
Bug bounty & VDP platform trusted by the world’s largest organisations! 🌍
5 subscribers
How to get URL link on X (Twitter) App

 1️⃣ Macros
1️⃣ Macros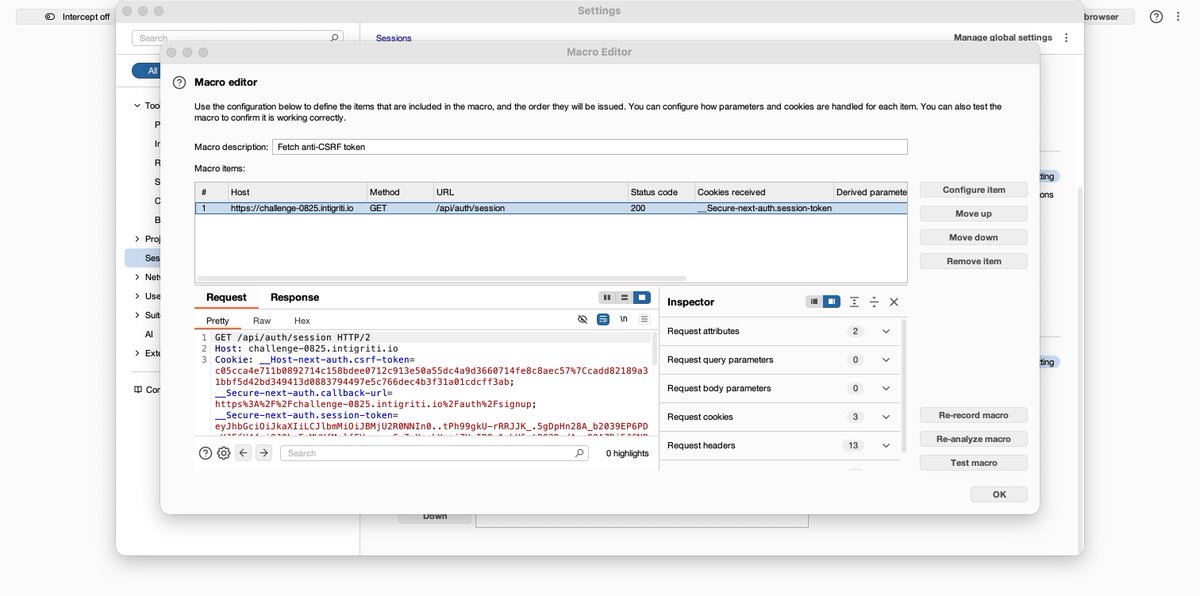

 Before we dive in, let's first cover what recon (short for 'reconnaissance') is.
Before we dive in, let's first cover what recon (short for 'reconnaissance') is.
 1️⃣ Blind XSS via request headers
1️⃣ Blind XSS via request headers

 XML eXternal Entity (XXE) injection is a vulnerability class that stems from inadequate user input validation during XML parsing, allowing attackers to take advantage of parser misconfigurations!
XML eXternal Entity (XXE) injection is a vulnerability class that stems from inadequate user input validation during XML parsing, allowing attackers to take advantage of parser misconfigurations!
 2-Factor authentication (2FA) vulnerabilities arise when the implementation of this security layer is weak or contains logic errors
2-Factor authentication (2FA) vulnerabilities arise when the implementation of this security layer is weak or contains logic errors
 AWS S3 (Simple Storage Service) buckets are a popular storage service often used by software companies to store data.
AWS S3 (Simple Storage Service) buckets are a popular storage service often used by software companies to store data.

 1️⃣ bypass-url-parser
1️⃣ bypass-url-parser
 Imagine this...
Imagine this...
 1⃣ SQLMap
1⃣ SQLMap
 Today, we will cover how you can successfully exploit XXE vulnerabilities
Today, we will cover how you can successfully exploit XXE vulnerabilitieshttps://twitter.com/intigriti/status/1684887385715376128

 A common mistake new hunters make is reporting XSS where the payload is supplied inside a request header
A common mistake new hunters make is reporting XSS where the payload is supplied inside a request header

