How to get URL link on X (Twitter) App

 Many economic exploits and oracle manipulation attacks are a result of treating high and low volatility assets the same.
Many economic exploits and oracle manipulation attacks are a result of treating high and low volatility assets the same.
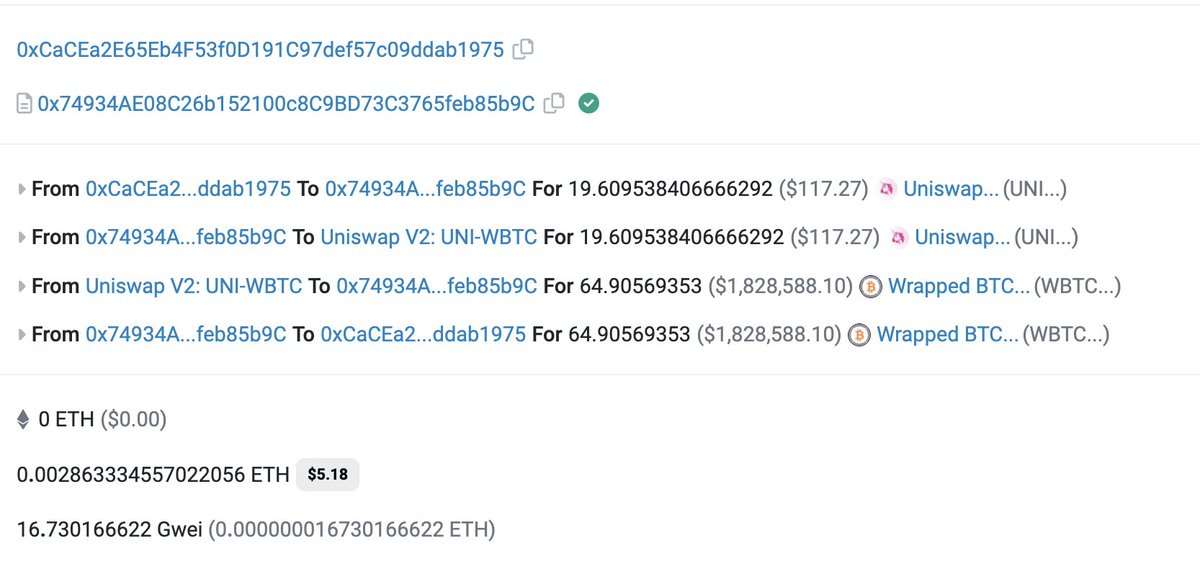
 It appears a (malicious?) validator spliced in their transaction, stealing funds from a MEV bot attempting to front-run.
It appears a (malicious?) validator spliced in their transaction, stealing funds from a MEV bot attempting to front-run. 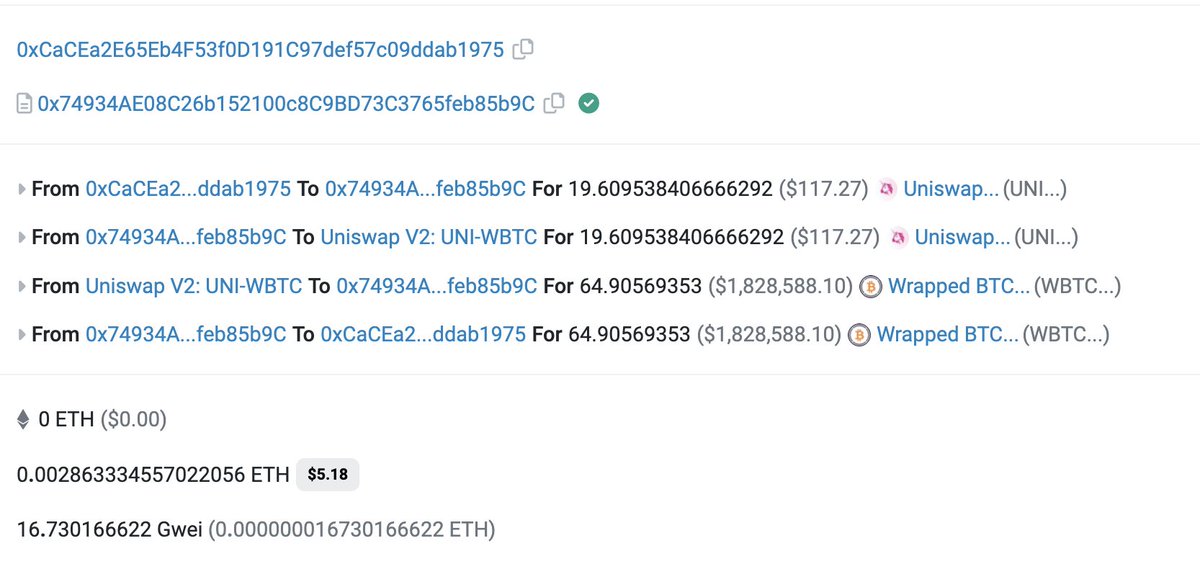

 The attacker is repeatedly invoking the withdraw_pnl instruction to withdraw fees from Raydium pools.
The attacker is repeatedly invoking the withdraw_pnl instruction to withdraw fees from Raydium pools. 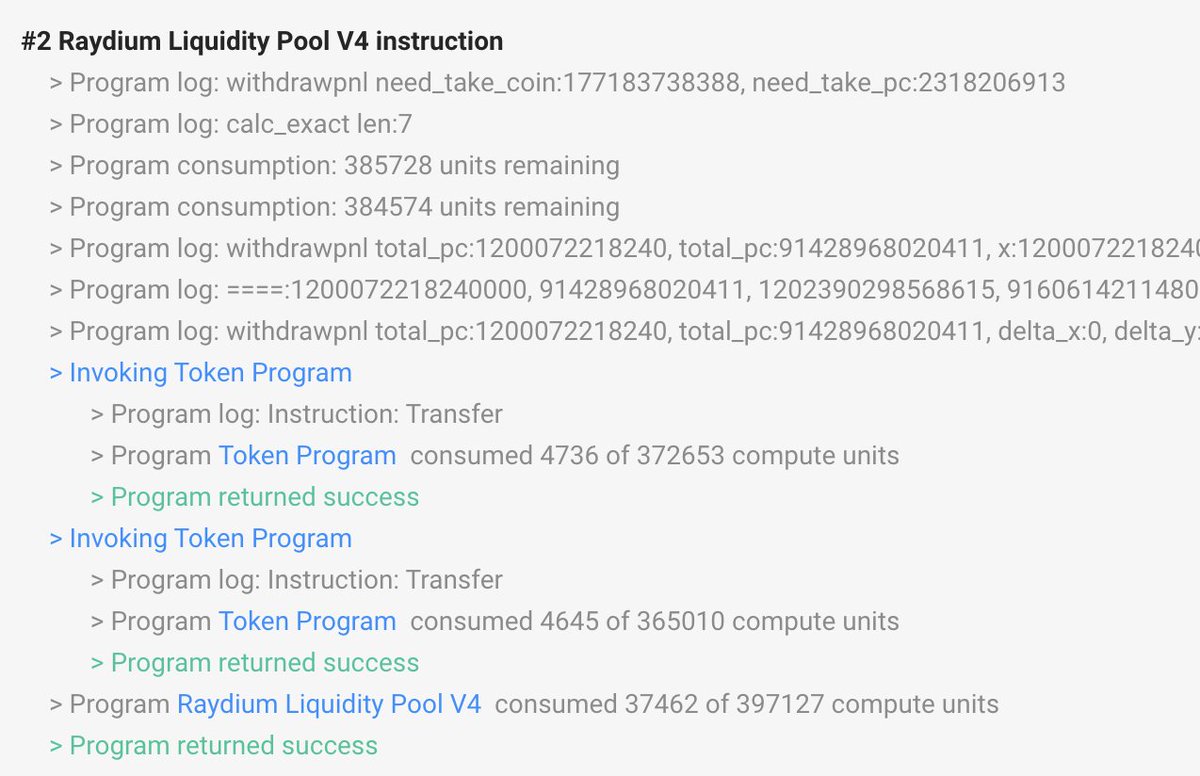
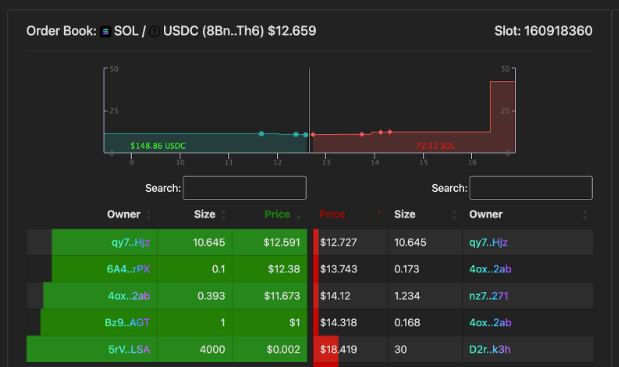
 2/ Even before FTX filed for bankruptcy, there were some red flags. A few days prior, their Solana USDC Account ran out of funds for withdrawals.
2/ Even before FTX filed for bankruptcy, there were some red flags. A few days prior, their Solana USDC Account ran out of funds for withdrawals.https://twitter.com/NotDeGhost/status/1590469676337070081
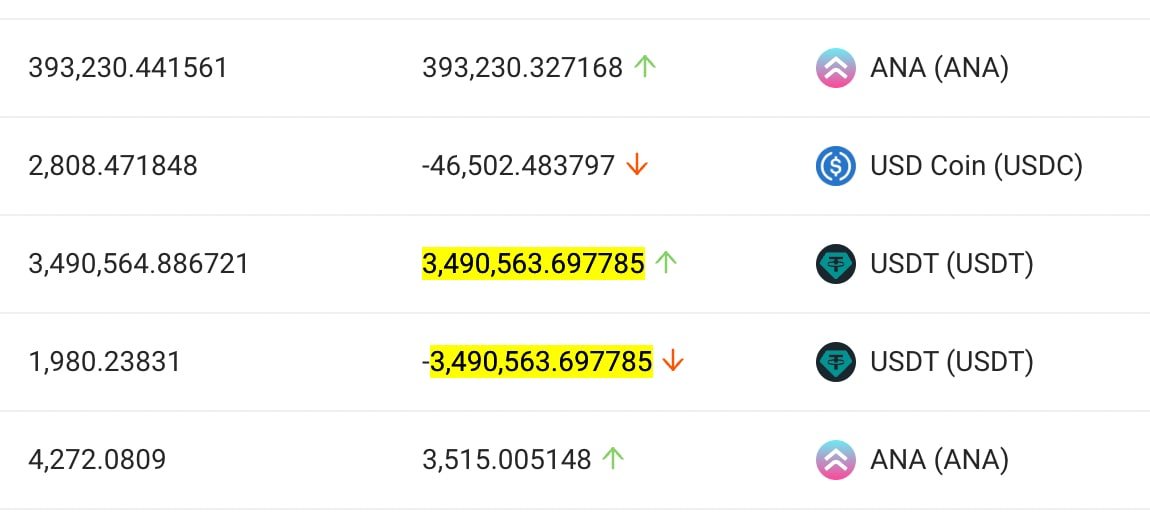
 2/ This hack beared many similarities to previous hacks. Similar to the @Crema_Finance hack, this too used Solend flashloans.
2/ This hack beared many similarities to previous hacks. Similar to the @Crema_Finance hack, this too used Solend flashloans. 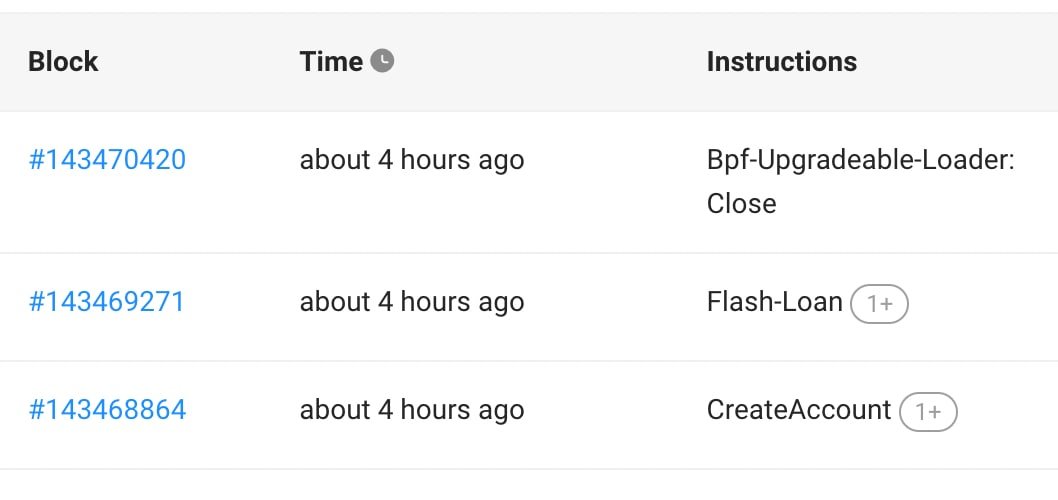


 In order to utilize flashloans, the attacker had to deploy their own onchain program. Unfortunately, this program was quickly closed after the exploit.
In order to utilize flashloans, the attacker had to deploy their own onchain program. Unfortunately, this program was quickly closed after the exploit.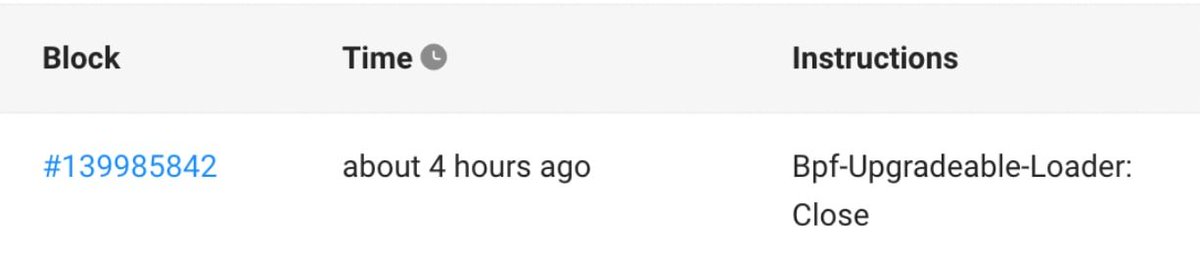
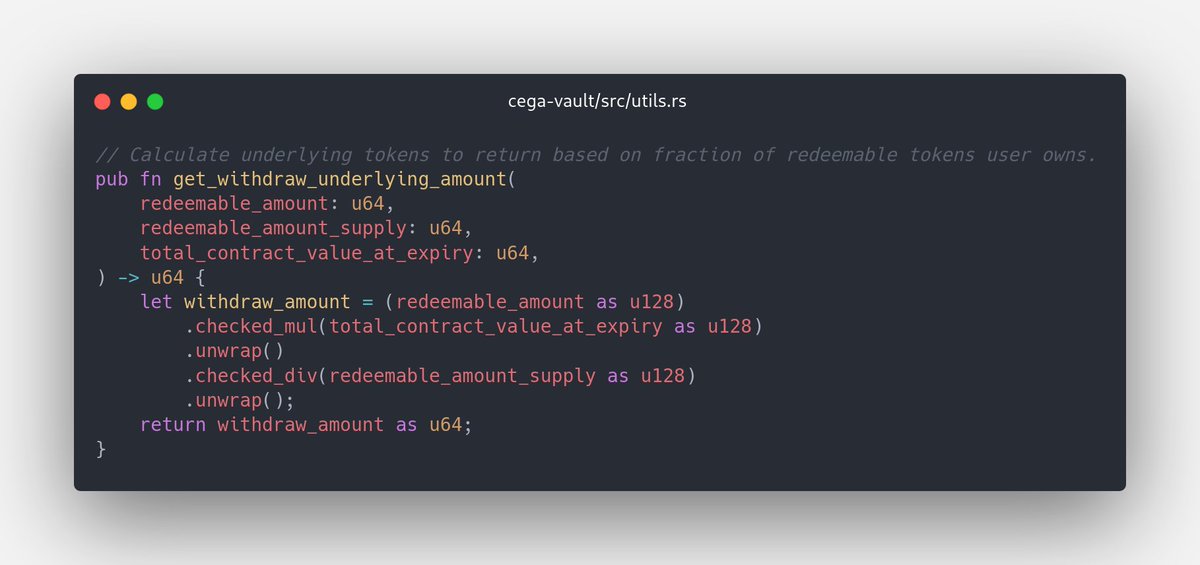


 2/ When implementing an arbitrage bot, we came across some unexpected behavior. We were somehow getting tokens out of nothing. In other words, we were able to put in 0 tokens and get out 1 token.
2/ When implementing an arbitrage bot, we came across some unexpected behavior. We were somehow getting tokens out of nothing. In other words, we were able to put in 0 tokens and get out 1 token.

 2/ In Jet’s original conversion code between tokens and shares, all rounding was done via floor division. This meant that the correctness of the code depended on floor division to not be in favor of the user.
2/ In Jet’s original conversion code between tokens and shares, all rounding was done via floor division. This meant that the correctness of the code depended on floor division to not be in favor of the user.
