
🔔Provide #Blockchain projects with intelligence and real-time risk alerts for security incidents including #Hacks, #rugpull and flashloan.
©By @Beosin_com
How to get URL link on X (Twitter) App


 2/ The total loss from hacks in Web3 has significantly decreased compared to last year.
2/ The total loss from hacks in Web3 has significantly decreased compared to last year. 


 2/ Circom is a zero-knowledge proof circuit compiler developed in Rust. The team behind Circom has also developed the SnarkJS library, which supports various functionalities, including trusted setups, generation and verification of zero-knowledge proofs.
2/ Circom is a zero-knowledge proof circuit compiler developed in Rust. The team behind Circom has also developed the SnarkJS library, which supports various functionalities, including trusted setups, generation and verification of zero-knowledge proofs. 


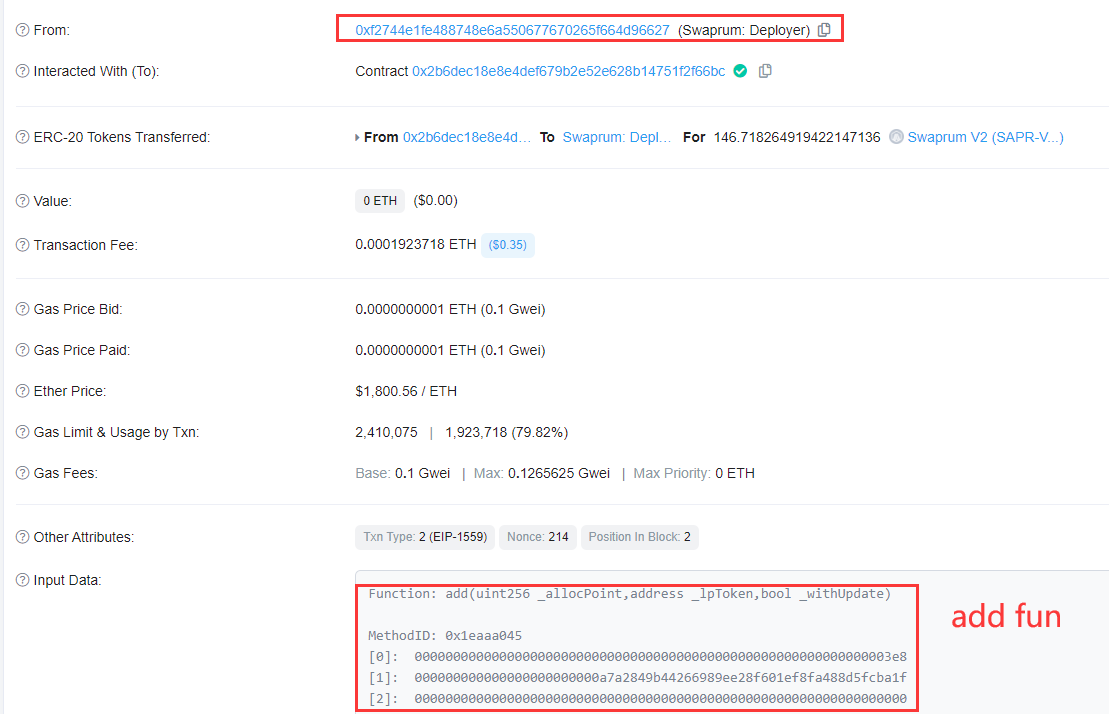 2/ The project has upgraded the the normal liquidity collateral reward contract to a contract containing backdoor functions.
2/ The project has upgraded the the normal liquidity collateral reward contract to a contract containing backdoor functions.




 1) The attacker created the malicious pool contract 30 days ago.
1) The attacker created the malicious pool contract 30 days ago.
https://twitter.com/sentimentxyz/status/1643319780042997763
 2/ The attacker first calls the "joinPool" function of Balancer Vault to make a deposit. Then he calls "exitPool" to withdraw, during which Balancer Vault sends eth to the attacker to call the fallback function of the attack contract.
2/ The attacker first calls the "joinPool" function of Balancer Vault to make a deposit. Then he calls "exitPool" to withdraw, during which Balancer Vault sends eth to the attacker to call the fallback function of the attack contract.

https://twitter.com/BeosinAlert/status/1642802983175061504
 On the other hand, because the MEV bot uses the attacker’s validator to produce the block, and the attacker has been trying to see if MEV uses his validator.
On the other hand, because the MEV bot uses the attacker’s validator to produce the block, and the attacker has been trying to see if MEV uses his validator. 
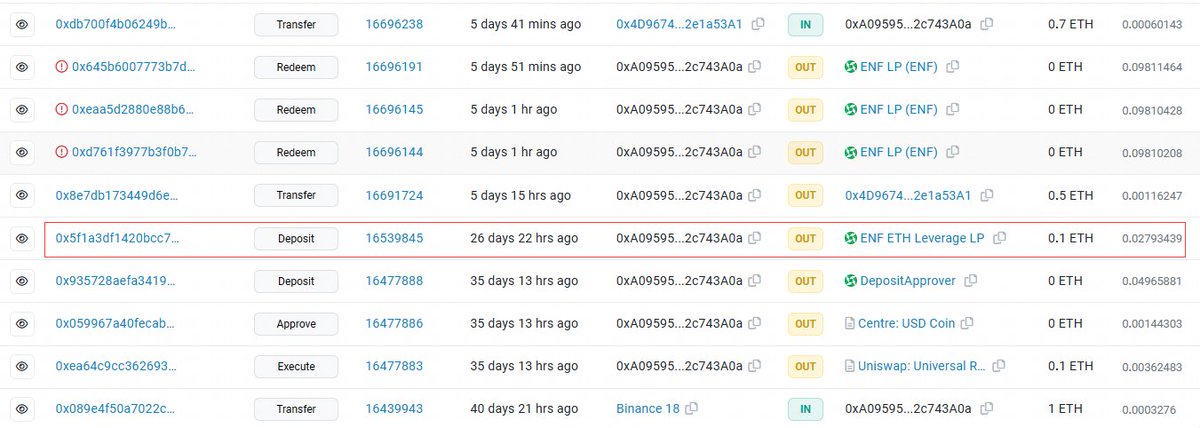
 2/ The project owner upgraded the EFVault contract by proxy before the attack.
2/ The project owner upgraded the EFVault contract by proxy before the attack.







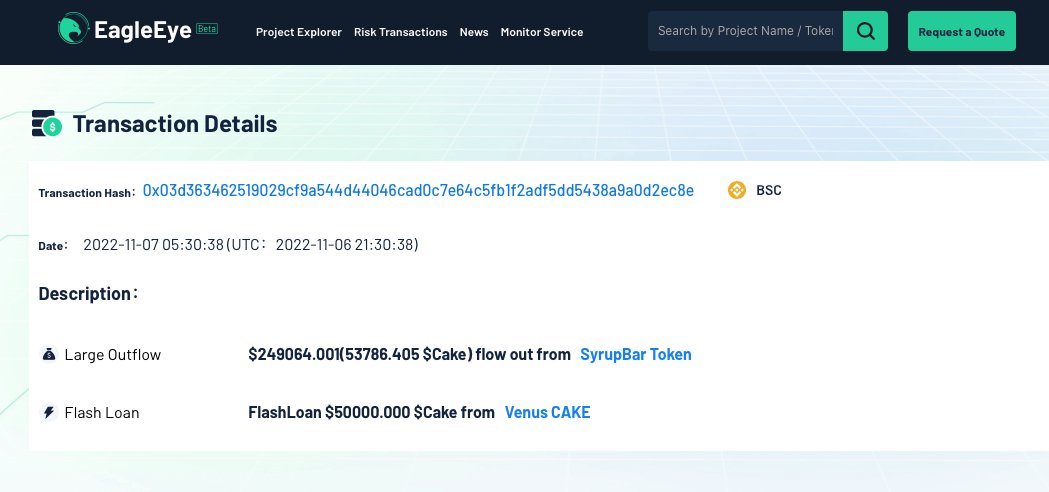
 2/ Tx:
2/ Tx:


https://twitter.com/TeamFinance_/status/1585562380591063043The attack contract 0xCFF07C4e6aa9E2fEc04DAaF5f41d1b10f3adAdF4 exploits the vulnerability that migrate function of the LockToken contract does not properly validate _id and params, and illegally migrate $WTH, $CAW, $USDC, $TSUKA tokens from V2 to V3 liquidity pool.

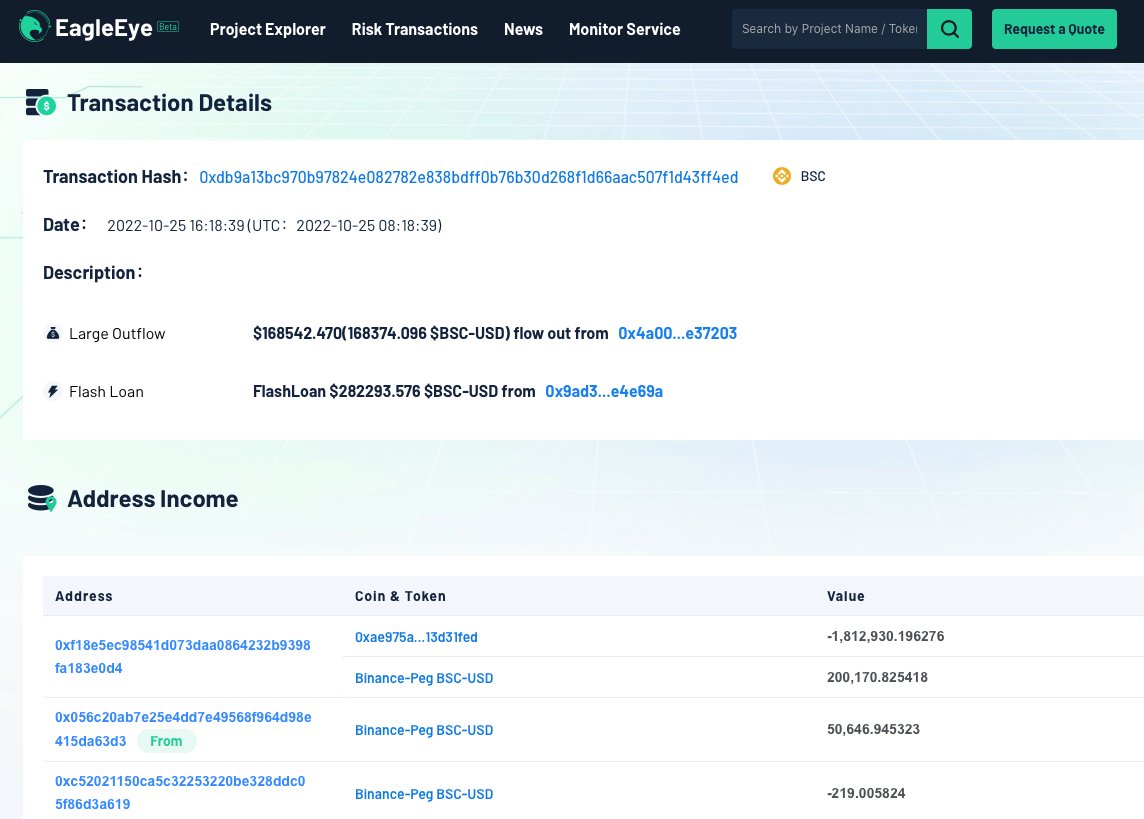
 2/ First borrow 1,000,000 BUSD via flashloan and swap for $ULME tokens through Pancakeswap. Here the attacker should have collected the list of users who approved the BUSD to the ULME contract.
2/ First borrow 1,000,000 BUSD via flashloan and swap for $ULME tokens through Pancakeswap. Here the attacker should have collected the list of users who approved the BUSD to the ULME contract. 

