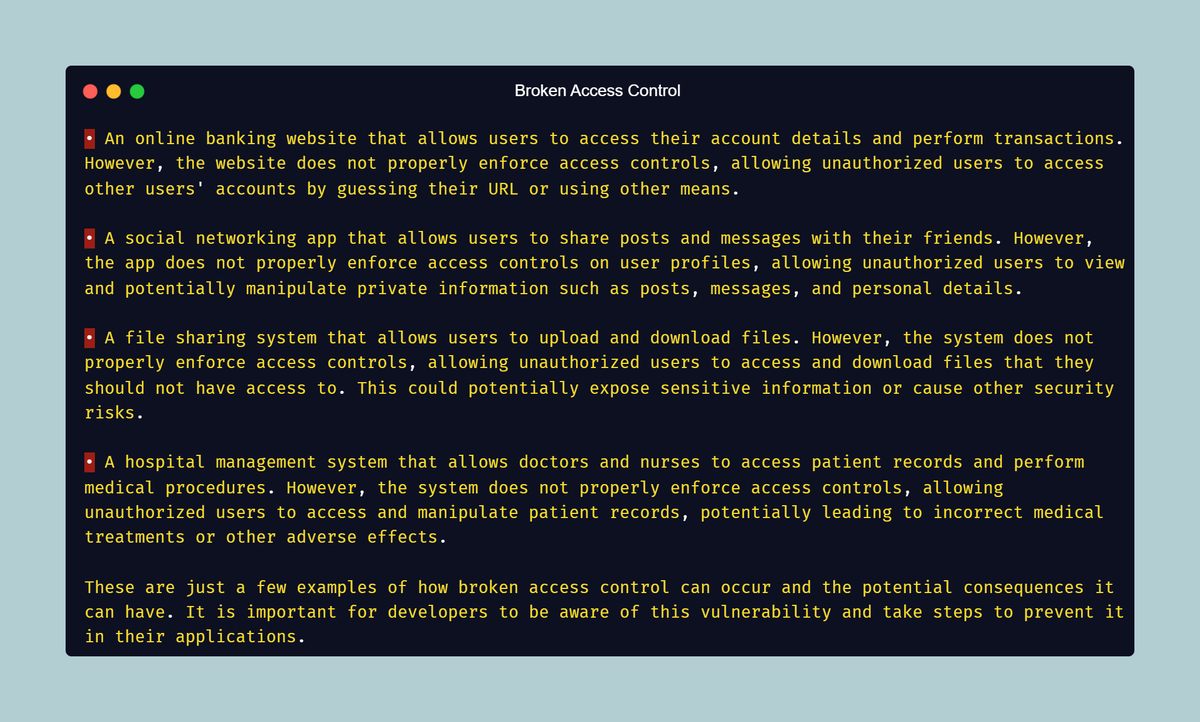
1. Raspberry Pi 4
This is very useful we can install entire Kali Linux on this credit card sized computer.
Raspberry Pi also can be used in many other projects. Cybersecurity experts use it on various way.
👇: More
This is very useful we can install entire Kali Linux on this credit card sized computer.
Raspberry Pi also can be used in many other projects. Cybersecurity experts use it on various way.
👇: More

2. USB Rubber Ducky
The USB Rubber Ducky delivers powerful payloads in seconds by taking advantage of the target computers inherent trust all while deceiving humans by posing as an ordinary USB drive.
👇: More
The USB Rubber Ducky delivers powerful payloads in seconds by taking advantage of the target computers inherent trust all while deceiving humans by posing as an ordinary USB drive.
👇: More

3. Wifi Pineapple
This will automate the auditing of WiFi networks and saves the results.
We can control it with awesome web based interface.
👇: More
This will automate the auditing of WiFi networks and saves the results.
We can control it with awesome web based interface.
👇: More

4. Ubertooth One
Ubertooth One is designed primarily as an advanced Bluetooth receiver, offering capabilities beyond that of traditional adapters,
Which allow for it to be used as a BT signal sniffing and monitoring platform.
👇: More
Ubertooth One is designed primarily as an advanced Bluetooth receiver, offering capabilities beyond that of traditional adapters,
Which allow for it to be used as a BT signal sniffing and monitoring platform.
👇: More

6. USB Killer
the USB Killer rapidly charges its capacitors from the USB power lines. When the device is charged, -200VDC is discharged over the data lines of the host device.
As the result target device becomes burned and unrepairable.
👇: More
the USB Killer rapidly charges its capacitors from the USB power lines. When the device is charged, -200VDC is discharged over the data lines of the host device.
As the result target device becomes burned and unrepairable.
👇: More

7. Bad USB
Attacker can easily carry it as a thumb drive and plug into any PC to inject payload, running own command on it, it also can be controlled over WiFi.
It looks like innocent USB thumb drive, which is a great advantage.
👇: More
Attacker can easily carry it as a thumb drive and plug into any PC to inject payload, running own command on it, it also can be controlled over WiFi.
It looks like innocent USB thumb drive, which is a great advantage.
👇: More

8. Hardware Keylogger
A hardware keylogger can be inserted between USB keyboard and computer. It captures all the keystrokes made from the keyboard, must have thing for every cybersecurity expert.
👇: More
A hardware keylogger can be inserted between USB keyboard and computer. It captures all the keystrokes made from the keyboard, must have thing for every cybersecurity expert.
👇: More

9. Micro-controllers
There are lots of micro-controllers used by ethical hackers.
NodeMCU ESP8266
A Wifi development board and Can be used in various way, It also can be used to create phishing pages over WiFi.
👇: More
There are lots of micro-controllers used by ethical hackers.
NodeMCU ESP8266
A Wifi development board and Can be used in various way, It also can be used to create phishing pages over WiFi.
👇: More

10. RTL-SDR
It can be used to intercept radio frequencies. We can use it for listening others conversations. It is also able to intercept GSM mobile calls and SMS. It is very useful for cybersecurity experts.
👇: More
It can be used to intercept radio frequencies. We can use it for listening others conversations. It is also able to intercept GSM mobile calls and SMS. It is very useful for cybersecurity experts.
👇: More

11. Proxmark3 NFC RFID Card Reader
This devices can make read the data of RFID and NFC cards and then make a copy of it. We can write the new copies on blank cards provided with this package
👇: More
This devices can make read the data of RFID and NFC cards and then make a copy of it. We can write the new copies on blank cards provided with this package
👇: More

12. WiFi Adapters (Monitor Mode & Packet Injection)
WiFi adapter specially which supports monitor mode and packet injection is essential for WiFi penetration testing. So most of the hackers uses it.
👇: More
WiFi adapter specially which supports monitor mode and packet injection is essential for WiFi penetration testing. So most of the hackers uses it.
👇: More

Thanks You Reading This Amazing Thread 🧵On :
Top 12 Accessories that Hacker use Mostly
Hope you'll like this 👍
Check out 👇 :
=====
My Bugbounty Tips Group : t.me/bugbountyresou…
=====
Top 12 Accessories that Hacker use Mostly
Hope you'll like this 👍
Check out 👇 :
=====
My Bugbounty Tips Group : t.me/bugbountyresou…
=====
• • •
Missing some Tweet in this thread? You can try to
force a refresh