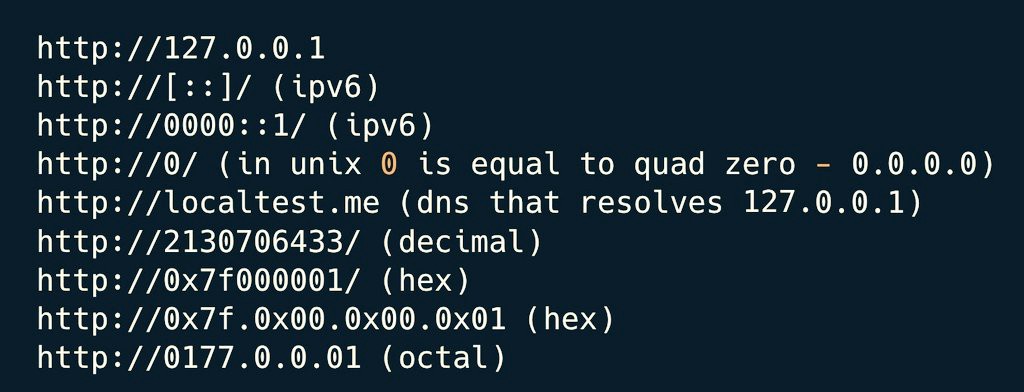
Day 0⃣2⃣/2⃣0⃣ -- [Registration/SignUp Page Vulnerabilities]
➡️ Day 2, we will cover potential vulnerabilities that can affect a Registration/Sign-Up Page of a web application
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 2, we will cover potential vulnerabilities that can affect a Registration/Sign-Up Page of a web application
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
3/n
weak registration page
weak registration page
5/n
Open Redirect in registration page
Open Redirect in registration page
6/n
Sql Injection On Login And SignUp Function
Sql Injection On Login And SignUp Function
10/n
No rate limiting while creating accounts
No rate limiting while creating accounts
11/n
Email verification link does not expire after use
Email verification link does not expire after use
12/n
Email Verification Bypass
Email Verification Bypass
14/n
Weak password policy
Weak password policy
15/n
Stored HTML Injection
Stored HTML Injection
n/n
Practice Makes Perfect!
Happy Hacking :)
See you here same time tomorrow!
Practice Makes Perfect!
Happy Hacking :)
See you here same time tomorrow!
• • •
Missing some Tweet in this thread? You can try to
force a refresh