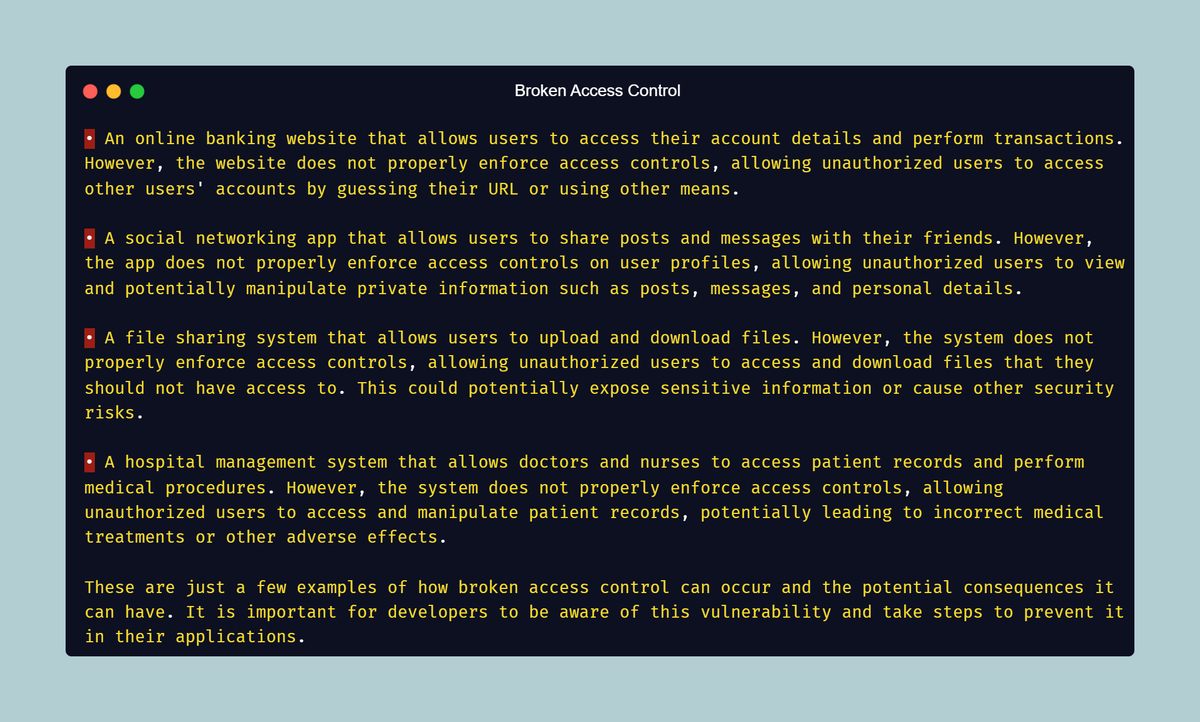
Advanced Header Filtering using tcpdump
To better inspect the request and responses in dump, we would like filtered data packets
To do this, we look for packets that contain PSH & ACK Flag
PSH Flag used to enforce immediate delivery
#bugbounty #infosec #hacking
Thread🧵: 👇
To better inspect the request and responses in dump, we would like filtered data packets
To do this, we look for packets that contain PSH & ACK Flag
PSH Flag used to enforce immediate delivery
#bugbounty #infosec #hacking
Thread🧵: 👇
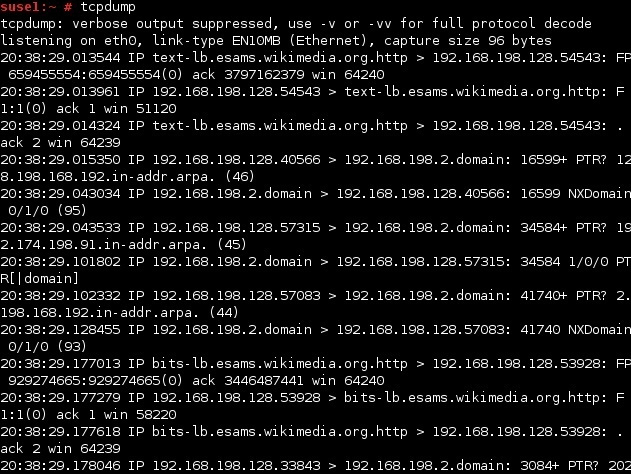
Following diagram depicts the TCP header and shows that TCP flags are defined starting from 14th byte
See img 👇 : we can see ACK & PSH Flag represented by fourth and fifth bits of the 14th byte
Calc req bytes :
CEUAPRSF
WCRCSSYI
REGKHTNN
00011000 = 24 decimal
More 🧵: 👇
See img 👇 : we can see ACK & PSH Flag represented by fourth and fifth bits of the 14th byte
Calc req bytes :
CEUAPRSF
WCRCSSYI
REGKHTNN
00011000 = 24 decimal
More 🧵: 👇
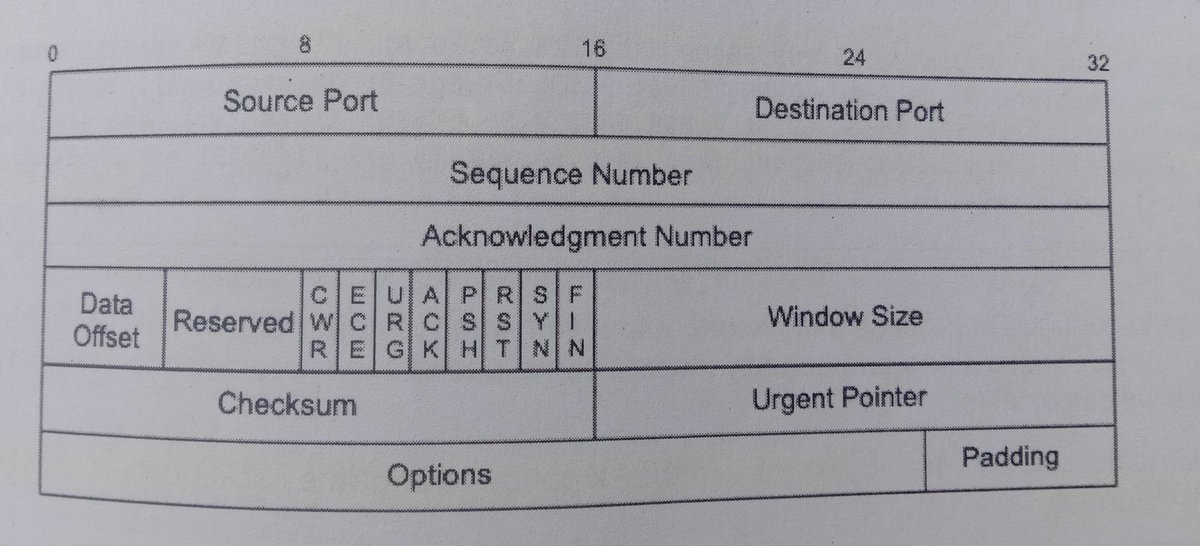
These bytes will give us 00011000, or decimal 24
We can pass this number to tcpdump with TCP[13] = 24 as display filter
To see on packets that contains ACK & PSH bit set represented by 4th and 5th byte (24) of 14th byte of TCP header
More 👇
We can pass this number to tcpdump with TCP[13] = 24 as display filter
To see on packets that contains ACK & PSH bit set represented by 4th and 5th byte (24) of 14th byte of TCP header
More 👇
Note : that TCP array index use for counting the bytes starts at zero 0, so syntax should be ( TCP[13] ).
This will show us that filtered https request and responses
This will show us that filtered https request and responses
Hope you like 👍 this Amazing header Filtering Trick
Join my 🪲 Bounty Tips and tricks Group : t.me/bugbountyresou…
#bugbounty #infosec
Join my 🪲 Bounty Tips and tricks Group : t.me/bugbountyresou…
#bugbounty #infosec
• • •
Missing some Tweet in this thread? You can try to
force a refresh