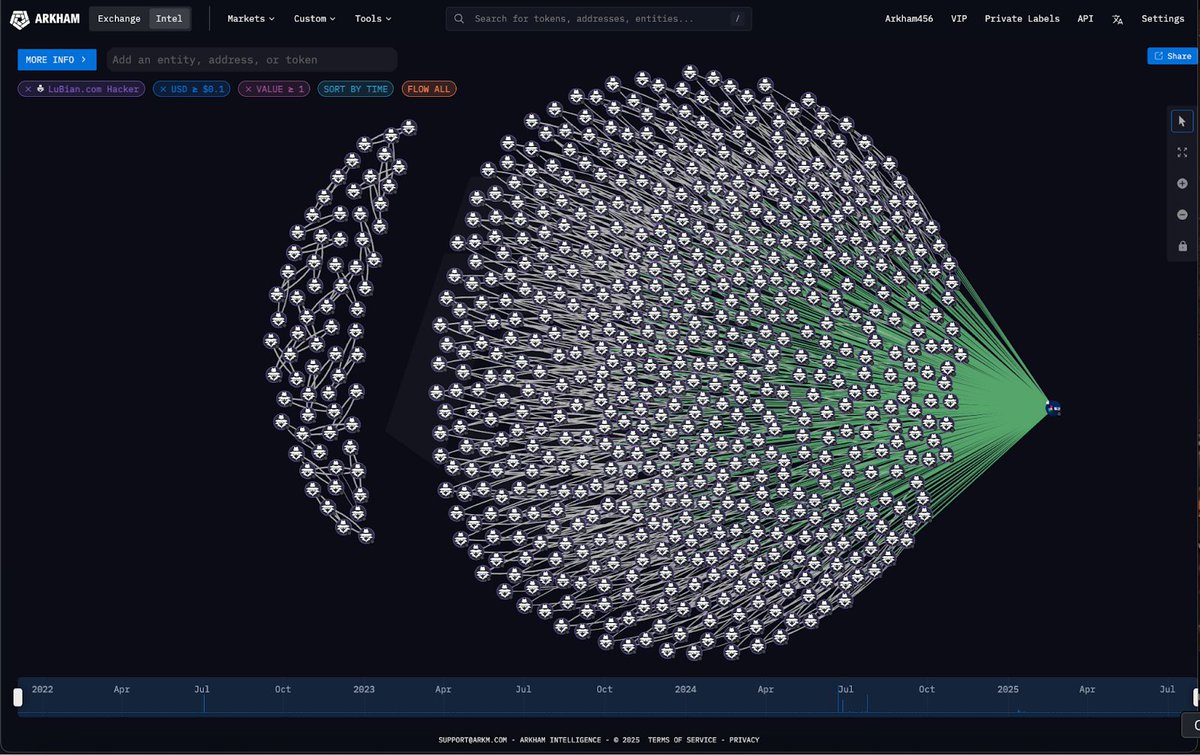
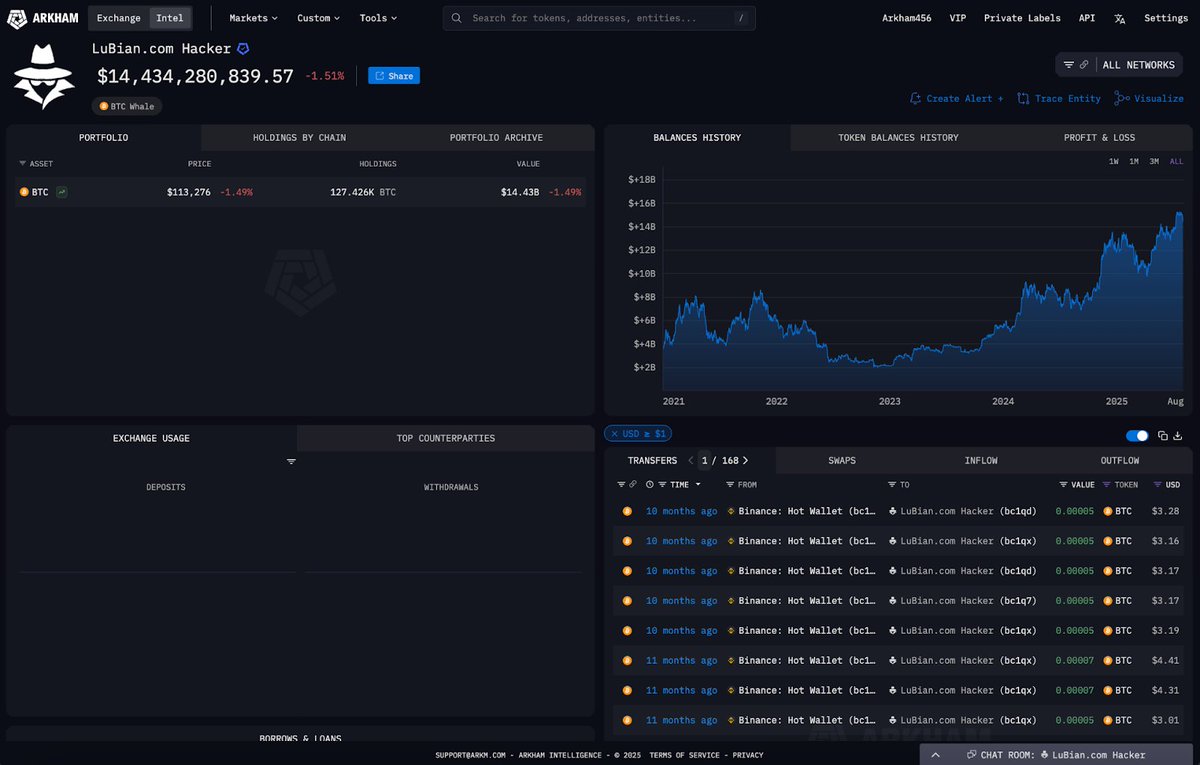
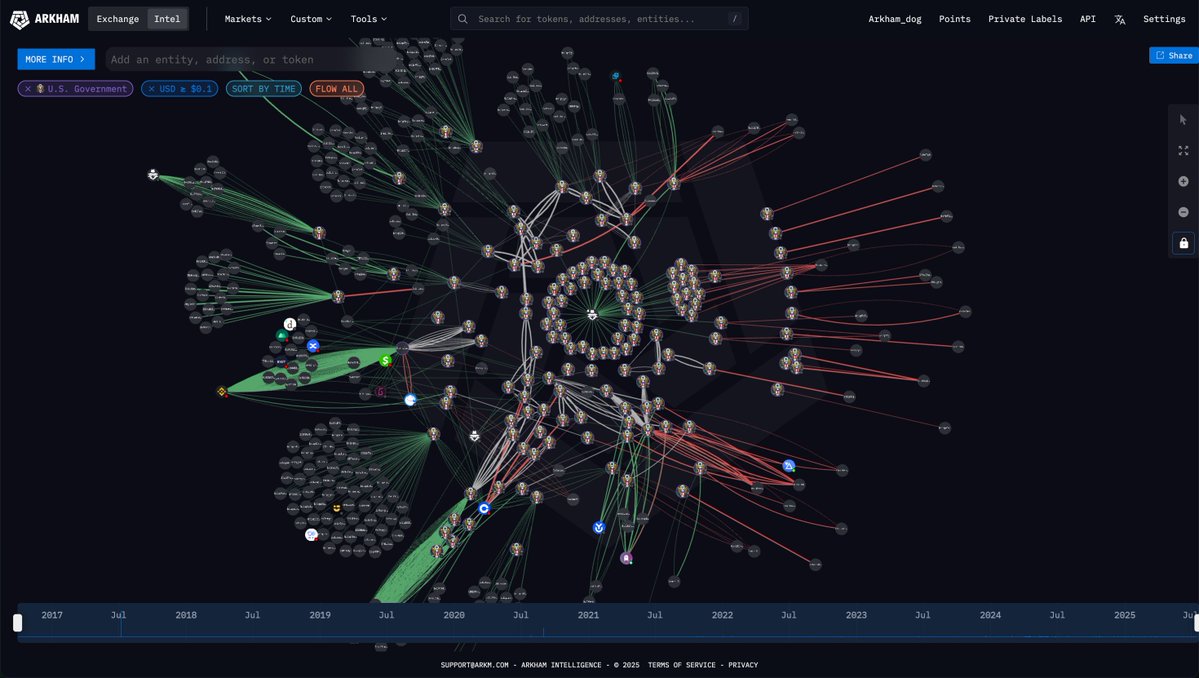
We are now 3 days deep into the attack on FTX.
So far, Paxos has blacklisted 4 addresses, and the attacker has repeatedly bridged to and from multiple different networks.
What will the FTX attacker do next?
An update on their current token balances and actions so far 👇
So far, Paxos has blacklisted 4 addresses, and the attacker has repeatedly bridged to and from multiple different networks.
What will the FTX attacker do next?
An update on their current token balances and actions so far 👇

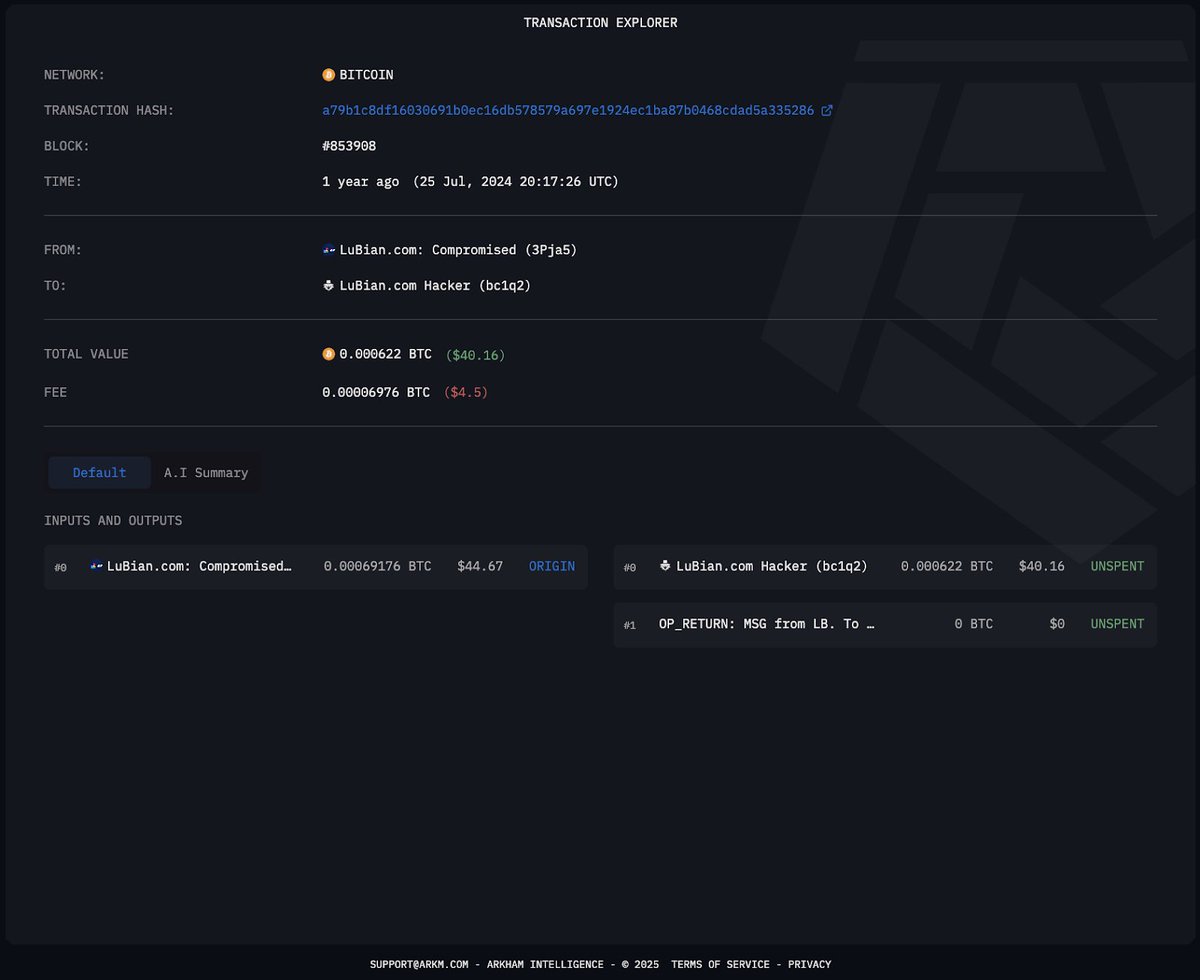
The original address that tokens were sent to, 0x59, received and dumped a multitude of FTX's remaining token holdings.
The attacker appeared to be panicking, and lost a large amount of their token holdings to slippage.
The attacker appeared to be panicking, and lost a large amount of their token holdings to slippage.
They also tried using different DEX aggregators including 1inch, Cowswap and DODO exchange.
In order to prevent slippage, the attacker was forced to sell PAXG, LINK and MATIC in batches.
In order to prevent slippage, the attacker was forced to sell PAXG, LINK and MATIC in batches.

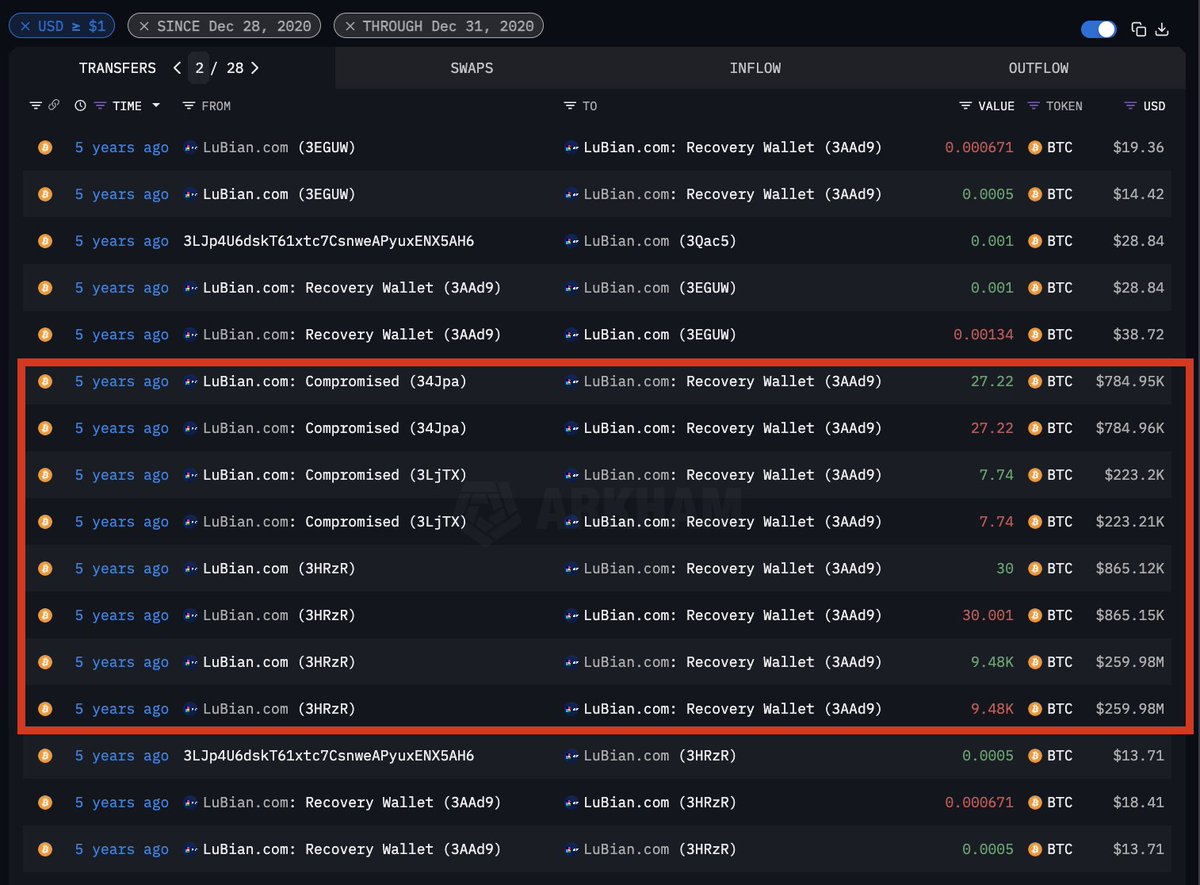
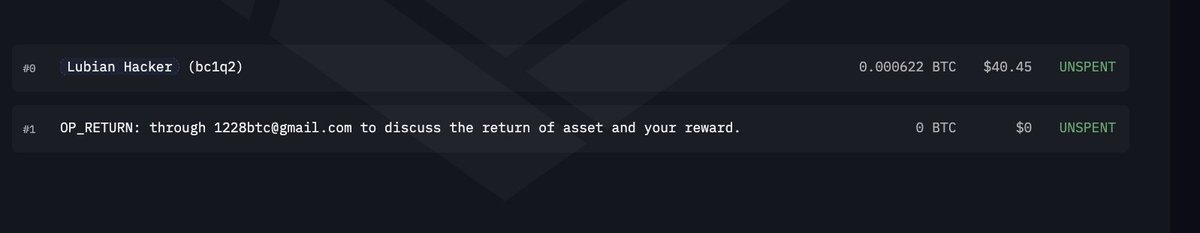
The attacker also sent funds to different wallets, distributing a total of just under 3000 PAXG to 3 separate wallets that were all subsequently blacklisted.
The attacker did not manage to get rid of all of their token holdings before their funds were frozen by Paxos.
The attacker did not manage to get rid of all of their token holdings before their funds were frozen by Paxos.

The attacker has been consolidating a balance of DAI and ETH, tokens that cannot be blacklisted or frozen on the ETH mainnet.
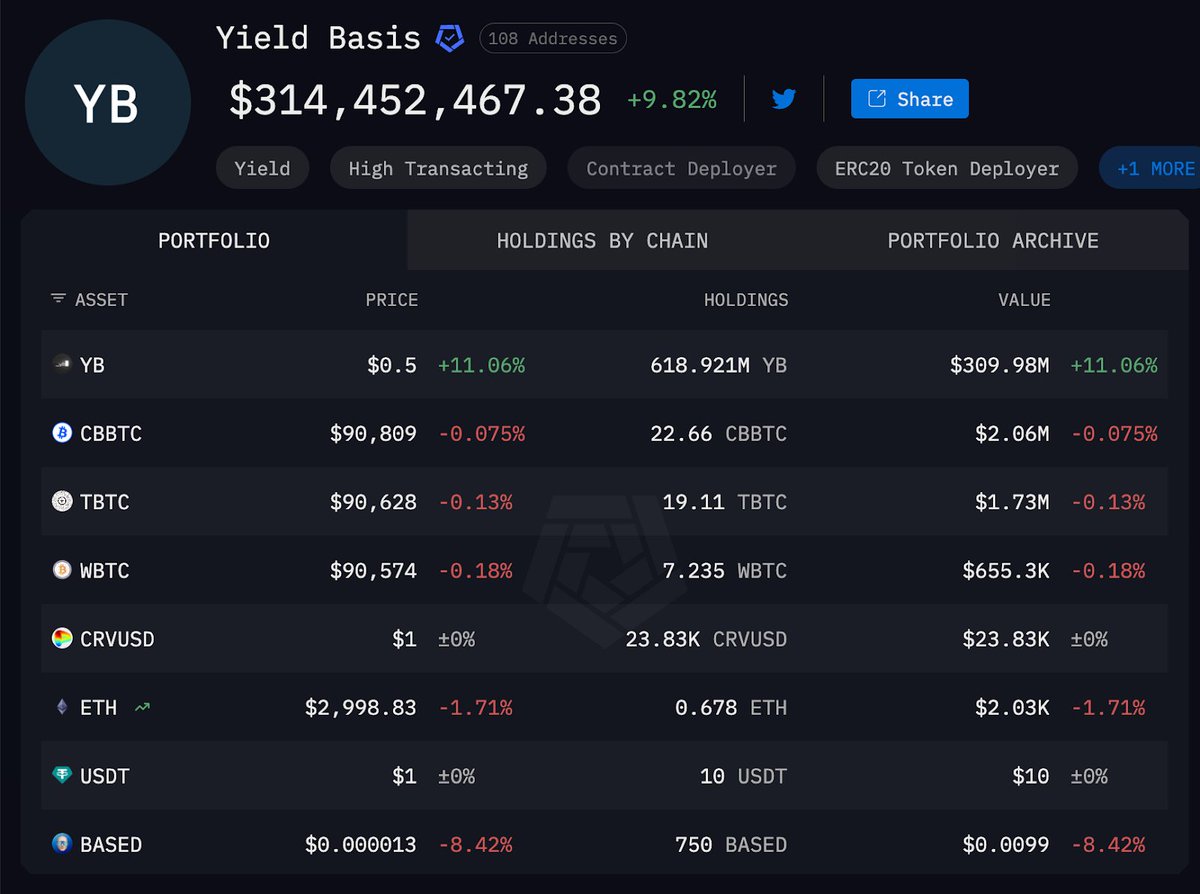
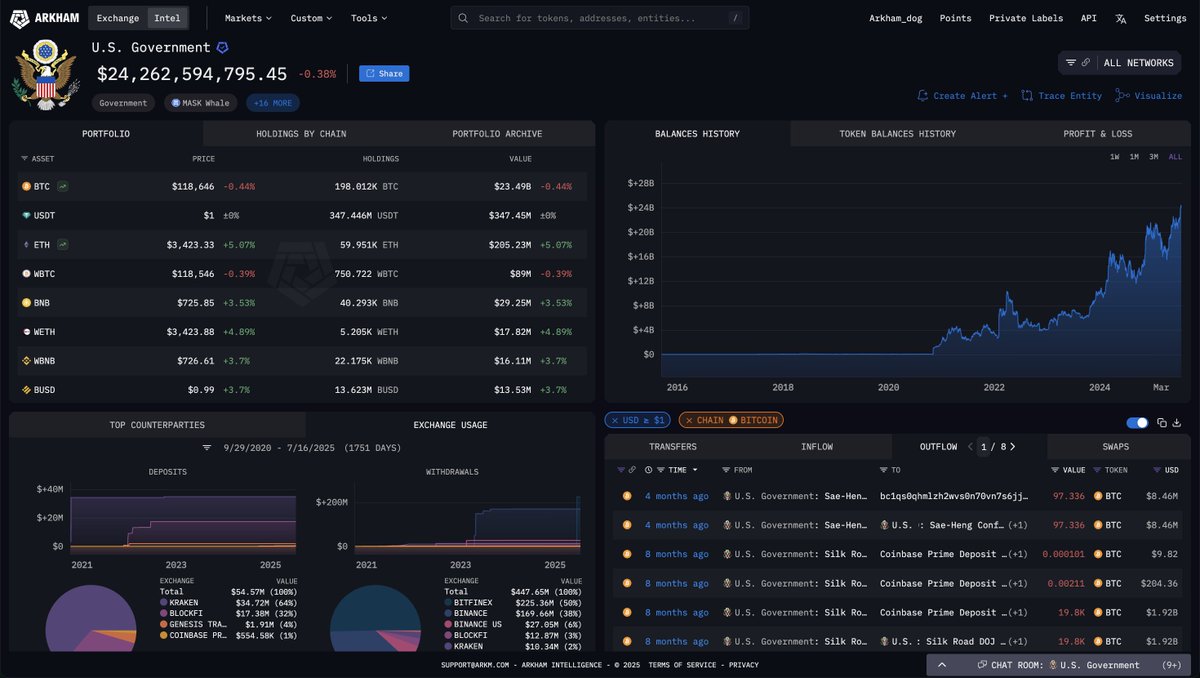
Currently, these are their current token balances on ETH mainnet.
FYI: the attacker also holds ~$55 million over BSC, Polygon and Avalanche networks.
Currently, these are their current token balances on ETH mainnet.
FYI: the attacker also holds ~$55 million over BSC, Polygon and Avalanche networks.

This address, 0x2cb, then bridged USDC back to Ethereum through Multichain/Anyswap, and now holds its balance entirely in Ether. 

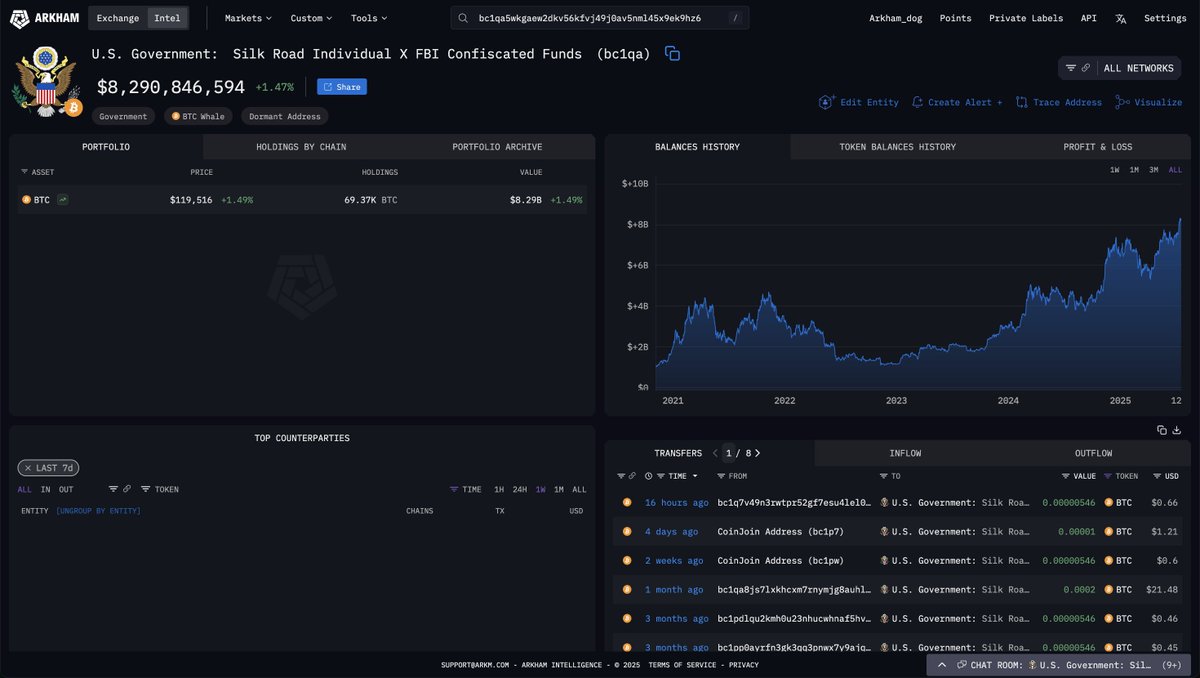
A total of almost $20 million in PAXG was frozen across the attacker's 4 addresses that hold PAXG.
The attacker also attempted to obfuscate fund transfers on BSC by 'swapping' tokens with the recipient address set to a separate address, 0x2cb.
The attacker also attempted to obfuscate fund transfers on BSC by 'swapping' tokens with the recipient address set to a separate address, 0x2cb.

The attacker used the same strategy to send almost $5 million worth of BUSD to a different wallet, 0x525, as USDC.
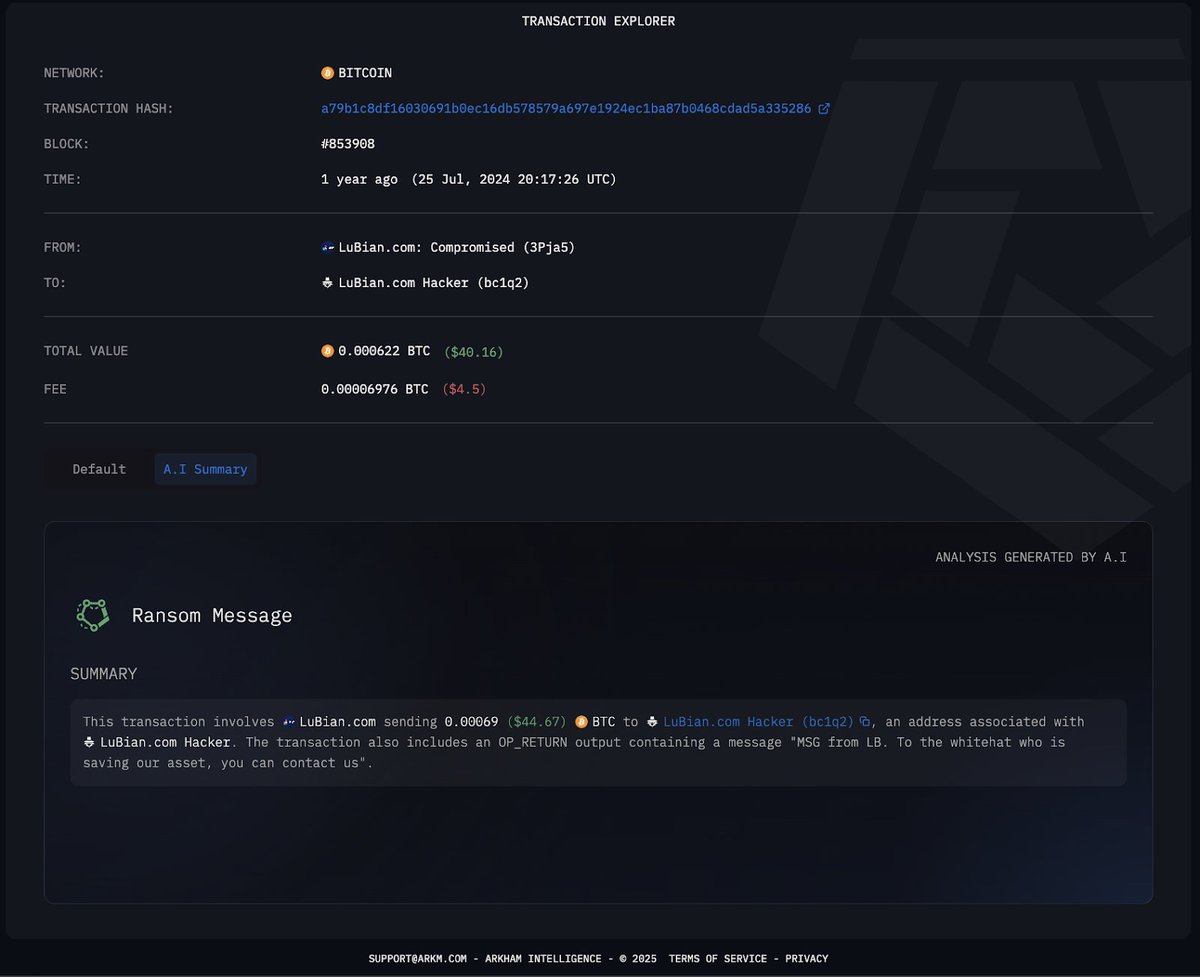
Here on line 3, "address, to" is not set to 0x59, despite 0x59 sending the transaction.
0x525 then bridged funds back to Ethereum, holding around $16m of Ether.
Here on line 3, "address, to" is not set to 0x59, despite 0x59 sending the transaction.
0x525 then bridged funds back to Ethereum, holding around $16m of Ether.

The attacker also withdrew funds on Polygon, the majority of which they sent to the 0x2cb address featured above.
Around $3.8 million of MATIC was withdrawn from Polygon over the Matic bridge, but the attacker needs to wait 7 days before accessing funds on Ethereum.
Around $3.8 million of MATIC was withdrawn from Polygon over the Matic bridge, but the attacker needs to wait 7 days before accessing funds on Ethereum.

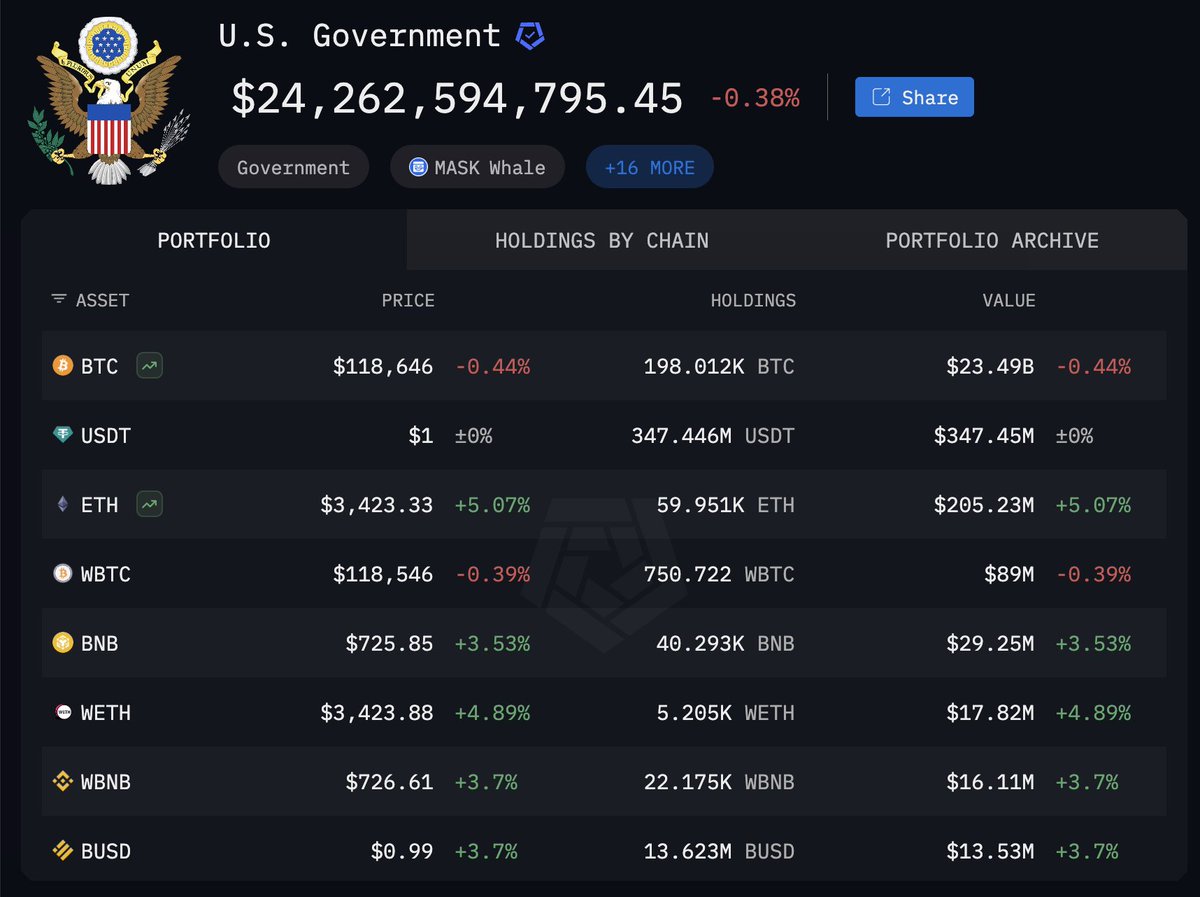
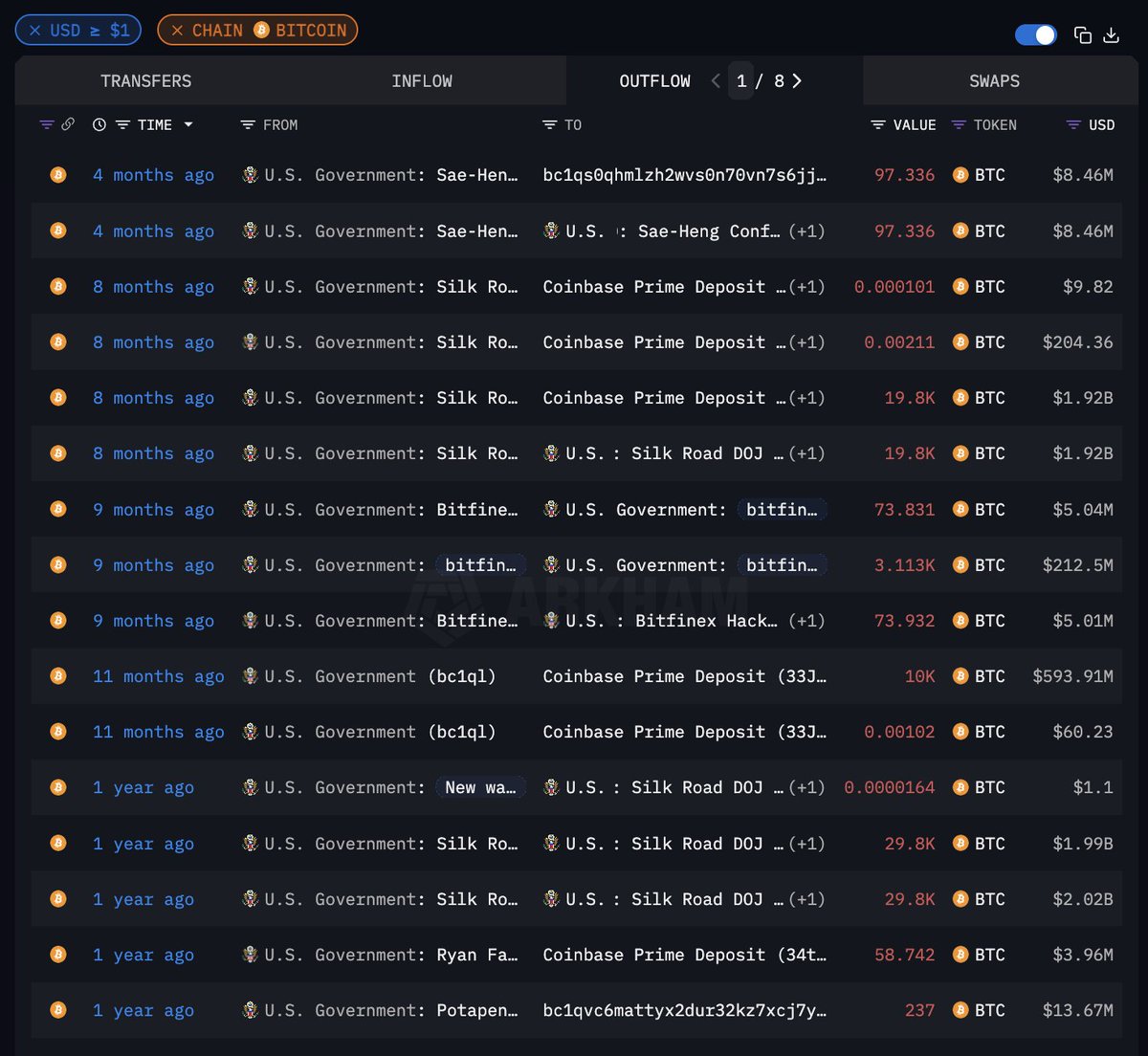
At the moment the hacker holds:
~$215m of Ether
~$48m DAI
~$41m of BNB on BSC
~$20m of frozen PAXG
~$7m DAI on BSC
~$4m USDT on Avalanche
~$3.8m of MATIC in the Matic Bridge
Arkham will provide further updates as the situation develops.
~$215m of Ether
~$48m DAI
~$41m of BNB on BSC
~$20m of frozen PAXG
~$7m DAI on BSC
~$4m USDT on Avalanche
~$3.8m of MATIC in the Matic Bridge
Arkham will provide further updates as the situation develops.
• • •
Missing some Tweet in this thread? You can try to
force a refresh