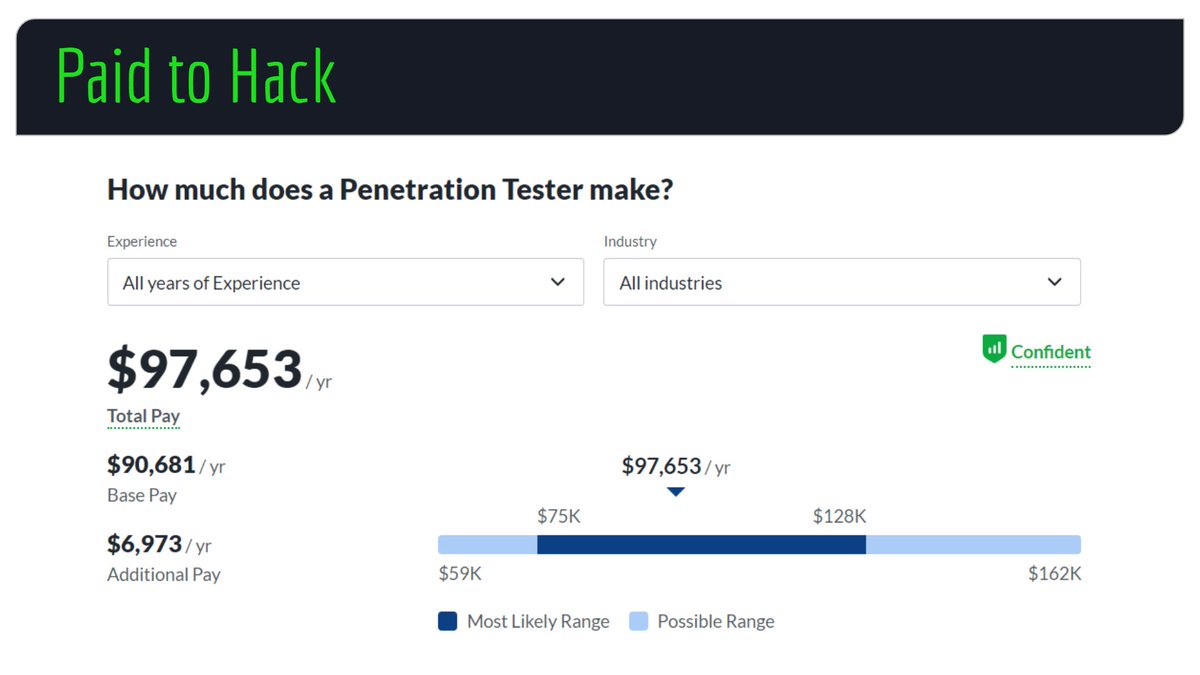
Paid to Hack!
How much money can you make in cybersecurity?
(thread)
How much money can you make in cybersecurity?
(thread)
10. I made a video with my insights on this. Numbers are from @Glassdoor and infosec-jobs.com.
Like, retweet, and follow me for more posts like this.
#infosec #pentesting #cybersecurity #appsec
Like, retweet, and follow me for more posts like this.
#infosec #pentesting #cybersecurity #appsec
• • •
Missing some Tweet in this thread? You can try to
force a refresh