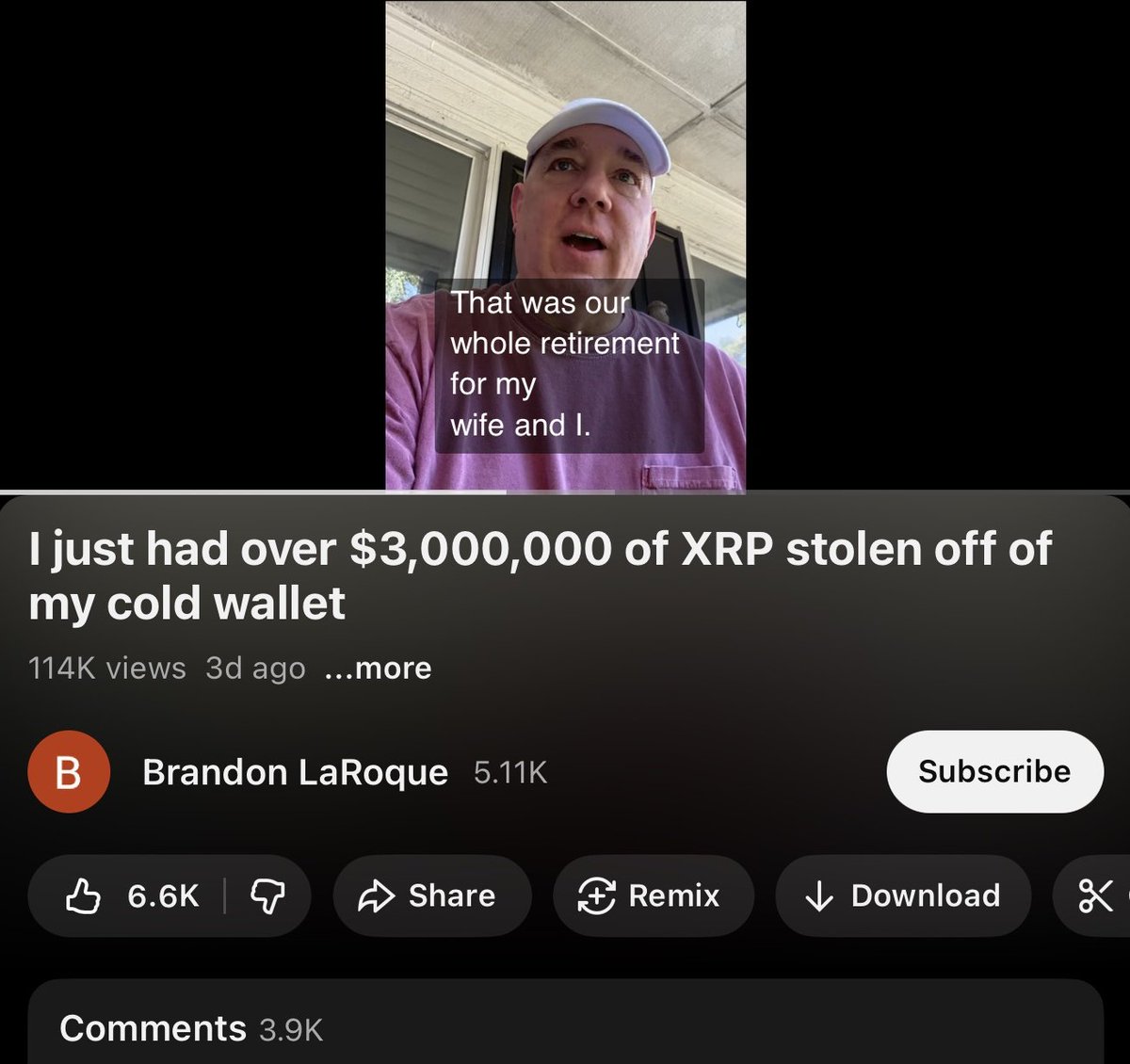
1/ Cameron Redman is the alleged person responsible for the hacked NFT Twitter accounts over the past few months
Does the name ring any bells? Well it should bc in February 2020 he SIM swapped a single person for $37 million worth of Bitcoin & Bitcoin Cash
Time for a thread


Does the name ring any bells? Well it should bc in February 2020 he SIM swapped a single person for $37 million worth of Bitcoin & Bitcoin Cash
Time for a thread



2/ On February 22, 2020 Josh Jones was sim swapped for ~60k BCH & 1547 BTC
BCH victim address
qzumak2rvxksjgkjuxe2fe5jxatktlsnhy5sthr5p7
BTC victim address 1
bc1qd0hveqwqu9h3x8flfq560hlyk9mptf3j2p89gg
BTC victim address 2
bc1qrwhh74sv88gzq6qgpz5u55u00w2lqprw30ke94

BCH victim address
qzumak2rvxksjgkjuxe2fe5jxatktlsnhy5sthr5p7
BTC victim address 1
bc1qd0hveqwqu9h3x8flfq560hlyk9mptf3j2p89gg
BTC victim address 2
bc1qrwhh74sv88gzq6qgpz5u55u00w2lqprw30ke94


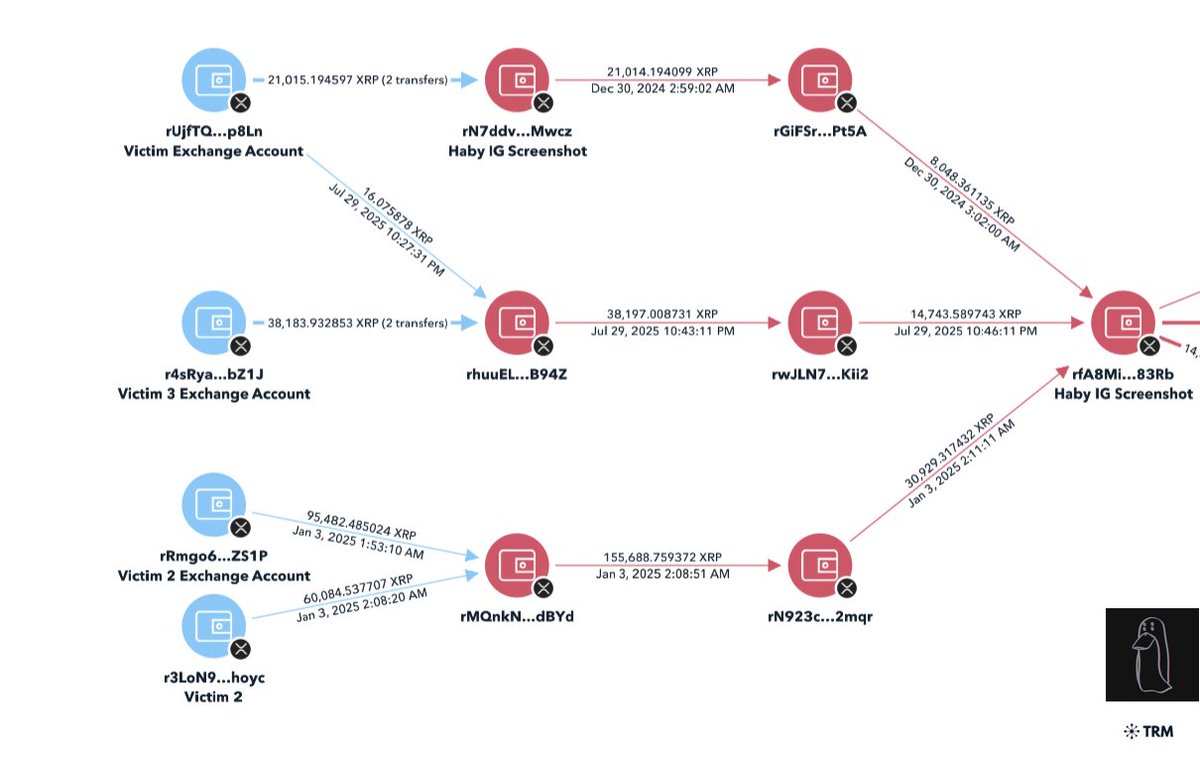
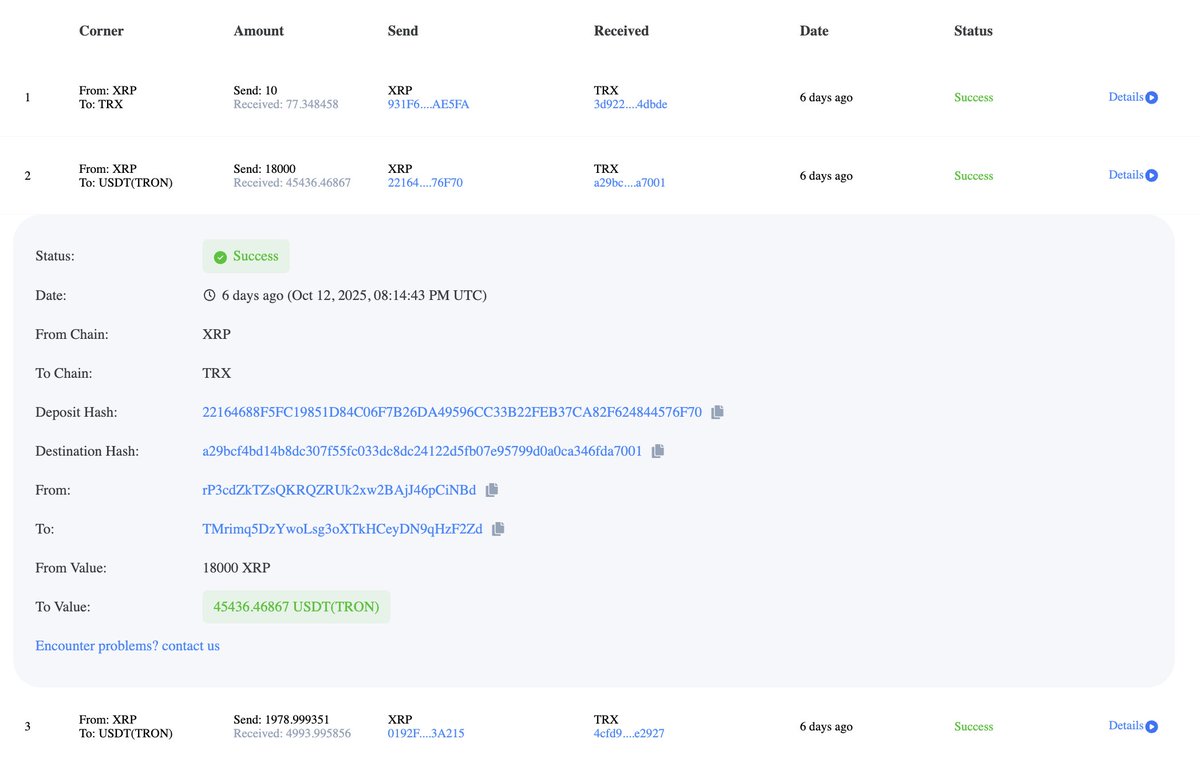
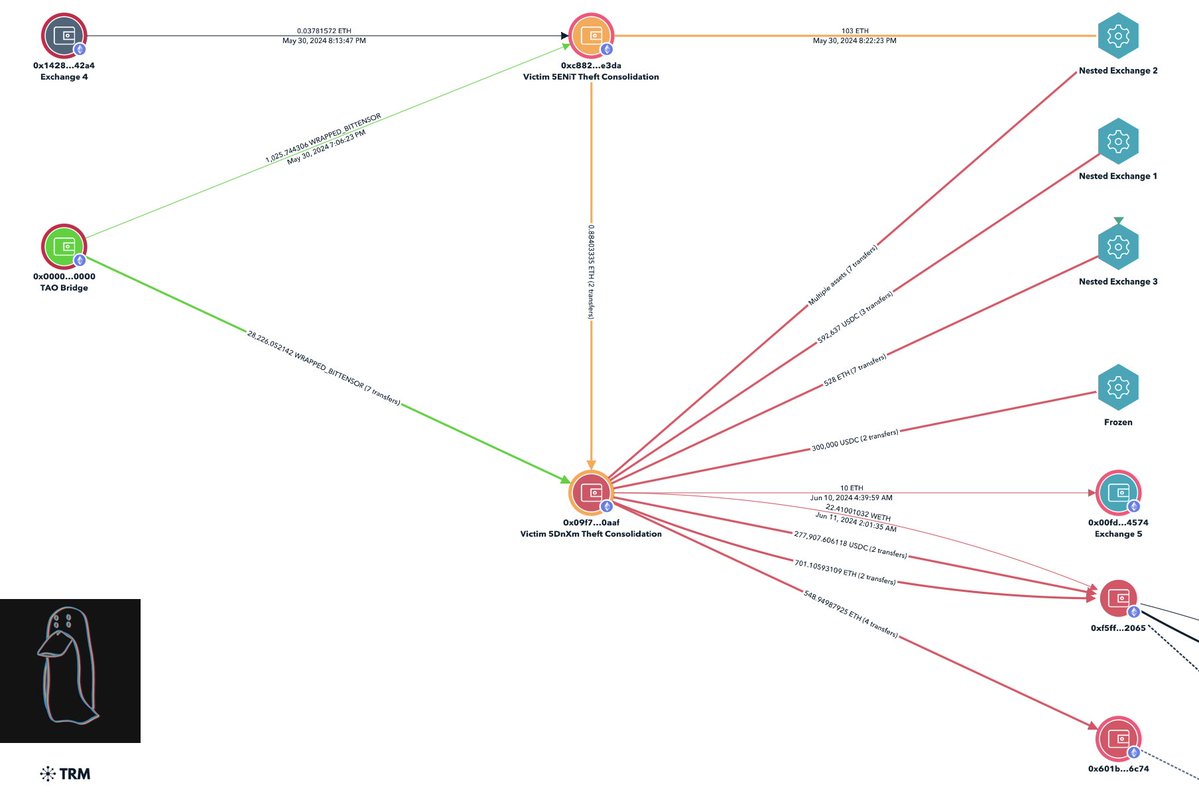
3/ Immediately following the attack the Redman laundered the 60k BCH with hundreds of transactions in small amounts to centralized exchanges (CEX).
This chart visualizes the movement of the 60k BCH with the majority ending up at two exchanges.
This chart visualizes the movement of the 60k BCH with the majority ending up at two exchanges.

4/ With the 1547 BTC stolen, a small portion was sent to CEXs but the majority was deposited into both Chip Mixer and Crypto Mixer. 

5/ On Nov 17 2021 Hamilton Police (Ontario, CA) formally charged Redman for the attack after working with FBI & US Secret Service
They seized $5.4m worth of crypto. The rest of the $31.5m still remains missing to this day
(he was underage at the time)
hamiltonpolice.on.ca/news/arrest-ma…
They seized $5.4m worth of crypto. The rest of the $31.5m still remains missing to this day
(he was underage at the time)
hamiltonpolice.on.ca/news/arrest-ma…
6/ Since May 2022 we’ve seen popular NFT Twitter accounts hacked such as @beeple @jenkinsthevalet @nounsdao @deekaymotion @Zeneca_33 @frankdegods @KeyboardMonkey3 @franklinisbored & more
The majority of these accounts all had 2FA on leaving people confused how this might happen.


The majority of these accounts all had 2FA on leaving people confused how this might happen.



7/ The hacked Twitter accounts lead to millions of dollars worth of crypto stolen in total.
This table shows a rough estimate for the amount of crypto stolen with each account in the Tweet above.
This table shows a rough estimate for the amount of crypto stolen with each account in the Tweet above.

8/ This lead to a post on the forum marketplace SWAPD by the user “Antihero” advertising a Twitter panel.
The prices to use the panel varied from $30k to $300k paid in crypto.


The prices to use the panel varied from $30k to $300k paid in crypto.



9/ On Twitter at July 29th 2022 antihero emerged with the name “Cam” on an account inactive for 14 yrs.
On Instagram he obtained the same username too.



On Instagram he obtained the same username too.




10/ On Instagram Redman posted a selfie of himself posing in front of mirror and also outside of a shopping center. 



11/ I zoom in and then look up the location of “Sunway Dental”
What do you know it happens to be in Missauga, ON very close to the Hamilton Police station in the city where Redman had been previously arrested in Nov 2021.


What do you know it happens to be in Missauga, ON very close to the Hamilton Police station in the city where Redman had been previously arrested in Nov 2021.



12/ If you’re still not convinced here’s more messages of him referencing Canada.
Prior to being charged for the SIM swap Redman had been also known by the aliases “Cream” “4k” “lucky” and for leaking unreleased Juice WRLD songs.


Prior to being charged for the SIM swap Redman had been also known by the aliases “Cream” “4k” “lucky” and for leaking unreleased Juice WRLD songs.
https://twitter.com/FallenLeaks/status/1461050441832312835
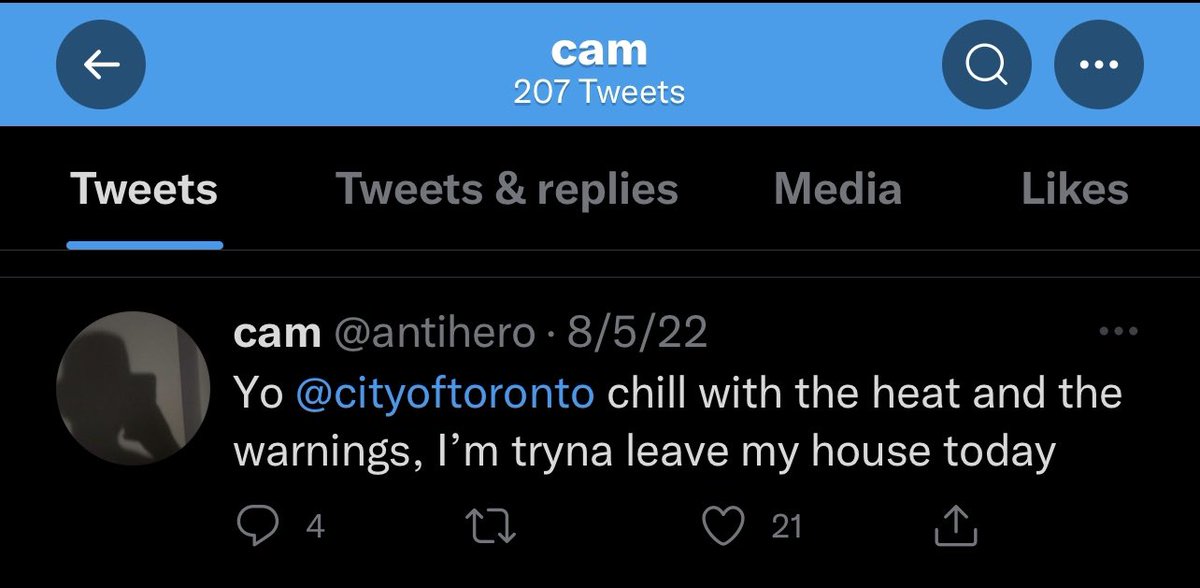


13/ Here’s two more posts Cam/Antihero made on SWAPD. Another person refers to the seller for the panel as Cam.
Archive:
archive.ph/ABvZy



Archive:
archive.ph/ABvZy




14/ Remember in Tweet 9 Redman began to eventually resell access to the panel.
On June 26 2022 Cam received a 230 ETH + 20 ETH payment for lifetime access to the Twitter panel.
0x0214ee97e9d828e1e6aa49a85b89982a7dceacc7

On June 26 2022 Cam received a 230 ETH + 20 ETH payment for lifetime access to the Twitter panel.
0x0214ee97e9d828e1e6aa49a85b89982a7dceacc7


15/ Just a few hours after the payment @nounsdao Twitter was hacked.
The scammers address had direct exposure to the JRNY club Twitter hacker, Nansen discord attack, and other Discord attacks.
Source:
chainabuse.com/search/address…

The scammers address had direct exposure to the JRNY club Twitter hacker, Nansen discord attack, and other Discord attacks.
Source:
chainabuse.com/search/address…


16/ Who bought the Twitter panel access from Redman? Well it was the scammers known as HZ/Chase and Popbob. Here’s HZ flexing panel access to @Serpent (a security researcher) 


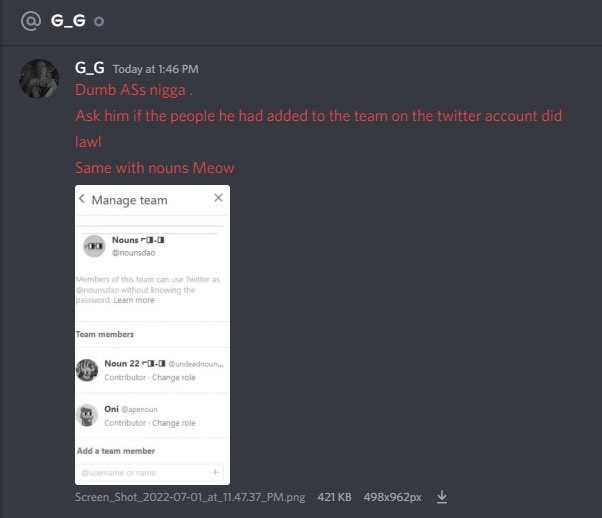


18/ It’s still unclear as to how Redman gained access to the panel to make elevated requests & reset passwords. As of now it appears the method stopped working
It’s wild someone can SIM swap a person for $37m, only return $5.4m, & go back to their old ways w/o serious jail time
It’s wild someone can SIM swap a person for $37m, only return $5.4m, & go back to their old ways w/o serious jail time
19/ Thanks for making it this far. Feel free to share this thread with others.
https://twitter.com/zachxbt/status/1562473638992850947
If you appreciate my research/work please consider donating to my ENS or Gitcoin.
ZachXBT.ETH
0x9D727911B54C455B0071A7B682FcF4Bc444B5596
bc1qrshu8d42ffq3jtrmzmujmmlh6swpw22a0qqt07l5u60n5efgazhqm5e4nk
gitcoin.co/grants/5039/za…
ZachXBT.ETH
0x9D727911B54C455B0071A7B682FcF4Bc444B5596
bc1qrshu8d42ffq3jtrmzmujmmlh6swpw22a0qqt07l5u60n5efgazhqm5e4nk
gitcoin.co/grants/5039/za…
Update: Cam deleted his SWAPD account and went private with the username on a fresh Instagram account. 



• • •
Missing some Tweet in this thread? You can try to
force a refresh