
12 #recon tools you NEED to know about! 🧵
Recon, the gathering of information about your target, is becoming more and more important! 🧠
Here are the tools to help you spot subdomains, vhosts, S3 buckets, parameters and more faster and more effective than the others 👇
Recon, the gathering of information about your target, is becoming more and more important! 🧠
Here are the tools to help you spot subdomains, vhosts, S3 buckets, parameters and more faster and more effective than the others 👇
[1️⃣] DNS
This DNS toolkit by @pdiscoveryio can do a lot! But let's focus on reverse DNS lookups 👀
Often, you have a huge list of IP addresses 📜
Just like resolving a domain to an IP, you can also try doing the opposite using PTR records!
Et voila! Domains to continue recon! 👇
This DNS toolkit by @pdiscoveryio can do a lot! But let's focus on reverse DNS lookups 👀
Often, you have a huge list of IP addresses 📜
Just like resolving a domain to an IP, you can also try doing the opposite using PTR records!
Et voila! Domains to continue recon! 👇

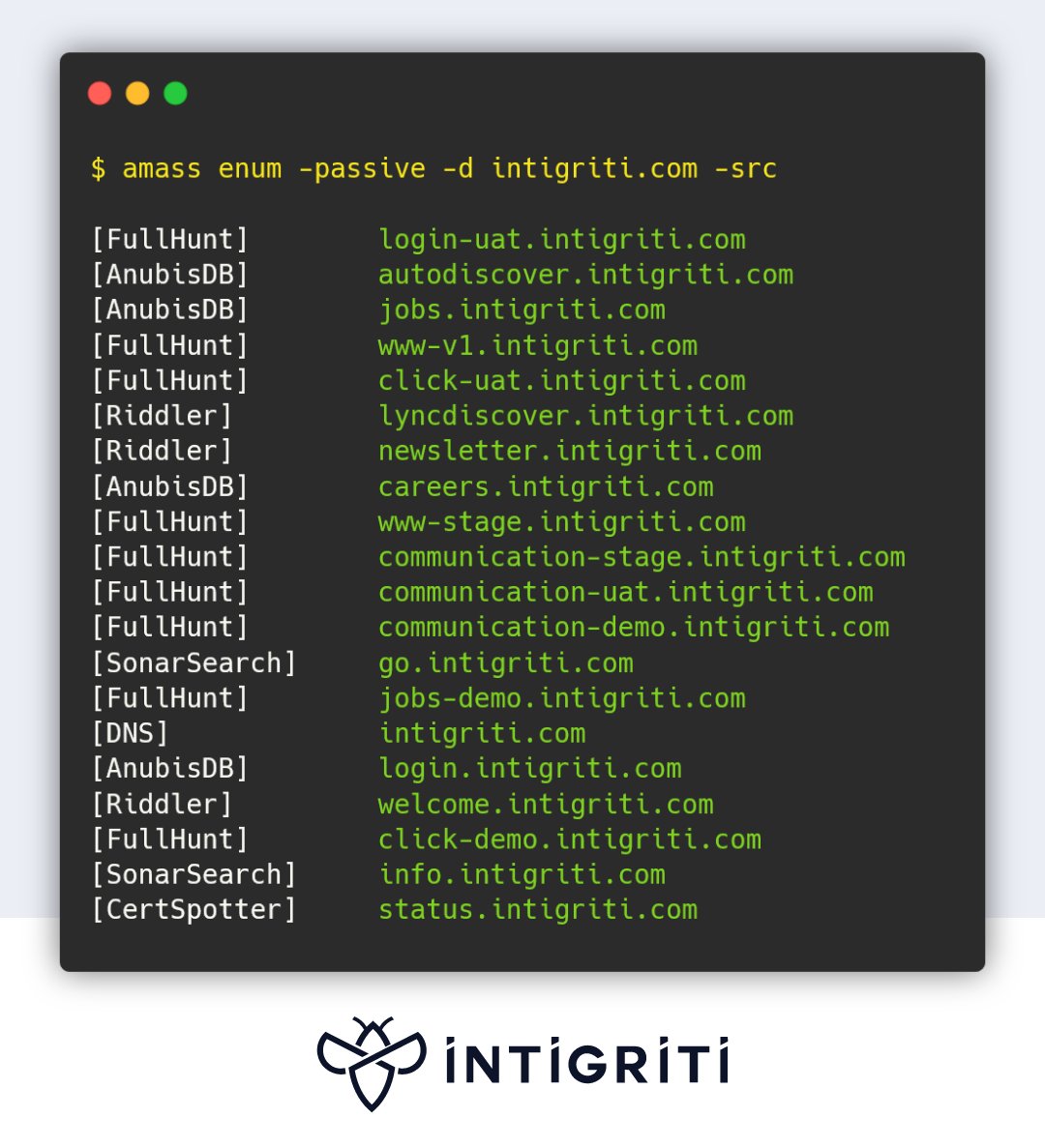
[2️⃣] Amass
This network mapping tool by @owasp is incredible, but let's hone in on doing subdomain enumeration. 🕸
The main domains companies use are often well-secured. But what about the domain that nobody knows about? Those can be riddled with bugs! 🐛
Let's find them! 👇
This network mapping tool by @owasp is incredible, but let's hone in on doing subdomain enumeration. 🕸
The main domains companies use are often well-secured. But what about the domain that nobody knows about? Those can be riddled with bugs! 🐛
Let's find them! 👇
[3️⃣] @nmap
Nmap stands for "Network Mapper" and that's precisely what it does.
This 25-year-old tool is FAR from outdated!
Let's use Nmap to find out what's actually running on those endless machines you've enumerated so far! 👇
Nmap stands for "Network Mapper" and that's precisely what it does.
This 25-year-old tool is FAR from outdated!
Let's use Nmap to find out what's actually running on those endless machines you've enumerated so far! 👇

[4️⃣] VHostScan
This Python scanner by @codingo_ is an excellent tool for finding virtual hosts! 👨💻
What's that? Unlike subdomains, vhosts allow multiple applications to be hosted on a single server. 🖥
This slightly esoteric feature means not many hunters are looking for this! 🔍
This Python scanner by @codingo_ is an excellent tool for finding virtual hosts! 👨💻
What's that? Unlike subdomains, vhosts allow multiple applications to be hosted on a single server. 🖥
This slightly esoteric feature means not many hunters are looking for this! 🔍

[5️⃣] Httprobe
All this recon has given us many subdomains, but what now? 🤷♂️
This tool by @TomNomNom will help us find all the web servers running on these subdomains! 👇
All this recon has given us many subdomains, but what now? 🤷♂️
This tool by @TomNomNom will help us find all the web servers running on these subdomains! 👇

[6️⃣] Waybackurls
Another tool by @TomNomNom can help us continue.
Instead of opting for active directory fuzzing, let's use the power of history to see what we can find on a target's website!
This tool uses the @waybackmachine to find new endpoints passively! 👇
Another tool by @TomNomNom can help us continue.
Instead of opting for active directory fuzzing, let's use the power of history to see what we can find on a target's website!
This tool uses the @waybackmachine to find new endpoints passively! 👇

[7️⃣] S3enum
This Go tool by @koenrh automates AWS S3 bucket enumeration.
Using this tool, you may be able to find the next big misconfiguration or overly permissive S3 bucket! 👇
This Go tool by @koenrh automates AWS S3 bucket enumeration.
Using this tool, you may be able to find the next big misconfiguration or overly permissive S3 bucket! 👇

[8️⃣] EyeWitness
If you're overwhelmed with endpoints, that's okay!
Let's bring some order to this madness using this tool by @FortyNorthSec 💪
It allows you to organize endpoints depending on their return value quickly. Screenshots of the page are a bonus! 🖼
If you're overwhelmed with endpoints, that's okay!
Let's bring some order to this madness using this tool by @FortyNorthSec 💪
It allows you to organize endpoints depending on their return value quickly. Screenshots of the page are a bonus! 🖼

[9️⃣] Relative URL extractor
JavaScript files are recon goldmines! They sometimes reference very interesting relative URLs that you need to know about! 🧠
But manually going through 1000s of JS files, no! 🪓
Use this great tool by @jobertabma 👇
JavaScript files are recon goldmines! They sometimes reference very interesting relative URLs that you need to know about! 🧠
But manually going through 1000s of JS files, no! 🪓
Use this great tool by @jobertabma 👇

[1️⃣0️⃣] TruffleHog
If you're lucky, you may have found a git repository during your recon! 🍀
Let's use this tool by @trufflesec to dig into it and uncover all secrets the repo has to hold! 👇
If you're lucky, you may have found a git repository during your recon! 🍀
Let's use this tool by @trufflesec to dig into it and uncover all secrets the repo has to hold! 👇

[1️⃣1️⃣] Arjun
Let's talk about enumerating GET parameters!
If you were thinking of brute-forcing thousands of them, then check out Arjun by @s0md3v 🛑
It can check for thousands of GET params in under 50 requests! 🤯
Let's talk about enumerating GET parameters!
If you were thinking of brute-forcing thousands of them, then check out Arjun by @s0md3v 🛑
It can check for thousands of GET params in under 50 requests! 🤯

[1️⃣2️⃣] Wappalyzer
One last trick we'll give you is fingerprinting everything you find using @Wappalyzer 👇
This way, you know what you're dealing with and what exploit might or might not work! 💪
One last trick we'll give you is fingerprinting everything you find using @Wappalyzer 👇
This way, you know what you're dealing with and what exploit might or might not work! 💪

🧵 And that's a wrap!
Note that there are alternatives to the tools we've showcased here, and looking around for something you like is highly recommended! 🛒
Be sure to like this tweet and follow @intigriti if you want more of these threads! 💜
Happy hacking! 👩💻
Note that there are alternatives to the tools we've showcased here, and looking around for something you like is highly recommended! 🛒
Be sure to like this tweet and follow @intigriti if you want more of these threads! 💜
Happy hacking! 👩💻
• • •
Missing some Tweet in this thread? You can try to
force a refresh







