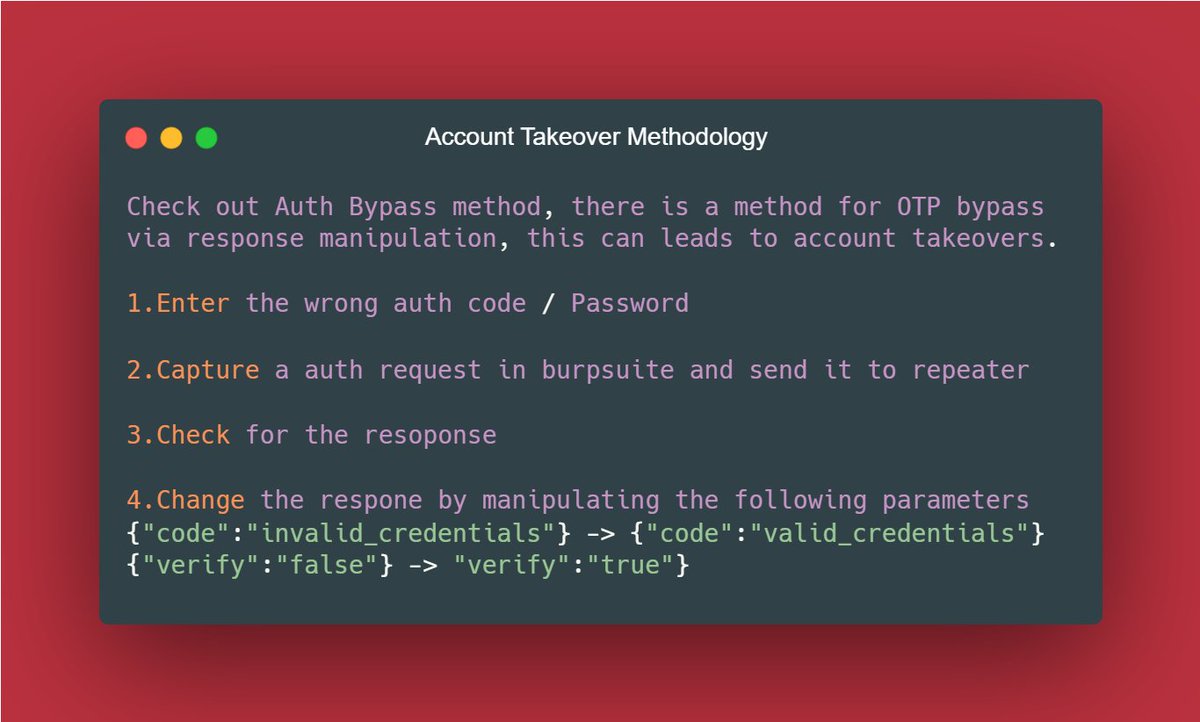
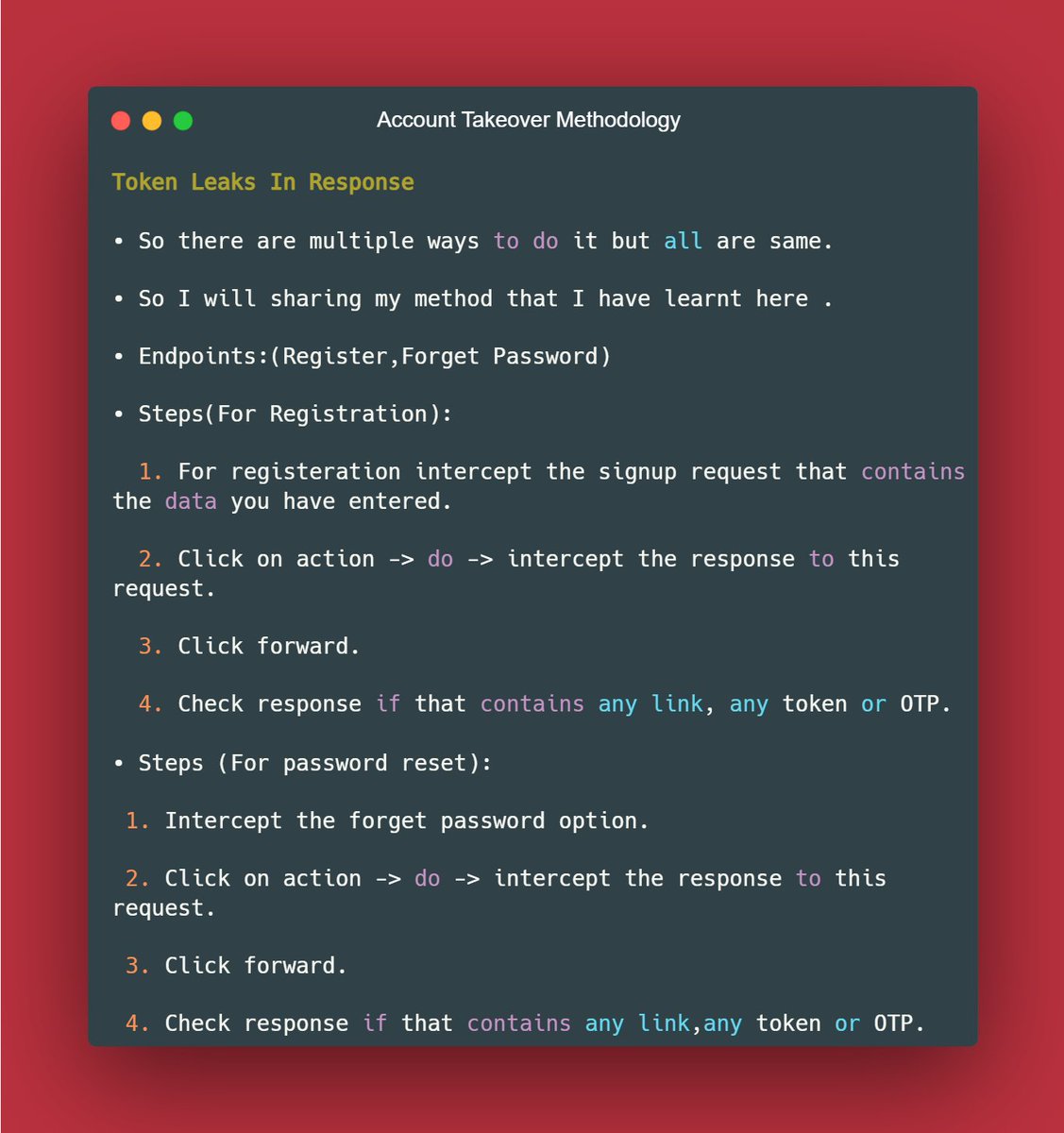
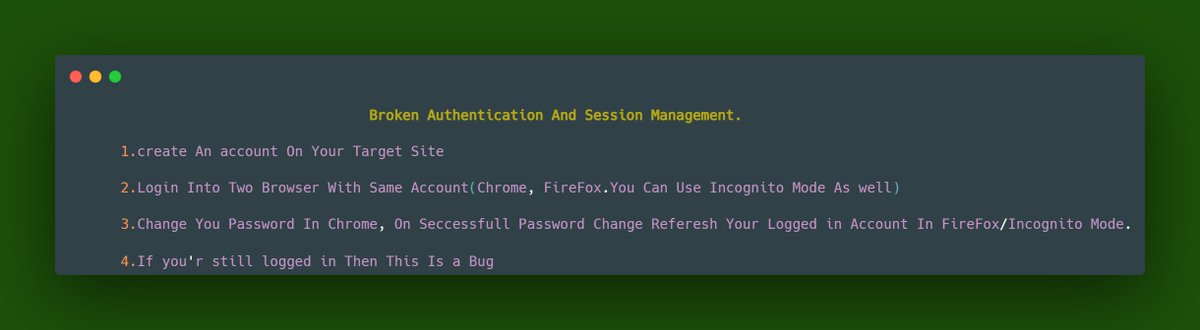
📌Chaining Session Hijacking with XSS
#bugbounty #Infosec
==
My Bugbounty Tips Group Link : 👇
t.me/bugbountyresou…
==
Thread🧵:👇
#bugbounty #Infosec
==
My Bugbounty Tips Group Link : 👇
t.me/bugbountyresou…
==
Thread🧵:👇
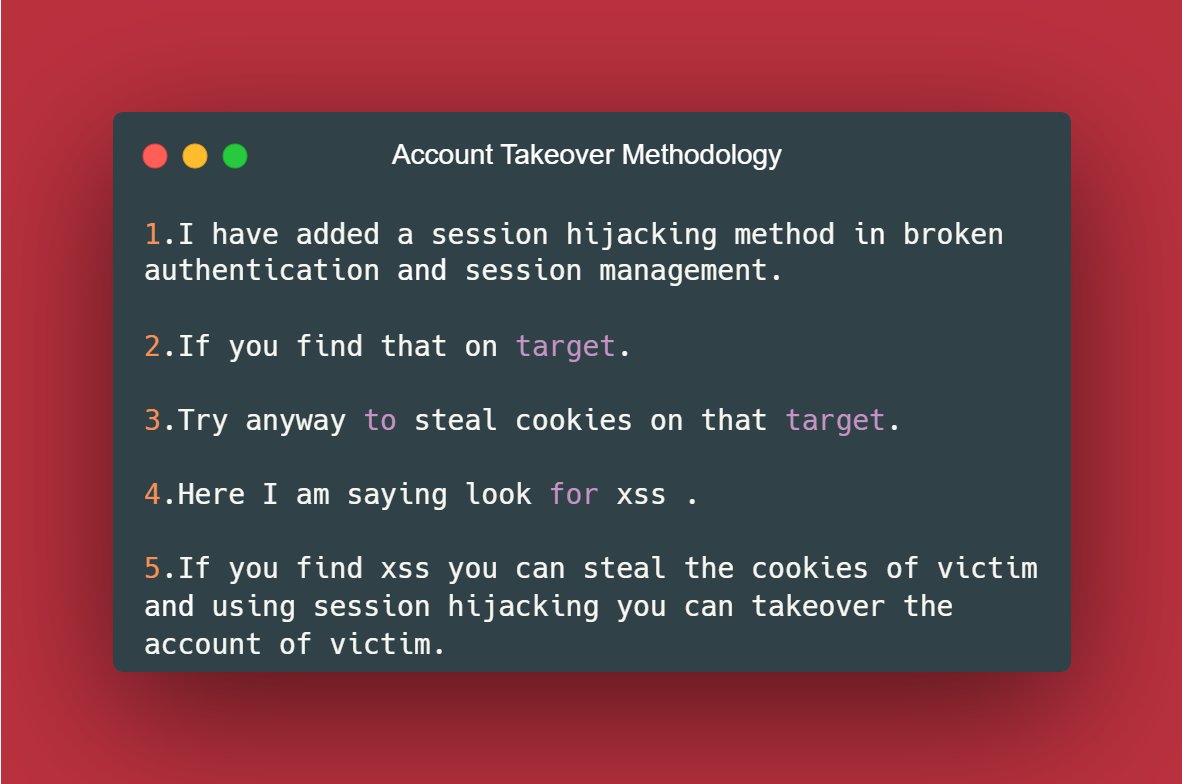
📌No Rate Limit On Login With Weak Password Policy
So if you find that target have weak password policy, try to go for no rate limit attacks in poc shows by creating very weak password of your account.
(May or may not be accepted)
Thread🧵:👇
So if you find that target have weak password policy, try to go for no rate limit attacks in poc shows by creating very weak password of your account.
(May or may not be accepted)
Thread🧵:👇
📌Try For CSRF On
#bugbounty #Infosec
1. Change Password function.
2. Email change
3. Change Security Question
Thread🧵:👇
#bugbounty #Infosec
1. Change Password function.
2. Email change
3. Change Security Question
Thread🧵:👇
Thanks For Reading This Amazing Thread 🧵On :
Account Takeover Methodology
Hope you ♥ Like These All
Follow me for more like👍 this
Account Takeover Methodology
Hope you ♥ Like These All
Follow me for more like👍 this
• • •
Missing some Tweet in this thread? You can try to
force a refresh