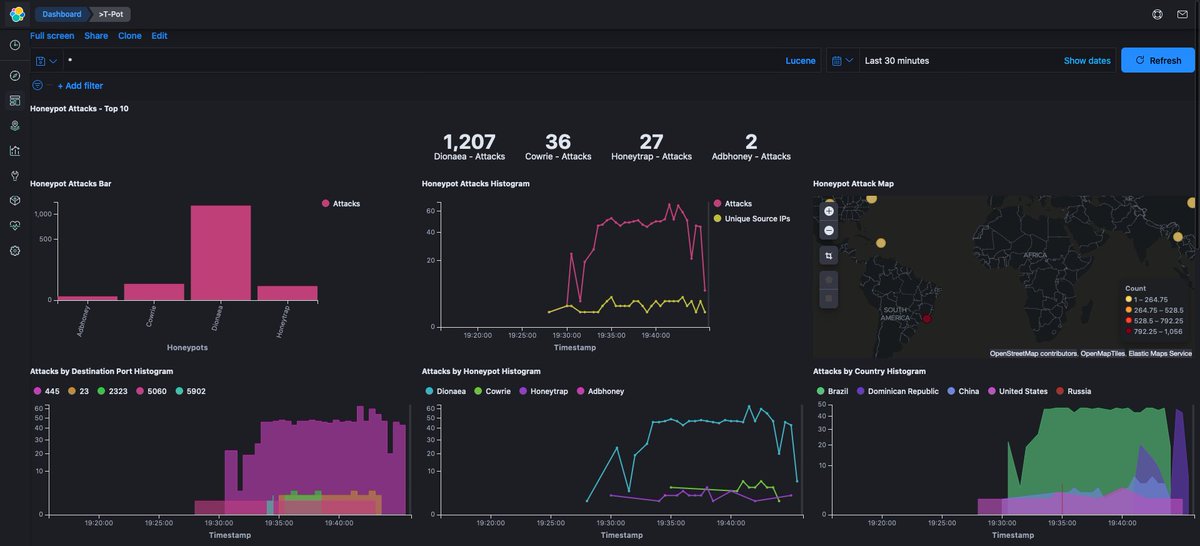
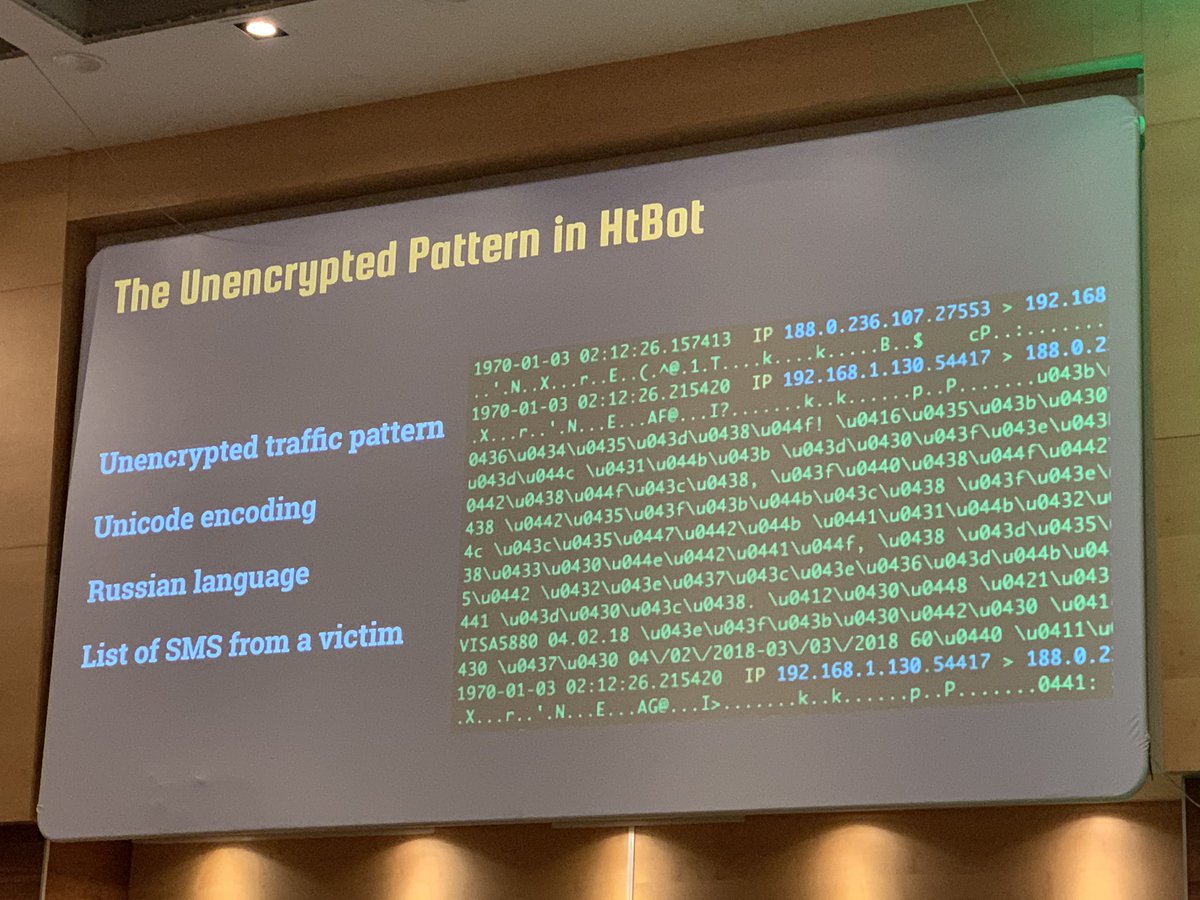
Now starting @juanandres_gs at @ekoparty on cyber espionage in #latam. Studying espionage is very interesting: involves knowing the context, the culture, the economic factors. But, how much there really is? #ekoparty 

We know hundreds of groups. Not all state-sponsored. The reality is that is not much on how much we know, but how much are we actually looking for. In Latin America we are not looking hard enough. We cannot longer say nothing is happening in #latam. #ekoparty
We are no looking hard enough in many regions. And there’s activity originating in some regions that are being ignored.
The money spent in one threat intelligence subscription in a first world country can create and fund a SOC in our #latam countries easily. There’s so much disparity and needs in every region, which sadly are not contemplated in some industries.
There’s a certain industry limitation. Like number of people doing threat intelligence, the attention of these people and teams, the motivation behind. If everyone was looking at the situation in Ukraine, who was tracking what North Korea, China and other countries were doing?
Crazy but true: no one is coming to rescue us (#latam).
Shoutout to @R3Dmx investigating the activities of #NSO and Pegasus in such a hostile environment and playing as locals.
We think countries in #latam do not have good economies; however they had purchasing power and resources to buy tools from hacking team, NSO and others. #ekoparty #EKO2022 

• • •
Missing some Tweet in this thread? You can try to
force a refresh