Folks, this is bad. Very, very bad. Hackers and/or malicious insiders have leaked the platform certificates of several vendors. These are used to sign system apps on Android builds, including the "android" app itself. These certs are being used to sign malicious Android apps!
https://twitter.com/maldr0id/status/1598068216391405568
Why is that a problem? Well, it lets malicious apps opt into Android's shared user ID mechanism and run with the same highly privileged user ID as "android" - android.uid.system. Basically, they have the same authority/level of access as the Android OS process!
(Here's a short summary of shared UID, from my Android 13 deep dive: blog.esper.io/android-13-dee…) 
The post on the Android Partner Vulnerability Initiative issue tracker shared SHA256 hashes of the platform signing certificates and correctly signed malware using those certificates. Thanks to sites like @virustotal and @APKMirror, it's trivial to see who is affected...
So, for example, this malware sample: virustotal.com/gui/file/b1f19…
scroll down to the certificate subject/issuer, and whose name do you see? The biggest Android OEM on the planet? Yeah, yikes.
scroll down to the certificate subject/issuer, and whose name do you see? The biggest Android OEM on the planet? Yeah, yikes.
Go to APKMirror and just search for the SHA256 hash of the corresponding platform signing certificate... apkmirror.com/?post_type=app…
Yeah, this certificate is still being used to sign apps.
Yeah, this certificate is still being used to sign apps.
That's just one example. There are others at risk, too.
https://twitter.com/mszustak/status/1598406354464829440
In any case, Google recommends that affected parties should rotate the platform certificate, conduct an investigation into how this leak happened, and minimize the number of apps signed with the platform certificate, so that future leaks won't be as devastating.
Okay, so what are the immediate implications/takeaways for users?
- You can't trust that an app has been signed by the legitimate vendor/OEM if their platform certificate was leaked. Do not sideload those apps from third-party sites/outside of Google Play or trusted OEM store.
- You can't trust that an app has been signed by the legitimate vendor/OEM if their platform certificate was leaked. Do not sideload those apps from third-party sites/outside of Google Play or trusted OEM store.
- This may affect updates to apps that are delivered through app stores if the OEM rotates the signing key, depending on whether or not that app has a V3 signature or not. V3 signature scheme supports key rotation, older schemes do not.
source.android.com/docs/security/…
source.android.com/docs/security/…
OEMs are not required to sign system apps with V3 signatures. The minimum signature scheme version for apps targeting API level 30+ on the system partition is V2.
You can check the signature scheme using the apksigner tool: developer.android.com/studio/command…
You can check the signature scheme using the apksigner tool: developer.android.com/studio/command…
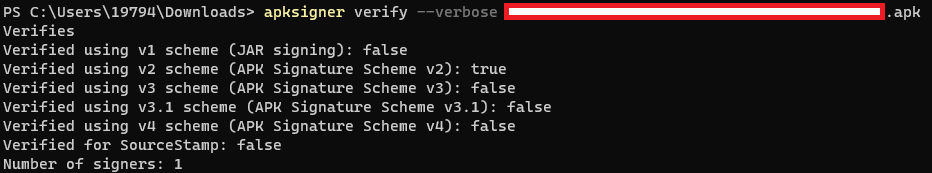
Affected OEMs can still rotate the cert used to sign their system apps that have V2 signatures and then push an OTA update to deliver the updated apps. Then they can push app updates with that new cert, but devices that haven't received OTAs won't receive those app updates.
The leaked platform signing certificates can't be used to install compromised OTA updates, thankfully.
https://twitter.com/maldr0id/status/1598467755887529990
Tip @Techmeme, this story has massive implications.
Statement from Google given to @9to5Google. 
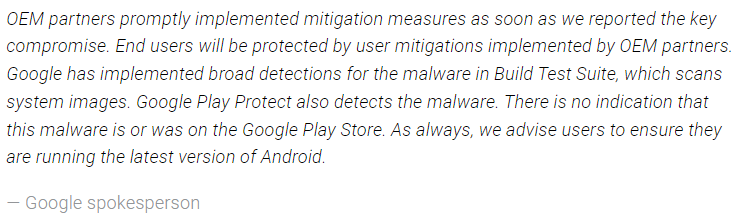
Google Play Protect can indeed mitigate this issue somewhat. Play Protect could flag apps signed by the leaked platform certificate as a potentially harmful application. Google Play already has a database of legitimate app releases from the legitimate vendor, after all.
Statement from Samsung given to @AndroidPolice. 

As @ArtemR and others have noted already, many of the malware samples submitted to VirusTotal are several years old.
• • •
Missing some Tweet in this thread? You can try to
force a refresh