I'm back home from #AWS #reInvent which means it's time to go through my top 10 favourite / most impactful announcements, in order. Let's begin! 

#10. Amazon Inspector now supports scanning the packages of deployed Lambda functions for Java, Node and Python. Previously, scanning tools would have to be embedded into CI/CD, or forced via ECR Lambda deploys. A great addition to close the gap. 

#9. AWS Verified Access is an identity-aware (ZTNA) HTTP/HTTPS proxy, which allows connections to an NLB, ALB or ENI within your VPC without a VPN or similar. Verified Access supports IAM Identity Center or OIDC for user-based, and Jamf or CrowdStrike for device-based access. 

#8. Both Organizations and AWS Backup now support delegated administrative accounts. This is an enourmous step towards the goal of making the management account a "no touch" zone. I'm hoping we'll see stronger controls to restrict use of the management account soon.
#7. KMS now supports using external key stores for the keying material of CMKs. Though pitched as a regulatory/compliance feature, I can see use cases to help complex centralization of keying material. Official blog does warn against the risks of this though. 

#6. We now have a number of solutions for getting data from S3, RDS, Kinesis and MSK through to Redshift without needing to roll your own pipelines, usually with near realtime consistency. This is a great reduction in operational overheads that data engineers used to endure. 



#5. EventBridge Pipes allows for data pipelines between AWS services such as DDB, SQS, Kinesis, MSK etc. to destinations such as Lambda, Kinesis, and other 3rd parties - including field-level mapping/filter/enrichment support, suspiciously similar to the way AppFlow works. 

#4. Amazon Verified Permissions is an upcoming authorization engine for your own applications. It uses a new syntax called Cedar for rule logic and is designed to replace your own custom authz code, for example in API Gateway Lambda Authorizers. I'm excited to see this one. 

#3. Step Functions have added the Distributed Map step type which supports up to 10k concurrent child executions of a subflow and also comes with an S3 ListObjects iterator out of the box. This makes SFN far more powerful for new workload types, such as ETL. 

#2. Everyone's talking about it...Lambda SnapStart. SnapStart is an opt-in feature which snapshots a functions memory post-invocation and uses that snapshot for future invocations to reduce cold start time, initially available for Java. Be careful of the nuances for this one! 

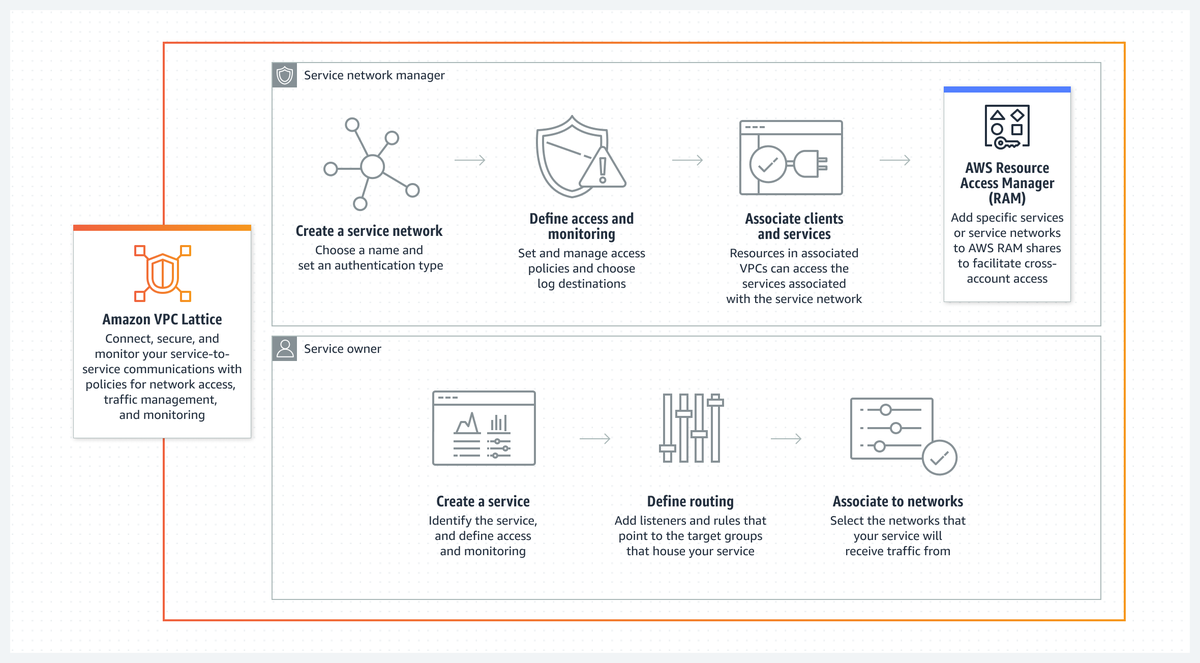
#1. VPC Lattice. This thing is amazing 😍 Imagine exposing your HTTP(S)/gRPC services like PrivateLink, but instead of an ENI it's a link-local address right in your compute - just like how the metadata service works. Features include IAM auth, cross-account, advanced routing. 
• • •
Missing some Tweet in this thread? You can try to
force a refresh

















