
NEW: The British government is introducing a mandatory reporting obligation on managed service providers to disclose cyber incidents, alongside minimum security requirements which could see them fined up to £17 million for non-compliance.
therecord.media/uk-introducing…
therecord.media/uk-introducing…
Why does this matter?
Managed service providers (MSPs) are a critical part of the IT industry. They basically provide the IT departments for a lot of small and medium-sized enterprises that aren't big enough to have their own, and usually also support large enterprises too.
Managed service providers (MSPs) are a critical part of the IT industry. They basically provide the IT departments for a lot of small and medium-sized enterprises that aren't big enough to have their own, and usually also support large enterprises too.
This means that MSPs' computer networks often connect into the networks of a lot of other companies.
So when one of them gets hacked - as happened to Kaseya, below - a lot of other companies can also get compromised. In that case more than 1,500.
therecord.media/kaseya-more-th…
So when one of them gets hacked - as happened to Kaseya, below - a lot of other companies can also get compromised. In that case more than 1,500.
therecord.media/kaseya-more-th…
And it's not just criminals targeting MSPs. Back in 2018 the UK's @NCSC and allies blamed the Chinese Ministry of State Security for a global espionage campaign called Cloud Hopper that was targeting MSPs in order to steal data from their clients.
gov.uk/government/new…
gov.uk/government/new…
The government is now updating essential services covered by the Network and Information Systems (NIS) Regulations (currently water, energy and transport) to include MSPs.
These are required to uphold security standards and notify relevant national authorities about incidents.
These are required to uphold security standards and notify relevant national authorities about incidents.
But this notification requirement has not necessarily proven to be a panacea, as previous coverage has explained.
Despite numerous incidents affecting the gas and energy sector, none at all were reported to Ofgem, the sector's relevant national authority.
news.sky.com/story/uk-cyber…
Despite numerous incidents affecting the gas and energy sector, none at all were reported to Ofgem, the sector's relevant national authority.
news.sky.com/story/uk-cyber…
Nine cyber attacks affecting the British transport sector were also not covered by the UK's mandatory reporting laws, although they were at least disclosed to the government on a voluntary basis. news.sky.com/story/nine-cyb…
The problem is the thresholds themselves for reporting an incident. They're based on whether the incidents impact the actual service being provided; for instance, whether at least 50,000 customers went without electricity supply for more than three minutes. 
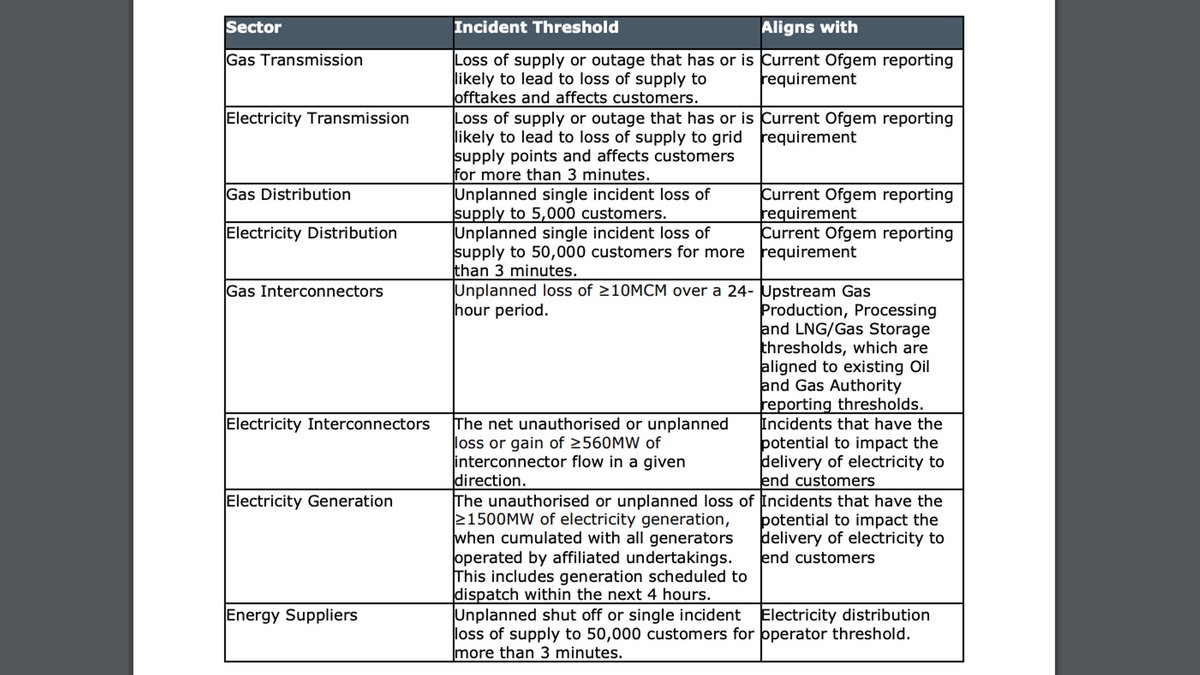
But they simply do not account for the risks that hackers' activities exploiting a network can pose before they turn into attacks.
The government is finally addressing this too.
The government is finally addressing this too.
Essential services will now need to notify regulators “of a wider range of incidents that disrupt service or which could have a high risk or impact to their service, even if they don’t immediately cause disruption,” the government announced on Wednesday.
The new thresholds have not yet been disclosed. They will be chosen by the sector-specific regulators in collaboration with the @NCSC, which it should be said has its own relationships with many of the essential service providers beyond the NIS directive.
🚨 #BrexitDividend🚨
Interestingly the government said it is “able to change the NIS regulations, which were originally derived from the EU’s NIS directive, because the UK has left the EU and can update these laws to better fit the country’s cyber security needs.”
Interestingly the government said it is “able to change the NIS regulations, which were originally derived from the EU’s NIS directive, because the UK has left the EU and can update these laws to better fit the country’s cyber security needs.”
I thought this was curious.
The UK’s major changes, particularly extending the remit of the directive to include MSPs, have already been introduced in the European Union’s own update to the NIS Directive known as NIS 2.
It didn't seem like there was anything really new. But...
The UK’s major changes, particularly extending the remit of the directive to include MSPs, have already been introduced in the European Union’s own update to the NIS Directive known as NIS 2.
It didn't seem like there was anything really new. But...
...there is.
The EU's NIS directives ban regulators from recovering the costs of enforcement activities. In the eyes of the UK this means the laws introduce a financial burden on member states when imposing the legislation that can't be fully recovered.
gov.uk/government/con…
The EU's NIS directives ban regulators from recovering the costs of enforcement activities. In the eyes of the UK this means the laws introduce a financial burden on member states when imposing the legislation that can't be fully recovered.
gov.uk/government/con…
The majority of respondents to the govt's public consultation disagreed that the current rules, which allow the sector-specific authorities to invoice specific companies to pay “the reasonable costs” of audits or inspections, needed to be changed.
assets.publishing.service.gov.uk/government/upl…
assets.publishing.service.gov.uk/government/upl…
The government said that in its view “in general the cost burden of regulation should fall on the regulated, not the general taxpayer. Therefore we need a cost recovery scheme for NIS that reduces the burden on the taxpayer.”
Which is ironic because it means that one of the first areas that Brexit allows the British government to deviate from EU law will be in purposefully introducing more costs for business for the sake of funding regulators. It may be a good idea, but is it the Brexit we voted for?
• • •
Missing some Tweet in this thread? You can try to
force a refresh





