
Product Manager @microsoft | Tweets my own
Built → https://t.co/ujxKqxXjf2 • https://t.co/QbUp63ffXf • Graph XRay • https://t.co/tSWrIw8Ajh
📰 Newsletter→ https://t.co/tPzAEl0Zuq
🎙️ Podcast→ https://t.co/TBlNKTzn8t
How to get URL link on X (Twitter) App

https://x.com/merill/status/1991753664499982661?s=20

 Who doesn't like Free!
Who doesn't like Free!

 Threat actors love apps.
Threat actors love apps. 
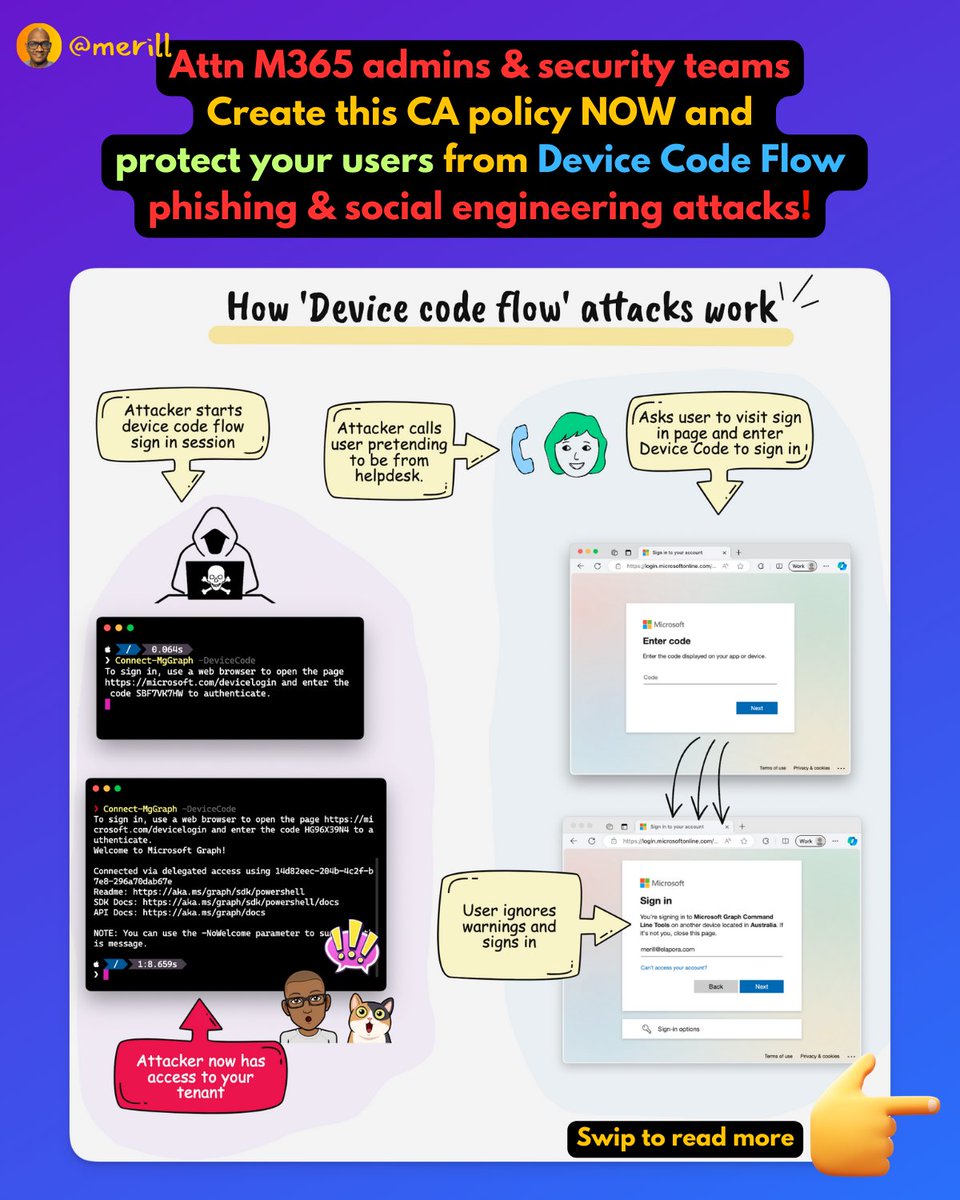
 ❇️ Why does device code flow exist?
❇️ Why does device code flow exist?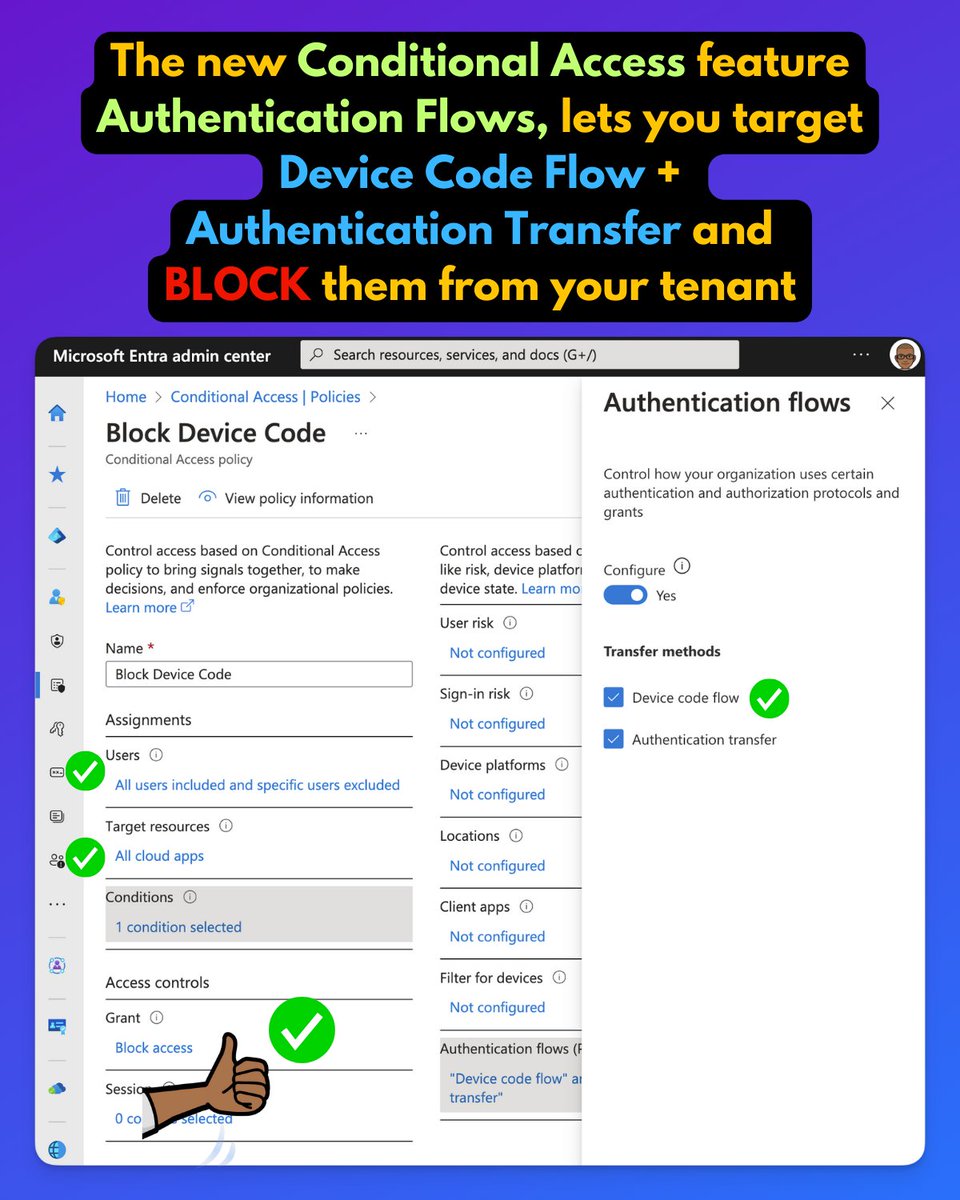
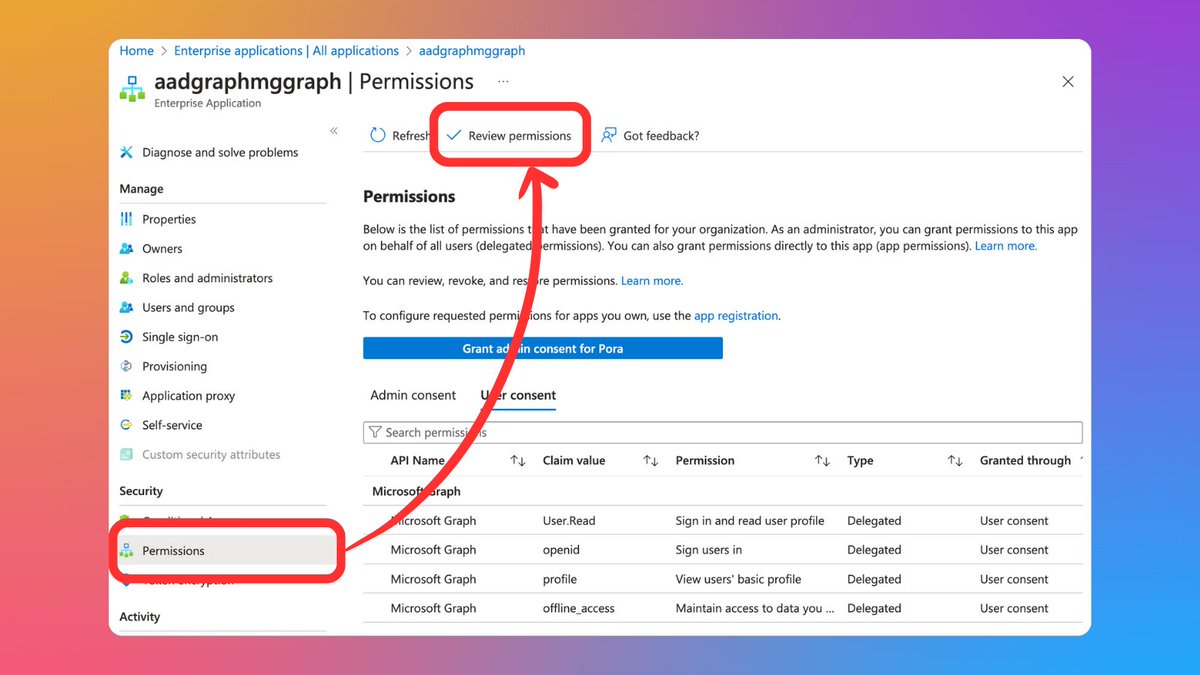
 Select 'This app is malicious and I'm compromised'
Select 'This app is malicious and I'm compromised' 



 💠
💠 
 Start by creating a CA policy.
Start by creating a CA policy.

 #1 Auth methods allowed for user
#1 Auth methods allowed for user

 Today users can choose their default sign-in method
Today users can choose their default sign-in method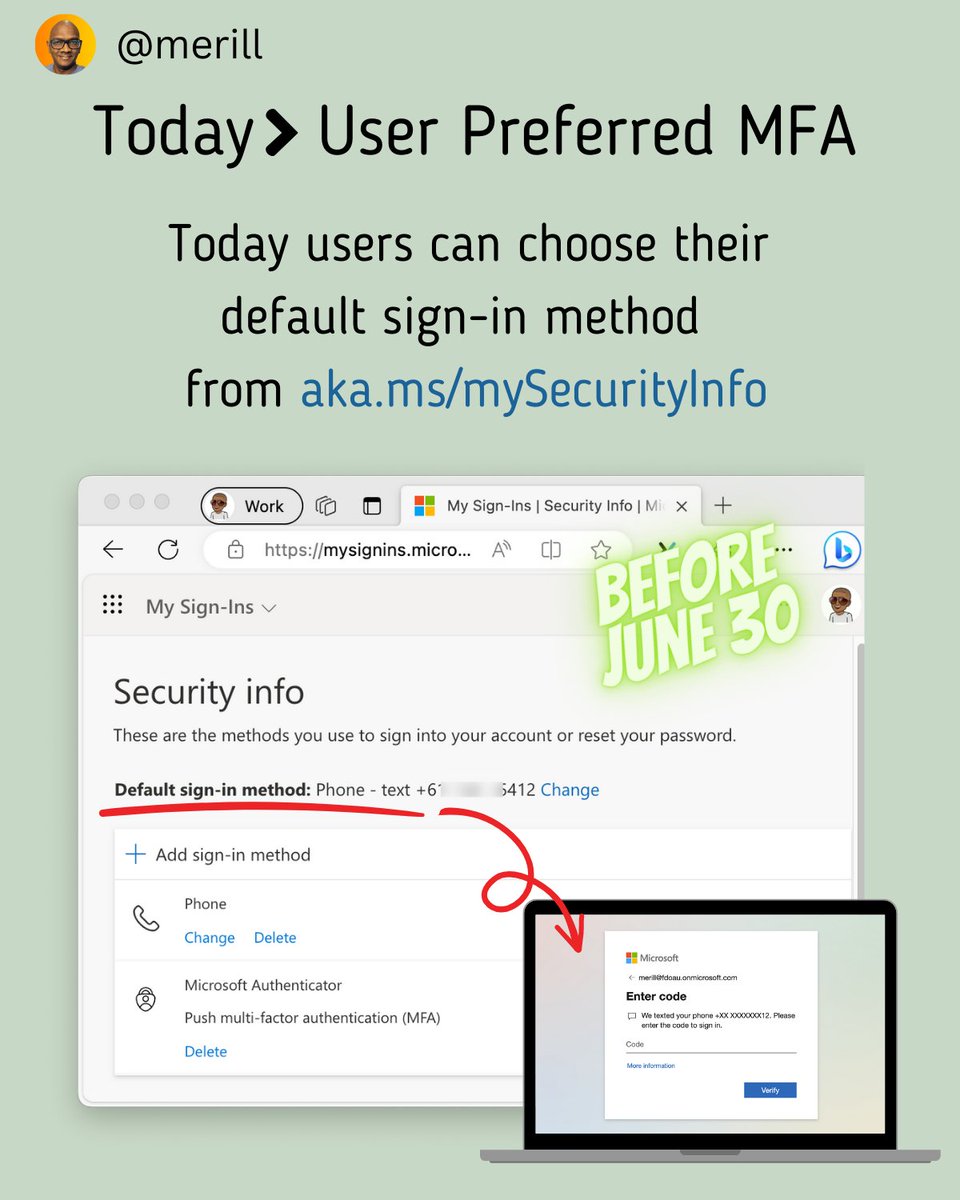

 Most enterprises I work with are putting together a roadmap to get to the highest maturity level over the next few years.
Most enterprises I work with are putting together a roadmap to get to the highest maturity level over the next few years. 

 The first one is Microsoft Authenticator App Number matching. Switching from push notifications to number match as the default was scheduled for last month.
The first one is Microsoft Authenticator App Number matching. Switching from push notifications to number match as the default was scheduled for last month.

 When your users connect, they will need to pass in the ClientId to use the custom app.
When your users connect, they will need to pass in the ClientId to use the custom app.

 With Solorigate attackers impersonated a cloud IDP and then hid in the cloud by creating credentials against multi-tenant apps.
With Solorigate attackers impersonated a cloud IDP and then hid in the cloud by creating credentials against multi-tenant apps.

 Let's say you want to start requiring a FIDO2 security key MFA whenever someone wants to activate the Global Administrator role.
Let's say you want to start requiring a FIDO2 security key MFA whenever someone wants to activate the Global Administrator role.

 Bonus tip, you can install the Messages for Web app on your desktop and pin it to your start menu (Windows) or the dock (mac), heck you can even add it to your home screen on your iPhone and iPad 🚀
Bonus tip, you can install the Messages for Web app on your desktop and pin it to your start menu (Windows) or the dock (mac), heck you can even add it to your home screen on your iPhone and iPad 🚀 



 This illustration from @Yubico shows that not all MFA is of equal strength when protecting your users. Some like Phone number and email are very weak compared to others.
This illustration from @Yubico shows that not all MFA is of equal strength when protecting your users. Some like Phone number and email are very weak compared to others.https://twitter.com/merill/status/1587216547894157312?s=20&t=AzbQLyqFTz9565eociL2nA

