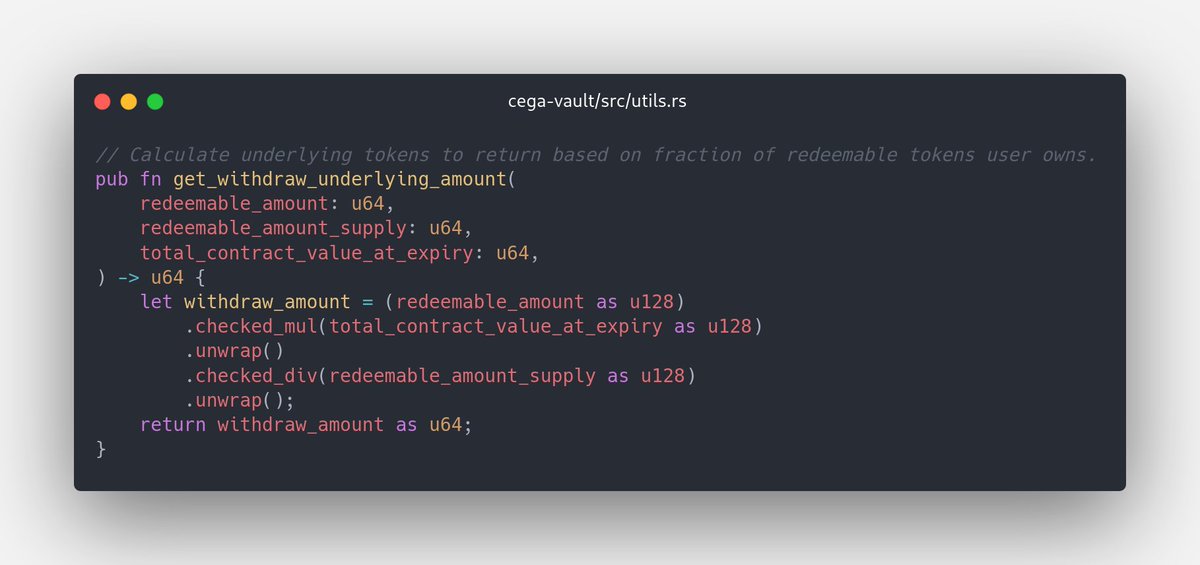
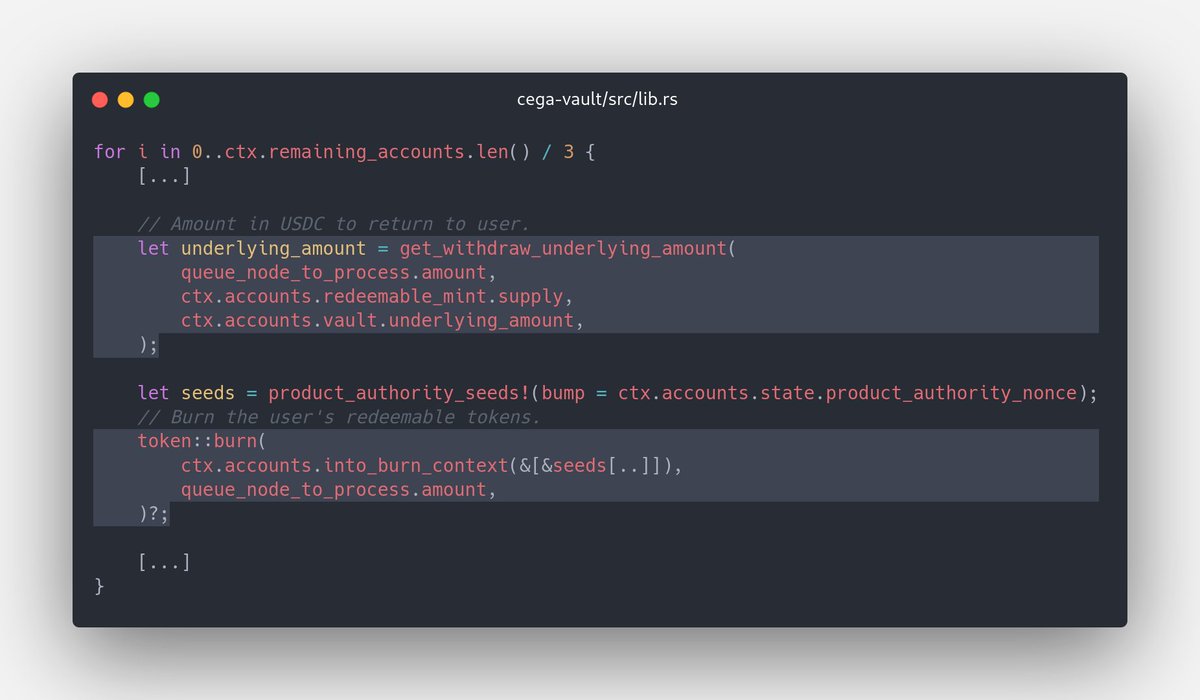
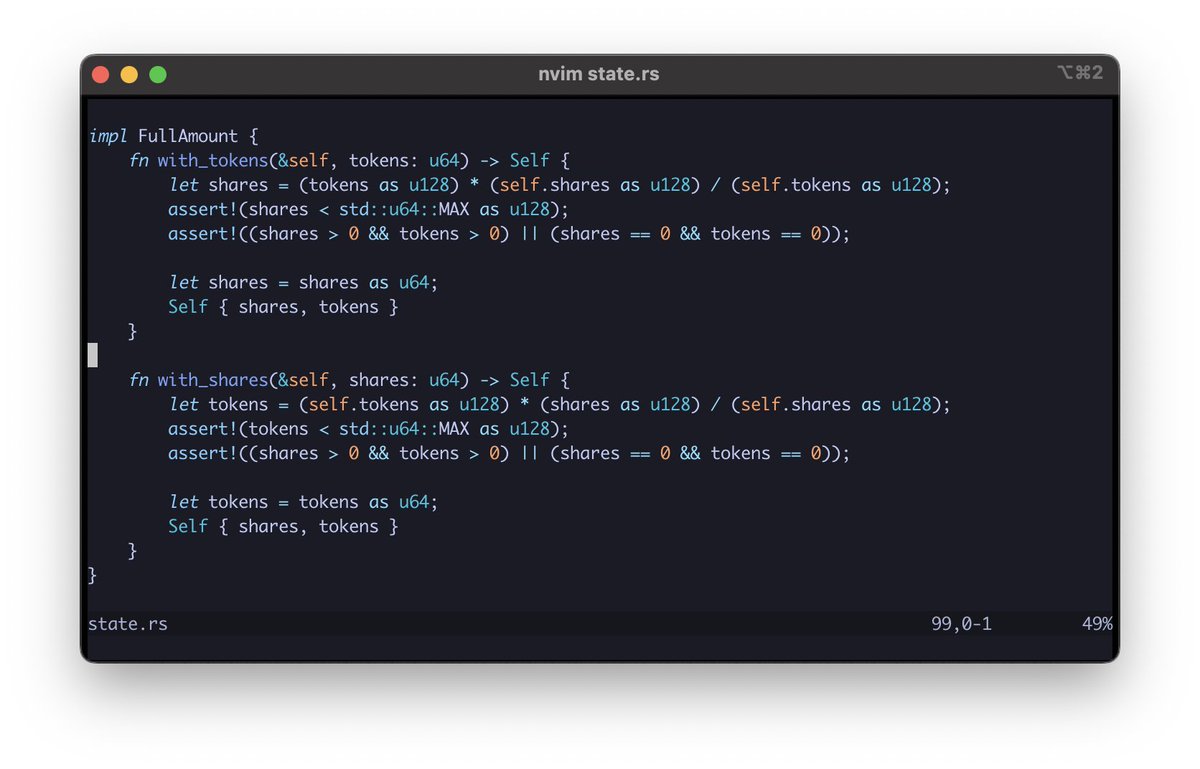
1/ Alameda has been a long-standing, loyal security audit client of ours. We also work closely with many projects on Solana, many of which are directly or indirectly affected by FTX’s insolvency.
Here’s our perspective.
Here’s our perspective.
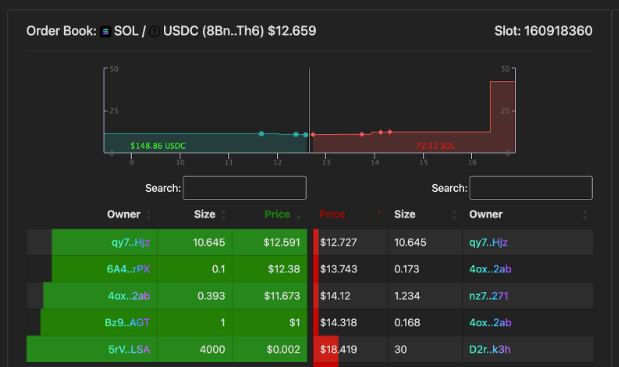
2/ Even before FTX filed for bankruptcy, there were some red flags. A few days prior, their Solana USDC Account ran out of funds for withdrawals.
https://twitter.com/NotDeGhost/status/1590469676337070081
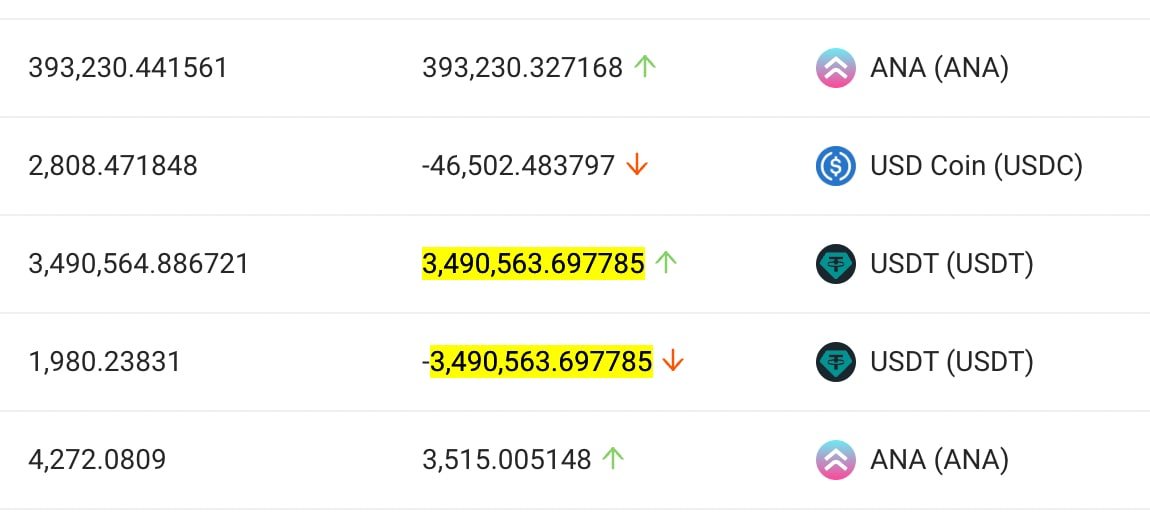
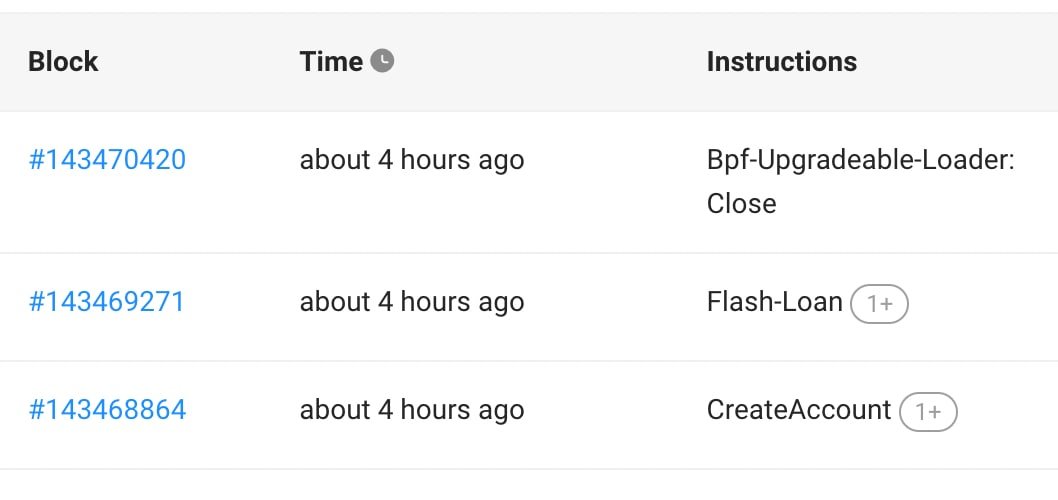
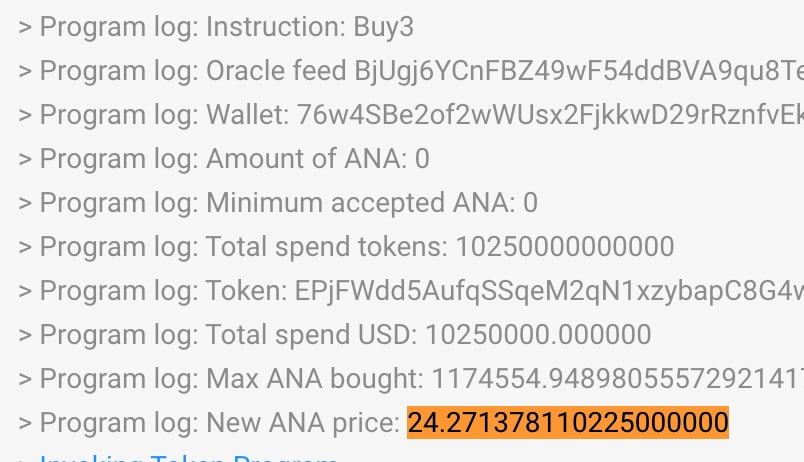
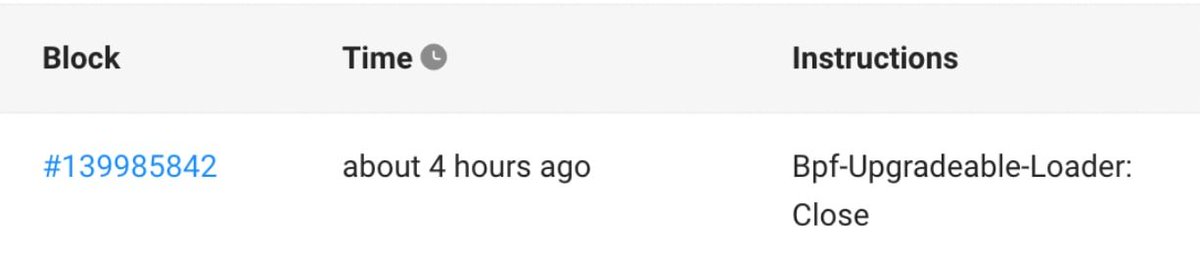
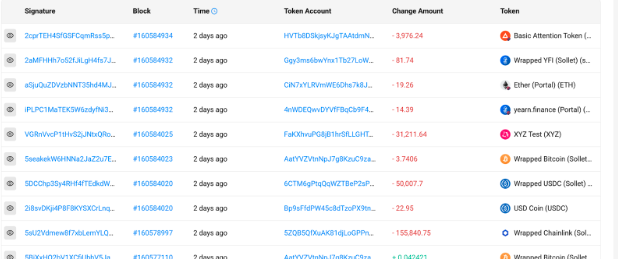
3/ Soon after the confirmed insolvency, suspicious transactions emerged on the FTX side, draining roughly $1B in user funds. A variety of token types were drained over the course of a few hours.
solscan.io/account/JBpj7y…
solscan.io/account/JBpj7y…
4/ Concerns were also raised around the safety of projects such as Serum, which have since been resolved by the efforts of:
https://twitter.com/m_schneider/status/1591636082890006529
5/ Sollet wrapped assets also lost their value. Thankfully, these assets were already in the process of being derisked on most major projects.
https://twitter.com/weremeow/status/1591473567778086917
6/ Looking forward, we strongly recommend using multisigs as a safe and secure way to custody assets. Protocols should also switch deployment keys over to a multisig if possible.
7/ Regardless of the recent happenings, we remain committed to ensuring the security of the Web3 ecosystem. The team at Alameda and FTX are some of the most intelligent engineers we’ve worked with, and we wish them the best moving forward.
To clarify, our engagement with Alameda consisted of their onchain programs alone. We were unfortunately, like many others, not involved or aware of the existence of any offchain backdoors.
• • •
Missing some Tweet in this thread? You can try to
force a refresh