Hey, Google's gotta make money somehow, yah know?
virustotal.com/gui/file/2de68…

virustotal.com/gui/file/2de68…
https://twitter.com/NFT_GOD/status/1614442010773004288


This is probably crazy, but hear me out...
What if, before Google pushes a paid advertisement link at customers, they checked with the Google-owned VirusTotal site to confirm that the site isn't distributing known malware?
You know, to at least pretend that they care...
🤔
What if, before Google pushes a paid advertisement link at customers, they checked with the Google-owned VirusTotal site to confirm that the site isn't distributing known malware?
You know, to at least pretend that they care...
🤔
Note that this OBS thing isn't an anomaly.
Go ahead and search for about anything that you can download.
The first hits are malware links that Google gets paid money to promote.
Just business as usual...
virustotal.com/gui/file/1e0a8…
virustotal.com/gui/file/d4984…
virustotal.com/gui/file/8fe23…



Go ahead and search for about anything that you can download.
The first hits are malware links that Google gets paid money to promote.
Just business as usual...
virustotal.com/gui/file/1e0a8…
virustotal.com/gui/file/d4984…
virustotal.com/gui/file/8fe23…




How about Notepad++?
As it turns out, there is a non-malware sponsored hit.
Why? Notepad++ paid for the shakedown.
"Sure would be a shame if somebody was looking for your software and got malware instead, wouldn't it?"



As it turns out, there is a non-malware sponsored hit.
Why? Notepad++ paid for the shakedown.
"Sure would be a shame if somebody was looking for your software and got malware instead, wouldn't it?"




Would checking VirusTotal work for preventing ads with malware?
Of course not! Don't be silly.
If you search for WinRAR, Google will suggest that you click on 2 links to download malware. But with 0 hits on VT.
How do I know it's malware? The MSI has super sketchy PowerShell. 😬



Of course not! Don't be silly.
If you search for WinRAR, Google will suggest that you click on 2 links to download malware. But with 0 hits on VT.
How do I know it's malware? The MSI has super sketchy PowerShell. 😬


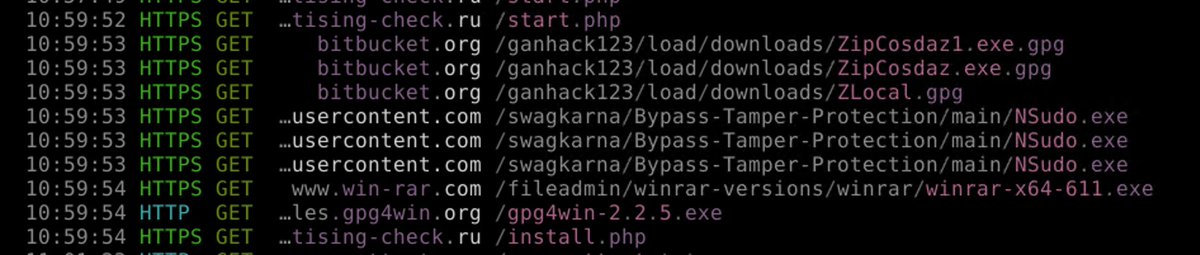

While this MSI has 0 VT hits virustotal.com/gui/file/54150…
it *does* trigger several Sigma rules.
The PowerShell payload is not embedded in the MSI, but is downloaded from: huggingface[.]co/Absurd/Xernya/raw/main/winrar
Raw here: controlc.com/ee999175
Decoded: controlc.com/34d11926

it *does* trigger several Sigma rules.
The PowerShell payload is not embedded in the MSI, but is downloaded from: huggingface[.]co/Absurd/Xernya/raw/main/winrar
Raw here: controlc.com/ee999175
Decoded: controlc.com/34d11926


By looking at the @huggingface
open directory, we can see that this actor is likely currently paying Google for their help in distributing malware via searches for:
VLC CryptoTab Filezilla KMPlayer Lightshot Notepad++ Rufus utorrent Winrar and 7-zip
huggingface.co/Absurd/Xernya/…
open directory, we can see that this actor is likely currently paying Google for their help in distributing malware via searches for:
VLC CryptoTab Filezilla KMPlayer Lightshot Notepad++ Rufus utorrent Winrar and 7-zip
huggingface.co/Absurd/Xernya/…

On the upside:
- Google seems to have taken down the malicious ads that we've all noticed.
- VirusTotal detection is up to THREE for the malicious WinRAR MSI that I downloaded.
So yeah, for those of you who rely on AV to protect you from all things bad...
virustotal.com/gui/file/54150…
- Google seems to have taken down the malicious ads that we've all noticed.
- VirusTotal detection is up to THREE for the malicious WinRAR MSI that I downloaded.
So yeah, for those of you who rely on AV to protect you from all things bad...
virustotal.com/gui/file/54150…

And while they're not linking to downloads of malware, the ads that are being served up even today sure have a sketchy feel to them.
"VirtualBox is a enormous application which will help you."
beijingrestaurantroanoke?
jasonbarrmusic?
No funny business going on here for sure. 🤔
"VirtualBox is a enormous application which will help you."
beijingrestaurantroanoke?
jasonbarrmusic?
No funny business going on here for sure. 🤔

Scratch that. The Google ads for VirtualBox are indeed linking to malware-distributing sites.
For some reason when I checked this morning the page was serving some oddly unrelated site.
But yeah, it's definitely bad stuff STILL being promoted by Google.🤦♂️
virustotal.com/gui/file/1152e…

For some reason when I checked this morning the page was serving some oddly unrelated site.
But yeah, it's definitely bad stuff STILL being promoted by Google.🤦♂️
virustotal.com/gui/file/1152e…


What's detected is not the EXE itself, but rather that it has a file that extracts to be very large.
Running the obfuscated .NET EXE makes a request to hxxp://79[.]137[.]197[.]29/rfbqtotg/Dpcejhz.bmp
(for me at least)
Which b64 decodes to a blob with a bunch of reversed strings.

Running the obfuscated .NET EXE makes a request to hxxp://79[.]137[.]197[.]29/rfbqtotg/Dpcejhz.bmp
(for me at least)
Which b64 decodes to a blob with a bunch of reversed strings.


Which, duh, is a .NET PE file that is simply reversed.
Reversing the order of the bytes in this file results in an EXE that is detected by 15 AV engines on VT:
virustotal.com/gui/file/3709b…
Reversing the order of the bytes in this file results in an EXE that is detected by 15 AV engines on VT:
virustotal.com/gui/file/3709b…

Google: "We reviewed the ads in question and have removed them"
The real world, several days later:
Google for KMPlayer and you get an Ad for a malware-serving lookalike site (oddly for VLC).
If you're on x86/x86_64 Windows, you'll get this malware: virustotal.com/gui/file/26a07…


The real world, several days later:
Google for KMPlayer and you get an Ad for a malware-serving lookalike site (oddly for VLC).
If you're on x86/x86_64 Windows, you'll get this malware: virustotal.com/gui/file/26a07…



This malware is different than the others I've seen in this (recent?) Google malvertising flurry.
This has an invalid signature from IP Izmaylov Artem Andreevich, and connects to 79[.]137[.]133[.]225:8081 for further instructions presumably.
This has an invalid signature from IP Izmaylov Artem Andreevich, and connects to 79[.]137[.]133[.]225:8081 for further instructions presumably.

Google: "We have robust policies prohibiting ads that attempt to circumvent our enforcement by disguising the advertiser’s identity and impersonating other brands, and we enforce them vigorously."
The real world: This is completely out of control and we can't do anything about it



The real world: This is completely out of control and we can't do anything about it




How about LibreOffice?
Surely I can trust Google Ads for that search, right?
Clearly you haven't been paying attention.
Until Google can prove to the world that their ads can be trusted, you better believe that ALL ads from them point to malware distribution websites.


Surely I can trust Google Ads for that search, right?
Clearly you haven't been paying attention.
Until Google can prove to the world that their ads can be trusted, you better believe that ALL ads from them point to malware distribution websites.



How about G*MP?
No, I won't say the name here as the last time I did that I got banned from this hellsite. But you know what app I'm talking about.
Yes. Malware.
If you get an ad from Google, it's going to be a link to malware.
And apparently this is just business as usual.


No, I won't say the name here as the last time I did that I got banned from this hellsite. But you know what app I'm talking about.
Yes. Malware.
If you get an ad from Google, it's going to be a link to malware.
And apparently this is just business as usual.



I mean, hell, even searching Google for "python" brings you to malware.
Please, Google. Convince me that you're doing something about this. Anything at all.



Please, Google. Convince me that you're doing something about this. Anything at all.




Google: "We have robust policies prohibiting ads..."
Translation: "We have rules written down somewhere that state 'thou shall not' under penalty of (??)"
Google: "... and we enforce them vigorously"
Translation: "We might get around to manually taking down violators eventually.


Translation: "We have rules written down somewhere that state 'thou shall not' under penalty of (??)"
Google: "... and we enforce them vigorously"
Translation: "We might get around to manually taking down violators eventually.



I'm continuing this thread to have a record of what Google ads link to what malware and when.
And also to periodically check if they've done anything about it.
Mute the thread if you already grok Google's business model of profiting from malware distribution.


And also to periodically check if they've done anything about it.
Mute the thread if you already grok Google's business model of profiting from malware distribution.



If you're a poor sap that used Google to search for Blender, you'll probably have to scroll to get past the malware ads.
Four out of the FOUR Ads for blender link to malware.
That's 100%. A+!

Four out of the FOUR Ads for blender link to malware.
That's 100%. A+!


How about @AMD or @nvidia?
Even though NVIDIA pays Google Ad money, Google encourages visitors to go to malware-distributing site instead of the real company, listing the malware ad first. Presumably for reasons.
Neat.


Even though NVIDIA pays Google Ad money, Google encourages visitors to go to malware-distributing site instead of the real company, listing the malware ad first. Presumably for reasons.
Neat.



Some of the domain names aren't "obviously" malicious.
e.g. the schumanlawfirm[.]com site that you get as an ad for "winrar" 🤔
It seems like a normal site.
But when you view it with the google Referer header, plus the appropriate utm_term value, you get the fake download site.



e.g. the schumanlawfirm[.]com site that you get as an ad for "winrar" 🤔
It seems like a normal site.
But when you view it with the google Referer header, plus the appropriate utm_term value, you get the fake download site.




You also get the same schumanlawfirm[.]com malware site when you search for 7-zip.
And it still serves up the WinRAR-branded malware.
"I don't click ads"
"I wouldn't fall for this"
"I use an ad blocker"
Congratulations?
Some people do fall victim to this. It's a numbers game.
And it still serves up the WinRAR-branded malware.
"I don't click ads"
"I wouldn't fall for this"
"I use an ad blocker"
Congratulations?
Some people do fall victim to this. It's a numbers game.

We're over 1 week into when I personally first started pulling this thread, and the Google malware ads are still going strong. Presumably it's been happening well before I started looking into it. 





Google employee 1: www[.]homeforcutepets[.]com has paid us money to advertise their link for any time somebody searches for "winrar"
This seems a bit... weird?
Google employee 2: What part of "has paid us money" don't you understand?
Google employee 1: Sorry. Let's promote it!
This seems a bit... weird?
Google employee 2: What part of "has paid us money" don't you understand?
Google employee 1: Sorry. Let's promote it!

How about winrar (again)?
Google ad for www[.]rajaimpexindo[.]com
which redirects to rar-lab[.]top
which has download w/ a VT detection rate of 0
But retrieves PowerShell from softs-lab[.]ru/winrar.gpg
which installs GPG and decrypts bad stuff w/ password of "putingod"



Google ad for www[.]rajaimpexindo[.]com
which redirects to rar-lab[.]top
which has download w/ a VT detection rate of 0
But retrieves PowerShell from softs-lab[.]ru/winrar.gpg
which installs GPG and decrypts bad stuff w/ password of "putingod"




It would be useful to know all the targeted #GoogleAdMalware ad words. But TBH, I'm just picking some apps that I think are popular, and/or ones that @malwrhunterteam mentions.
Google might be doing *something* about it, but it's not enough to be noticeable.
The ads are bad. 🤦♂️


Google might be doing *something* about it, but it's not enough to be noticeable.
The ads are bad. 🤦♂️



And while the #GoogleAdMalware download for Visual Studio Code gets 10 detections on VirusTotal, the malicious fake WinRAR installer still gets ZERO detections, despite being first submitted two days ago.
Google is still promoting malware.
AV isn't detecting things.
Good luck? 🤷♂️


Google is still promoting malware.
AV isn't detecting things.
Good luck? 🤷♂️


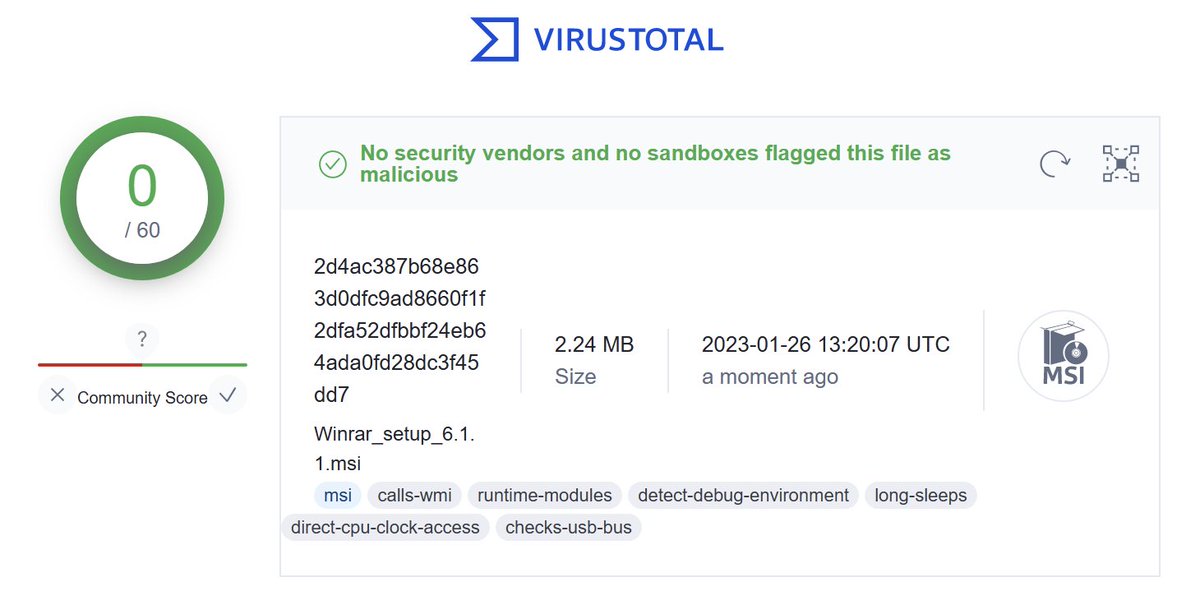
I've heard a rumor that Google is trying to do something about the #GoogleAdMalware problem.
However, as a member of the unwashed masses and I see THREE malicious Blender ads before the legitimate site ad is listed, I remain firmly in the "I'll believe it when I see it" camp.
However, as a member of the unwashed masses and I see THREE malicious Blender ads before the legitimate site ad is listed, I remain firmly in the "I'll believe it when I see it" camp.

Are you one of those security weirdos who hovers links before clicking them to see where they go?
You are?? Neat.
You know that doing this proves nothing, right?



You are?? Neat.
You know that doing this proves nothing, right?




This Thunderbird #GoogleAdMalware isn't alone in this technique.
The Docker one plays the exact same trick, with a similarly-named payload. So presumably the same threat actor.
Pretty much the only thing that VirusTotal detects is the trick of a file that extracts quite large.


The Docker one plays the exact same trick, with a similarly-named payload. So presumably the same threat actor.
Pretty much the only thing that VirusTotal detects is the trick of a file that extracts quite large.



How about OpenOffice?
I bet there are people out there who would use Google to find where to download it from.
The #GoogleAdMalware link points to a domain that uses a lowercase L, which sort of looks OK?
Google gets paid; threat actor gets their malware deployed. Everybody wins?


I bet there are people out there who would use Google to find where to download it from.
The #GoogleAdMalware link points to a domain that uses a lowercase L, which sort of looks OK?
Google gets paid; threat actor gets their malware deployed. Everybody wins?



To be fair, not ALL ads are of the #GoogleAdMalware type.
Sometimes you're lucky enough to only get a full page of questionable-value links. Like searching for Adobe Reader.
🤷♂️
Sometimes you're lucky enough to only get a full page of questionable-value links. Like searching for Adobe Reader.
🤷♂️

How about CPU-Z?
If you're not careful, you might end up with the 300MB malware version that Google wants you to install.
Not the real version, which is 2MB.

If you're not careful, you might end up with the 300MB malware version that Google wants you to install.
Not the real version, which is 2MB.


Somebody might use Google to search for where to download Adobe (Reader)
Hopefully they don't click on the #GoogleAdMalware links.
Is it ironic that one of the VirusTotal hits for the malware Google is advertising is... Google?


Hopefully they don't click on the #GoogleAdMalware links.
Is it ironic that one of the VirusTotal hits for the malware Google is advertising is... Google?



Adobe Reader not your thing?
That's fine. #GoogleAdMalware links for searches for your other PDF readers, like Foxit, are there for you.
Google, the whatever-the-heck-is-on-VirusTotal thing detects it as malware.
But Google, the website, is encouraging you to go to the site. 🤔



That's fine. #GoogleAdMalware links for searches for your other PDF readers, like Foxit, are there for you.
Google, the whatever-the-heck-is-on-VirusTotal thing detects it as malware.
But Google, the website, is encouraging you to go to the site. 🤔




How about Java?
I bet I could use Google to find out where to download it.
Oh, right. Just another #GoogleAdMalware link to a completely normal domain name that was registered a couple days ago.
VirusTotal comes up with 0 hits for the download, so I'm sure that's safe to run...


I bet I could use Google to find out where to download it.
Oh, right. Just another #GoogleAdMalware link to a completely normal domain name that was registered a couple days ago.
VirusTotal comes up with 0 hits for the download, so I'm sure that's safe to run...



About this #GoogleAdMalware:
- Written in JavaFX
- Bundles its own JRE
- 0 detections on VT.
- Retrieves and runs chatgpt-go\.online/java.exe
- The *payload* is detected by 15 on VT
- Doesn't work if logged on as a non-admin.
I guess writing malware in Java is the way to go??


- Written in JavaFX
- Bundles its own JRE
- 0 detections on VT.
- Retrieves and runs chatgpt-go\.online/java.exe
- The *payload* is detected by 15 on VT
- Doesn't work if logged on as a non-admin.
I guess writing malware in Java is the way to go??



Let's look at some Adobe #GoogleAdMalware
- 0 hits on VT
- Loader is PyArmor-encrypted, providing its own Python. Thanks nesrak1 Bone Density!
- This python downloads an encrypted binary (AES256 + pbkdf2 + password), and decrypts it with its own openssl.exe
- Final EXE: 49 on VT



- 0 hits on VT
- Loader is PyArmor-encrypted, providing its own Python. Thanks nesrak1 Bone Density!
- This python downloads an encrypted binary (AES256 + pbkdf2 + password), and decrypts it with its own openssl.exe
- Final EXE: 49 on VT




With both the JavaFX and the PyArmor #GoogleAdMalware, an observer of MITM'd Windows HTTPS traffic will simply see no web requests occur.
Neither Python nor Java use the Windows-level trusted Root CA list.
Presumably this is done to avoid sandbox detonations showing requests.🤔
Neither Python nor Java use the Windows-level trusted Root CA list.
Presumably this is done to avoid sandbox detonations showing requests.🤔
Looking at the signing certificate of "Agilable Consulting Inc." (Issued by @sslcorp), we can #GoogleAdMalware that was signed over 2 months ago.
Samples signed by "Pinesville Ltd" (Issued by @Entrust_Corp) is a touch newer.
AV detection is abysmal.

Samples signed by "Pinesville Ltd" (Issued by @Entrust_Corp) is a touch newer.
AV detection is abysmal.


Both certificates are from presumably the same threat actor, given that the #GoogleAdMalware installer structure is virtually identical. 20 diff't installers retrieve an encrypted payload from one of #batloader C&Cs:
pixelarmada\.su
statisticpixels\.com
updateclientssoftware\.com
pixelarmada\.su
statisticpixels\.com
updateclientssoftware\.com
The #GoogleAdMalware fun seems to have slowed down. Not so much the percent of ads that lead to malware, but rather the number of searches that show ads at all.
If you do get an ad, it's still probably bad news.
MSI -> python -> PyArmor -> statisticpixels\.com -> openssl decode.


If you do get an ad, it's still probably bad news.
MSI -> python -> PyArmor -> statisticpixels\.com -> openssl decode.



yummyrecipes\.site?
Sure, that sounds like official place to download Adobe Reader from!
But hey, at least by now we're up to
*checks notes*
TWO antivirus products that detect this #GoogleAdMalware installer as something you perhaps don't want.


Sure, that sounds like official place to download Adobe Reader from!
But hey, at least by now we're up to
*checks notes*
TWO antivirus products that detect this #GoogleAdMalware installer as something you perhaps don't want.



User: Asks Google where they can get Adobe Reader.
Google: Might I interest you in fox1t\.rcishoes.com?
User: ...
I can't definitively say that this is #GoogleAdMalware, as the offered EXE download is currently 0kb in size. But yeah, pretty sure we all know what's going on here.

Google: Might I interest you in fox1t\.rcishoes.com?
User: ...
I can't definitively say that this is #GoogleAdMalware, as the offered EXE download is currently 0kb in size. But yeah, pretty sure we all know what's going on here.


Some of these threat actors seem sort of sloppy.
- Convincing Google to push out #GoogleAdMalware?✅
- Being able to run a web server without producing 500 errors?❌

- Convincing Google to push out #GoogleAdMalware?✅
- Being able to run a web server without producing 500 errors?❌


I suppose what's non-trivial about running this web server is that these #GoogleAdMalware Adobe Reader installers seem to be digitally signed (by "Pinesville Ltd" in this case) on demand.
As such, no two installers will have the same file hash.
Detection on VirusTotal is 1/50 👍



As such, no two installers will have the same file hash.
Detection on VirusTotal is 1/50 👍




• • •
Missing some Tweet in this thread? You can try to
force a refresh












![[Issuer]](https://pbs.twimg.com/media/FseYbrgaMAIrIAP.png)













