Day 0⃣3⃣/2⃣0⃣ -- [How To Hack A Login Page!]
➡️ Day 3, How To Hack A Login Page "Exploiting Vulnerabilities On A Login Page"
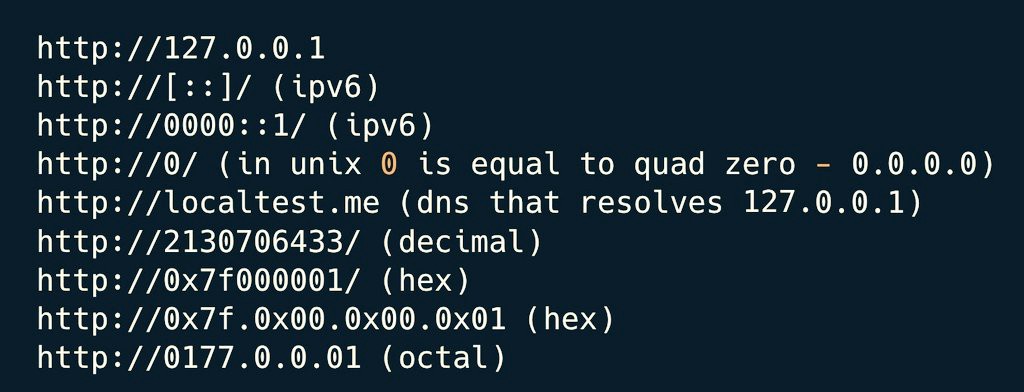
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 3, How To Hack A Login Page "Exploiting Vulnerabilities On A Login Page"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
4/n
BlackHat Cookie Hijacking
BlackHat Cookie Hijacking
6/n
Account Takeover using multiple vulnerabilities
Account Takeover using multiple vulnerabilities
7/n
Reflected XSS after login
Reflected XSS after login
10/n
OTP Bypass - No Rate Limit
OTP Bypass - No Rate Limit
11/n
OTP Bypass Via Response Manipulation
OTP Bypass Via Response Manipulation
13/n
Sql 1njection on Login Page
Sql 1njection on Login Page
14/n
Admin Password via SQL Injection Vulnerability
Admin Password via SQL Injection Vulnerability
15/n
Weak login function - over http
Weak login function - over http
16/n
Admin panel login Bypass
Admin panel login Bypass
n/n
Practice Makes Perfect!
Have a lovely weekend, Don't Drink & Drive!
Happy Hacking :)
See you here same time tomorrow!
Practice Makes Perfect!
Have a lovely weekend, Don't Drink & Drive!
Happy Hacking :)
See you here same time tomorrow!
• • •
Missing some Tweet in this thread? You can try to
force a refresh