#BeosinAlert #Flashloan
$PLTD suffers a price manipulation attack with a profit of 24,497 $BUSD for the hacker.
(Tx provided by @bbbb)
TX:0x8385625e9d8011f4ad5d023d64dc7985f0315b6a4be37424c7212fe4c10dafe0
Attacker’s address:0x6ded5927f2408a8d115da389b3fe538990e93c5b
$PLTD suffers a price manipulation attack with a profit of 24,497 $BUSD for the hacker.
(Tx provided by @bbbb)
TX:0x8385625e9d8011f4ad5d023d64dc7985f0315b6a4be37424c7212fe4c10dafe0
Attacker’s address:0x6ded5927f2408a8d115da389b3fe538990e93c5b
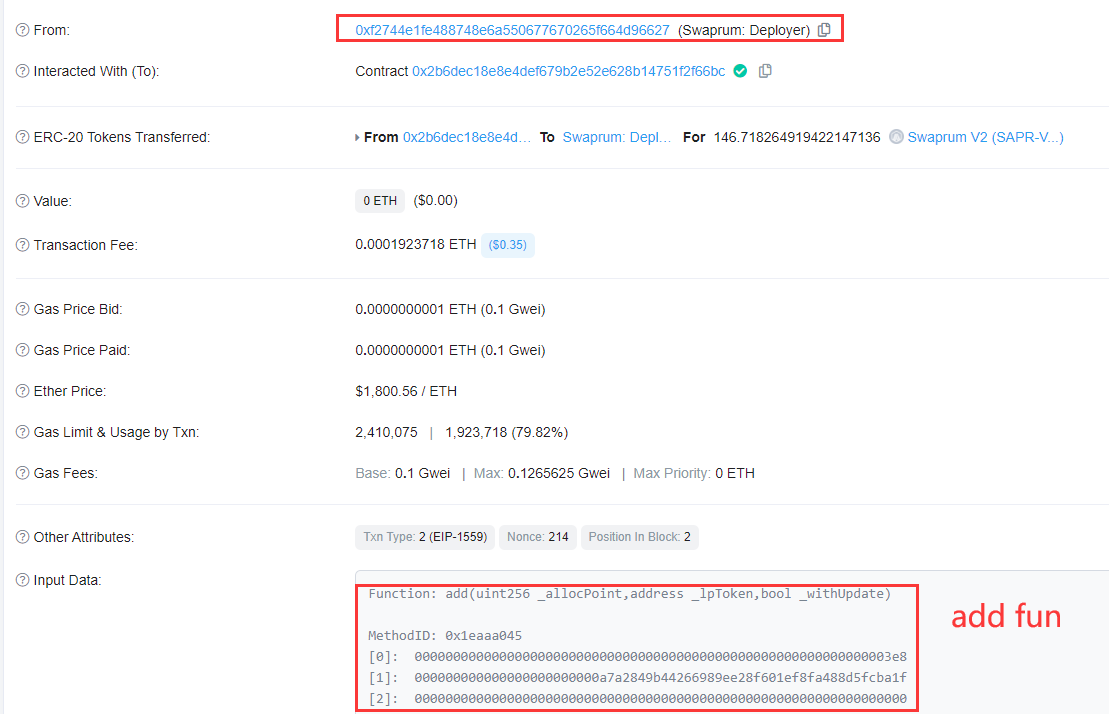
The attacker mainly exploits the vulnerability in the PLTD contract to reduce the balance of PLTDs in Case-LP (0x4397c7) to 1 via flashloan, and then uses the $PLTD to swap all the $BUSD into the attack contract.
Step 2: The attacker swaps all the 666,000 $BUSD into 1.57M $PLTDs, at which point the attacker already holds a large amount of PLTD tokens, which will subsequently be used for the purpose of manipulating the balance of PLTD tokens in Cake-LP. 

Step 3: The attacker queries the current bron value and the PLTD balance of the Commite-LP, which is a check before the attack. Note that these two values are critical and relate to the success of the attack. 

Step 4: The attacker sends 116,000 $PLTD tokens directly to Commite-LP (0x4397c7), note that this amount is just twice the balance of $PLTDs in Commite-LP in the previous step minus 1
Why this number? We can find answers from the code.

Why this number? We can find answers from the code.


1) Call the transfer function.
2) The target address is uniswapV2Pair, we look at else if branch in line 344. The from address is the attack contract, takeFee is true, and the internal function _tokenTransferSell is called.

2) The target address is uniswapV2Pair, we look at else if branch in line 344. The from address is the attack contract, takeFee is true, and the internal function _tokenTransferSell is called.


3) The internal code of the _tokenTransferSell function is as follows. In lines 423-426, this part of the code sets the _bron to half the number of this transfer, i.e. the balance of the Cake-LP minus 1. 

Step 5: Let's back to the attack. Here the attacker uses skim to take back the PLTD transferred in step 4. As in the _transfer function, if the from address is uniswapV2Pair, then it will call _tokenTransferBuy.
(The function will not affect the value of _bron)
(The function will not affect the value of _bron)

Step 6: All the previous operations are for this step. The attacker transfers 1 $PLTD to the address 0x16b9a82891338f9ba80e2d6970fdda79d1eb0dae, and since this address is not the address of Take-LP, the internal function _tokenTransfer is called for this transfer. 

Look at line 451 to 456. In step 4, _bron is set to the balance of Cake-LP minus 1, and the fifth step restores the balance of Cake-LP. This step directly reduces the balance of Cake-LP to 1, and then calls the sync function of Cake-LP to synchronize the balance to reserve. 


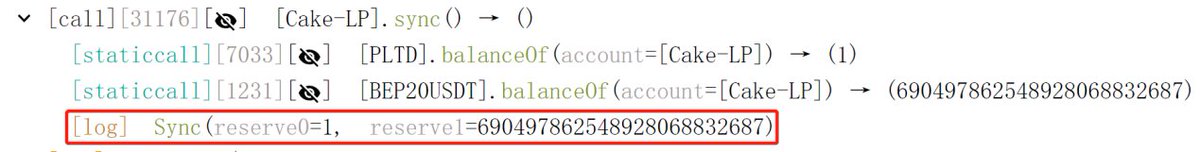
Step 7: The attacker swaps all the $PLTD tokens to $BUSD, almost draining the entire BUSD balance of Case-LP.
The attacker gains 690,000 $BUSD and repays the 666,000 BUSD flashloan. The remaining 24,497 $BUSD profit is sent to 0x083c057221e95D45655489Fb01b05C4806387C19
The attacker gains 690,000 $BUSD and repays the 666,000 BUSD flashloan. The remaining 24,497 $BUSD profit is sent to 0x083c057221e95D45655489Fb01b05C4806387C19

• • •
Missing some Tweet in this thread? You can try to
force a refresh