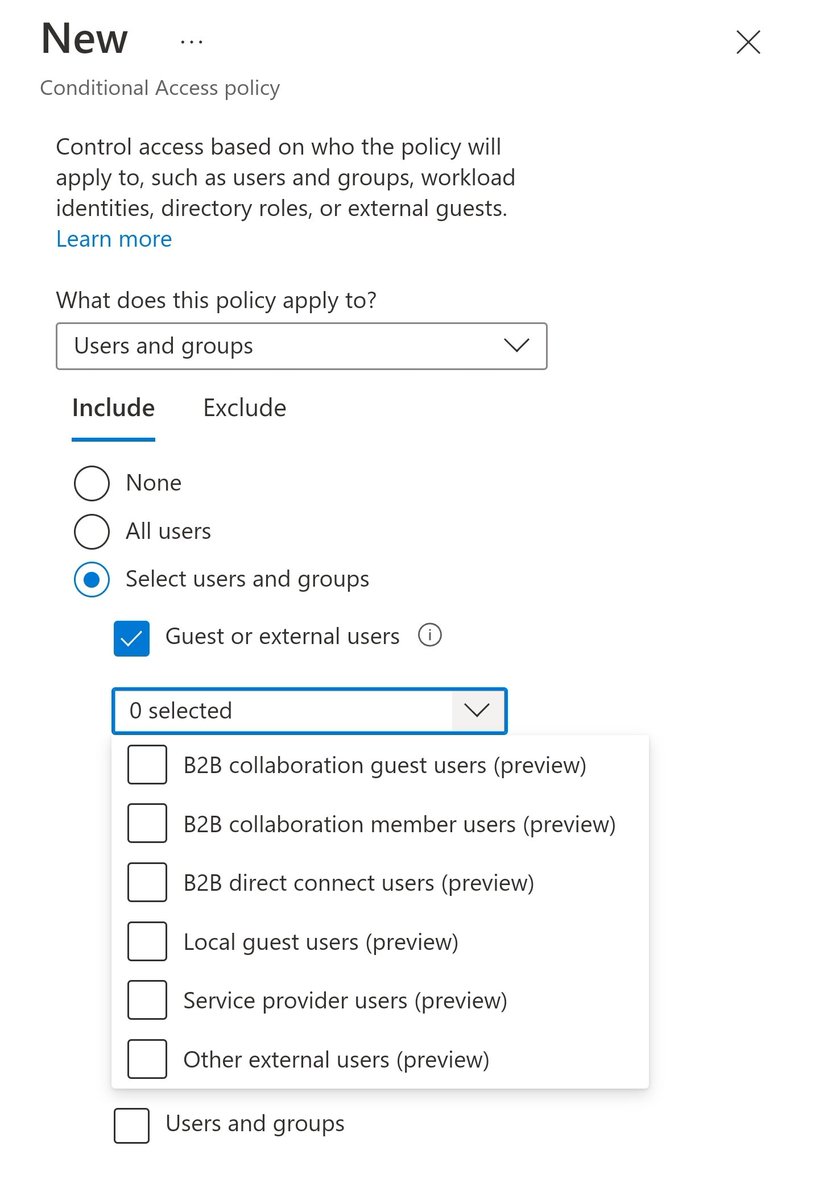
Why is everyone so excited about the new #azuread Authentication Strength feature in Conditional Access that was announced at Ignite last month?
Here's are short thread about the feature.
PS. There is a bonus if you read all the way to the end 😉👇
Here's are short thread about the feature.
PS. There is a bonus if you read all the way to the end 😉👇

This illustration from @Yubico shows that not all MFA is of equal strength when protecting your users. Some like Phone number and email are very weak compared to others.
I shared more about this in a previous thread
I shared more about this in a previous thread
https://twitter.com/merill/status/1587216547894157312?s=20&t=AzbQLyqFTz9565eociL2nA

Moving away from Voice and SMS is in fact called out by NIST who classify PSTN based auth like SMS and Voice as RESTRICTED.
They explain in more detail in this FAQ.
pages.nist.gov/800-63-FAQ/#q-…
They explain in more detail in this FAQ.
pages.nist.gov/800-63-FAQ/#q-…

That's all well and good but moving our users off Voice/SMS is going to take some time.
Now this is where Authentication Strength comes into play. Before this feature was released, the only way to remove phone MFA was to turn it off at the tenant level at adlegacymfa.cmd.ms
Now this is where Authentication Strength comes into play. Before this feature was released, the only way to remove phone MFA was to turn it off at the tenant level at adlegacymfa.cmd.ms

As you can imagine it's going to be total chaos if you unchecked the Phone and SMS options for all your users.
Instead what you really want is to gradually improve the auth strength in your org.
An ideal place to start could be to remove Phone/SMS for privileged admin users.
Instead what you really want is to gradually improve the auth strength in your org.
An ideal place to start could be to remove Phone/SMS for privileged admin users.
Applying Auth Strengths is a two step process.
#1 Decide/ define the Authentication Strength
You can use one of the built-in strengths or create your own.
Here I'm following NIST guidelines and creating a custom auth strength that excludes SMS & Voice.
#1 Decide/ define the Authentication Strength
You can use one of the built-in strengths or create your own.
Here I'm following NIST guidelines and creating a custom auth strength that excludes SMS & Voice.

#2 Enforce the Auth Strength using a Conditional Policy
Next we head over to adca.cmd.ms and define a CA policy that requires this new auth strength.
Since this is in CA you get to use all the various filters to scope the where and when this strength is enforced.
Next we head over to adca.cmd.ms and define a CA policy that requires this new auth strength.
Since this is in CA you get to use all the various filters to scope the where and when this strength is enforced.

All set!
Now the most important part. What is the user's experience?
If their original MFA doesn't meet the requirement the user is prompted with a step up experience to the stronger auth.
For this user we applied a policy that excluded Voice.
Now the most important part. What is the user's experience?
If their original MFA doesn't meet the requirement the user is prompted with a step up experience to the stronger auth.
For this user we applied a policy that excluded Voice.

Interested in learning more about this feature?
Click Set Reminder below and you get to chat with the folks that built this feature including @inbarck and @YusukeKodama85 as they join @JefTek, @BaileyBercik and myself in spaces this week.
twitter.com/i/spaces/1ynJO…
Click Set Reminder below and you get to chat with the folks that built this feature including @inbarck and @YusukeKodama85 as they join @JefTek, @BaileyBercik and myself in spaces this week.
twitter.com/i/spaces/1ynJO…
Did you like this? Please retweet this thread and share.
Plus, feel free to follow me, I try to post at least one new topic each week.
Plus, feel free to follow me, I try to post at least one new topic each week.
• • •
Missing some Tweet in this thread? You can try to
force a refresh