
Find JavaScript Files
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

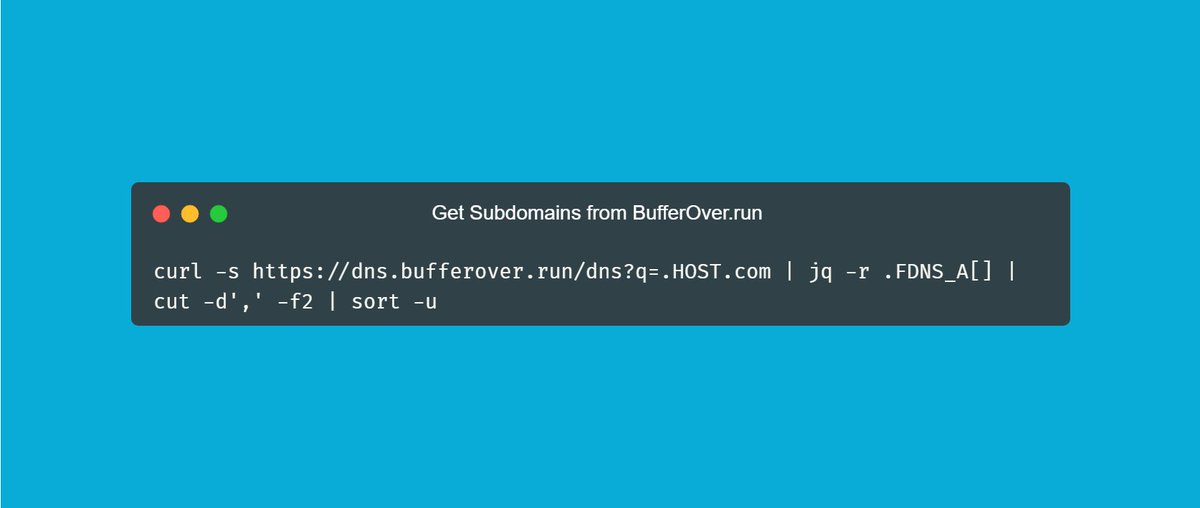
Get Subdomains from BufferOver. run
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
Extracts Juicy Informations
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

Get Subdomains from Riddler. io
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

Get Subdomains from Archive
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

Get Subdomains from crt. sh
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

Dump In-scope Assets from chaos-bugbounty-list
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

I love you all of you guys to support me
I Provide Useful and juicy info and Resources that help infosec community to grow
Hope You'll Like My Work 👍
Hit A like If you want More Like These
I Provide Useful and juicy info and Resources that help infosec community to grow
Hope You'll Like My Work 👍
Hit A like If you want More Like These
• • •
Missing some Tweet in this thread? You can try to
force a refresh






