#Qakbot Dumpulator Script has now been added to Github! 😀
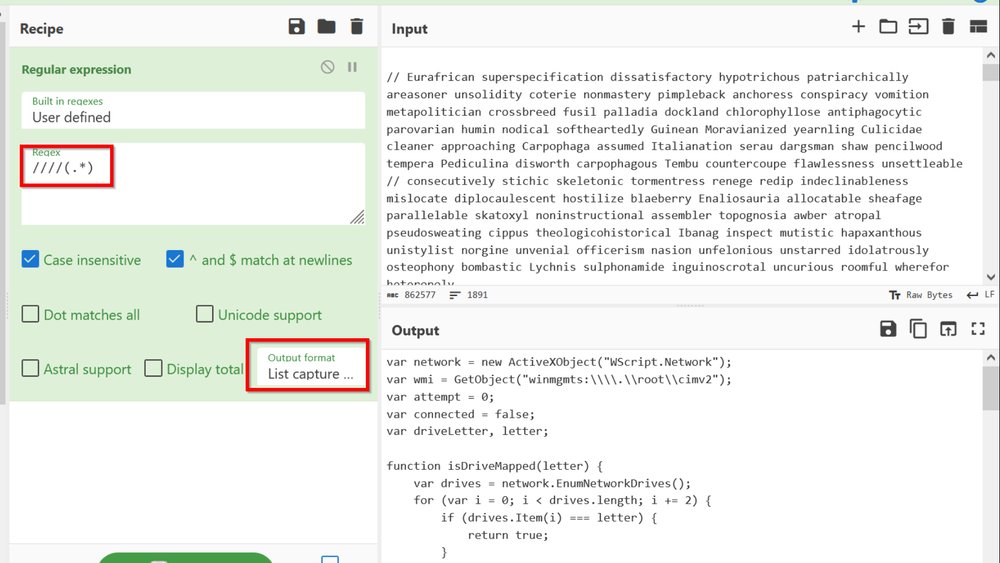
This script is capable of dumping decrypted strings from the encrypted string table used by recent Qakbot malware.
1/ (notes and details below)
#malware #qakbot #dumpulator #RE



This script is capable of dumping decrypted strings from the encrypted string table used by recent Qakbot malware.
1/ (notes and details below)
#malware #qakbot #dumpulator #RE
https://twitter.com/embee_research/status/1575380832965259265




2/ The script *should* work on the samples that I have provided in the readme, however you may need to change some register values to get it to work on different samples.
In particular, "dp.regs.ecx" and "dp.regs.esp+0x4" may need to be changed. As these ...
In particular, "dp.regs.ecx" and "dp.regs.esp+0x4" may need to be changed. As these ...
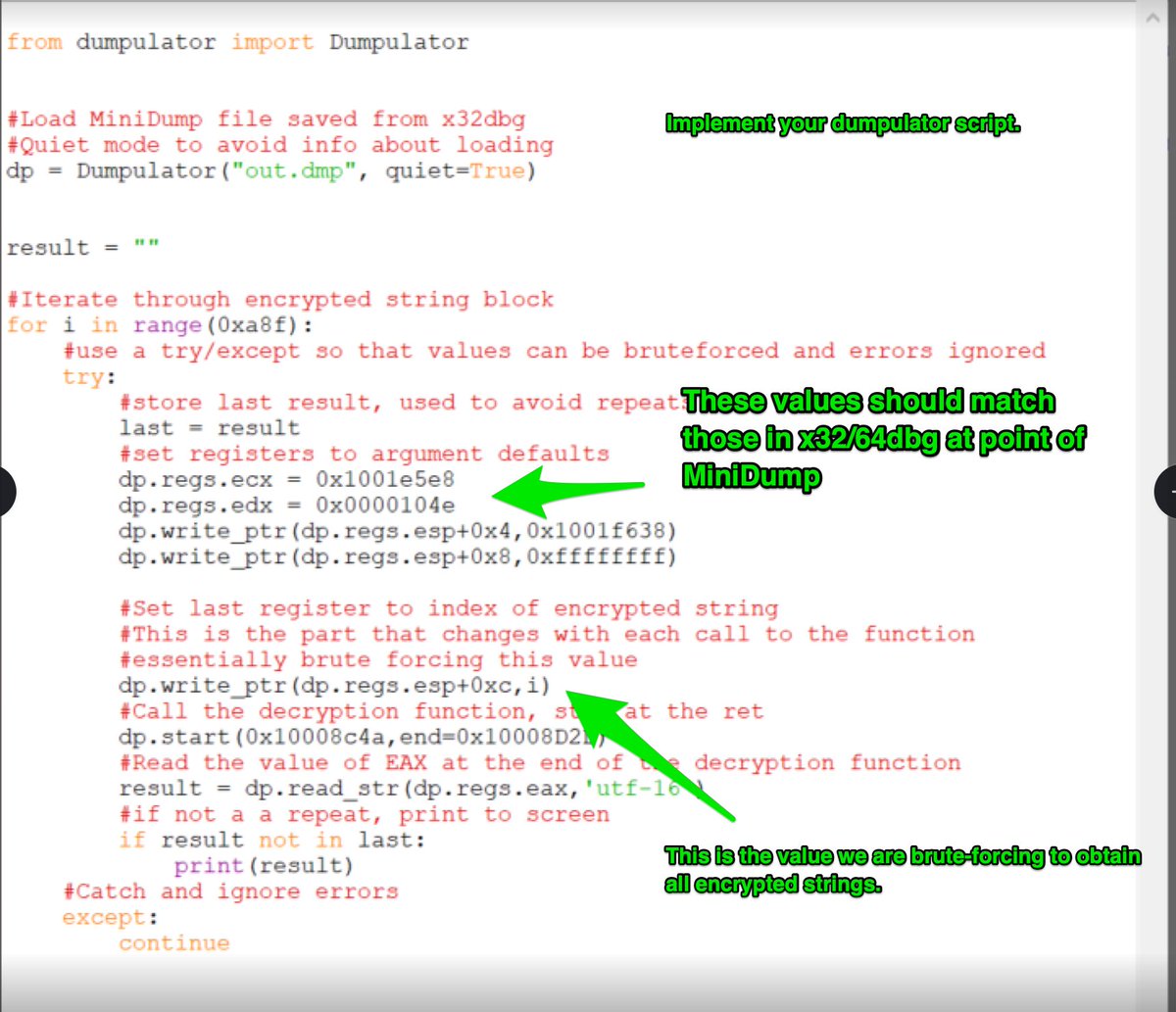
3/ cont'd... as these values point to the encrypted string table and key, which will differ between samples. You can re-use the same dump file if you wish, as the code will likely remain the same.
4/ You can experiment with extracting your #MiniDump at different points in the code. But you will likely need to change the registers depending on the location that you choose.
Further away from intended code = more registers to manually specify in script.
Further away from intended code = more registers to manually specify in script.
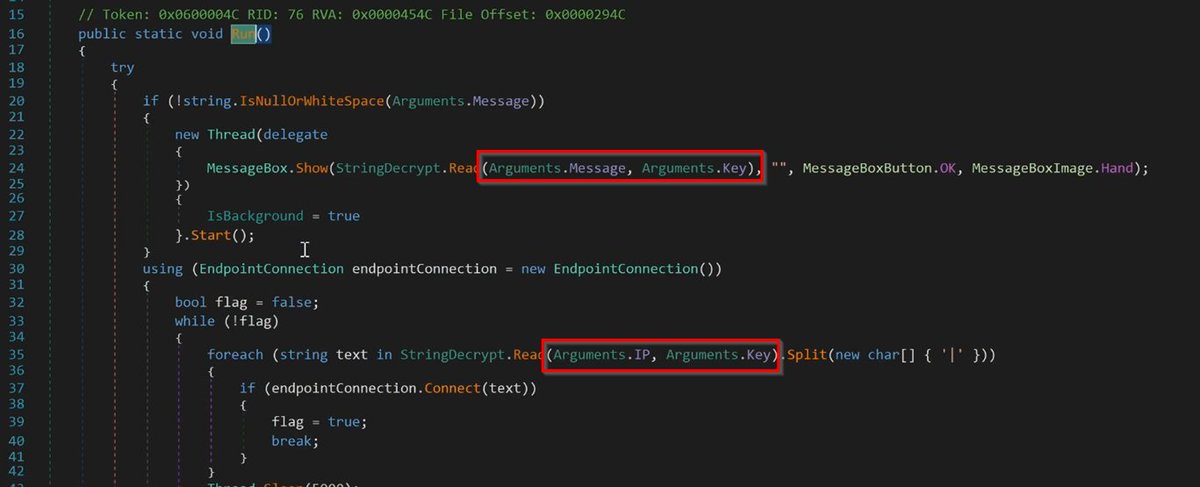
5/ Since my MiniDump was extracted at the point of the decryption function, I could probably get away with specifying fewer registers.
However, I found that the more I specified, the less errors I ran into when calling the same function over and over again.
However, I found that the more I specified, the less errors I ran into when calling the same function over and over again.
6/ For some reason, the same code didn't work when using "dp.call" rather than "dp.start" on the same address.
@mrexodia
@mrexodia
7/ In case you have access to only a packed #Qakbot sample. You can use a #debugger to break on VirtualAlloc calls. Then set hardware breakpoints on the returned addresses.
If done correctly, you should hit a hardware breakpoint when the unpacked sample is unpacked.
If done correctly, you should hit a hardware breakpoint when the unpacked sample is unpacked.
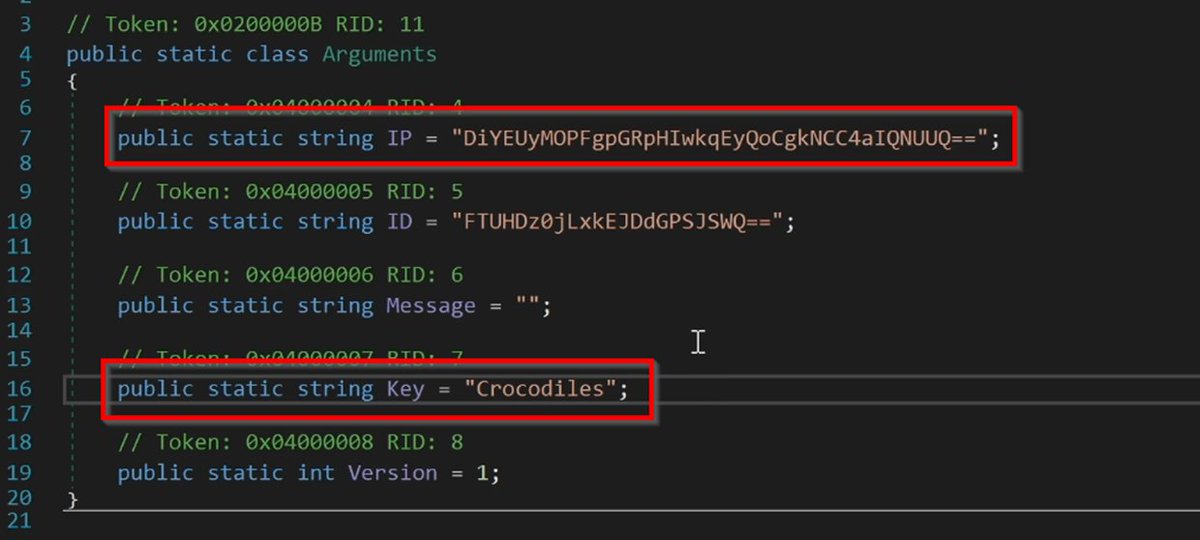
8/ I also found that the encrypted buffers could be decrypted from other samples by manually copying them out of the data section, and passing them to the script.
There's probably a way to automate this. And could be a a fun challenge for someone.
There's probably a way to automate this. And could be a a fun challenge for someone.
9/ The same concept of locating function -> x32dbg -> take minidump -> call from dumpulator. Works on other malware families as well.
I was able to get this working for #IcedID. Assuming it may work on other malware families too.
I was able to get this working for #IcedID. Assuming it may work on other malware families too.
10/ For some other examples of Dumpulator scripts, @herrcore has some fantastic examples on the OAlabs blog. Which can be found here.
research.openanalysis.net/matanbuchus/lo…
research.openanalysis.net/matanbuchus/lo…
11/ A significant help for me when developing this script, was this blog by @vinopaljiri @_CPResearch_ . I would highly recommend everyone to check it out.
research.checkpoint.com/2022/native-fu…
research.checkpoint.com/2022/native-fu…
• • •
Missing some Tweet in this thread? You can try to
force a refresh