
I wanted to share some findings about RDP, Network Layer Authentication, LogonTypes and brute forcing 🔭
Recently, we perused some EventID 4625s (login failures) originating from public IPv4s brute forcing...
🧵
Recently, we perused some EventID 4625s (login failures) originating from public IPv4s brute forcing...
🧵

I kept finding LogonType 3s (network)
However only RDP was externally exposed on the machine, which usually records LogonType 10....
When this has happened before, I usually just assume its Windows jank and continue with my investigation 🤷♂️
But this time, I wanted to know WHY
However only RDP was externally exposed on the machine, which usually records LogonType 10....
When this has happened before, I usually just assume its Windows jank and continue with my investigation 🤷♂️
But this time, I wanted to know WHY

The wise @DaveKleinatland suggested Network Layer Authentication (NLA) would explain this:
"
NLA takes place before the session is started... without NLA things can be exposed before any sort of authentication.... like domain name, usernames, last logged on user, etc
"
- Dave 🧙♂️
"
NLA takes place before the session is started... without NLA things can be exposed before any sort of authentication.... like domain name, usernames, last logged on user, etc
"
- Dave 🧙♂️
Some detailed explanations of Network Layer Auth, and its relationship with RDP, come from the also wise @SteveSyfuhs
- syfuhs.net/should-i-turn-…
- syfuhs.net/how-authentica…
- syfuhs.net/should-i-turn-…
- syfuhs.net/how-authentica…
So the possible explanation:
Network Layer Authentication, when enabled, can change RDP login fails to be type 3s and not type 10s
Well, returning back to our case, lets validate that by querying the following in the Windows Registry 🧑🔬...
Network Layer Authentication, when enabled, can change RDP login fails to be type 3s and not type 10s
Well, returning back to our case, lets validate that by querying the following in the Windows Registry 🧑🔬...
`HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp`
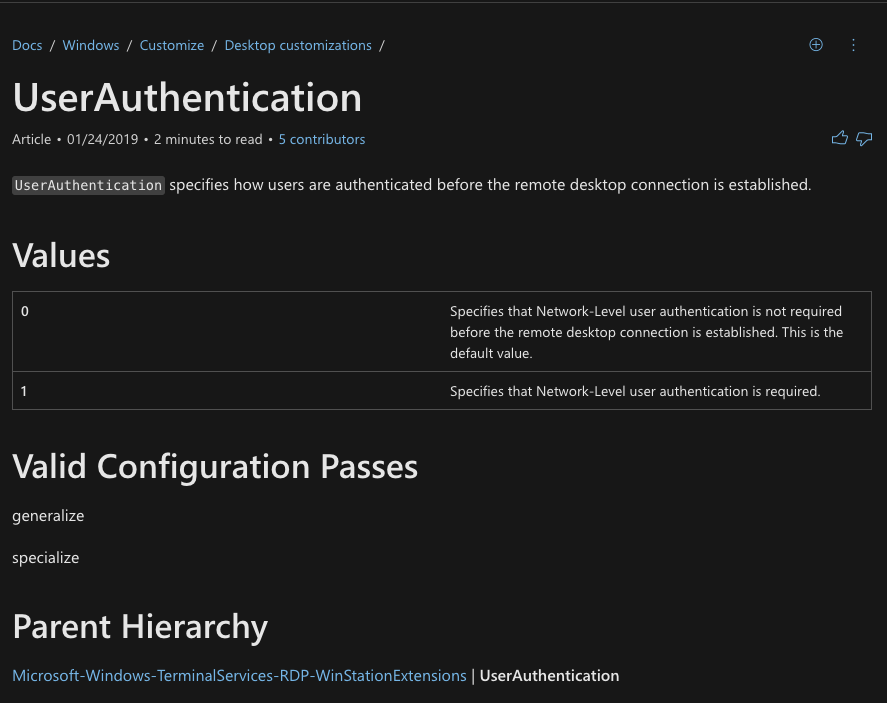
Look for `UserAuthentication`
According to documentation, if
- UserAuthentication = 0, NLA is not enabled.
- UserAuthentication = 1, NLA is enabled.
0 is default
docs.microsoft.com/en-us/windows-…
Look for `UserAuthentication`
According to documentation, if
- UserAuthentication = 0, NLA is not enabled.
- UserAuthentication = 1, NLA is enabled.
0 is default
docs.microsoft.com/en-us/windows-…
Querying our problem machine, we do indeed see that UserAuth = 1 and NLA is enabled.
Therefore we have an explanation why the RDP brute forces came in as LogonType 3s and not 10s.
Therefore we have an explanation why the RDP brute forces came in as LogonType 3s and not 10s.

To further validate this explanation, I found an old case that had RDP exposed and had LogonType 10 failures
Here, when we query the same registry location, UserAuth = 0 and NLA is not enabled.
That NLA was absent explains why there are numerous Type 10s when we check the 4625s
Here, when we query the same registry location, UserAuth = 0 and NLA is not enabled.
That NLA was absent explains why there are numerous Type 10s when we check the 4625s

In summary for our case:
Network Layer Auth will report RDP-related 4625s as LogonType 3s and not the 10s that we would expect.
Many knew about this already, and I've included some of their tweets below
Network Layer Auth will report RDP-related 4625s as LogonType 3s and not the 10s that we would expect.
Many knew about this already, and I've included some of their tweets below
https://twitter.com/Cyb3rSn0rlax/status/1123611511325376519?s=20&t=HcKrCiqvK6_NYTMlPTST3A
https://twitter.com/xknow_infosec/status/1237659767071481856?s=20&t=HcKrCiqvK6_NYTMlPTST3A
https://twitter.com/dfir_locard/status/1101945302108450816?s=20&t=HcKrCiqvK6_NYTMlPTST3A
I hope this proves useful to someone!
Do you like seeing real attack data alongside explanations?
You'll probs enjoy the upcoming @HuntressLabs TradeCraft Tuesday, led by the Godparents of #DFIR Jamie Levy (@gleeda) and Harlan Carvey (@keydet89)
huntress.com/resources/webi…
🧵✂️
Do you like seeing real attack data alongside explanations?
You'll probs enjoy the upcoming @HuntressLabs TradeCraft Tuesday, led by the Godparents of #DFIR Jamie Levy (@gleeda) and Harlan Carvey (@keydet89)
huntress.com/resources/webi…
🧵✂️
• • •
Missing some Tweet in this thread? You can try to
force a refresh













